About Resources
The Analytics > Resources page allows you to view all of your IaaS and Container Resources in AWS, Azure, and GCP enabled with Skyhigh CASB. (For AWS resources, the Resources are shown after an On-Demand Scan is performed.)
It also provides visibility into Amazon’s storage container service, Amazon Elastic Container Registry (ECR), and provides the compliance status for each resource that has a Config Audit Policy incident, DLP incident, or Skyhigh Security CWS threat.
The Resources page also provides visibility of container assets for Azure Container Registry (ACR) and Google Container Registry (GCR), displaying container images stored as resources, and operating system inventory from container images.
Users with the Usage Analytics role can access the Analytics > Resources page.
You can also add the Resources card to your Dashboards. For details see About My Dashboard.
Risk Score
At any given time, your IaaS infrastructure has hundreds of resources and thousands of incidents, and it is difficult to prioritize critical incidents for analysis and remediation. To solve this issue, Skyhigh CASB provides risk scores for all resources in the Risk table column, (Low: 1-3, Medium: 4-6, High: 7-9). This allows you to focus on the riskiest resources first.
Risk scores are calculated based on different types of incidents like Configuration Audit, DLP and Malware, Vulnerabilities, Workload Hardening, and related attribute categories. For details, see Resource Risk Details.
Table View
The Resources page Table view is the default view.
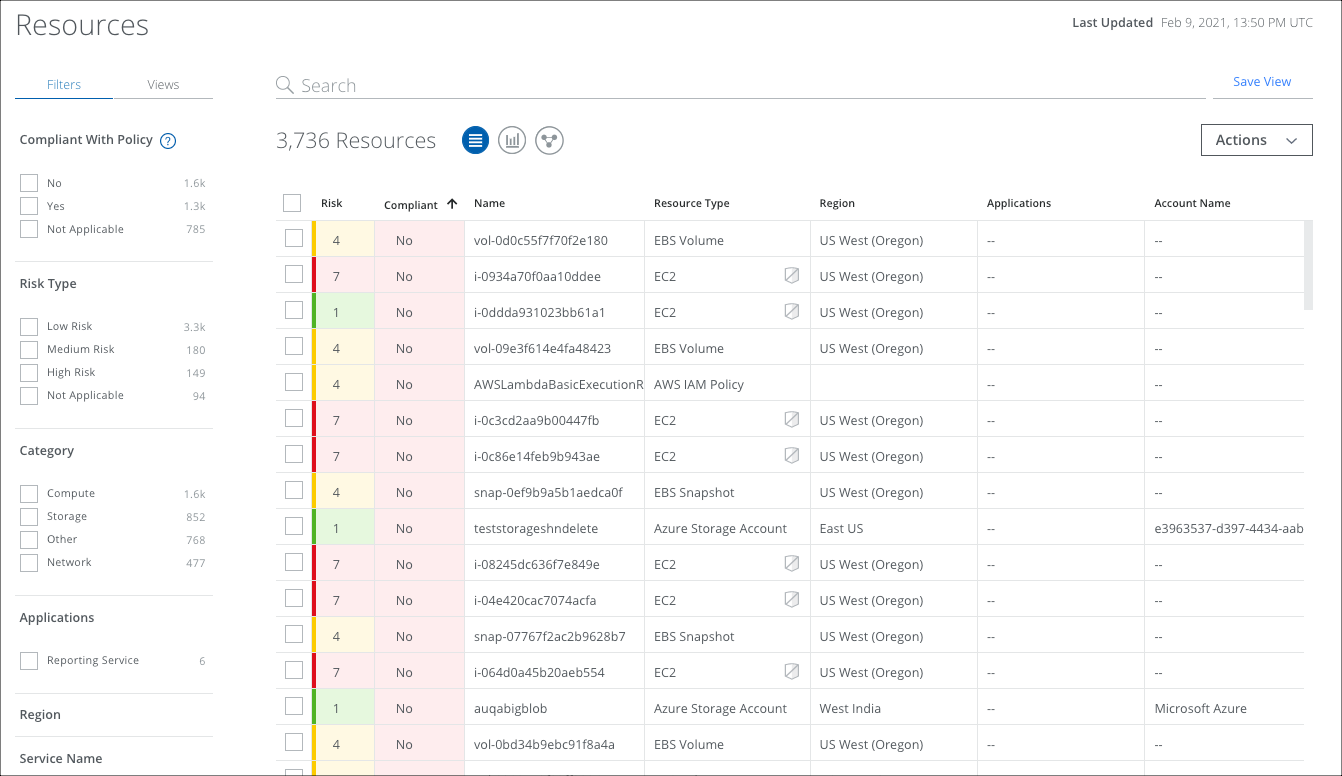
The Resources page provides the following information and actions:
- Filters. Select options on the Filters tab to scope down your search.
