Export Threats to a CSV File
The data contained in many areas of Threat Protection can be exported as a Comma Separated Value (CSV) file, suitable for importing into a third-party software security system or opening in a spreadsheet program. The data in the spreadsheet may provide greater detail than what is displayed in the Skyhigh CASB UI.
The following tables can be exported in CSV format:
- Threat Table List
- Activities page
Download the CSV File in Threat Table
Go to Incidents > Threats and select the required threat to download the CSV file from the table. Under Actions, click Download CSV. The CSV file downloads automatically.
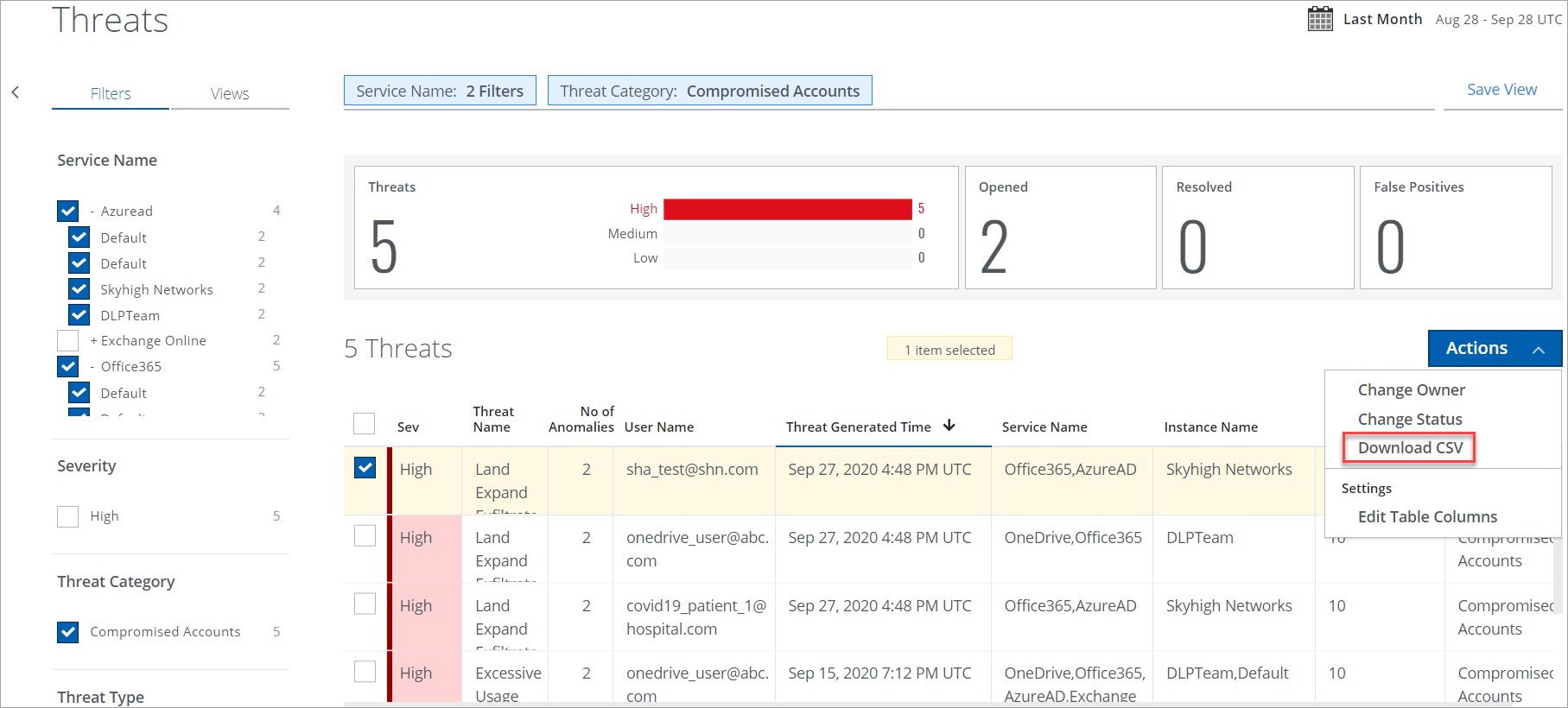
NOTE: Under Settings > Edit Table Columns, you can customize the table columns and set the required table column in the Threats table. For details, see Edit Table Columns.
CSV Columns in Threats
The following information is captured in the CSV file. The data available depends on the exported page.
| Column Name | Description | Available Options |
|---|---|---|
| Comments | Any additional comments with the threat. | |
| Device ID | The identification number of the device where the threat occurred. | |
| Device IP | The IP address of the device where the threat occurred. | |
| Device Managed | A True/False flag that checks if the activity interacted with a device is managed or unmanaged. |
|
| Device Type | The type of device used to generate the activity. |
|
| Instance Name | The instance where the threat occurred. | |
| No of Anomalies | The number of anomalies in the threat. | |
| Owner | The name of the owner who is assigned to the threat. | |
| Risk Score | The risk score of the event based on severity. | |
| Service Name | The service where the event occurred. | |
| Severity | The risk posted by the event ranked based on severity. |
|
| Threat Category | The upper-level category of the threat. | |
| Threat Generated Time | The timestamp for when the threat was processed by Threat Protection. | |
| Threat ID | The identification number of the threat. | |
| Threat Name | The specific name of the threat. | |
| Threat Significant Updated Time | The updated time of the threat to Skyhigh CASB. | |
| Threat Status | The status of the threat. |
|
| Threat Updated Time | The timestamp for when the threat was processed by Threat Protection. | |
| User Agent | The web browser where the threat generated. |
|
| User Name | The user who triggered the anomaly or threat. |
Download the CSV File in Activity Table
Go to Incidents > User Activity > Activities . The following information is captured in the CSV file. The data available depends on the exported page.
