About Anomalies
Anomalies are actions or behaviors that exceed set thresholds in Threat Protection. While anomalies do not always indicate malicious behavior, they should be investigated to determine their cause.
Anomalies come in many types, including Access Anomalies, Administration Anomalies, Custom Anomalies, and Data Anomalies. For more information, see Anomaly Types.
The Anomalies user interface is located at Incidents > Anomalies > Anomalies.
All service anomalies are consolidated on this page, or you can choose to view the anomalies occurring in just one Service. You can view the anomaly incidents in a Table view or a Chart view. It also provides easy access to filters, Saved Views, and displays anomaly details with a single click.
You can also add the Anomaly card to your Dashboard. For details, see Add a New Card.
Table View
Select a service using the Service Name filter to view and analyze incidents for that service. Only services with active Skyhigh CASB Secure licenses are available.
The default anomalies table displays information about specific clusters of anomalies that strongly suggest your cloud services may have been compromised. Your security response team will use this information to observe and respond to anomalies. The Anomalies page Table view is the default view.
IMPORTANT: The anomaly count as shown in-hero stats and in the table includes resolved, false positive, new, and open states - so you might see a slightly higher count than was shown in the older UI (as it filtered resolved and false positive states). Suppressed anomalies are filtered by default, though you can search for them explicitly. This is the same behavior as on the Incidents page. You can filter (or create a Saved View) for the desired states if you wish.
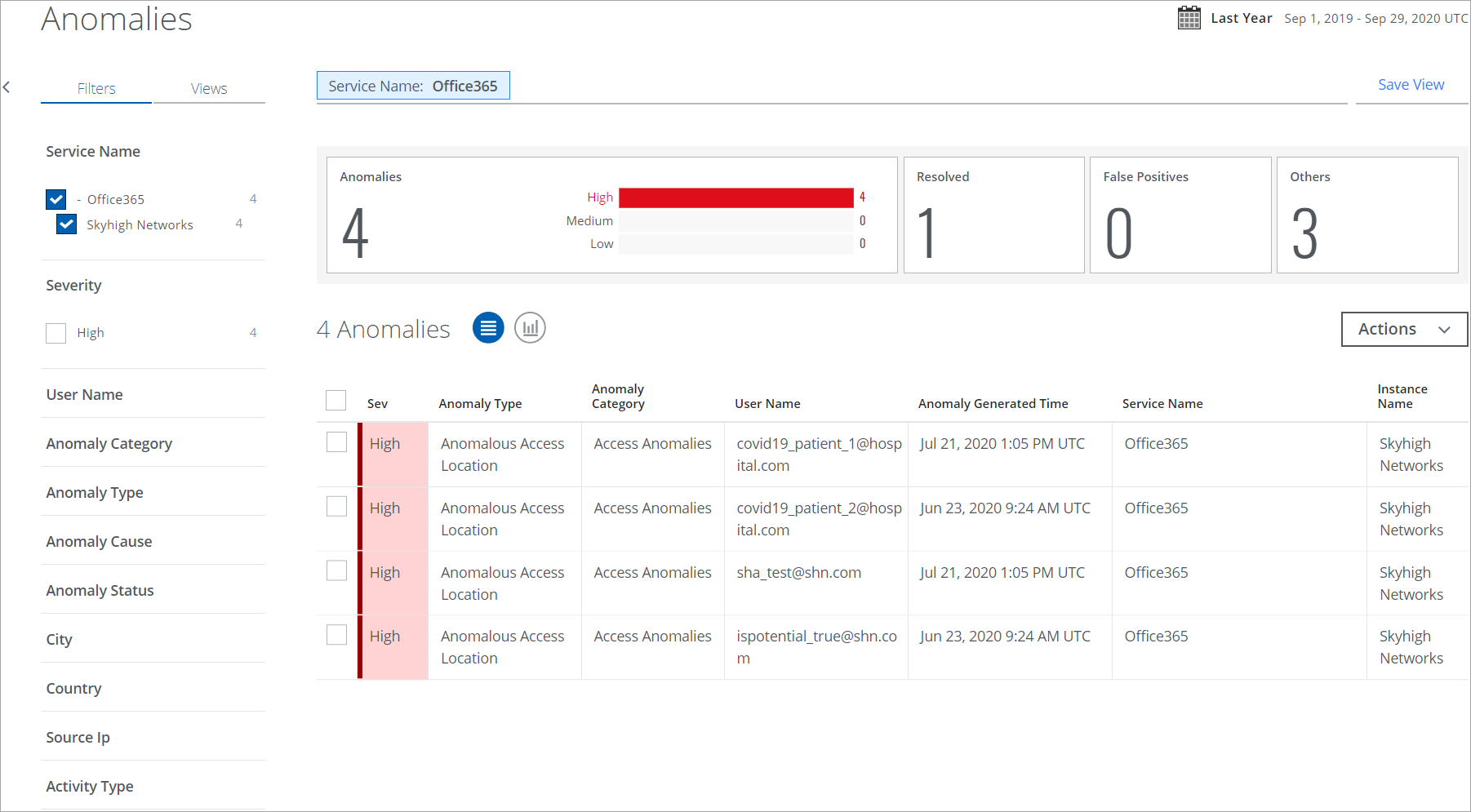
The Anomalies table provides the following information and actions:
- Search. Use the search bar to search for your anomaly with the terms listed in Threat Protection and Activity Monitoring Search Terms.