- Views. Select Saved Views created by you or shared with you by another user to reuse specified search parameters from a previous search on current data.
- Search. Search via the Omnibar.
- On the Resources page, you can also use the Omnibar to search based on tags for specific values across AWS accounts and Azure subscriptions. For example, tag-based search allows you to search for specific values across AWS accounts and Azure subscriptions, such as:
- List all Untagged Resources, where no tags are defined. This is used, for example, if your company has a policy that all resources must have a set of mandatory tags.
- List all resources that have All possible values for a given tag-key.
- List all resources with No Values, or where only a tag-key is defined.
- You can also search by CVE Number. For details, see CVE Number Search.
- You can use NOT operators to exclude specific terms from your search results. For details, see NOT Operator.
- On the Resources page, supported for ECR and ACR, you can also search for:
- Namespaces. For example, Ubuntu or Centos.
- Packages. For example, OpenSSL or bZIP.
- Operating systems.
- On the Resources page, you can also use the Omnibar to search based on tags for specific values across AWS accounts and Azure subscriptions. For example, tag-based search allows you to search for specific values across AWS accounts and Azure subscriptions, such as:
- Save View. Click to create a Saved View from your search query.
- Actions. Click Actions to:
- Install Skyhigh Security Agent. (This option is only available if you have Skyhigh Security Cloud Workload Protection). See Install the Skyhigh Security Agent via Download URL and Install the Skyhigh Security Agent via Chef Script.
- Download CSV. Select to generate a CSV file of the Resources list and download it immediately.
- Settings
- Create Report.
- Business Report (PDF). Create a PDF report and run it immediately, which then appears in the Report Manager.
- CSV. Create a CSV report and run it immediately, which then appears in the Report Manager.
- XLS. Create an XLS report and run it immediately, which then appears in the Report Manager.
- Schedule. Schedule a report to run later, which then appears in the Report Manager.
- Risk. Provides the resource's risk score and allows you to investigate resources based on your priorities. Click the Risk score (Low: 1-3, Medium: 4-6, High: 7-9) to See Risk Details in the Cloud Card. Filter the table by Risk Type for Low, Medium, and High risk resources.
- Compliant. Displays whether the resource is compliant as Yes, No, or Not Applicable.
- Name. The name of the Resource.
- Resource Type. Displays the type of resource: such as S3, Security Group, User, Container Security Repository and Registry, Operating System, image, and more. The shield icon refers to the CWPP Agent. The shield is green if the agent is installed, and grey if the agent is not installed.
- Region. The geolocation of the resource.
- Applications. Displays the names of any Application associated with the Resource.
- Provider. The cloud service provider of the resource.
- Account Name. The name of the account that the resource belongs to.
Resource Cloud Card
Click an incident to display the Resource Cloud Card, which lists details about the resource along with Mini Cards that provide the total number of incidents for each type, such as Configuration Audit, DLP and Malware, Vulnerabilities, and more. It also includes information on policies that have made that resource non-compliant. Click the number of incidents to go to the Policy Incidents page with appropriate filters for more information.
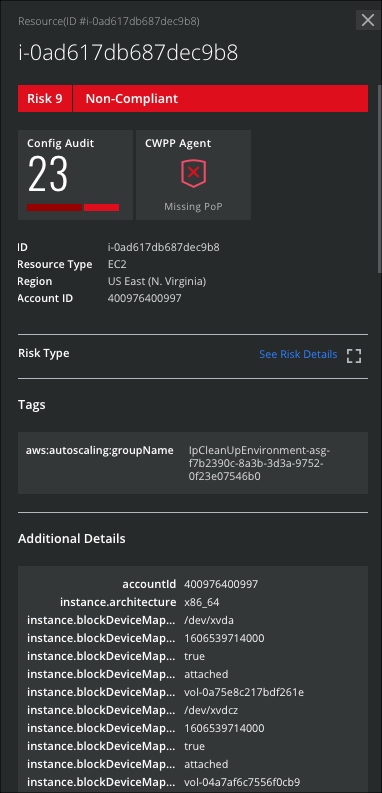
The Resource Cloud Card displays the following details:
- Name. The name of the Resource.