CSV Columns in Activity Table
The following information is captured in the CSV file. The data available depends on the exported page.
| Column Name | Description | Available Options |
|---|---|---|
| Users Tab | ||
| Activities | The number of activities. | |
| Anomalies | The number of anomalies. | |
| Profile | This information is pulled from user profile information stored in the cloud service. | |
| Role | This information is pulled from user profile information stored in the cloud service. | |
| Service Identifier | Skyhigh CASB's internal mapping ID for the cloud service. | |
| Service Name | The service where the event occurred. | |
| Sub - Service Name | This is used for O365 services, which have the Service Name of O365 and a sub-service of OneDrive or Sharepoint. | |
| Threats | The number of threats. | |
| User | The user who triggered the anomaly, threat, or activity. | |
| Anomalies Tab | ||
| Activity Count | The number of activities performed. | |
| Activity Name | The specific name of more than 100 possible activities performed. | |
| Anomaly | The specific name of the anomaly. | |
| Anomaly Category | The top-level category for the anomaly. | |
| Anomaly Cause | The cause of the anomaly. | |
| Anomaly Created Time | The time that the anomaly was detected and processed by Threat Protection. | |
| Anomaly Threshold | The numeric value of the anomaly threshold at the time of the anomaly. | |
| Anomaly Updated Time | The time that the anomaly was detected and processed. | |
| Incident ID | The identification number of anomaly generated Incident. | |
| Instance | The instance where the anomaly occurred. | |
| Search Key | Skyhigh CASB's internal key to look up the info indices where keys are stored. | |
| Service Name | The service where the anomaly occurred. | |
| Severity | The risk posted by the event ranked based on severity. |
|
| Threshold Duration | The period of time where the threshold evaluated to determine if an anomaly has occurred. |
|
| Source City | The name of the city, where the anomaly occurred. | |
| Source Country | The name of the country, where the anomaly occurred. | |
| Source IP | The IP address where the anomaly occurred. | |
| Source Latitude | Map coordinate of the origin of the activity, based on the IP address. | |
| Source Longitude | Map coordinate of the origin of the activity, based on the IP address. | |
| Source Network Type | The network type where the anomaly occurred. | |
| Source Organization | The name of the organization, where the anomaly occurred. | |
| Source Proxy Type | The proxy where the anomaly occurred. | |
| Source Region | The name of the region, where the anomaly occurred. | |
| Source Timestamp | The original timestamp of when the event occurred. | |
| Sub - Service Name | This is used for O365 services, which have the Service Name of O365 and a sub-service of OneDrive or Sharepoint. | |
| User | The name of the user who triggered the anomaly. | |
| Activities Tab | ||
| Account ID | The identification number of the account. | |
| Action ID | The identification number of the action. | |
| Activity Identifier | An internal ID that maps the activity type to Skyhigh CASB's internal database. | |
| Activity Name | The specific name of more than 100 possible activities performed. | |
| Activity Processed Time | The event processed time by Threat Protection. | |
| Activity Timestamp | The original timestamp of when the activity occurred. | |
| Activity Trust | A True/False flag that checks if the activity is trusted. |
|
| ASN | The unique identifier number to identify the network. | |
| ASN Name | The name of the Autonomous system. | |
| City | City of origin for the activity, based on the IP address. | |
| Country | Country of origin for the activity, based on the IP address. | |
| CSP ID | The identification number of CSPs. | |
| Device ID | The identification of the device where the activity occurred. | |
| Device Managed | A True/False flag indicates if the activity interacted with a device is managed or unmanaged. |
|
| Device Type | The type of device used to generate the activity. |
|
| Directory | A True/False flag that checks if the activity interacted with a folder. |
|
| Domain | The collaboration group, based on the user's email address. | |
| File/Folder Path | If available, the location of the file or report associated with the activity. | |
| File Owner | The owner of the file. | |
| File/Report Name | The file/report name where the activity occurred. | |
| File Size | The size of the file where the activity performed. | |
| File Type | The type of file where the activity performed. | |
| Instance | The instance where the activity occurred. | |
| IP Organization | The IP address of the organization where the activity occurred. | |
| Last Modified | If any modified file for the current activity | |
| Network Type | The type of network where the proxy occurred. | |
| Number of Events | The number of events occurred in the activity. | |
| Operation | The parameter for the activity. | |
| Operating System (OS) | The operating system used to generate the activity. |
|
| Other Info | Reserved for future functionality. | |
| Parent Service Name | The name of the parent service. | |
| Profile | This information is pulled from activity profile information stored in the cloud service. | |
| Proxy Description | The description of the proxy. | |
| Proxy Type | The type of proxy where the activity occurred. | |
| Region | The name of the region, where the activity occurred. | |
| Report Details | The detailed report of the activity. | |
| Role | This information is pulled from activity profile information stored in the cloud service. | |
| Sharing Enabled | Reserved for future functionality. | False |
| Site URL | The URL of the site where the activity occurred. | |
| Source IP | The IP address where the activity occurred. | |
| Sub-Service Name | This is used for O365 services, which have the Service Name of O365 and a sub-service of OneDrive or Sharepoint. | |
| Target ID | An internal identifier for the file or folder involved in the activity. | |
| Trust For | The activity is trusted for tenants or organizations. | |
| Trust Reason | The reason for the trust. | |
| URL | The file path, used in Skyhigh CASB for cloud service activity. | |
| User Agent | The web browser used to generate the activity. |
|
| User Name | The user who triggered the anomaly, threat, or activity. | |
