Setup SAML SSO with ADFS and Slack via Proxy
Use the following procedure to configure Single Sign-On using ADFS for Slack and Skyhigh CASB via SAML proxy connection.
Slack provides an Assertion Consumer Services (ACS) in the SAML request to identify the provider with a SAML proxy for both the SAML request from Slack and the SAML assertion from ADFS.
Prerequisites
Make sure you have the following before setup with ADFS and Slack:
- Access to Slack Enterprise account.
- Access to Skyhigh CASB
- Enable Skyhigh CASB proxy for Slack service.
- Functioning ADFS server to reach over the Internet with a valid SSL certificate and DNS resolvable hostname.
- Single Sign-On working setup without Skyhigh CASB proxy (Slack and ADFS direct SSO).
Step 1: Configure Slack Proxy in Skyhigh CASB
NOTE: Slack doesn't require the SP certificate, so you can fake the SP certificate using the IDP certificate.
- Login to Skyhigh CASB.
- Go to Settings > Service Management.
- Click Add Service Instance.
- Click Slack, and enter an Instance Name.
- Click Done.
- Select your Slack instance from the Services list. (If no services are listed, contact Skyhigh Security Support for help.)
- Click the Setup tab, and under Proxy, click Get Started.
- Under Configure Proxy, click Configure.
- For Select Proxy Location, select Skyhigh CASB. Click Next.
- Configure the proxy domain as shown:
- Host Name: Enter a name and make sure to use the enterprise domain.
- Proxy Domain: Select the required option.
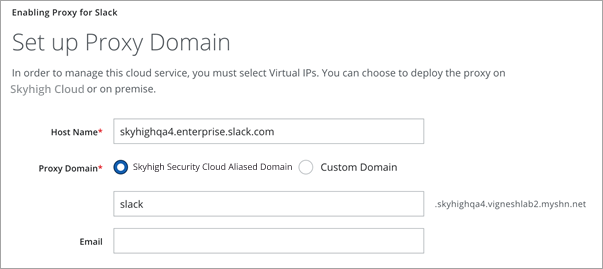
- Click Done.
- Under Setup SAML, click Configure.
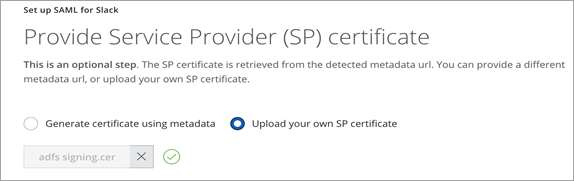
- Upload the IDP Certificate in both the IdP and SP Certificate fields and save SAML Settings.
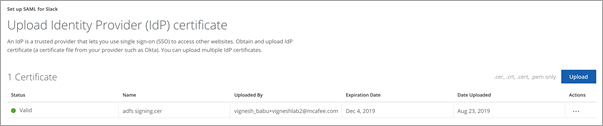
- Export the proxy certificate to use in the Slack enterprise account.
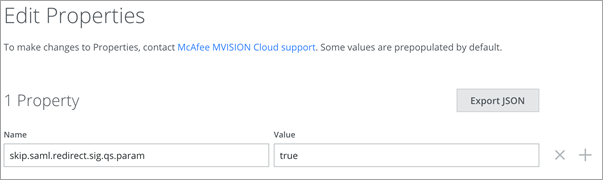
- Add the proxy property skip.saml.redirect.sig.qs.param to true.
Step 2: Configure ADFS
- Open the relying party trust properties configured for Slack.
