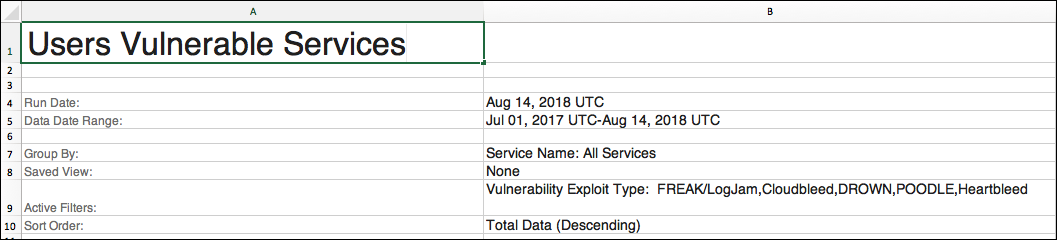
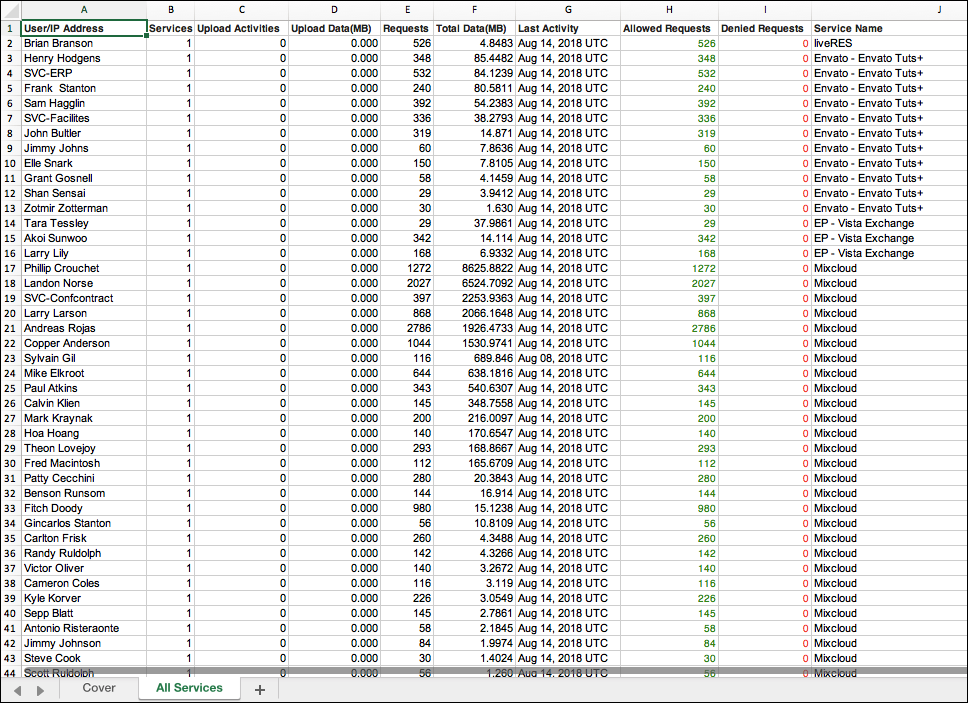
Report - Users Exposed to Vulnerable Services
This report lists users who have been exposed to vulnerable services.
- On the Users page, search for Vulnerability Exploit Type - Registry Attribute, and add all of the attribute values: Cloudbleed, DROWN, Freak/Logjam, Heartbleed, and POODLE.
- Select Create Report > Schedule.
- Report Name. Enter a unique name for your report.
- File Format. Select XLSX or CSV. (Group by All Services is not supported for PDF reports.)
- Group By. Select Group by > Service Name. Then select All Services.
- For Frequency, select:
- Run Now. The report will run immediately and then appear in the Report Manager.
- Schedule. Schedule a report to run at a later time, which then appears in the Report Manager.
- Recipients. Enter the email addresses of anyone to which you would like to automatically email the report. Separate email addresses with commas.
- Share report with other users within your Skyhigh CASB account. Select this option to make the report public within your organization.
- Click Schedule.
The report is emailed to you in the format that you selected.