Reverse Proxy for Office 365 via Azure AD
Skyhigh Security's Reverse Proxy is a method to restrict access of authorized applications from unmanaged devices. Generally, the reverse proxy allows unmanaged devices to go through the SAML authentication process. As a result, authorized applications from all managed or unmanaged devices are redirected to the Skyhigh CASB proxy. But if you use Office 365 and authenticate via Azure Active Directory (also called Passthrough Authentication), then this method is unsuccessful because the authentication is not redirected through SAML authentication.
To overcome this problem, Azure AD provides a security feature called Conditional Access. This topic describes the steps to Configure Reverse Proxy for Office 365 via Azure AD.
How it Works
Azure AD Conditional Access allows your devices to access Office 365 only when you log in through the Web Gateway Cloud Service (WCGS) IPs or Skyhigh CASB reverse proxy IPs. If you login directly to Office 365 without passing through WGCS or Skyhigh CASB's reverse proxy IPs, your IP address is blocked by Azure AD Conditional Access.
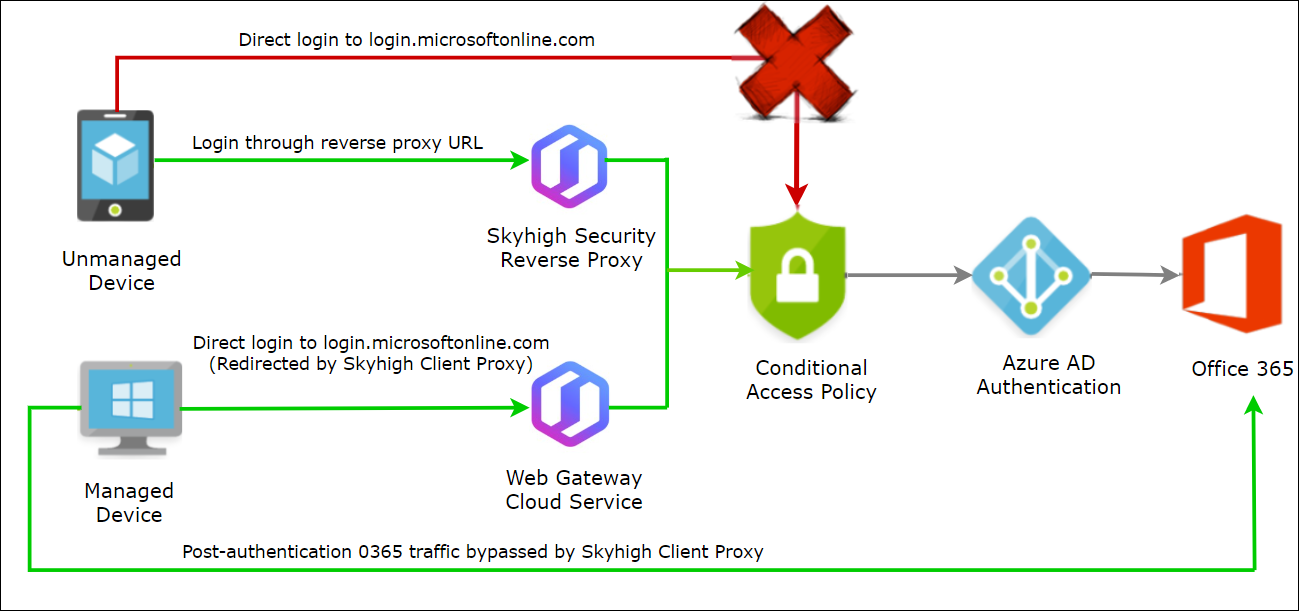
For Managed Devices, Conditional Access policies are applied only to the login process, and you are not required to send Office 365 network traffics such as office.com or office365.com through WGCS.
All non-authentication URL requests or the post-authentication requests can be bypassed in Skyhigh Security Client Proxy (SCP). At this point, the login process is proxied to meet the Conditional Access policy requirements, so proxy passes all subsequent network traffic directly to Office 365. This way Microsoft's policy is not violated in third-party network devices while inspecting Office 365 network traffic.