- Risk. Provides the resource's risk score and allows you to investigate resources based on your priorities. Click the Risk score (Low: 1-3, Medium: 4-6, High: 7-9) to See Risk Details in the Cloud Card. Filter the table by Risk Type for Low, Medium, and High-risk resources.
- Compliant. Displays whether the resource is compliant as Yes, No, or Not Applicable.
- Config Audit Mini Card. Click to view Security Configuration Audit incidents for this Resource.
- CWPP Agent Mini Card. Click the Mini Card to extend the Cloud Card with details on each individual CWPP Agent. Click an individual Resource in the list to see more information and instructions. Supported Agent statuses are: Not installed, No communication, Missing PoP, and Managed.
- DLP and Malware Mini Card. Click to view DLP and Malware incidents for the resource.
- Vulnerabilities Mini Card. Click to view Vulnerability incidents.
- ID. The Resource Name.
- Resource Type. Displays the type of resource: such as S3, Security Group, User, Container Security Repository and Registry, Operating System, image, and more.
- Region. The geolocation of the resource.
- Account ID. The account ID for the resource.
- Risk Type. Click See Risk Details to open the Resource Risk Details modal.
- Tags. Displays the tags associated with this resource.
- Additional Details. Displays complete details about the resource.
Resource Risk Details
In the Resource Cloud Card, when you click See Risk Details, the Resource Risk Details modal is displayed. The Resource Risk Details modal provides risk score and distribution of incidents based on Priority Groups and attribute categories.
Skyhigh CASB policies are mapped to attribute categories. Based on the severity of the policies, they are grouped into four priority groups.
- Priority Group 1. Contains all policies with High severity from the attribute categories Unrestricted Access, Network Security, Data Exfiltration, and Malware.
- Priority Group 2. Contains all policies with High severity from the remaining attribute categories.
- Priority Group 3. Contains all policies with Medium priority from all the attribute categories.
- Priority Group 4. Contains all policies with the severity Low, Warning, and Info from all the attribute categories.
For example, in the following screenshot, you can see one incident in each Priority Group 1, Priority Group 2, and Priority Group 4. You can see three incidents under Priority Group 3.