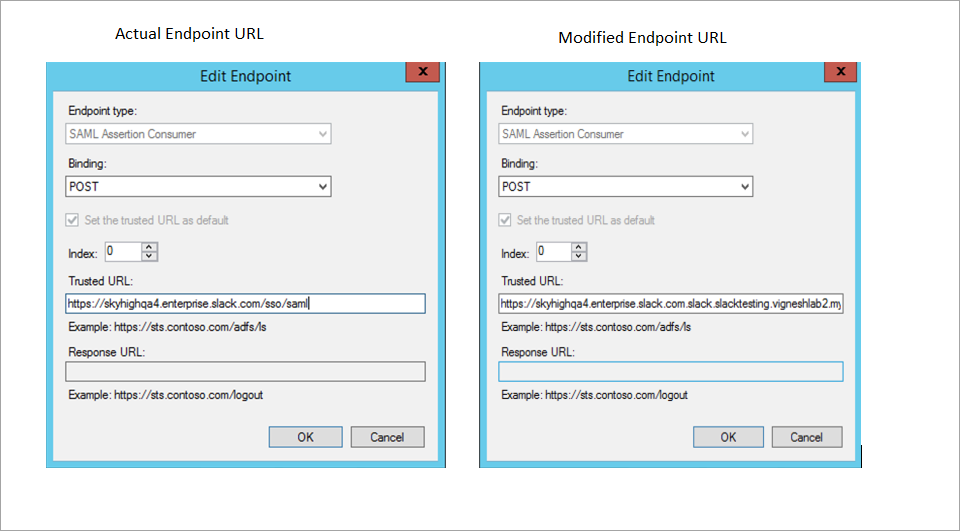
- Replace the actual endpoint URL with modified proxy URL:
- Actual endpoint URL: https://skyhighqa4.enterprise.slack.com/sso/saml
- Modified endpoint URL: https://skyhighqa4.enterprise.slack.com.slack.slacktesting.vigneshlab2.myshn.net/sso/saml?shnsaml
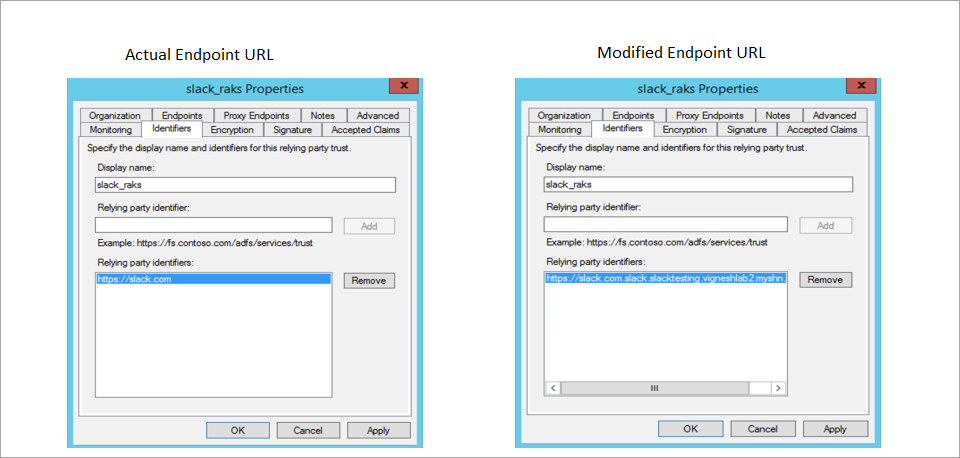
- Replace actual identifier value with the modified proxy URL:
- Actual identifier value: https://slack.com
- Modified identifier value: https://slack.com.slack.slacktesting.vigneshlab2.myshn.net
Step 3: Configure Slack SSO for Skyhigh CASB SAML Proxy
- Login to your Slack Enterprise account and select Manage Organization Setting.
- Go to Security > SSO Configuration and you are redirected to Change SSO Configuration page.
