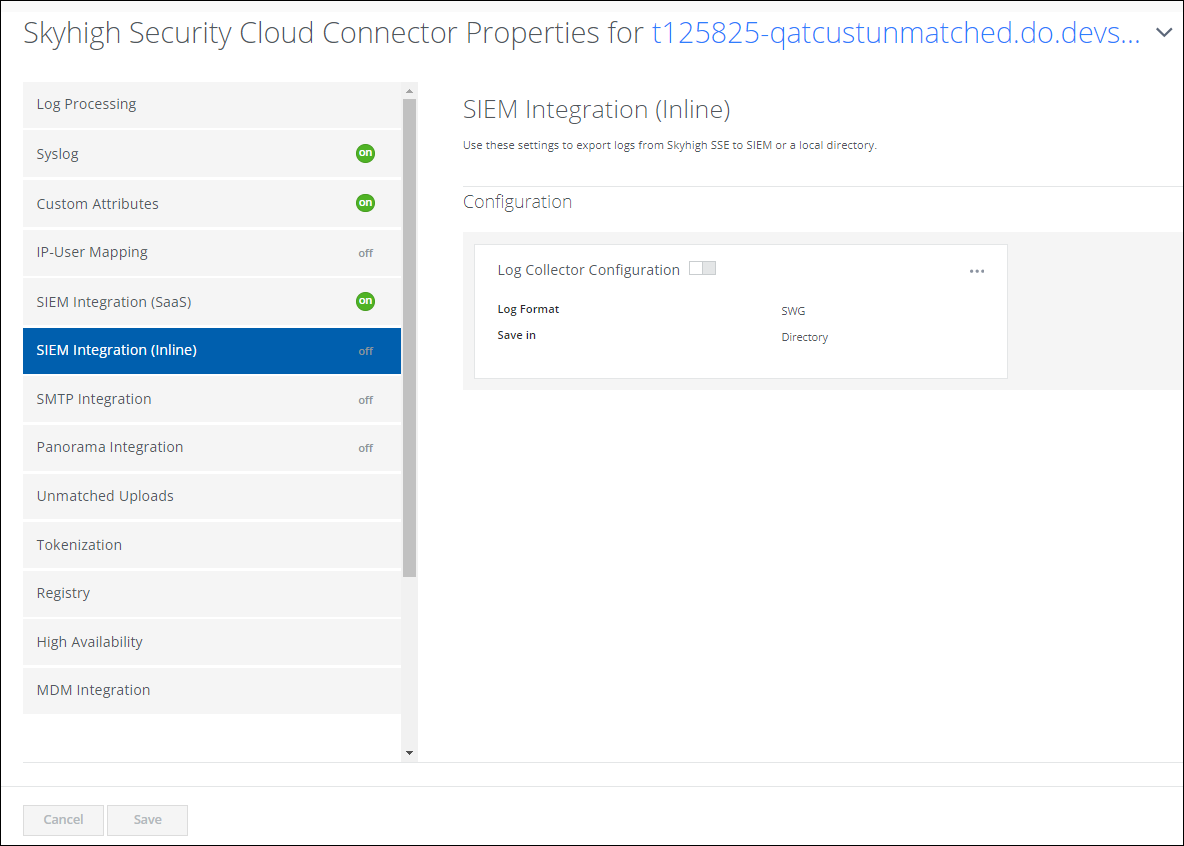
SIEM Integration (Inline)
Use SIEM Integration (Inline) to export Security Service Edge (SSE) web access data to your third-party SIEM systems (Security Information and Event Management). The SSE web access data contain the logs originating from Secure Web Gateway (SWG), Remote Browser Isolation (RBI), Private Access, and Cloud Firewall.
Use SIEM Integration (SaaS) to export Anomalies, Threats, Incidents, and Audit Logs to your third-party SIEM systems.
Before you Begin
Make sure the following prerequisites are met:
- Download and install Cloud Connector version 6.7.1 or above. To download the latest version of the Cloud Connector, see Download Skyhigh Cloud Connector. Before installing the Cloud Connector, make sure all prerequisites have been met. For details, see Skyhigh Cloud Connector Prerequisites.
- You must have the Cloud Connector User and Usage Analytics Users role to install and configure Cloud Connector. For details, see About User Roles and Access Levels.
- You must access Skyhigh CASB user interface from the same network on which your Cloud Connector is installed. Otherwise, an error message displays and you cannot enable the feature or configure settings. Error message: "SIEM Integration (Inline) setting cannot be configured, viewed or modified if accessed from an external network or the Cloud Connector is not reachable. You need to be inside your company's network and the Cloud Connector instance needs to be up and running."