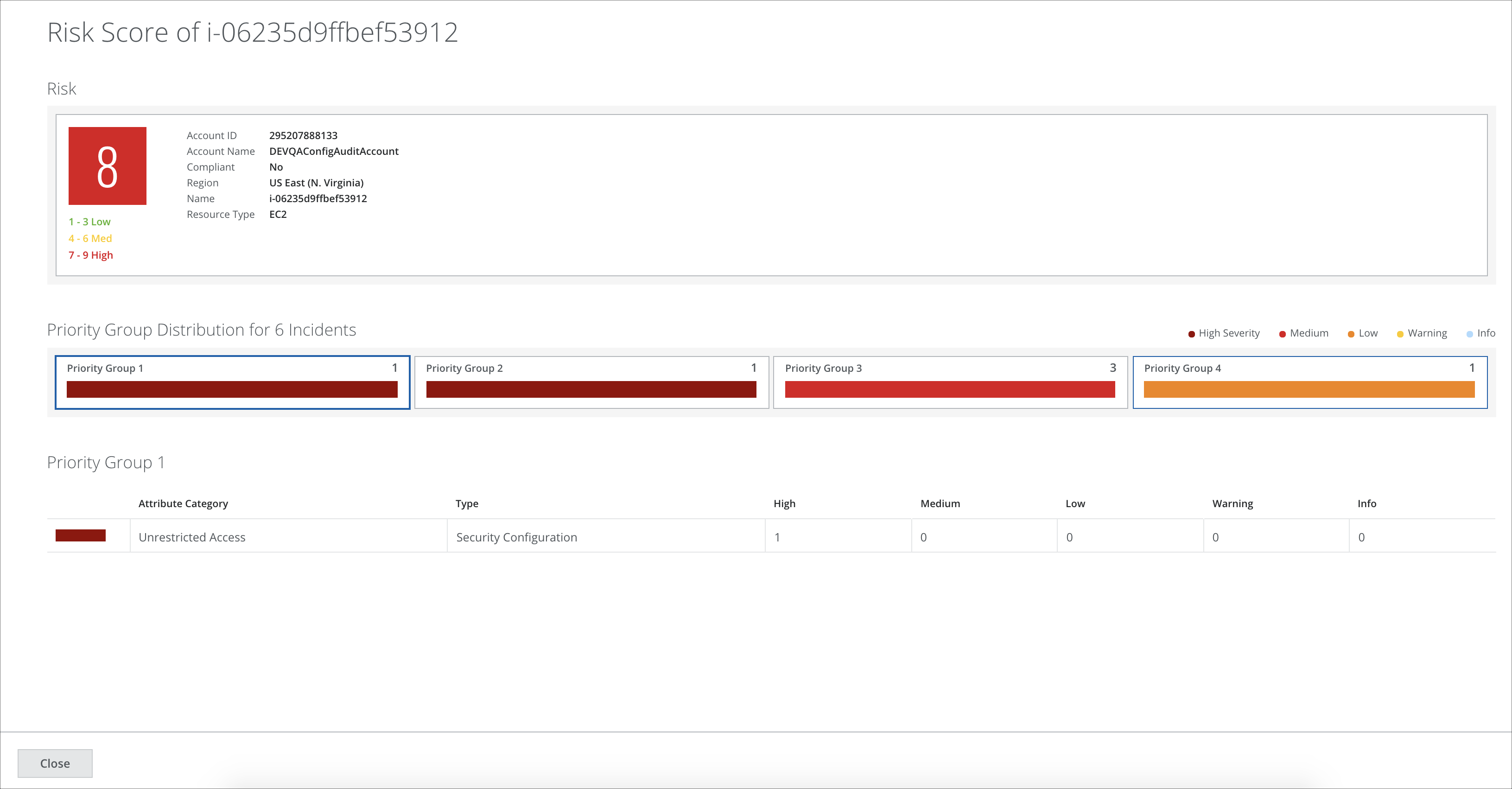
The Resource Risk Detail modal displays the following information:
- Risk. Provides the resource's risk score and allows you to investigate resources based on your priorities. Click the Risk score (Low: 1-3, Medium: 4-6, High: 7-9) to See Risk Details in the Cloud Card. Filter the table by Risk Type for Low, Medium, and High risk resources.
- Account ID.
- Account Name. The name of the account that the resource belongs to.
- Compliant. Displays whether the resource is compliant as Yes, No, or Not Applicable.
- Region. The geolocation of the resource.
- Name. The name of the Resource.
- Resource Type. Displays the type of resource: such as S3, Security Group, User, Container Security Repository and Registry, Operating System, image, and more.
- Priority Group Distribution for Incidents. Displays the distribution of Priority Groups for the incidents against this Resource. Click the group to display the following information:
- Attribute Category. Attribute Category maps to the Business Requirements from the Policy Templates page.
- Type. Policy belongs to Config Audit, DLP, or Vulnerability.
- High. The severity of the policies.
- Medium. The severity of the policies.
- Low. The severity of the policies.
- Warning. The severity of the policies.
- Info. The severity of the policies.
Attribute Categories
| Type | Attribute Category |
|---|---|
| Security Configuration | Unrestricted access |
| Security Configuration | Identity And Access Management |
| Security Configuration | Network Security |
| Security Configuration | Encryption |
| Security Configuration | Logging |
| Security Configuration | Monitoring |
| Security Configuration | Certificate And Key Management |
| Security Configuration | Backup & recovery |
| Security Configuration | Infrastructure Management |
| Security Configuration | Application Security |
| Security Configuration | Others |
| DLP And Malware | Data Exfiltration |
| DLP And Malware | Document Classification Solutions |
| DLP And Malware |
Malware |
| DLP And Malware | Others |
| Container Vulnerabilities |
Vulnerabilities |
| Device Posture | Vulnerabilities |
| Hardening | Device Posture |
Chart View
To display your Resource data in a chart, click the Chart icon, under the Omnibar.
