Deployment Model Best Practices
Figure 5 depicts guidance on which deployment models are aligned to managed and unmanaged devices:
- Managed Devices to Sanctioned SaaS. Since corporate data is permitted to exist on both the sanctioned SaaS and the managed endpoint, there is no need to intercept communications between them. Skyhigh CASB protects data while it is in the cloud, while the endpoint security protects the device. Once authenticated to the cloud service, the Reverse Proxy will redirect the client to connect to the SaaS directly.
- Managed Devices to Unsanctioned SaaS. Here, corporate data is allowed on the managed devices, but not in the unsanctioned SaaS. To prevent exfiltration, controls must be put in place to prevent the transfer of data to the unsanctioned SaaS. Augmented by Skyhigh CASB’s Shadow IT registry and service groups, existing forward proxies and Secure Web Gateways are well equipped for this task.
- Unmanaged Devices to Sanctioned SaaS. In this case, corporate data can be in the sanctioned SaaS but not necessarily on the unmanaged device. Without an endpoint agent, there is no way to protect data that might be downloaded to this device. The reverse proxy is the best approach to ensuring that data is not placed at risk on these devices.
- Unmanaged Devices to Unsanctioned SaaS. Since neither the endpoint nor the cloud service provider is owned by the company, this combination should generally be considered out of scope. Placing protections here would be tantamount to spying on employees’ personal activities on personal devices, particularly when on private Internet connections.
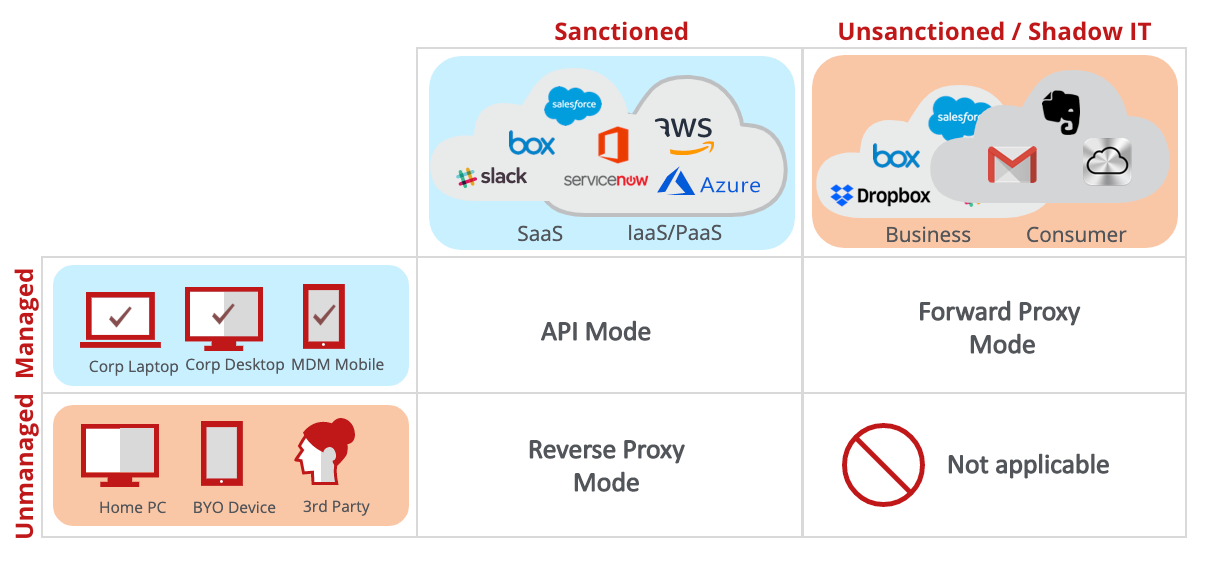
Figure 5 – Guidance on CASB Deployment Modes