Prerequisites
Before you begin, make sure you have met the following prerequisites:
- Access to an Office 365 tenant authenticated via Azure AD (default authentication mechanism) and your Office 365 tenant should be licensed for Azure AD Premium P1. For more details, see Azure Active Directory Pricing and Microsoft-365-business-service-description.
- Admin Access to Azure AD portal (https://portal.azure.com).
- Access to Skyhigh CASB tenant enabled with the Web Gateway Cloud Service (WCGS) or Skyhigh Security Service Edge (SSE).
- A managed or unmanaged device installed and configured with Skyhigh Security Client Proxy to pass network traffic through WGCS or SSE.
- An unmanaged device that does not send network traffic through WGCS or SSE.
To get the reverse proxy IP address for specific POPs or tenants, contact Skyhigh Security Support.
Configure Reverse Proxy for Office 365 via Azure AD
Perform the following steps to configure Reverse Proxy for Office 365 via Azure AD.
Step 1: Configure Conditional Access in Azure AD Portal
To achieve this configuration, make sure your Office 365 tenant is licensed for Azure AD Premium P1.
This configuration blocks direct login attempts of unmanaged devices to Office 365 and allows only the devices that login through WGCS or Skyhigh CASB reverse proxy.
To configure conditional access, perform the following activities:
Configure New Location
- Download the current list of outbound IP ranges for WCGS and the IP ranges for Skyhigh CASB reverse proxy.
To get the Skyhigh CASB reverse proxy IP address for specific POPs or tenants, contact Skyhigh Security Support.
- Login to the Azure AD admin portal.
- Go to Azure Active Directory > Security > Conditional Access > Named locations and click New location.
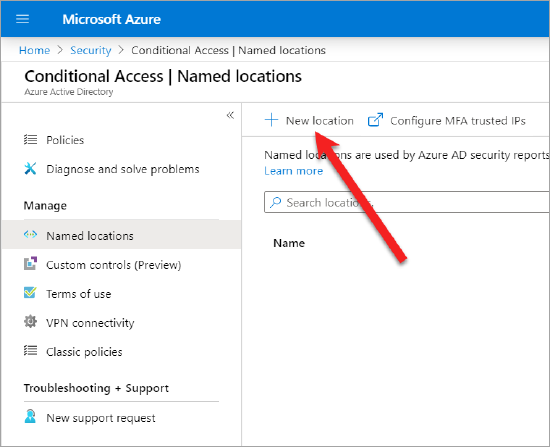
- Enter a name for your new location. For example, Skyhigh Security WGCS.
- Click IP ranges radio button. Copy and paste the IP ranges from the list you downloaded in step 1.
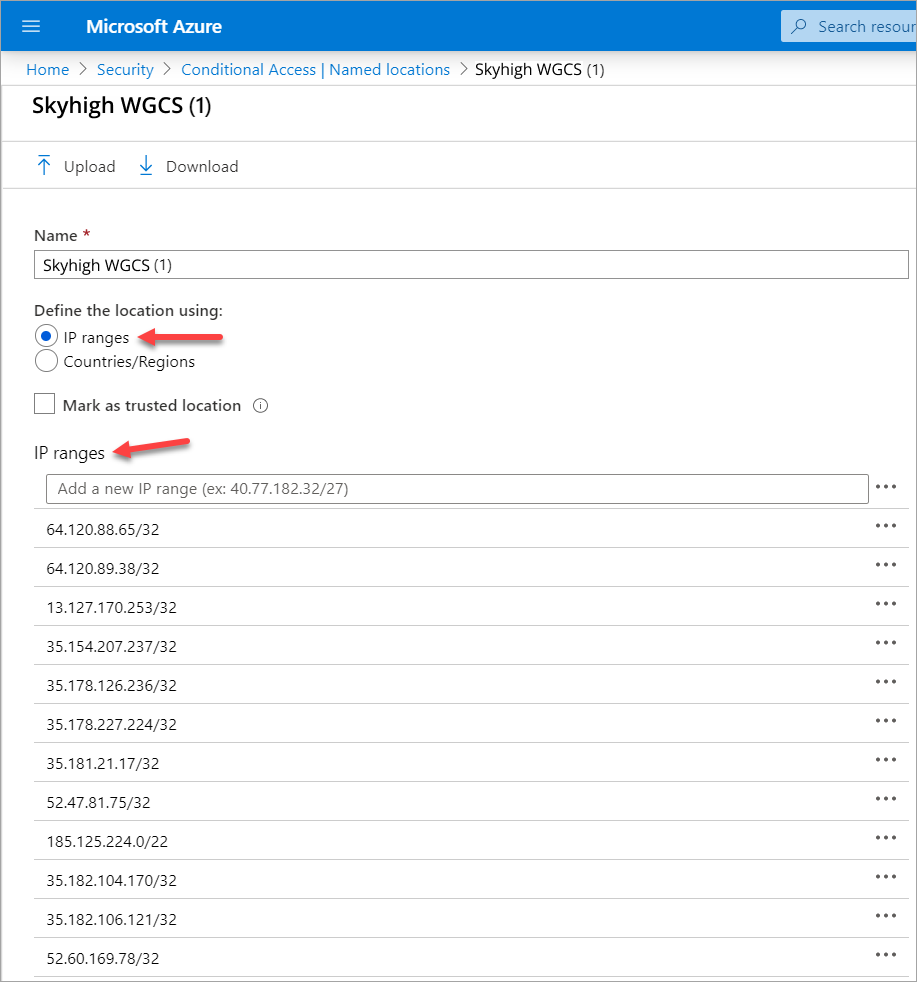
The limit of IP ranges per location is 12.