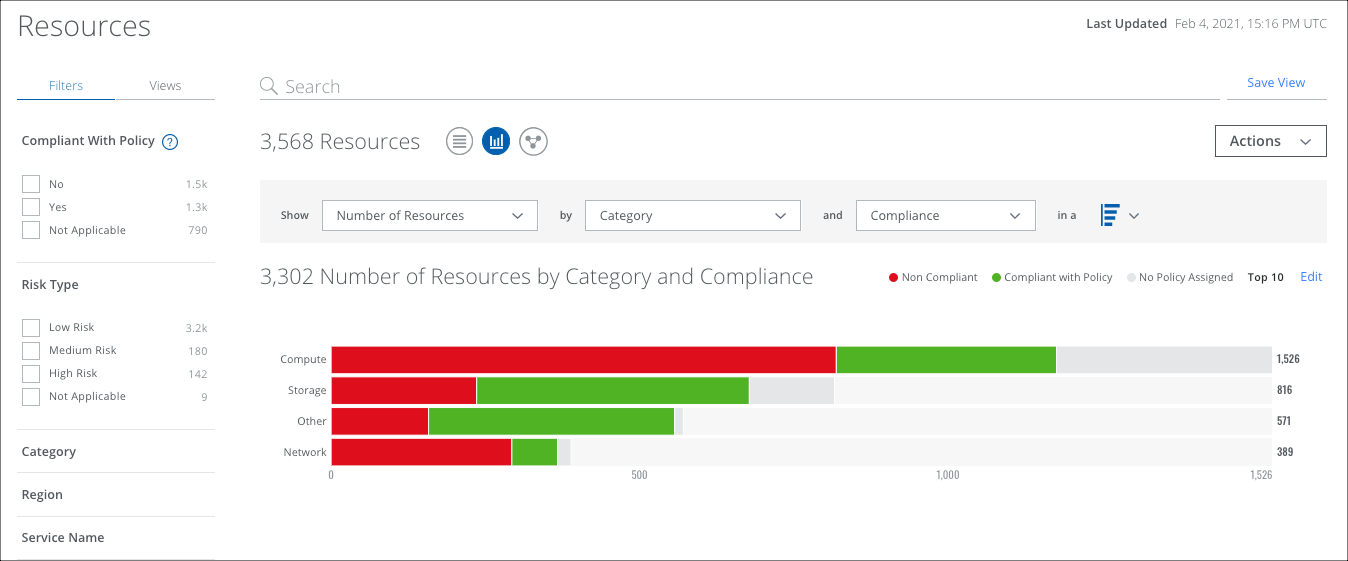
To display Resources data in a chart:
- Show. Select an item from the Show list to determine the X axis of your chart.
- By. Select an item from the By list to determine the Y axis of your chart.
- And. In the and dialog, select the third parameter, if available.
- In a. From the In a list, select your chart type:
- Trend. Line or vertical bar chart.
- Breakdown. Donut or horizontal bar chart.
Your data is displayed in the chart.
Connections Graph View
The Resource Connections Graph View provides an interactive graph of IaaS and Container Security resource asset connections and network flow for AWS, Microsoft Azure, and Google Cloud Platform (GCP).
If you have enabled Amazon Virtual Private Cloud (VPC) Flow Logs, the connections graph is also overlaid with VPC Flow Logs data. For example, you can view all external IP addresses, including