Salesforce Custom Objects and Field Encryption
You can search for and add Salesforce custom objects, then configure encryption schemes for the fields in those custom objects. Any new custom fields in the objects already added to the Skyhigh CASB tenant are automatically discovered by Skyhigh CASB through a background process that runs every few hours.
To search for and add a custom object, enable API access for Salesforce.
Add a Custom Object
- Choose Sanctioned Services > Service Management.
- Click the shield on the managed Salesforce instance.
- In the Encryption Policies screen, click Add Custom Object.
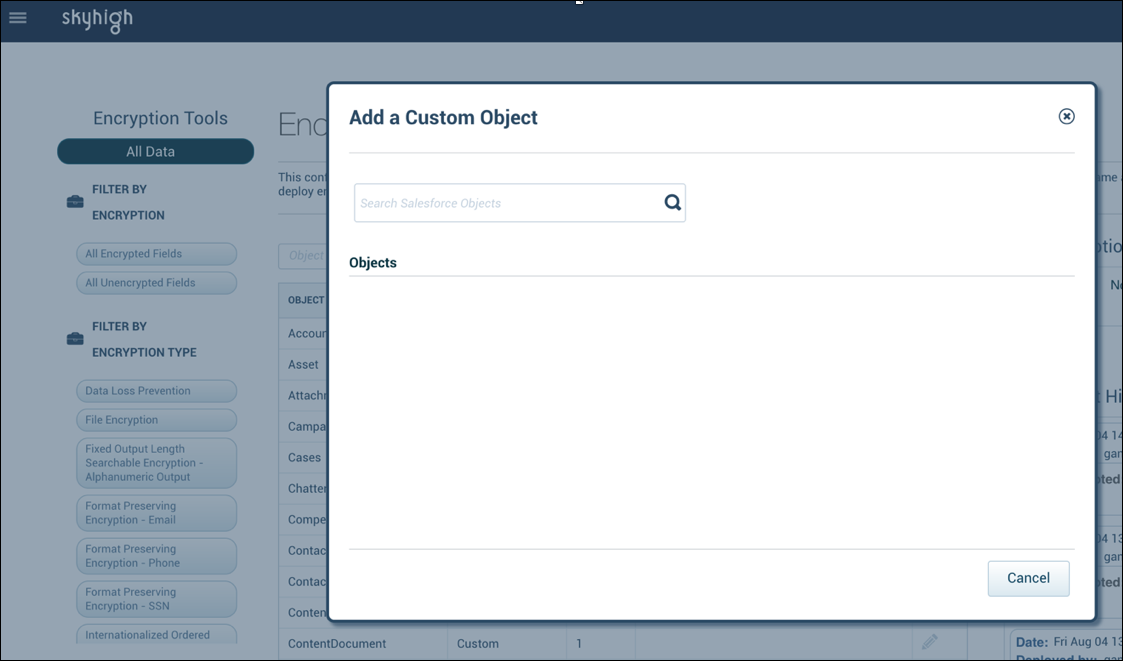
- Enter the name of the object in the search field, and then select the object listed in the Objects section.
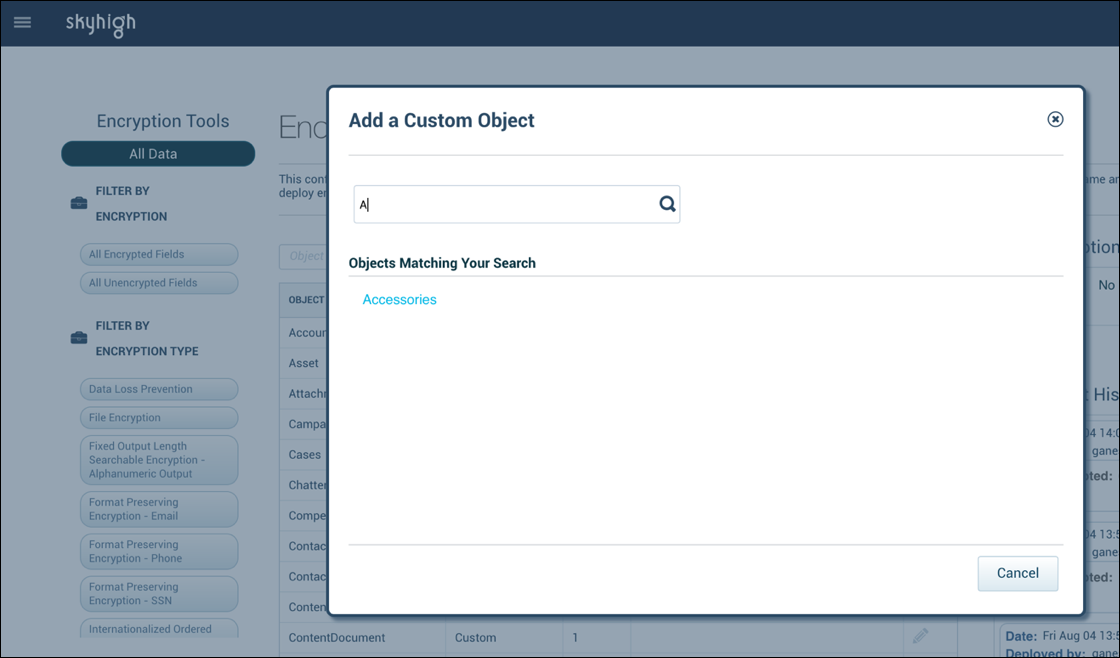
You will see the custom object added to the encryption policies grid. You can set up encryption schemes for the custom object fields.
After configuring the instances of the custom object in Salesforce Lightning UI, follow the steps below to make sure that any custom object instances created from custom visual force pages are encrypted or decrypted by Skyhigh CASB.
Manage Field Identifiers in Skyhigh CASB
- Click Edit for any object used in the custom visual force page.
- Click Edit for the field to configure identifiers. If the same field is used in multiple pages, configure the unique identifier used for that field in each of those pages.
- In the Manage Field Identifiers screen, click Add identifier.
- Select Create New Page and specify the details of the visual force page.
- Specify the unique ID used in the visual force page and click Save.
- Repeat steps 1–5 for each occurrence of the field in any page where it's used.
Custom Fields
For objects already present in the Encryption Policies grid in your Skyhigh CASB tenant, any new fields added are automatically discovered by Skyhigh CASB, and an email is sent to the admins with the details of the fields discovered. You can configure the email IDs of the admins who are notified of custom fields discovery in the service properties of the managed Salesforce instance.
LIMITATIONS: The mapping files (nsm) will be generated only for encrypt/decrypt in case of custom objects and not applicable to reports.