- Repeat the steps 3 to 5 until you add all the IP ranges from the WGCS and MVC reverse proxy lists. Optionally, you can add any public IPs specific to your deployment that are egress IPs from on-premises locations.
- Click Save.
Configure New Policy
- Go to Policies and click New policy.
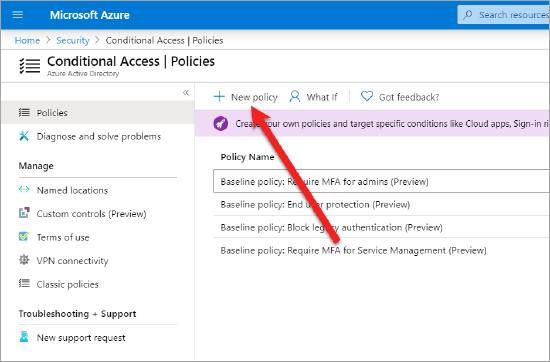
- Enter your policy name. For example, Allow only WGCS and Skyhigh CASB reverse proxy.
- Choose Users and groups, click the Select users and groups radio button, and select the checkbox Users and Groups.
- To add a user to the policy, click Select.
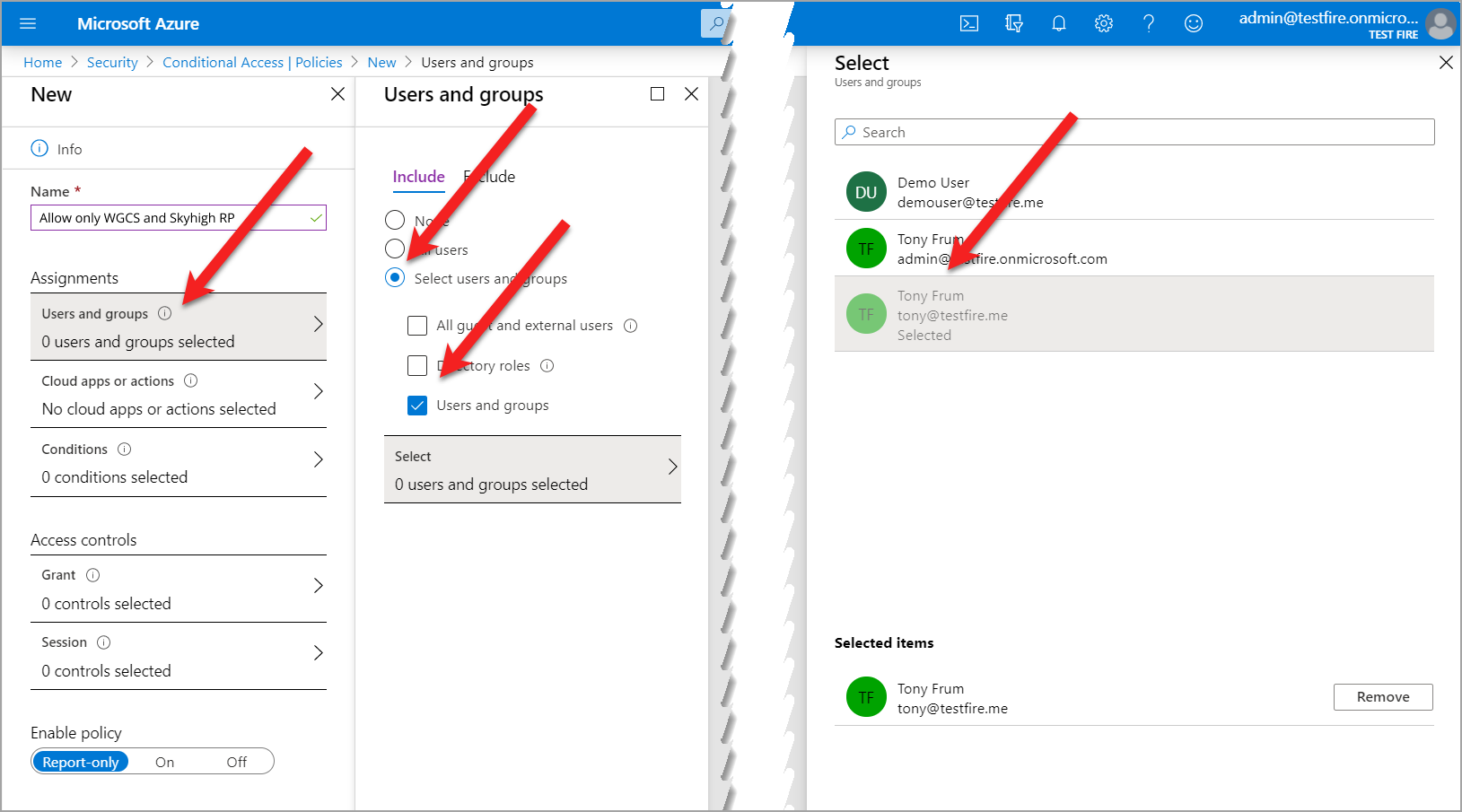
- Select the required user and click Done.
You can lock inside the Office 365 tenant entirely if you apply this policy to all users.
- Click Conditions > Locations. Under Configure, click Yes and under Include, click Any location radio button.
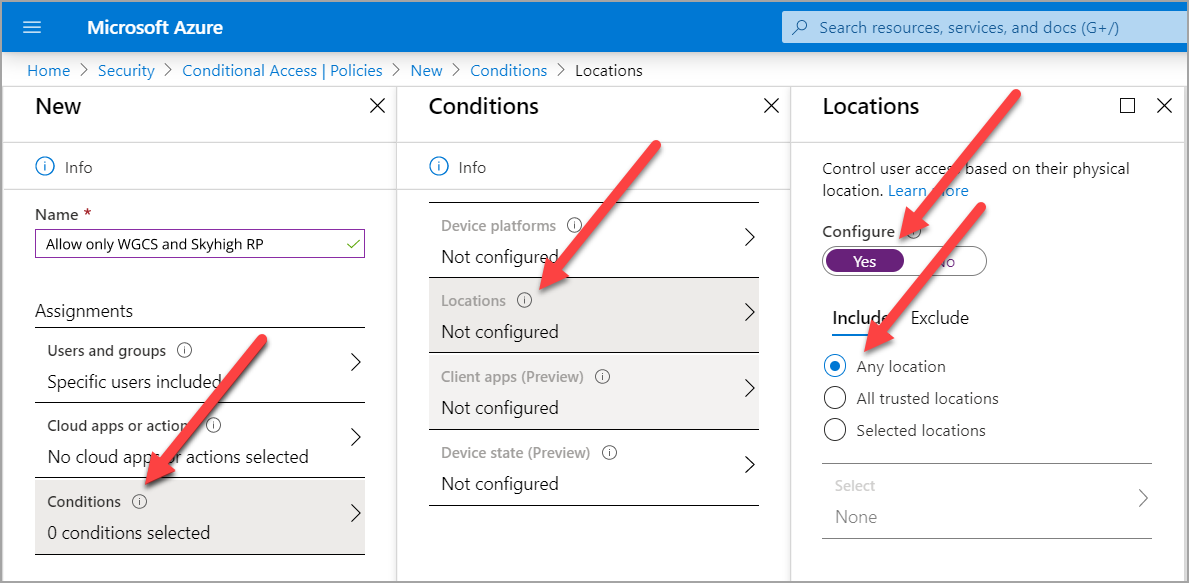
- Under Exclude, click Selected locations radio button. Click Select and select all the locations created in the section Configure New Location.