- To enable SIEM Integration (Inline), you must have the Skyhigh Secure Web Gateway (SWG), Remote Browser Isolation (RBI), Skyhigh Private Access, or Skyhigh Cloud Firewall license.
- To migrate from Logging Client to Log Collector, see Migrate Logging Client to Log Collector.
Log Collector
NOTE: The Logging Client is integrated into Skyhigh Cloud Connector (on-premise) and is renamed as the Log Collector on the Cloud Connector SIEM Integration (Inline) tab. The Log Collector functions in the same manner as the Logging Client.
The Log Collector (found under Settings > Infrastructure > Cloud Connector > SIEM Integration (Inline)) collects Security Service Edge web access data in your network or feeds directly into your reporting and analytics tools. You can use these files to investigate or to perform analysis with Skyhigh SSE. The Log Collector retrieves and stores the logs at configured intervals. You can save the logs to a local directory or send them from Skyhigh CASB to your third-party SIEM systems (Security Information and Event Management) through a Syslog server.
The Log Collector can simultaneously download the data originating from different log types such as SWG, Remote Browser Isolation (RBI), Private Access, and Cloud Firewall which eliminates running multiple instances to collect data from different log types. A single Enterprise Cloud Connector accommodates downloading multiple log types at the same time.
Log Collector Configuration
NOTE: By default, the API version is set to the latest version. However, you can update the API version through CLI commands. Remote Browser Isolation (RBI), Private Access, and Cloud Firewall support API version 9 and above whereas the SWG supports all the API versions from 1 until the latest version. For details, see Reporting Fields.
By default, the Log Collector Configuration is turned OFF. Use the toggle button to turn it ON, and then configure the settings based on the table below:

| Fields | Description |
|---|---|
| Region |
Choose a region depending on where your data is stored. By default, North America is the selected region:
|
| Scheduling Interval |
Enter the scheduling interval, a periodic interval starting from 2 minutes up to 30 minutes. The Cloud Connector fetches the logs from the database according to the time interval that you set. By default, the interval is set to 2 minutes. |
| Log Type |
You can simultaneously download different types of logs, including logs with data originating from the SWG, Remote Browser Isolation (RBI), Private Access, and Cloud Firewall. By default, the Log Type is selected as SWG. The Log Collector downloads log data based on the chosen log types. NOTE: To access Secure Web Gateway (SWG), Remote Browser Isolation (RBI), Private Access, and Cloud Firewall log files, you must have the corresponding licenses. For SSE license details, see About Skyhigh Security Service Edge, and for assistance, contact Skyhigh Support.
|
| Save in Directory |
Use this option to store the log files in your local directory. If you select this option, choose the path to download the logs to your system. You can store the log files in two different formats:
|
| Send as Syslogs |
Use this option to send the log files to the Syslog server. If you choose to Send as Syslogs, configure the following options:
|
IMPORTANT: If you are migrating from the Logging Client, follow the process provided in the Migrate Logging Client to Log Collector after configuring the Log Collector.
Once the Log Collector is successfully configured, the Cloud Connector pulls the Log Collector configurations and you will see the following message in the debug log.
24 Jan 2024 22:55:37 [DEBUG] [taskScheduler-1] c.s.l.c.t.LoggingClientTask| Logging Client enabled,fetching Data
You can find debug logs with the file name shnlogprocessor-debug.log at the path, <EC-Installed-Directory>/logs.
If you experience any issues with the configurations, contact Skyhigh Support for assistance.
CLI Commands
| Usage | CLI Commands |
|---|---|
|
Replay Logging Client data: Used to retrieve the logs within the specified time frame. |
root@EC-VM12:/shn/swathi/qaar/lc# ./shnlpcli replayLoggingClientData --startTime 2023.12.11.04.55.00 --endTime 2023.12.11.07.15.0 --logType SWG |
|
Update Logging Client last success: Used to pull the logs from the specified time. |
root@EC-VM12:/shn/swathi/qaar/lc# ./shnlpcli updateLoggingClientLastSuccess --updateTime 2024.01.29.08.40.00 --logType SWG |
|
Update forensic API version: Used to update the forensic API version. |
root@EC-VM12:/shn/swathi/qaar/lc# ./shnlpcli ufav --version 12 NOTE: You can update the forensic API version to all the log types collectively. However, you cannot update different API versions to individual log types separately. For example, you can update API version 11 to all the log types, but you cannot update API version 9 to SWG, 10 to RBI, 11 to Private Access, and 12 to Cloud Firewall. |
|
Show the current forensic API version: Used to display the configured forensic API version. |
root@EC-VM12:/shn/swathi/qaar/lc# ./shnlpcli sfav |
|
IMPORTANT: The following command lists all CLI commands available in CC: root@ecqa-automation00-new:/shn/balu-perf# ./shnlpcli --help |
|
