Configure Workday for Okta (IdP) Passthrough Method
This configuration is for the Okta passthrough method.
Configure Okta IdP
- Login into Okta and go to Admin > Add Application > Create New App.
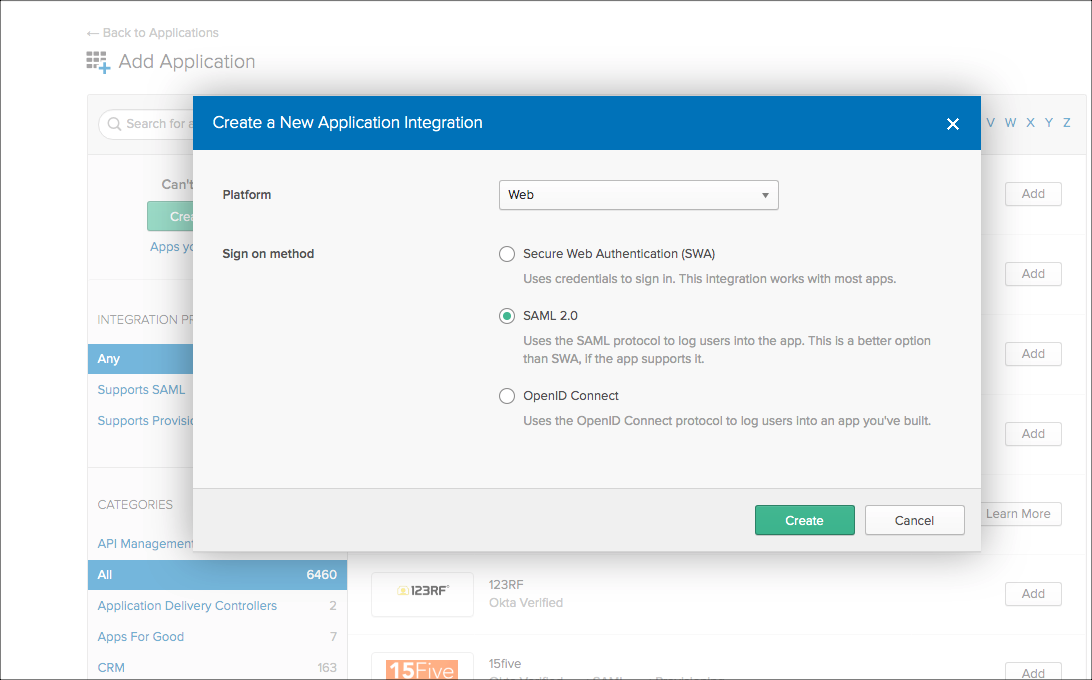
- Configure the ACS URL to end with &shnsaml or ?shnsaml, as shown.
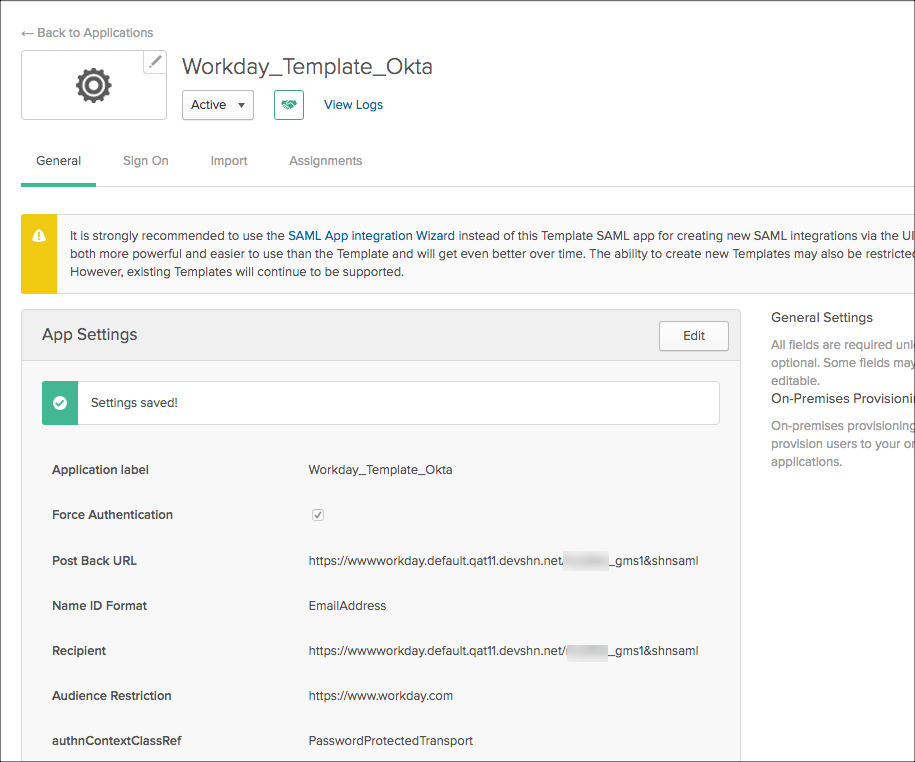
- Download the Okta certificate (IdP certificate) from the IdP metadata.