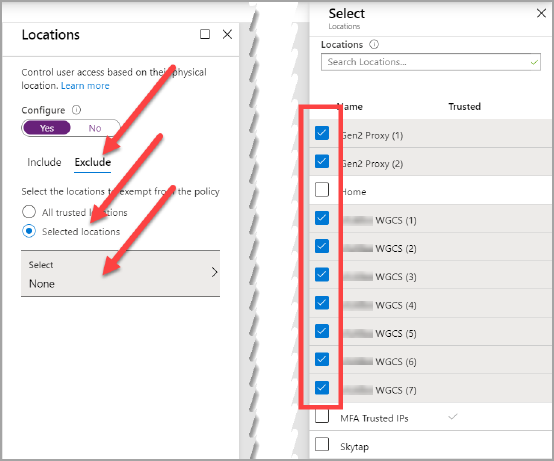
- Click Done.
- Choose Grant and click Block access radio button. To confirm this selection, click Select.
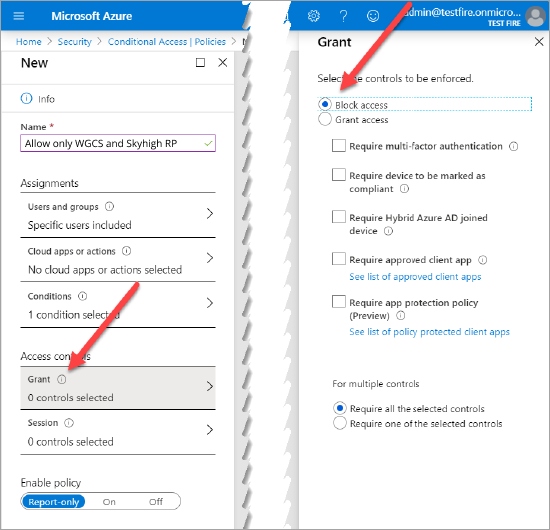
- To enable the policy, click On.
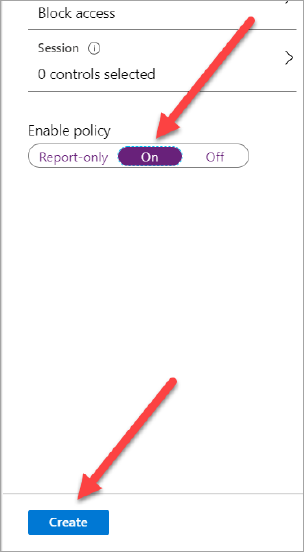
- Click Create.
If you get an error when enabling the proxy due to these two reasons, then do the following:
- Either no IP address is assigned to your tenant: If you have never tried to enable proxy in this tenant before, then you need to create a support ticket.
- Any duplicate configuration present: If you have successfully enabled proxy at some point in the past, then you need to rename your service instance to resolve a potential duplicate configuration.
Step 2: Configure Skyhigh CASB Reverse Proxy
This configuration allows you to create a proxy URL for Office 365 in Skyhigh CASB. The integration with the identity provider (Azure AD) is not supported, so this is not considered to be a complete reverse proxy configuration.
To configure the reverse proxy, perform the following activities:
- Login to Skyhigh CASB and go to Settings > Service Management.
- Click Add Service Instance.
- Click Microsoft Office 365 and OneDrive and enter a name for your service instance.