- Filters. Select options on the Filters tab to scope down your search.
- Date Picker. Use the Date Picker to specify a date range to display data.
- Views. Select Saved Views created by you or shared with you by another user to reuse the specified search parameters from a previous search on the current data.
- Executive Summary. The Executive Summary displays an at-a-glance view of the current anomaly count in the Anomaly and Anomaly Status categories, with a weekly count of anomalies.
- Severity. Each anomaly is ranked based on severity.
- Red. High.
- Orange. Medium.
- Yellow. Low.
- Anomaly Type. The name of the anomaly type is derived from the Anomaly Category.
- Anomaly Category. The name of the anomaly category and the specific anomaly triggered to understand what sort of anomaly you are looking at and why it may represent a risk to your cloud services. The three anomaly categories are Access Anomalies, Administration Anomalies, Data Anomalies, and Custom Anomalies.
- User Name. The user who triggered the anomaly.
- Anomaly Generated Time. The date and time that the anomaly was detected.
- Service Name. The service where the anomaly occurred.
- Instance Name. The instance where the anomaly occurred.
- Actions. Click Actions to:
- Change Owner. To change the owner of multiple incidents.
- Change Status. To change the status of multiple incidents.
- Download CSV. Click CSV to Export Anomalies to a CSV File. The download begins immediately. It is suitable to import CSV into a third-party software security system or to open it in a spreadsheet program. The data in the spreadsheet may provide greater detail than the details displayed in the UI.
- Create an Exception
- Adjust Anomaly Thresholds. Administrators may want to manually adjust anomaly detection thresholds to control the generation of new anomalies.
- Create Report.
- Business Report (PDF). Create a PDF report and run it immediately, which then appears in the Report Manager.
- CSV. Create a CSV report and run it immediately, which then appears in the Report Manager.
- XLS. Create an XLS report and run it immediately, which then appears in the Report Manager.
- Schedule. Schedule a report to run later, which then appears in the Report Manager.
- User Risk Report. Generate and download a User Risk Report to identify high, medium, and low-risk users for sanctioned services in your organization. You can generate or schedule a report, and access the generated reports via email or in the Report Manager.
NOTES:
- The User Risk Report includes data from the last 100 days.
- You cannot view the Filters configured for the User Risk Report on the Schedule Report page.
Generate User Risk Report includes the following options:
- Generate Report. Click to generate a report. By default, the report is generated in the CSV file format. The report's title includes the report's name, current date, and time. For example, User Risk Report 10_09_23 1_56_50 PM UTC.
- Select your report format. Select CSV or XLSX file formats to generate a report.
- Schedule. (Optional) Schedule a report to run later, which then appears in the Report Manager.
An email is sent to the recipients with a link to download the report from Report Manager, and the report is attached if the size is less than 25 MB. The report includes user details such as username, user email, user risk score, number of incidents, threats, anomalies, activities, Active Directory (AD) attributes, and more.
- Settings
- Edit Table Columns. You can edit table columns and save your changes as a Saved View.
Click any anomalies in the table to see the Cloud Card for the specific anomaly. To learn more about the anomalies, click to view the Anomaly Cloud Card.
Historical User Risk Type Filter
From the list of anomalies, you can filter and categorize your search by Historical User Risk Type for low, medium, and high-risk users.
Historical User Risk Score is a risk score assigned to the user whenever an anomaly is created, and it is rated on a scale of 1–9. This score is measured based on various factors such as the severity of the violation, the user’s security posture, and metadata about the user's overall compliance history. The score identifies the deviations as high, medium, and low-risk types:
- High (7-9). This score indicates a great potential for cloud services and data to become vulnerable to threats. This level is the least trustworthy.
- Medium (4-6). This score indicates a moderate potential for cloud services and data to become vulnerable to threats.
- Low (1-3). This score indicates little potential for cloud services and data to become vulnerable to threats. This level is the most trustworthy.
The Historical User Risk Score allows you to track and manage users’ typical usage patterns related to data security, and take necessary actions to strengthen the defense against potential threats in your organization.
