Configure Cloud Connector to use LDAPS
Lightweight Directory Access Protocol Secure (LDAPS) allows client and directory services to use the LDAP protocol over a secure channel. LDAPS secures the session on connection, usually using port TCP 636. When used with Active Directory, where the target server is also a Global Catalog and part of a multi-domain environment, use ports TCP 3269 or 3268. (Global Catalogs only contain a Partial Attribute Set (PAS) and more configuration is necessary for the included attributes.)
LDAPS is used to protect authentication credentials when binding to the Directory Server. While it supports any Directory Service, Active Directory is the most common use case.
NOTE: Another variety of secure LDAP communication uses STARTTLS, but this is not LDAPS.
For information about Azure, see Enable LDAPS Support on Azure Active Directory.
Prerequisites
Before you begin, you will need:
- Install and start Skyhigh Cloud Connector.
- The Directory Server's Public Certificate, in PEM or CRT format.
- Access to Java. Use the keytool utility in the java install path/bin to create a Java TrustStore to contain the Public Certificate.
- Notepad++ or another text editor that respects Unix EOL characters.
Create a Java TrustStore
Create a Java TrustStore repository to contain the Directory Server's Public Certificate. This TrustStore is then used by Cloud Connector when it connects the Directory Server.
- Copy the Public Certificate to a computer with Java installed. (This does not have to be the system where Cloud Connector is installed.)
- Open a terminal or command window on the host, change to the Java bin directory, and run the following command:
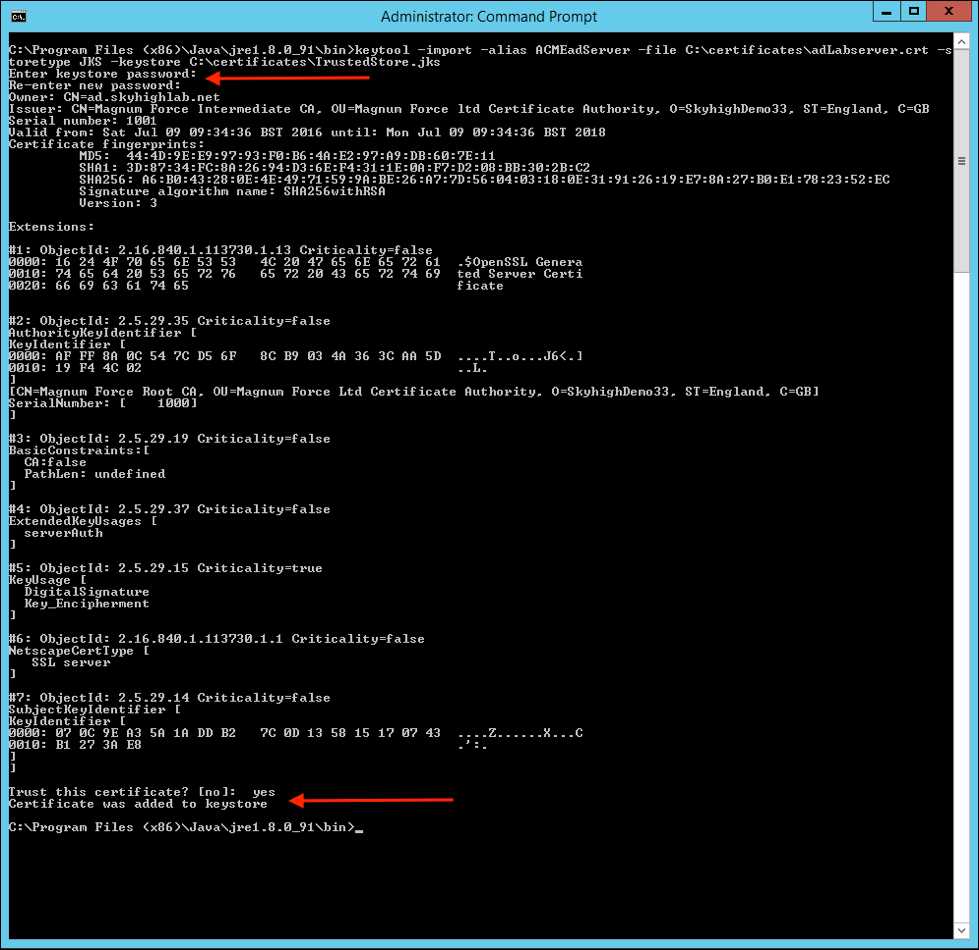
keytool -import -alias <aliasname> -file <adServerCertificate> -storetype JKS -keystore <trustStoreName>
aliasnameis used as a reference in the store. You can name it anything that is useful.adServercertificateis the path to the Public Certificate file.trustStoreNameis the name, with optional location, where the TrustedStore file will be created.