malicious IP addresses, communicating with your infrastructure at a resource level. You can also see the other resources a particular resource is communicating with, as it may not be allowed.
To configure VPC Flow Logs for Skyhigh CASB, see Enable Amazon VPC Flow Logs for Skyhigh CASB.
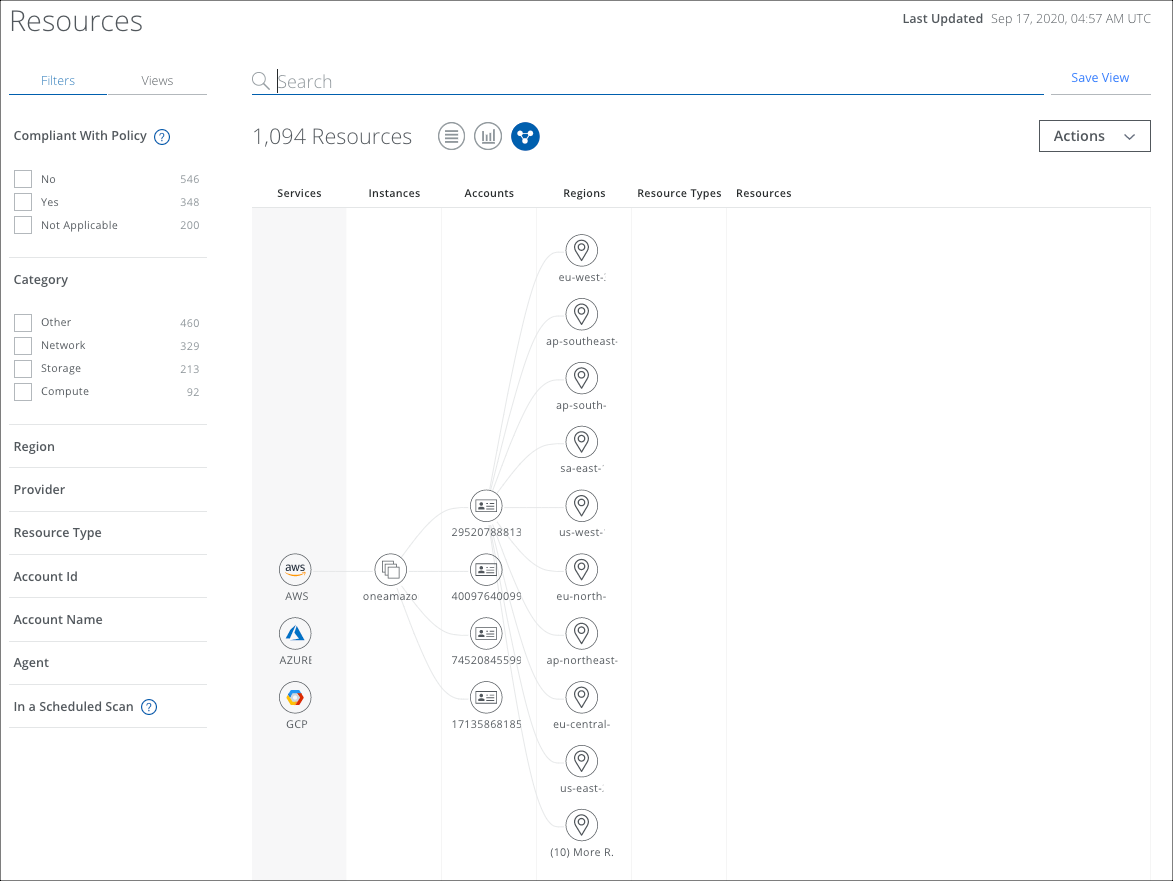
When you click on the Connections View icon, you will see your full inventory of Resources.
The Resources Connections Graph provides the following columns, which represent all of the resource entities in your environment as interactive nodes:
- Services
- Instances
- Accounts
- Regions
- Resource Types
- Resources
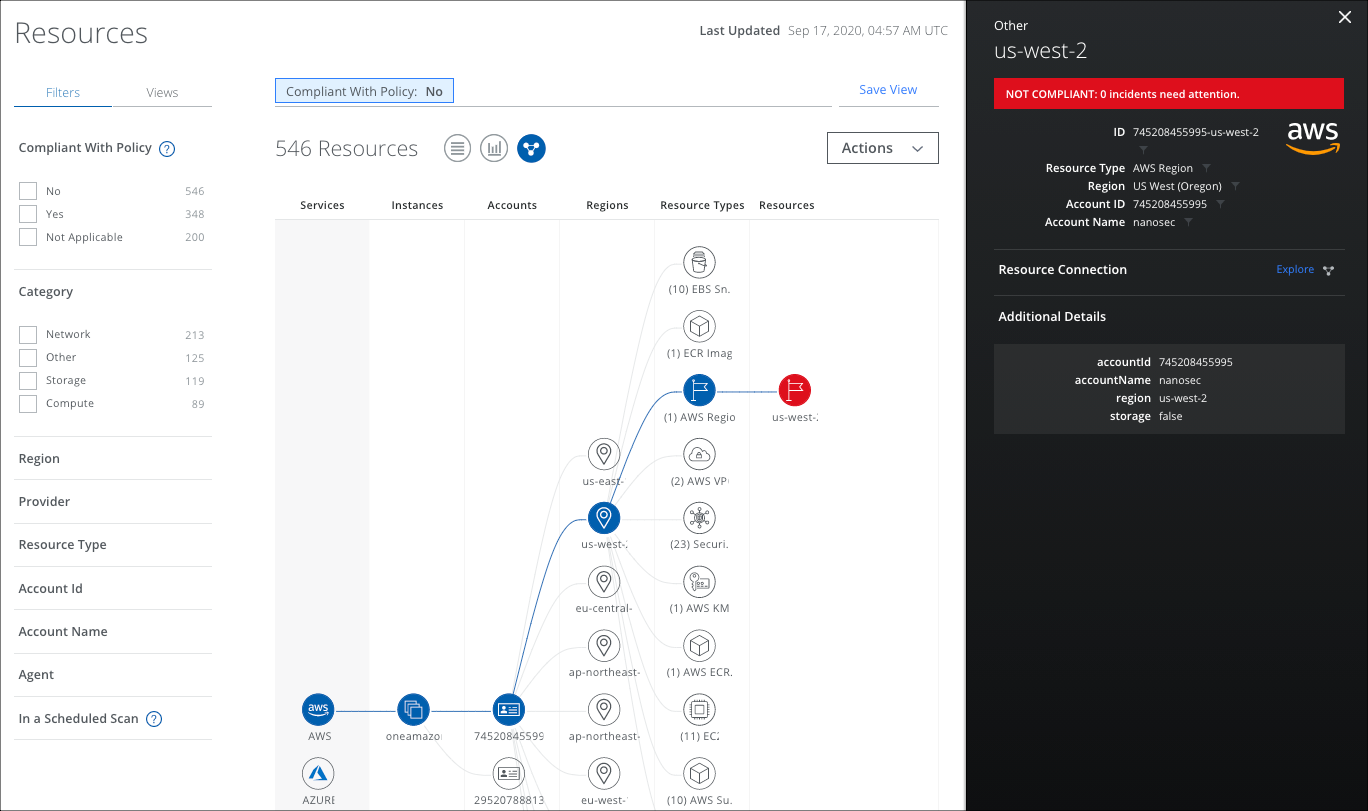
To search for Resources in the Connections Graph:
- Use Filters and Omnibar search terms to display only relevant resources and interconnections for your investigation and highlight resource compliance.
