About Vulnerable Storage
In Skyhigh CASB, the Analytics > Vulnerable Storage page allows you to identify vulnerable S3 buckets and perform Closed Loop Remediation (CLR) on them to make sure they are secured.
Amazon Web Services (AWS) S3 buckets are used for storage by many third-party applications. AWS uses a shared security responsibility model for S3 buckets, meaning that you as a customer are responsible your own S3 bucket configuration. Skyhigh Security Skyhigh CASB has identified a vulnerability called GhostWriter in misconfigured S3 buckets that incorrectly allow public read and write access to data. If an S3 bucket has inappropriate permissions and allows public write access, a third party can use it to inject malicious code. For complete details, see Skyhigh CASB Discovers GhostWriter: MITM Exposure In Cloud Storage Services.
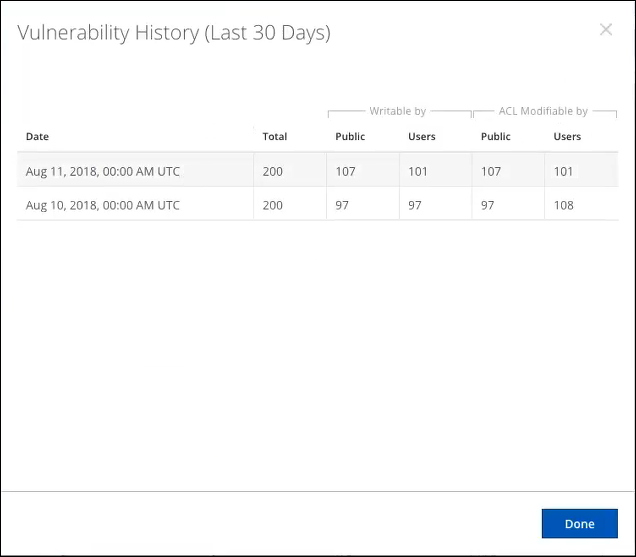
Using Shadow IT logs, Skyhigh CASB identifies unique S3 buckets by virtual-hosted–style and path-style URLs. Once this list is generated, an out-of-band process scans the buckets for vulnerabilities, which occurs every 24 hours. The scan includes S3 buckets accessed in the last 30 days (shown in the Vulnerability History dialog).
NOTE: For information about how to view the status of your S3 buckets, see Identifying Public Buckets Using Bucket Permissions Check.
NOTE: If no vulnerable S3 buckets are discovered, the following message is displayed, "No vulnerable storage resources were discovered. View more information to verify the configuration."
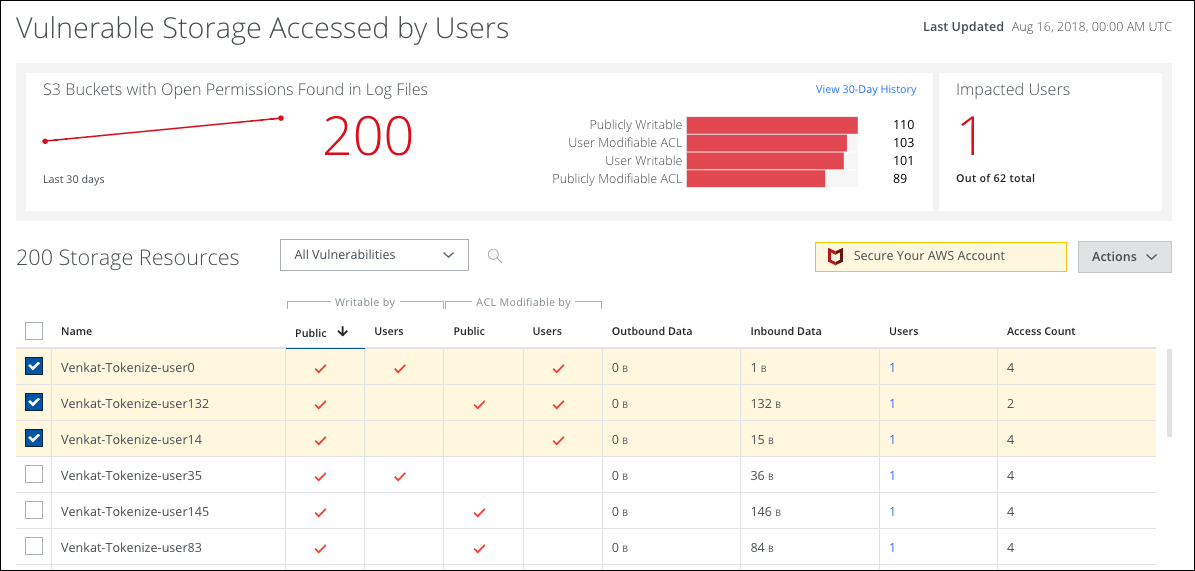
The Vulnerable Storage page provides the following information and actions:
- S3 Buckets with Open Permissions Found in Log Files. Displays the number of S3 buckets with open permissions found in log files for the last 30 days.
- View 30-Day History. Click to view a 30-day history of the number of Publicly Writable, User Writable, User Modifiable ACL, or Publicly Modifiable ACL S3 buckets.
- Impacted Users. The number of impacted users out of the total users.
- All Vulnerabilities. Select to display all vulnerabilities, or to display S3 buckets by vulnerability: Publicly Writable, User Writable, User Modifiable ACL, or Publicly Modifiable ACL.
- Actions.
- Download CSV. Download a CSV file containing the URLs for selected S3 buckets.
- Edit Table Columns. Allows you to show or hide table columns to customize your view.
- Select. Click to select the S3 bucket.
- Name. The name of the S3 bucket.
- Writable by. Checkmarks display whether an S3 bucket is Publicly Writable or User Writable.
- ACL Modifiable by. Checkmarks display whether an S3 bucket is User Modifiable ACL or Publicly Modifiable.
- Outbound Data. Displays outbound data for the S3 bucket.
- Inbound Data. Displays inbound data for the S3 bucket.
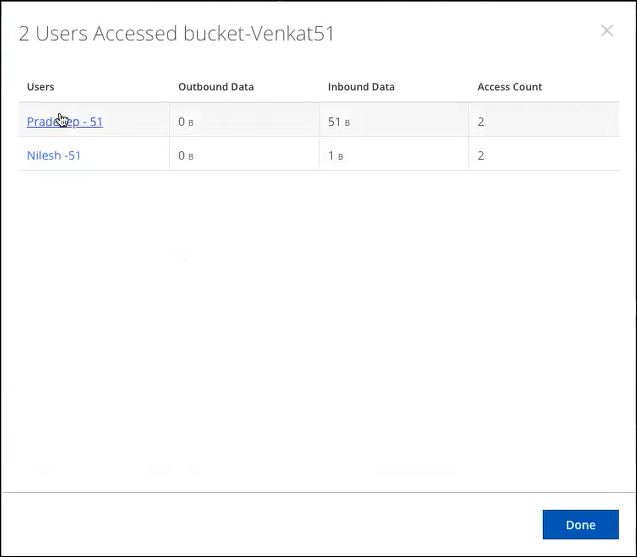
- Users. Displays the number of users associated with the S3 bucket. Click to display a dialog of all users who have accessed this S3 bucket.
- Access Count. Displays how many times that bucket has been accessed.
