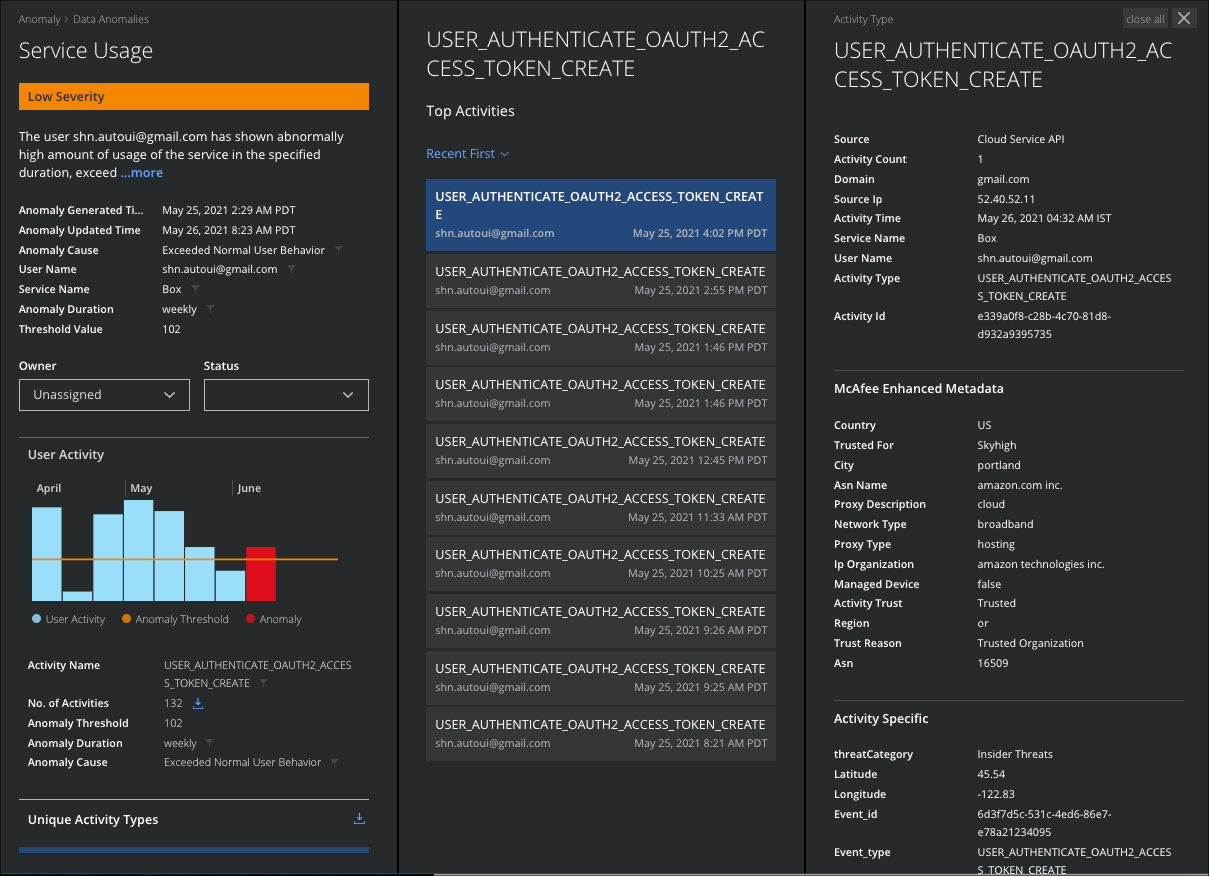
Anomaly Cloud Card
The Anomaly Cloud Card provides specific information on a selected anomaly, including information on how the anomaly was determined.
The Cloud Card may contain additional information on the anomaly, depending on the anomaly type. This information can further assist your investigation of the anomaly.
Click any anomaly in the Anomalies table to see the Cloud Card for the specific anomaly, including information on how the anomalies were determined.
Anomaly Cloud Card provides the following information:
- Anomaly Category. The top-level category for the anomaly. This can be used to better understand what sort of anomaly you are looking at and why it may represent a risk to your cloud services.