- Click through the graph nodes to navigate and drill down for more information.
- The graph displays 10 nodes per column, but when you have many more resources available, they are combined into an aggregated node. It displays a number in front of the name in parenthesis (such as (8) More Re., for Regions). Select the aggregated node to display a dialog, and you can search the remaining Regions or Resources.

- Or click a Resource node to display the Cloud Card.
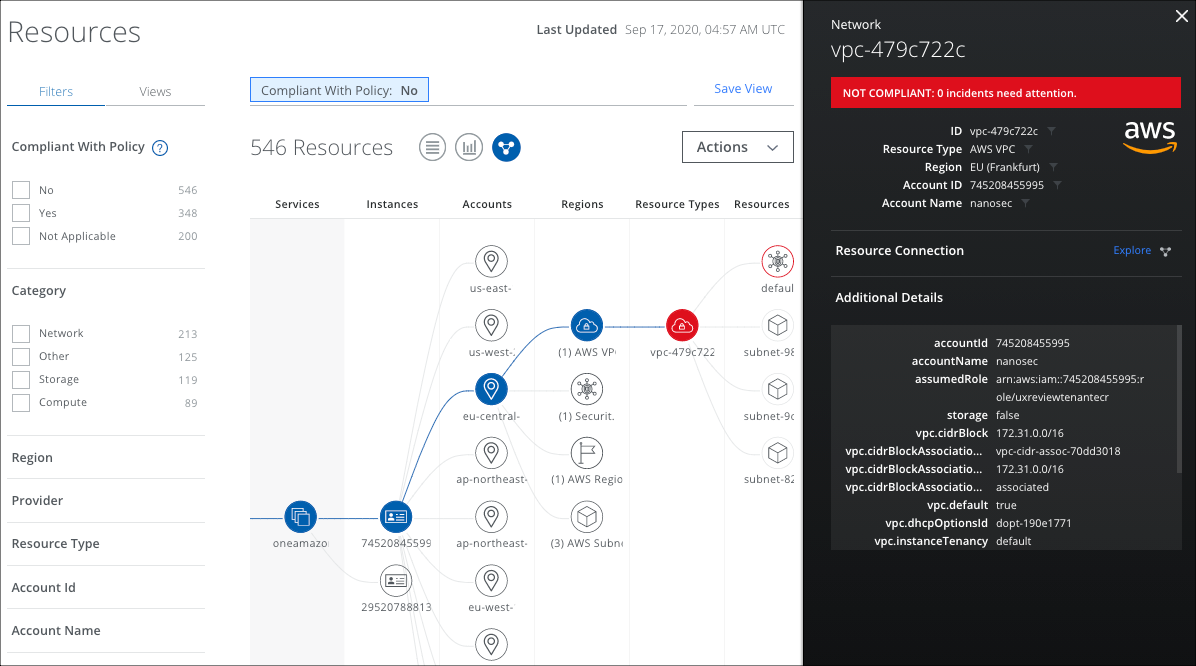
- To explore a single resource, in the main Table View, you can select a resource row, then click the Connections View icon.
- That resource is displayed with its connections.