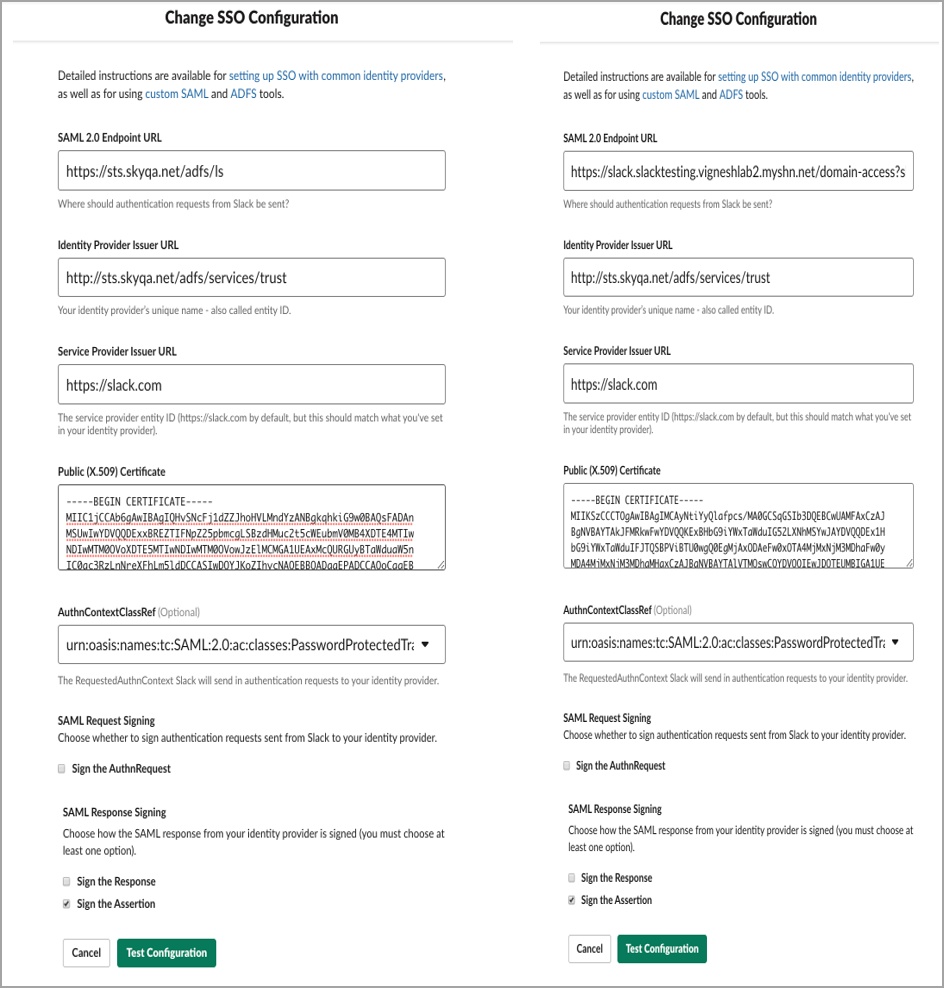
- Replace the ADFS signing certificate with an Skyhigh CASB proxy certificate. Replace as follows:
- The Original SAML 2.0 endpoint URL: https://sts.skyqa.net/adfs/ls
- Skyhigh CASB proxy domain alias: slack.slacktesting.vigneshlab2.myshn.net
- Modified / New SAML 2.0 endpoint URL: https://slack.slacktesting.vigneshlab2.myshn.net/domain-access?shnsaml-request=https%3A%2F%2Fsts.skyqa.net%2Fadfs%2Fl
- Click Test Configuration to authenticate the ADFS.
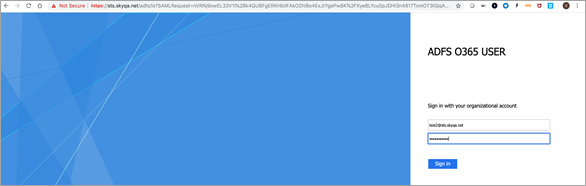
- Once the test mode is successfully updated, click Confirm Update.
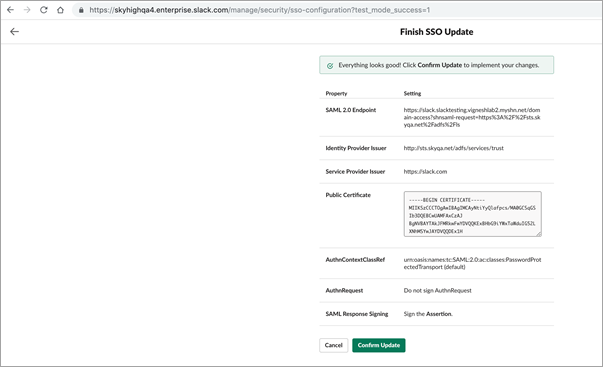
NOTE: When you logged into Slack Service, if you see a blank page instead of Slack Home page then you need to configure the following on Slack SSO:
- Under SAML Response Signing, select the Assertion Signed.
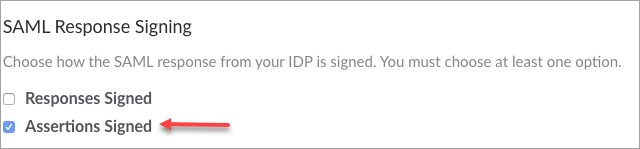
- Save your configuration.