- Severity. The value (on a Low/Medium/High scale) of by how much the anomaly exceeds the threshold for the action.
- Anomaly Name. The specific name of the anomaly.
- Description. A paragraph describes, what the current anomaly is and how it was generated, based on Skyhigh CASB's definitions of the anomaly. You can use this information to better understand what the anomaly represents and why it may indicate a risk to your data security.
- Anomaly Generated Time. The recorded time when the anomaly occurred. (This is dynamically adjusted to the local time zone of your computer.)
- Anomaly Updated Time. The recorded time when the anomaly occurred and updated in Skyhigh CASB.
- Anomaly Cause. The reason for which the anomaly occurred.
- User Name. The name of the user who triggered the anomaly. Knowing which user is connected to the anomaly will assist your investigation in order to find out the circumstances of the anomalous behavior directly.
- Service Name. The Cloud Service where the anomaly occurred.
- Threshold Duration. The period during which the threshold is exceeded to count as an anomaly. Knowing when and for how long the anomaly occurred can assist in building a timeline for your investigation.
- User. Click to see User Details Cloud Card.
- Owner. Select to assign an owner.
- Status. Select the status of the anomaly.
- Archived. The anomaly has been archived and removed from the table. (Archived anomaly does not appear in table results unless you explicitly filter for them in the Omnibar.)
- False Positive. Select to mark an anomaly as false positive.
- Opened. An anomaly is marked opened when it is resolved and found again as an anomaly to Skyhigh CASB.
- New. The anomaly has not yet been acted on.
- Resolved. Select to resolve an anomaly.
- Suppressed. Select to suppress the anomaly that is a duplicate of a previously generated anomaly.
- MITRE. Click Full View to view the detected tactics and techniques associated with this anomaly on the MITRE dashboard.
- User Activity. You can either view a geography-based anomaly or a threshold-based anomaly based on the type of anomaly. For details, see the Anomalies User Activity section.
- Activity. Click the Download icon to download the various activities associated with this anomaly in the CSV file.
- Notes. Enter a note for the anomaly and click Add. Each note added is visible separately below the Notes field. For notes that you have added, you can Edit or Delete them. For notes written by other users, you may only view them. The default limitation is 10 notes per incident, and 300 characters per note. To use the Incident Notes feature, you must use your own Data Storage. You cannot use Skyhigh CASB Data Storage. For details on configuration, see Data Storage.