To filter your Historical User Risk Type for anomalies:
-
On the Anomalies page, select any service, and then select Low (1-3) on the Historical User Risk Type filter. The Anomalies table displays only the low-risk users of the selected service.

- Click any anomaly on the table to open the cloud card and view the Historical User Risk Score of the user and activities details.

Chart View
To display your Anomaly data in a chart, click the Chart icon under the Omnibar.
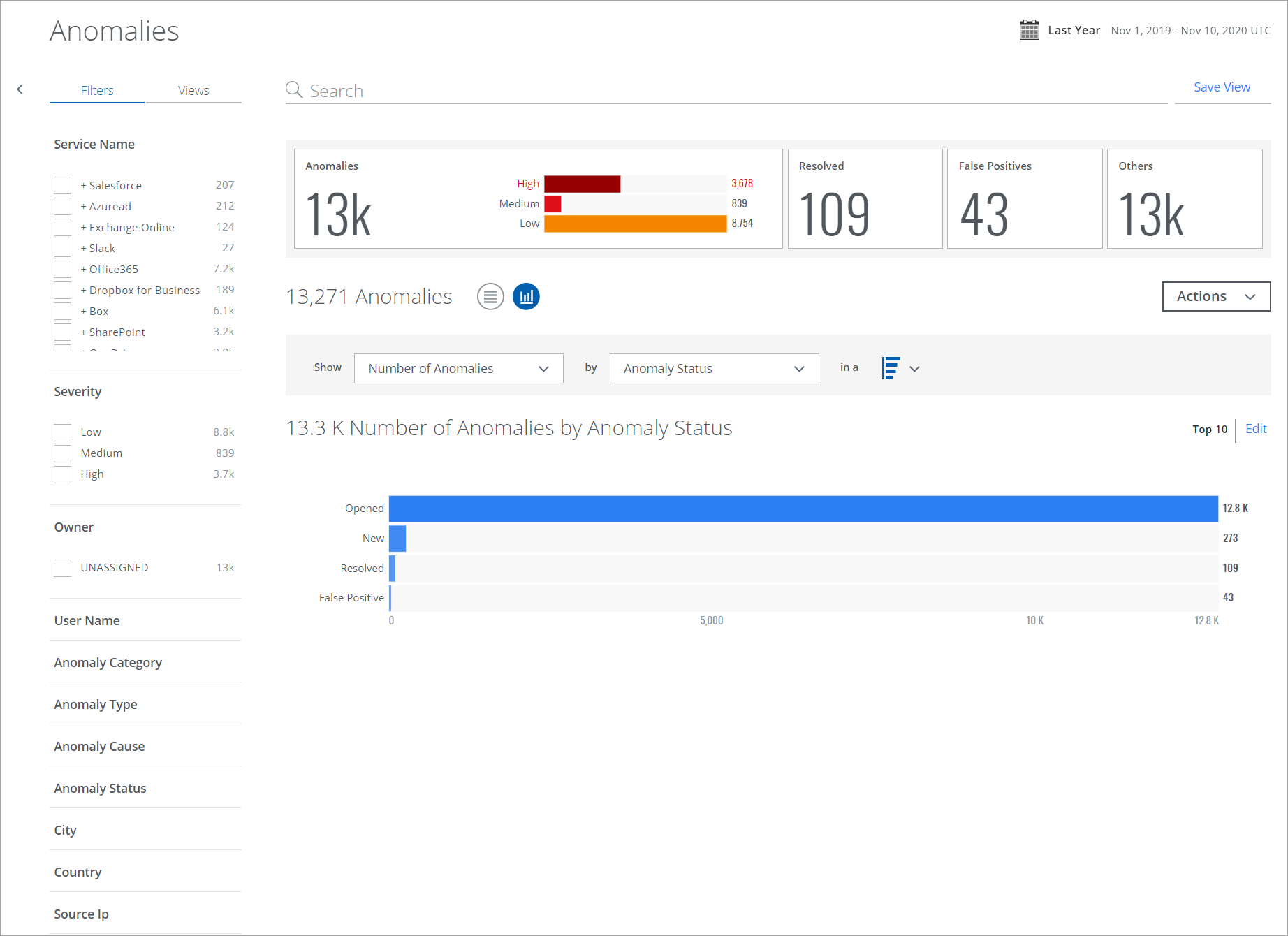
To display Anomaly data in a chart:
- Show. Select an item from the Show list to determine the X-axis of your chart.
- By. Select an item from the By list to determine the Y-axis of your chart.
- In a. From the In a list, select your chart type, if available:
- Trend. Line or vertical bar chart.
- Breakdown. Donut or horizontal bar chart.
Your data is displayed in the chart.
To edit an existing chart, click Edit.