For example, your command may look similar to:
keytool -import -alias ACMEadServer -file C:\certificates\adLabserver.pem -storetype JKS -keystore C:\certificates\TrustedStore.jks
- Create a password when prompted. This password is used later to configure Cloud Connector .
- Trust the certificate when prompted by answering Yes.
IMPORTANT: If you created the TrustStore using a system different from the one where Cloud Connector is installed, copy this file to the Cloud Connector system.
Configure Cloud Connector to Use LDAPS
To enable LDAPS on Cloud Connector
- In Skyhigh CASB go to Settings > Infrastructure > EC Configuration.
- On the Custom Attributes tab:
- Toggle to ON, then click Actions > Edit.
- Select the data source Active Directory.
- For Enable Secure LDAP for AD, select Yes.
- Enter the Trust Store Path and Trust Store Password.
- Enter the LDAP User Upload Endpoint.
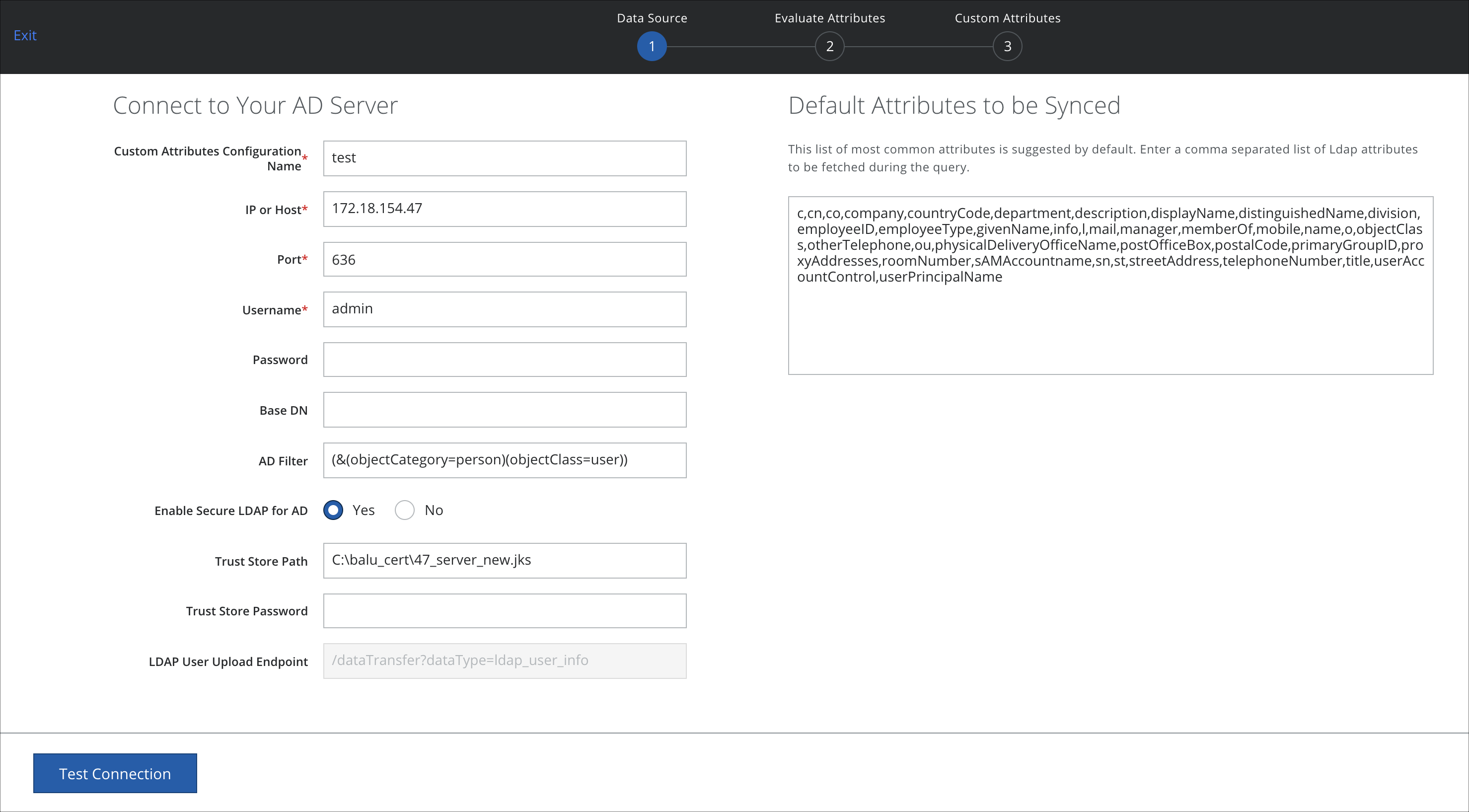
- Click Test Connection.