- Assign users to the application you added.
Configure the Skyhigh CASB Tenant for SAML
- Log into Skyhigh CASB.
- Go to Service Management > Workday instance.
- In the Proxy section, go to SAML certificates. Upload the Okta certificate under IDP, and upload the Workday certificate under SP.
- Download the proxy certificate.
Configure Workday for SAML
- Login to the Workday instance admin console.
- Search for Edit Tenant Setup - Security.
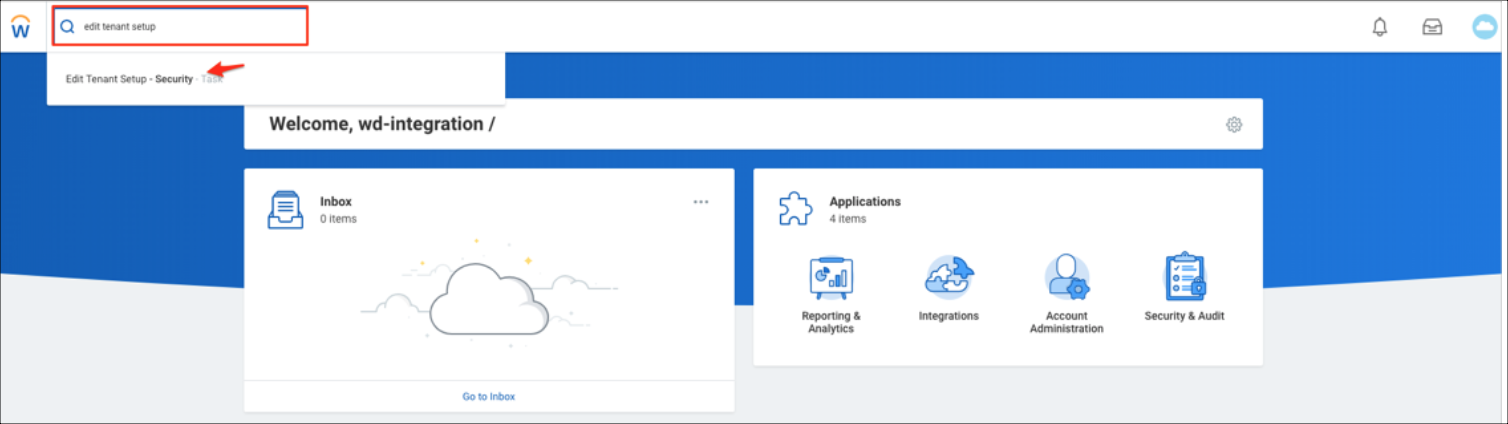
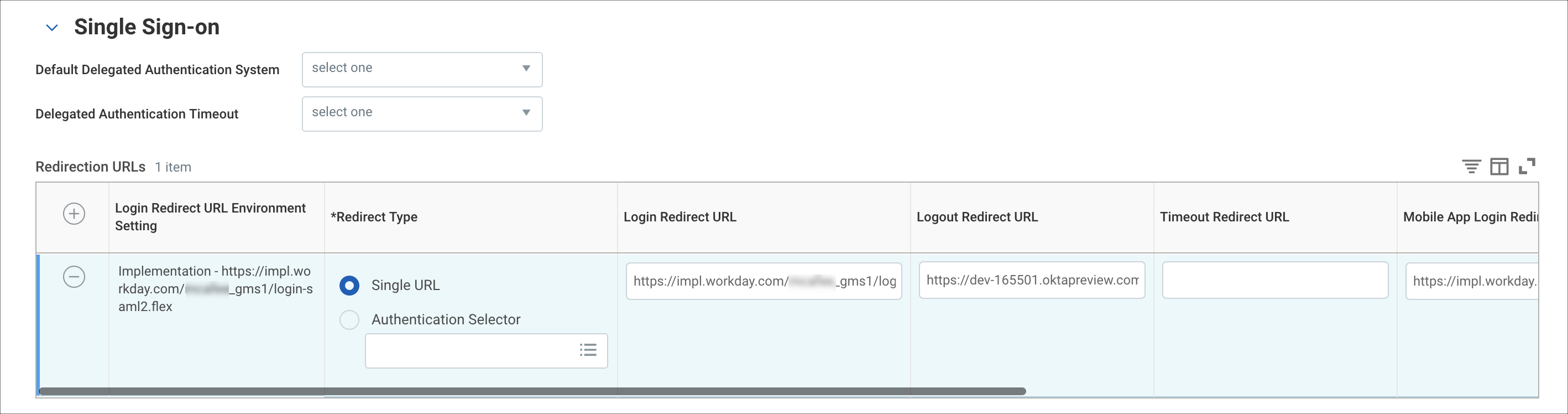
- Go to Single Sign-On. Click +, then enter the following:
- Login Redirect URL. For example: https://impl.workday.com/<instance_name>/login-saml2.flex
- Mobile App Login Redirect URL. For example: https://impl.workday.com
- Mobile Browser Login Redirect URL. For example: https://impl.workday.com/<instance_name>/login-saml2.flex
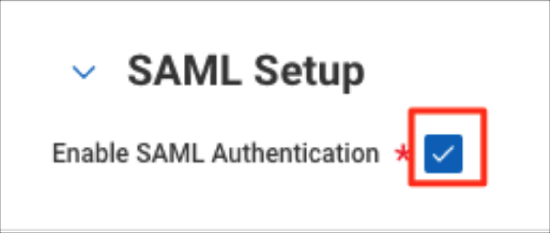
- Under SAML Setup, enable SAML Authentication.
