Explore Key Features of Cloud Connector
Skyhigh Cloud Connector can be installed on UNIX or Windows operating systems, or on virtual machines.
The following Cloud Connector features bring value to your organization.
Data Transfer
Skyhigh Cloud Connector requires username/password authentication to establish a connection to Skyhigh Security Skyhigh CASB. This username/password is unique for each customer.
All communication between the Cloud Connector and Skyhigh CASB is encrypted using SSL on port 443. Connections are only initiated from the on-premises Cloud Connector outbound to Skyhigh CASB.
Detokenization
Skyhigh Cloud Connector also acts as a token server, which converts tokenized user information to clear text. This allows administrators to view tokenized user identifiable data within Skyhigh CASB.
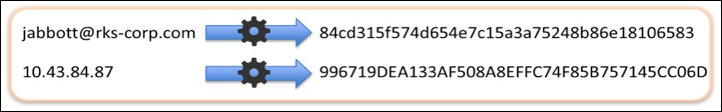
There are two types of identifiable personal data found in egress device logs that organizations might want to protect: source IP address and user ID. Customers can tokenize these values using the on-premises Cloud Connector so that these clear text values are never uploaded to Skyhigh CASB. Only tokenized values are uploaded and only customers retain the ability to detokenize the data in the Skyhigh CASB dashboard.
Skyhigh CASB provides two options for tokenization, one with SHA-1 and another with the SHA-256 algorithm:
- Tokenize the original data and generate a hash value.
- Use the user-provided salt/secret to the original value before hashing to provide protection against pre-computed rainbow tables.
Active Directory Integration
Cloud Connector collects login/logout activity from Active Directory Domain controllers to map the IP address to the username and collects user attribute information from Active Directory.
This process requires a read-only user account with access to all domains in the directory. Cloud Connector then establishes itself as an Active Directory listener and is notified of IP addresses that are mapped to usernames.
SIEM Integration
Cloud Connector allows you to publish detected anomalies from Skyhigh CASB servers to the customer Security Information and Events Management (SIEM) systems using Syslog. The Syslog target is configured during the Cloud Connector server installation.
SIEM integration using Syslog provides:
- A method to generate a Syslog output for anomalies.
- A method to define the Syslog target system.
- A server daemon on the log processor to feed Syslog events.
- A method to retrieve anomalies from the SHN dashboard.
- A configuration tab in Alerts and Settings that allows an administrator to enable or disable the Syslog function.
Cloud Connector includes a Syslog server to accept message logs from security solutions that support this method. The Syslog server aggregates received messages up to a threshold, based on age or total size, and publish to a file for Cloud Connector to process.
Checkpoint FW API Integration
Providing a service to collect logs from Checkpoint Firewall logs using a Log Extraction Agent (LEA), Cloud Connector Checkpoint Firewall FW API Integration enables API-based log consumption of Checkpoint logs.
Separate Service Credentials
The login credentials for the Cloud Connector and Skyhigh CASB dashboard are different. Customers use a dedicated Cloud Connector service account, which is different from the Skyhigh CASB access user account.