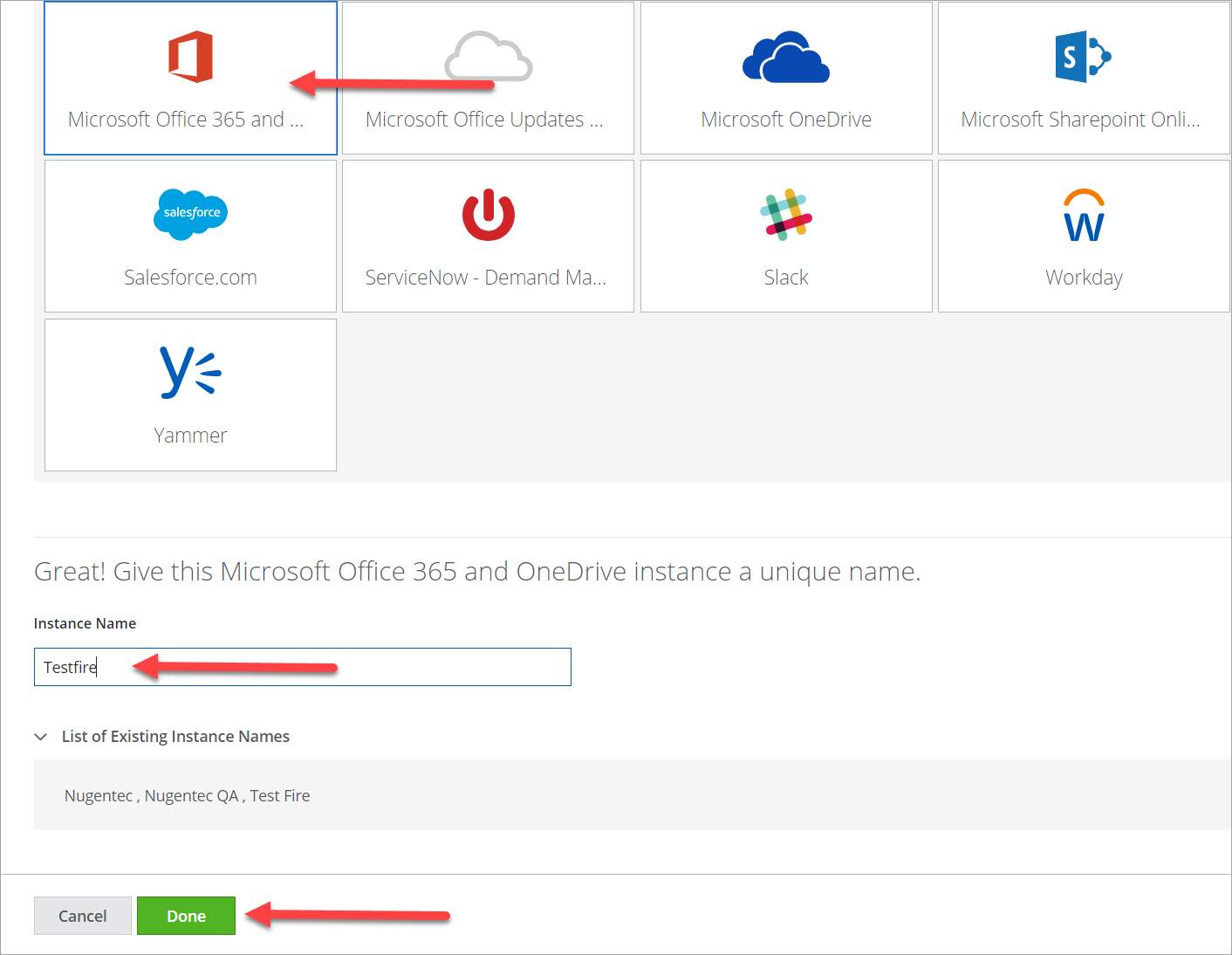
- Click Done.
- On the Service Management page, expand Microsoft Office 365 and OneDrive and click your service instance name.
- Go to Setup and click Get Started.