Confirm Cloud Connector is Using LDAPS
- Open the logprocessor.db.script file and check for the following properties:
INSERT INTO PROPERTY VALUES('activeDirectory.port','\u0005\u00b2\u0099','2018-11-19 00:08:06.685000') INSERT INTO PROPERTY VALUES('activeDirectory.trustStorePassword','@\u00f4\u00ddmQ|','2018-11-19 00:09:54.795000') INSERT INTO PROPERTY VALUES('activeDirectory.trustStorePath','p\u00bb\u0080kGf9\u00c2\u0080\u00026\u00bf{(\u00afN\u00e5\u001bt$\u0008t\u00d6\u00a7','2018-11-19 00:09:28.154000') INSERT INTO PROPERTY VALUES('anamaly_import.timestamp','0','2018-11-18 23:42:14.638000') - Make sure the profile has changed from false to true:
activeDirectory: enableSSL: "true"
- Enable AD integration using port number 636 (LDAPs).
- Check the logs to confirm that AD fetch functionality is working using LDAPs, for example:
19 Nov 2018 08:25:03 [INFO ] [https-jsse-nio-8443-exec-4] c.s.e.w.s.LPRestlet | Serving web request for path /activedirectoryquery 19 Nov 2018 08:25:03 [DEBUG] [https-jsse-nio-8443-exec-4] c.s.e.w.s.l.a.ActiveDirectoryQueryHandler| Getting users for ActiveDirectoryFetchQuery{csvDataSource=null, directoryUserDataSource=ActiveDirectoryDataSource{host='172.23.5.165', port=636, userName='ecqa\administrator', activeDirectoryQuery=ActiveDirectoryQuery{base=null, attributes=c,cn,co,company,countryCode,department,description,displayName,distinguishedName,division,employeeID,employeeType,givenName,info,l,mail,manager,memberOf,mobile,name,o,objectClass,otherTelephone,ou,physicalDeliveryOfficeName,postOfficeBox,postalCode,primaryGroupID,proxyAddresses,roomNumber,sAMAccountname,sn,st,streetAddress,telephoneNumber,title,userAccountControl,userPrincipalName, filter=(&(objectCategory=person)(objectClass=user)), virtualAttributes=[]}, activeDirectorySslSettings=null}, numberOfUsers=20} 19 Nov 2018 08:25:03 [INFO ] [https-jsse-nio-8443-exec-4] c.s.e.l.i.DirectoryUserConnectionFactoryImpl| Connecting LDAPS host: 172.23.5.165 port: 636 19 Nov 2018 08:25:04 [INFO ] [https-jsse-nio-8443-exec-4] c.s.e.l.i.DirectoryUserConnectionFactoryImpl| LDAP bind successful 19 Nov 2018 08:25:04 [INFO ] [https-jsse-nio-8443-exec-4] c.s.e.l.i.ActiveDirectoryUsersFetcher| Determined BaseDN from defaultNamingContext as: DC=ecqa,DC=com 19 Nov 2018 08:25:04 [INFO ] [Active Directory Import Thread] c.s.e.l.i.ActiveDirectoryUsersFetcher| Starting Active Directory Import Thread 19 Nov 2018 08:25:04 [INFO ] [Active Directory Import Thread] c.s.e.l.i.ActiveDirectoryUsersFetcher| Determined BaseDN from defaultNamingContext as: DC=ecqa,DC=com 19 Nov 2018 08:25:04 [DEBUG] [Active Directory Import Thread] c.s.e.l.i.ActiveDirectoryUsersFetcher| Executing search request 'SearchRequest(baseDN='DC=ecqa,DC=com', scope=SUB, deref=NEVER, sizeLimit=0, timeLimit=0, filter='(&(objectCategory=person)(objectClass=user))', attrs={c, cn, co, company, countryCode, department, description, displayName, distinguishedName, division, employeeID, employeeType, givenName, info, l, mail, manager, memberOf, mobile, name, o, objectClass, otherTelephone, ou, physicalDeliveryOfficeName, postOfficeBox, postalCode, primaryGroupID, proxyAddresses, roomNumber, sAMAccountname, sn, st, streetAddress, telephoneNumber, title, userAccountControl, userPrincipalName})' 19 Nov 2018 08:25:04 [INFO ] [Active Directory Import Thread] c.s.e.l.i.ActiveDirectoryUsersFetcher| Search Reference returned : 4 19 Nov 2018 08:25:04 [INFO ] [Active Directory Import Thread] c.s.e.l.i.ActiveDirectoryUsersFetcher| Search Reference returned : 4