- Under SAML Identity Providers, click +, then enter the following:
- Identity Provider Name. Name for reference. For example, OKTA.
- Issuer. Identity Provider Entity ID. For example, exkjrv6a79B3N9CdK0h7)
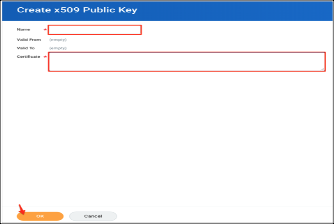
- X509 Certificate. In the Create x509 Public Key screen, enter a unique name for your certificate. For example, proxy.cert. Then click OK.
- Service Provider ID. Service Provider Entity ID, according to the Workday document here: http://www.workday.com
- Select the checkbox Enable SP initiated SAML Authentication.
- IdP SSO Service URL. Add Identity Provider SSO URL (for example, https://dev-165501.oktapreview.com/app/workday/exkjrv6a79B3N9CdK0h7/sso/saml)
- Enable Do Not Deflate SP-initiated Authentication Request.
- Authentication Request Signature Method. Select SHA1.
- Select the checkbox Enable Signature KeyInfo Validation.
For SP initiated access: https://impl.workday.com/<instance_name>/login-saml2.flex
For IDP initiated access: https://dev-165501.oktapreview.com/app/workday/exkjrv6a79B3N9CdK0h7/sso/saml
Access the Workday Native App
The Workday native app is actually an embedded browser.
- To access the Workday native app, provide the instance name as you configured the mobile app login URL: https://impl.workday.com.
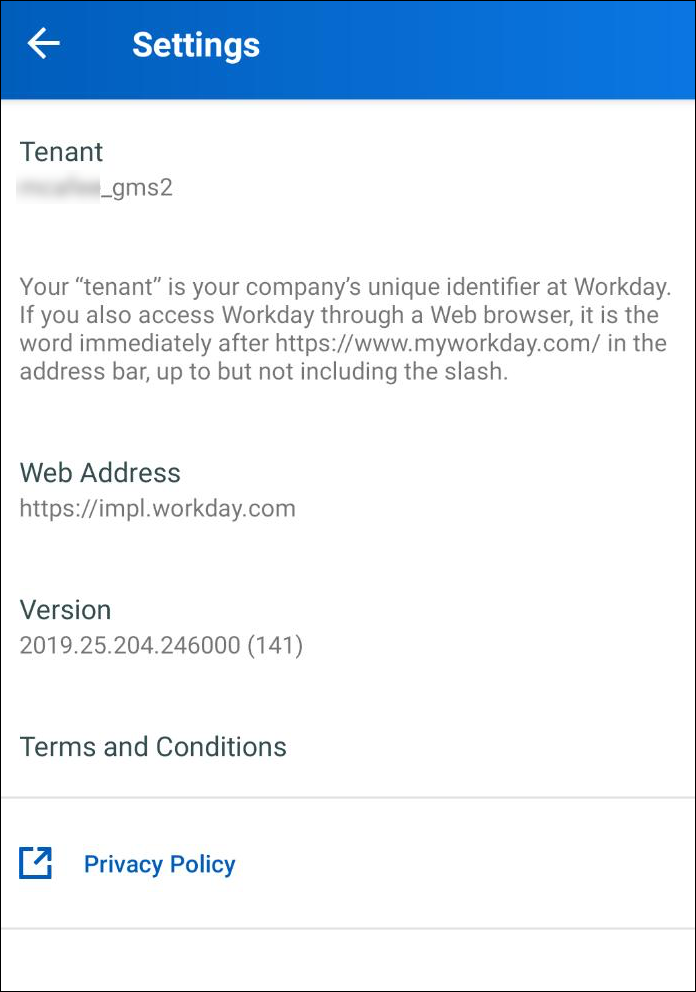
- By default, the native app appends the instance name to the direct URL. For example, https://impl.workday.com/<instance_name> eventually landing to OKTA login page.