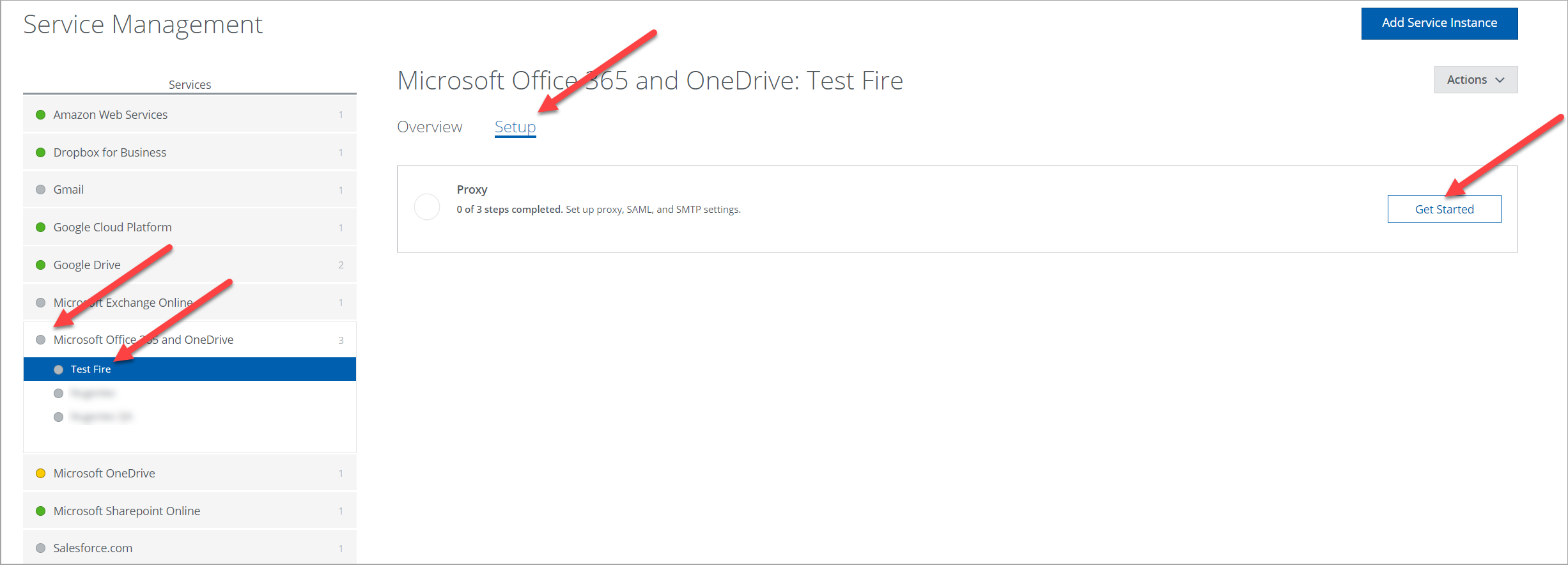
- Under Configure proxy, click Configure.
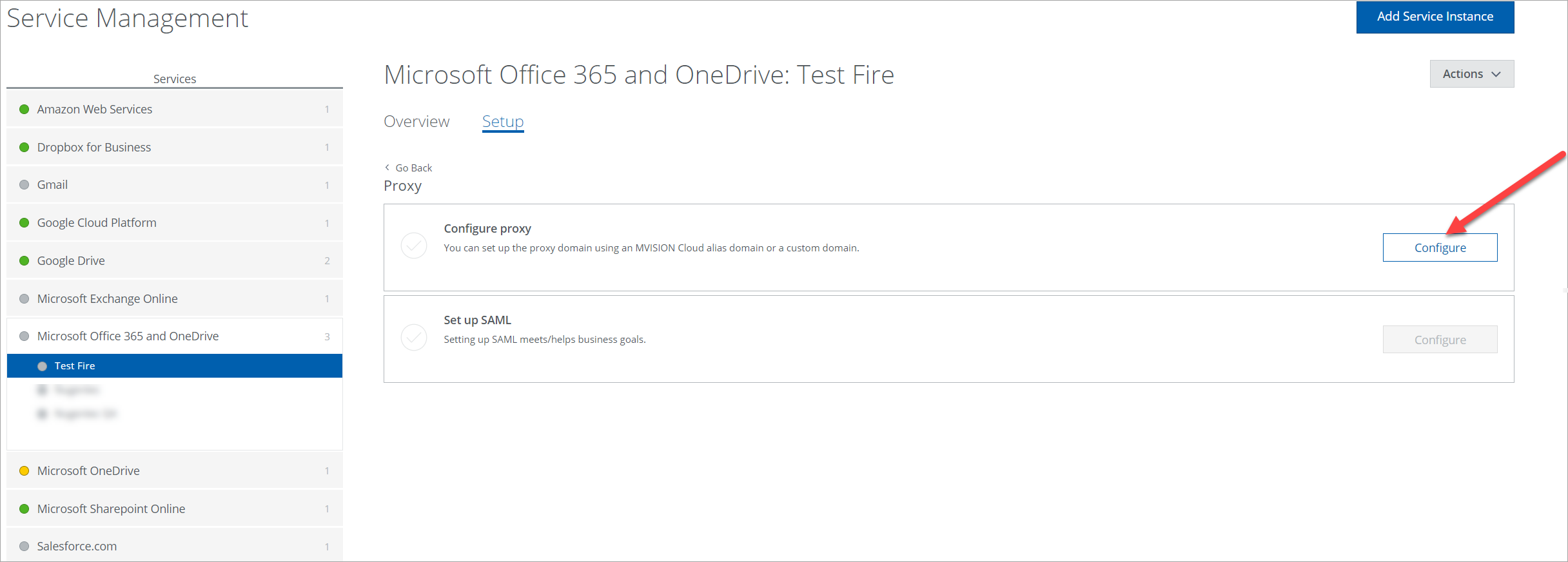
- Under Select Proxy Location, set the Proxy Location as Skyhigh CASB and click Next.
