Configure User Agent Rules
IMPORTANT: Activity Count and Activity Type or Category are mandatory rules to complete your custom anomaly rule statement. The Incomplete Rule message will be displayed if these rules are not added.
The User Agent rule allows you to detect and monitor the users who are performing activities on service using legacy user agents (old authentication mechanisms). You can also define the rule with other parameters such as Activity Count, Device ID, Source IP, Location, and more. Anomalies are triggered when a user performs any activities on a service using the configured user agent that exceeds the expected activity count.
The User Agent allows you to add the user agent string to the rule. Multiple user agents can be added and use a comma to separate user agents. If the User Agents value is a string such as Mozilla/5.0 (Windows NT 10.0; Win64;x64) then add only the substring of the real string in the User Agent input box such as Windows NT 10.0.
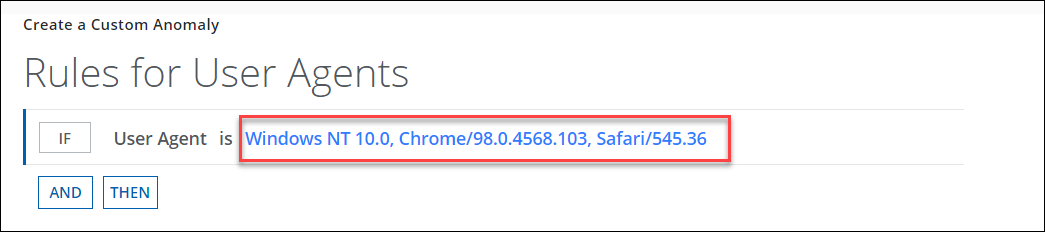
Use Case: Suppose you want to be notified when a user performs more than 1 admin activity on Box in a week using the user agents Mozilla/5.0 (Windows NT 10.0; Win64;x64) and Chrome/98.0.4568.103 Safari/545.36.
To configure this rule:
- Go to Incidents > Anomalies > Anomaly Settings.
- Click Actions > Create a Custom Anomaly.
- On the Name & Scope page, enter a name, description, services, and users.
- On the Rules & Exceptions page, select Activity Type or Category from the list. For example, Administration.
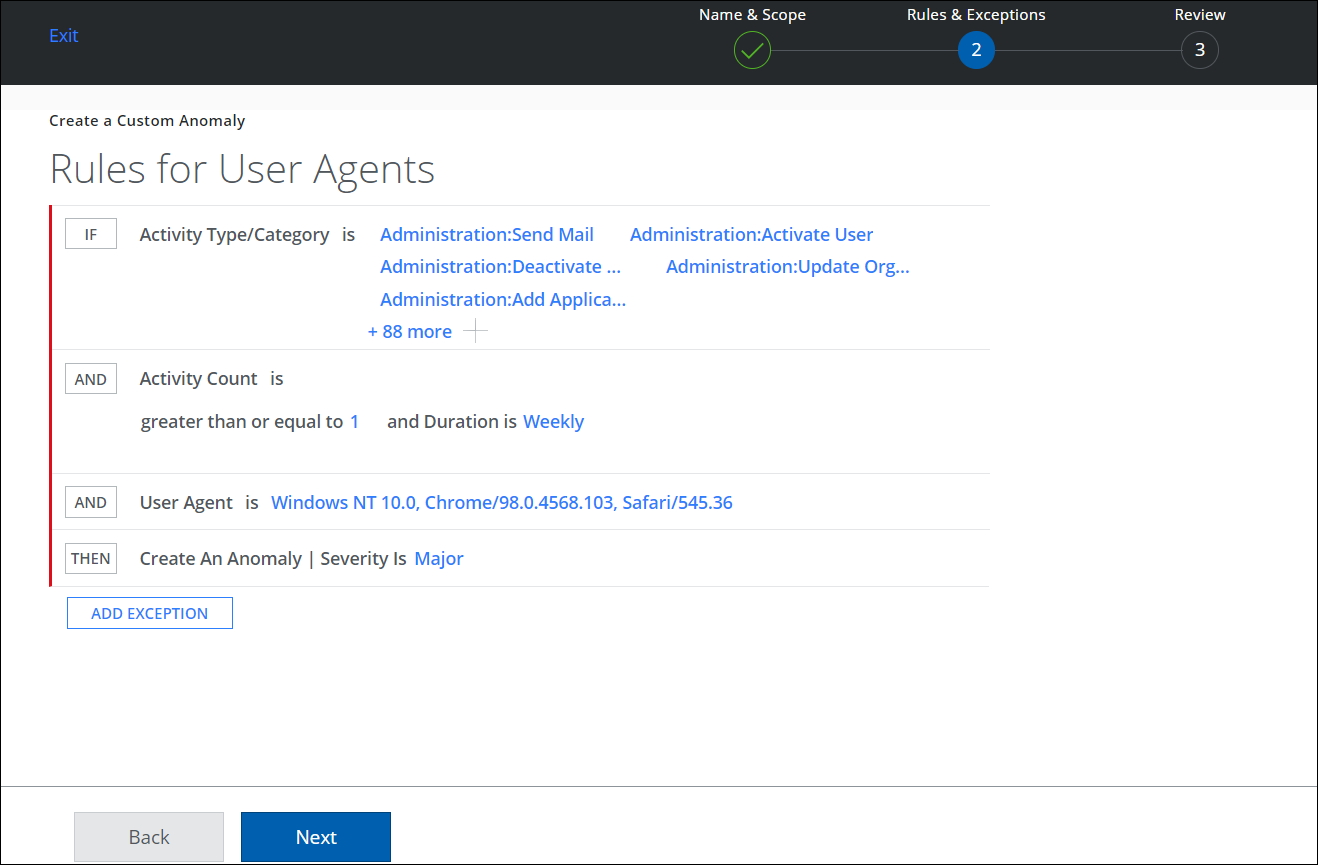
- Click AND to:
- Enter a value for Activity Count is greater than or equal to. For example, 1.
- Set the Duration for a custom anomaly detection. For example, Weekly.
- Click AND to add the selected user agents to the rule. For example, Chrome/98.0.4568.103, Safari/545.36. For a string value such as Mozilla/5.0 (Windows NT 10.0; Win64;x64), add only substring as Windows NT10.0.
- Click THEN to create an Anomaly and select a Severity. For example, Major.
- Click Next.
- Review the custom anomaly rule and click Save.
