Monitor User Activities for Shadow Cloud Services
Skyhigh CASB provides you visibility into a user's download, login, and upload activities on any shadow cloud service in the cloud registry. You can monitor user activities for shadow cloud services and view the activity details associated with a user based on the selected activity type on the Activities page. You can use activity monitoring to protect your users from risky activity trends.
NOTE: Users with Secure Web Gateway Cloud license can access this feature in the Skyhigh CASB dashboard.
About Activity Monitoring
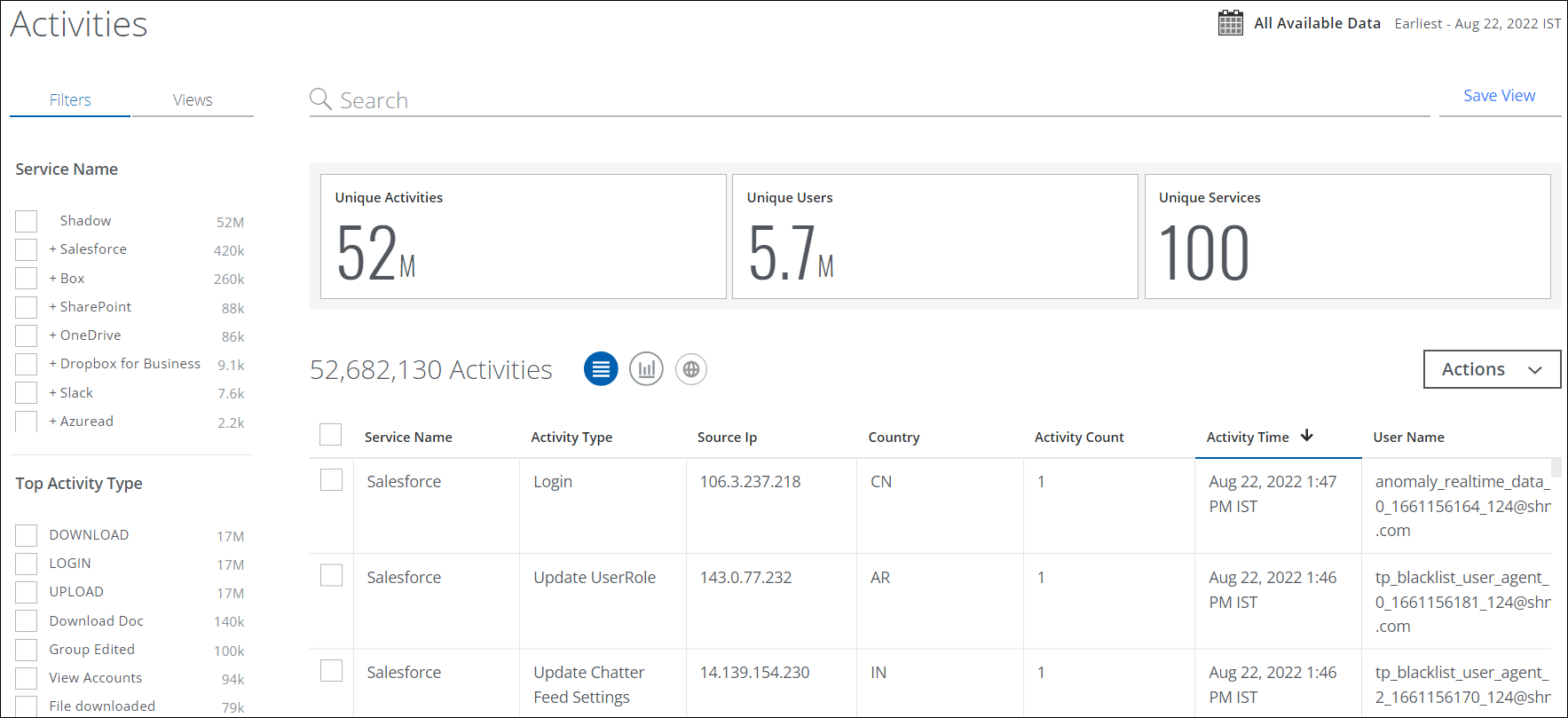
The Activities page allows you to monitor a user's login, upload and download activities across all shadow cloud services. You can monitor how users within your organization use cloud services over time to detect risk activity trends for the entire organization. For details on Activities page, see About Activities.
Find the page at Incidents > User Activity > Activities.
You can monitor user activities for shadow cloud services based on the filters defined in the Activities page.
Monitor User Activities
To monitor user activities for shadow cloud services:
- Log in to Skyhigh CASB.
- Go to Incidents > User Activity > Activities.
- On the Activities page, use the Filters tab to filter for user activities based on the selected shadow cloud services.

- From the Service Name filter, select the shadow cloud services.
- From the Top Activity Type filter, select any of the following user activities:
- Download
- Login
- Upload
NOTE: You can use additional filters or select the options on the Filters tab to narrow the scope of your search.
The Activities page displays the count of user activities, users and shadow cloud services along with the user activity details for each user activity.
Activity Control
After you use activity monitoring to detect risky activity trends, you can use activity control to restrict specific user activities for shadow cloud services. You can configure your web policy to block user activities based on service groups, service categories, and individual services. For details, see About Activity Control.