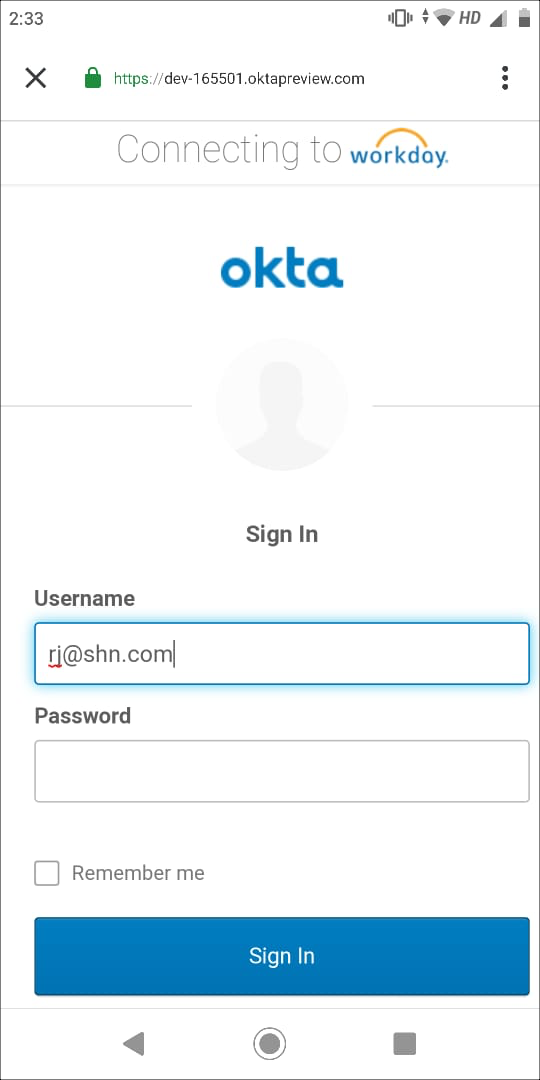
- After the Okta IdP login, the IdP will redirect to the proxy URL for a proxy session.
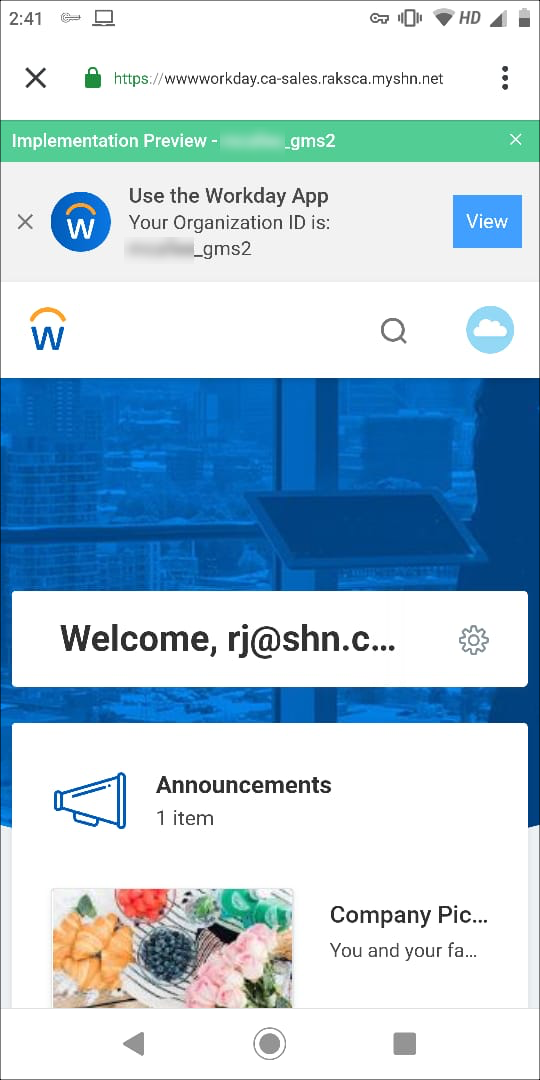
Notes
All of the above is accessed via the embedded browser of the Workday native app and is purely the behavior of the app. So configuring the following will not work:
- Cloud Access Policy with Device Type as Native App for Workday will not work and should be considered as iOS or Android, as the proxy session activity uses the browser.
- Clicking the app view in the image above would crash and close the app, as Workday doesn't take any URL apart from the direct Workday URL. For example, https://impl.workday.com or www.myworkday.com.
Known Issue: After configuring the Workday Mobile app and when the proxy is configured, when you access Workday, it accesses Workday only via the combined browser of the native app and not via the Workday mobile app itself.
