About Custom Anomalies
Custom Anomalies enable you to create your own anomaly structure based on the risk parameters identified in the Sanctioned IT cloud service activities. Creating Custom Anomalies allows you to align with your organization's risk posture and raise an incident when anomalies are detected so this information can further assist your investigation of the anomaly.
The Security Operations Center (SOC) analysts can use Custom Anomalies to detect emerging threats, enhance the effectiveness of existing detections and prevent the progression of a cloud data breach. As a result of these efficiencies, security analysts can reduce their investigation time.
You can define Custom Anomalies by configuring the rule with risk parameters such as activity type/category, location, IP address, device, and more. Once the required parameters are configured, if any criteria match the rule, incidents are generated for cloud services and displayed on the Anomalies page.
The Custom Anomalies user interface is located at Incidents > Anomalies > Anomaly Settings page. You can find the Create a Custom Anomaly option under Actions.
Troubleshooting Warning Messages
Different scope and criteria can cause the Custom Anomaly limit to exceed and warning messages are displayed on the Anomaly Settings, Name & Scope, and Rules & Exceptions pages. Troubleshoot the following warning messages:
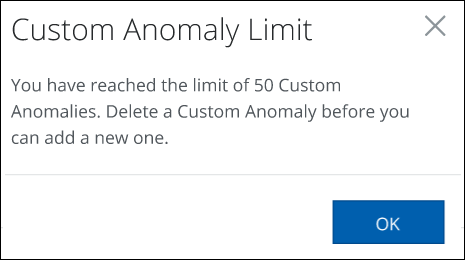
Custom Anomaly Limit
A maximum of 50 custom anomalies can be created and saved on the Anomaly Settings page. When the limit is reached, the following message will be displayed. Delete a Custom Anomaly before you can add a new one.
Quota for Custom Anomalies
On the Anomalies Settings page, the number of generated anomalies for each custom anomaly rule per duration is limited. The limits are as follows:
- Daily Quota. Each rule with the duration set as Daily may generate a maximum of 100 anomalies per day.
- Weekly Quota. Each rule with the duration set as Weekly may generate a maximum of 200 anomalies per week.
- Monthly Quota. Each rule with the duration set as Monthly may generate a maximum of 300 anomalies per month.
For example, a weekly rule can generate up to 200 incidents for each week. If the limit is reached for the current week, the quota system auto-disables the rule and stops generating incidents for that rule in that week. The rule gets auto-enabled again from next week and incidents are generated until the limit is reached for that week.
When the limit is reached for one or more custom anomalies, the following message will be displayed and the custom anomaly status changes to disabled. To enable this anomaly, you need to adjust the anomaly thresholds in order to generate fewer incidents.
Active Custom Anomaly Limit
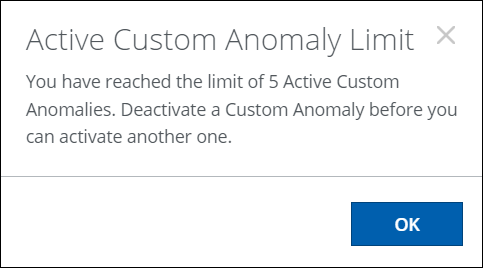
A maximum of 5 custom anomalies can be activated on the Anomaly Settings page. If the maximum limit is reached, the following message will be displayed. Deactivate a Custom Anomaly before you can activate another one.
Parameter Limit
Quota for Rule Parameter Values
On the Rules & Exceptions page, the number of values for custom anomaly rule parameters is limited. The limits are as follows:
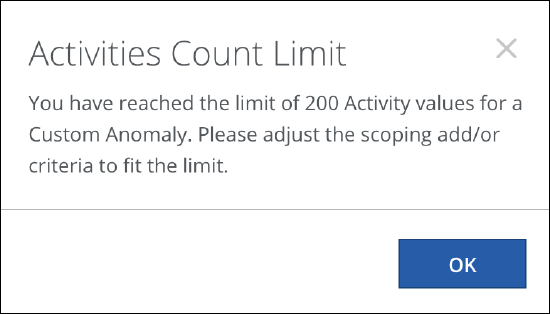
Activities Count Limit
A maximum of 200 user activities can be selected for the Activity Type/ Category rule parameter.
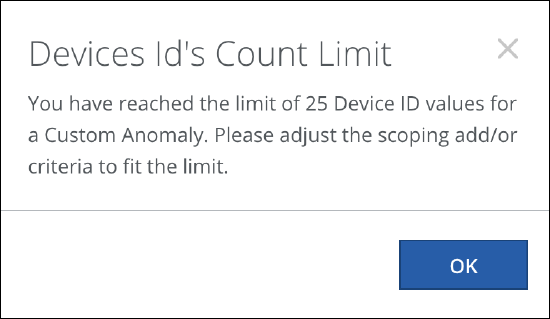
Device ID Count Limit
A maximum of 25 device IDs can be selected for the Device ID rule parameter.
Locations Count Limit
A maximum of 25 locations can be selected for the Location rule parameter.
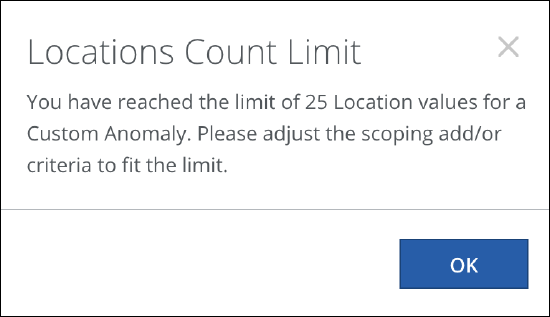
When the limit is reached for the values of these rule parameters, the above messages will be displayed. Adjust the values of the rule parameters within the specified limits. For details, see Create a Custom Anomaly.
About Rules and Parameters
Custom Anomalies rules define the conditions to match the criteria for anomaly detection. This means the rule must match the criteria to trigger an anomaly. To define a rule, different types of parameters can be combined using Boolean logic. All rule parameters are logically combined with IF, THEN, and AND operators. Add an exception to exclude or ignore the criteria if needed and it can also be combined with Boolean logic.
Rules are assigned by Severity: Warning, Info, Minor, Major, or Critical. This allows you conditionally create an anomaly based on the triggered rules.
You can configure rules with these parameters:
| Rule Parameters | Description |
|---|---|
| Activity Type/ Category | The Activity Type or Category rule allows you to detect and monitor the type of user activities in the service. |
| The Activity Count rule allows you to detect and monitor the number of user activities performed in the service within the specified duration. | |
| The Device ID rule allows you to detect and monitor the unique identification number of the device from which users perform activities on the service. | |
| Device | The Device rule allows you to detect and monitor the device type from which users perform activities on the service. |
| Location | The Location rule allows you to detect and monitor the location where the user performs activities on the service. |
| The Source IP rule allows you to detect and monitor the Source IP address of the user performing activities on the service and prevents unauthorized users from gaining access to your service through restricted IP ranges. | |
| The Source rule allows you to detect and monitor the trusted and untrusted activities performed by users on the service. | |
| The User Agent rule allows you to detect and monitor the users who are performing activities on service using legacy user agents with the old authentication mechanisms. |