Anomalies User Activity
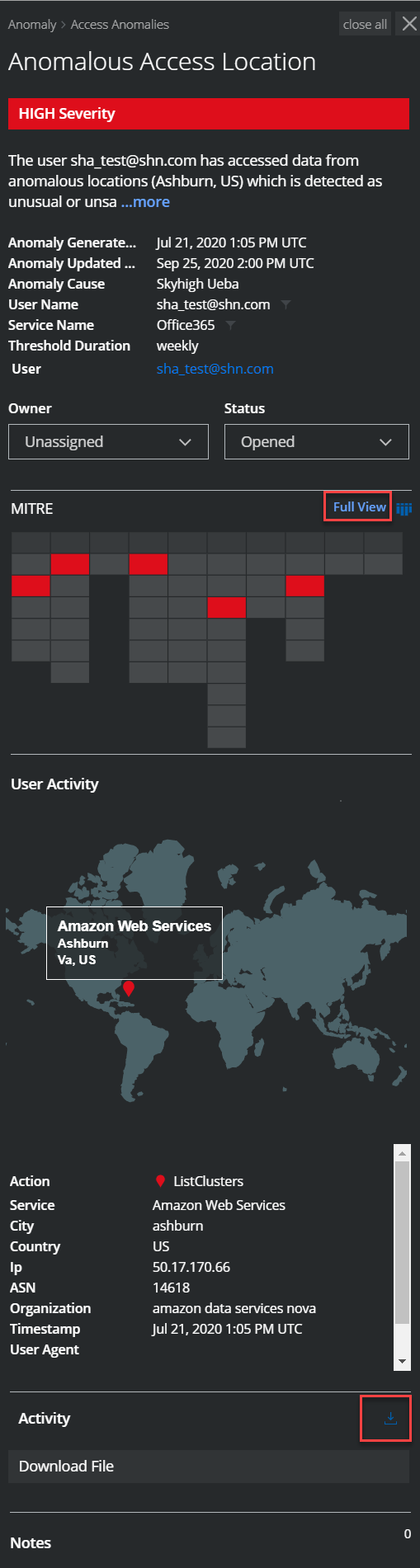
Geography-Based Anomaly
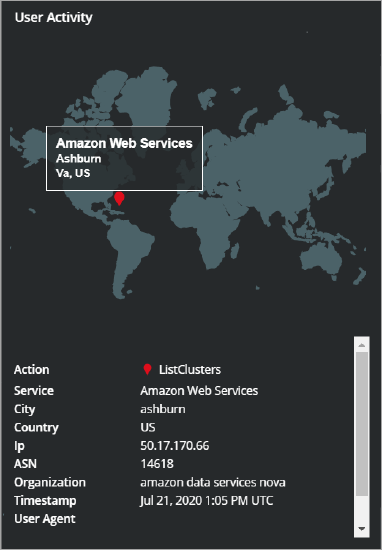
Displays a geographical map showing the anomalous locations. You can view the threat activity within your organization, you are provided with the login activity details. It can be used to monitor the activity of the users within your organization and detect risk activity trends for the entire organization over time.
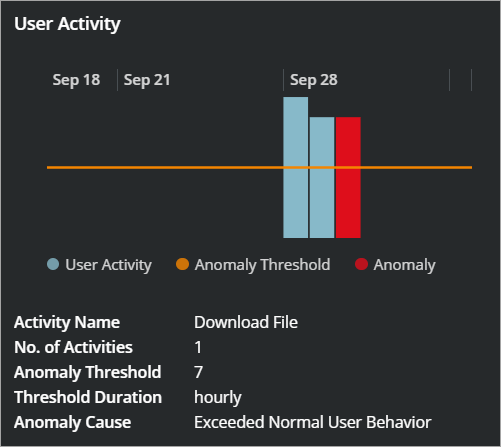
Threshold-Based Anomaly
Anomaly thresholds are the foundation of the Skyhigh CASB Threat Protection platform. Understanding what the threshold was at the time of the anomaly is useful for determining the validity of an anomaly and can be used to identify a false positive. It displays a chart that shows the threshold and by how much the activity exceeded the threshold. This can be used to estimate the severity of an anomaly; an anomaly that significantly exceeds the threshold may incident a larger security risk than an anomaly that just slightly crosses the threshold.
NOTE: In cases where the activity processing is delayed by more than an hour, the anomaly chart is unable to display.
The Threshold graph displays activity by date, with each vertical segment representing a day.
- Blue bars represent user data that does not represent an anomaly.
- Red bars represent user data that has exceeded the current threshold.
- The orange line represents the current thresholds. Any activity that exceeds the thresholds is registered as an anomaly.
The Threshold-based anomaly displays the following information:
- Activity Name. The specific name of more than 100 possible activities performed. Understanding which type of activity is monitored will aid in tracing back the action that triggered the anomaly during your investigation.
- No. of Activities. How many times during this period the activity occurred. Knowing how many activities contributed to the anomaly may help determine if this was a continued pattern of attack or a single event.
- Anomaly Threshold. The line at which the activity is considered an anomaly. Knowing how the anomaly was determined and to what extent the threshold was exceeded can aid your investigation.
- Threshold Duration. The period during which the threshold is exceeded to count as an anomaly. Knowing when and for how long the anomaly occurred can assist in building a timeline for your investigation.
- Anomaly Cause. The reason for the anomaly.
Anomalies to Activity Cloud Card
Under Unique Activity Types, you can click to display details on Top Activities, then click an item in the list to drill down into specific user activities. This allows you to drill down to specific activities that led to an anomaly.