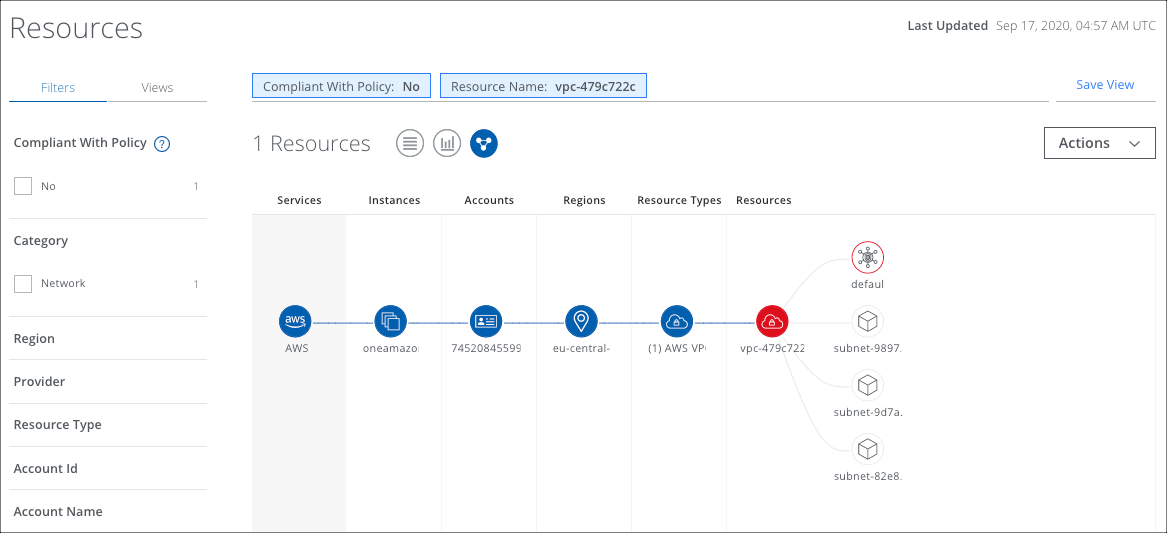
- Any Resource that is non-compliant is shown in red. A Resource that is compliant is shown in green.
- If you have enabled VPC Flow Logs, you can view known bad external IP addresses.
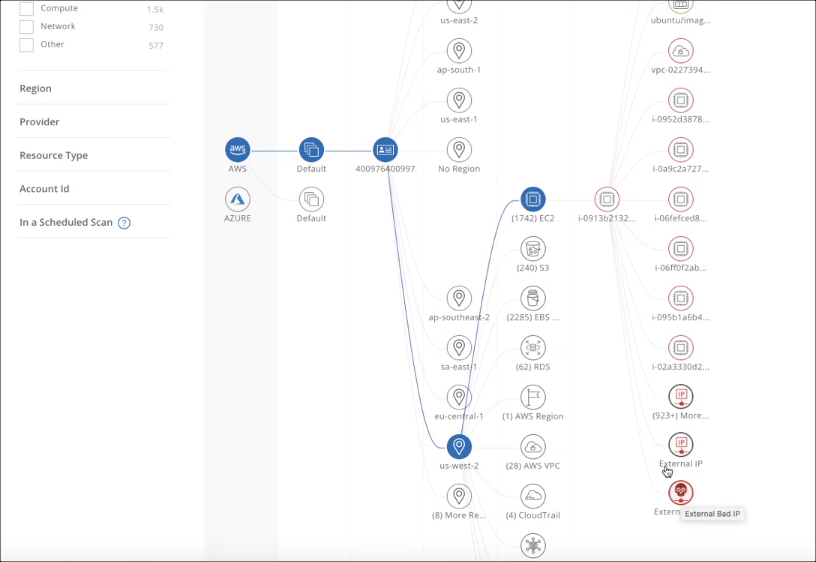
- Click an External IP or External Bad IP to display details.
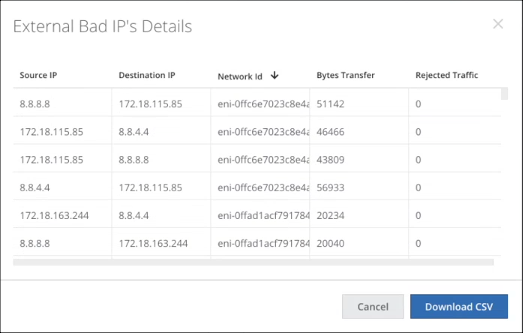
- Click Download CSV to download a CSV report from the Report Manager with the following details:
- Source IP
- Destination IP
- Network ID
- Bytes Transfer
- Rejected Traffic