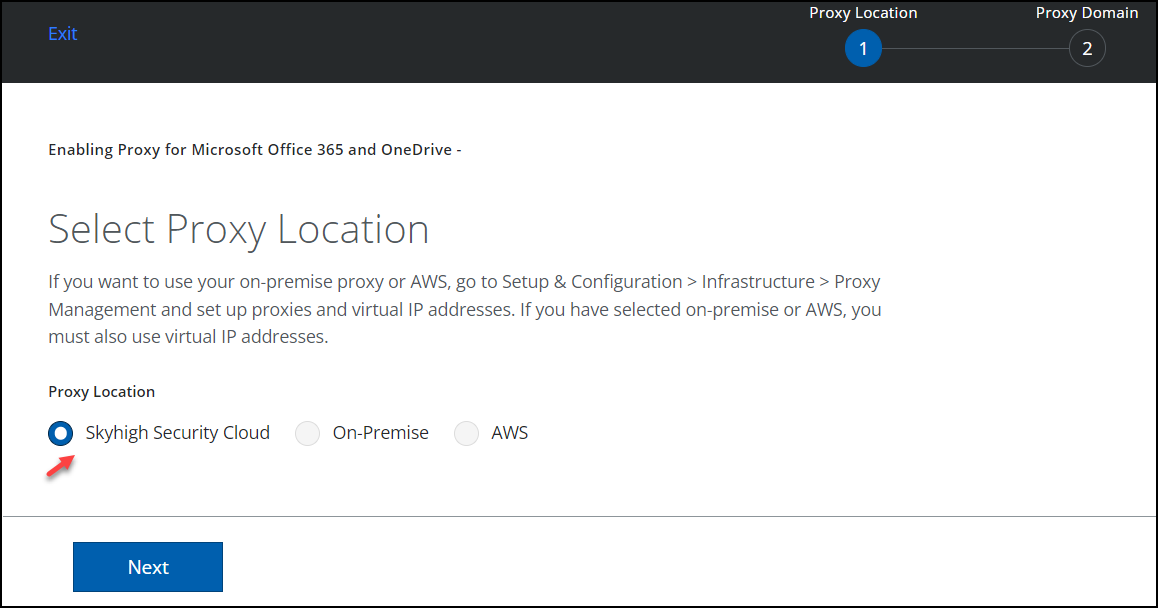
- Under Set up Proxy Domain, configure the following:
- Set the Host Name as portal.office.com
- Select Proxy Domain as {{product}} Aliased Domain and click Next.
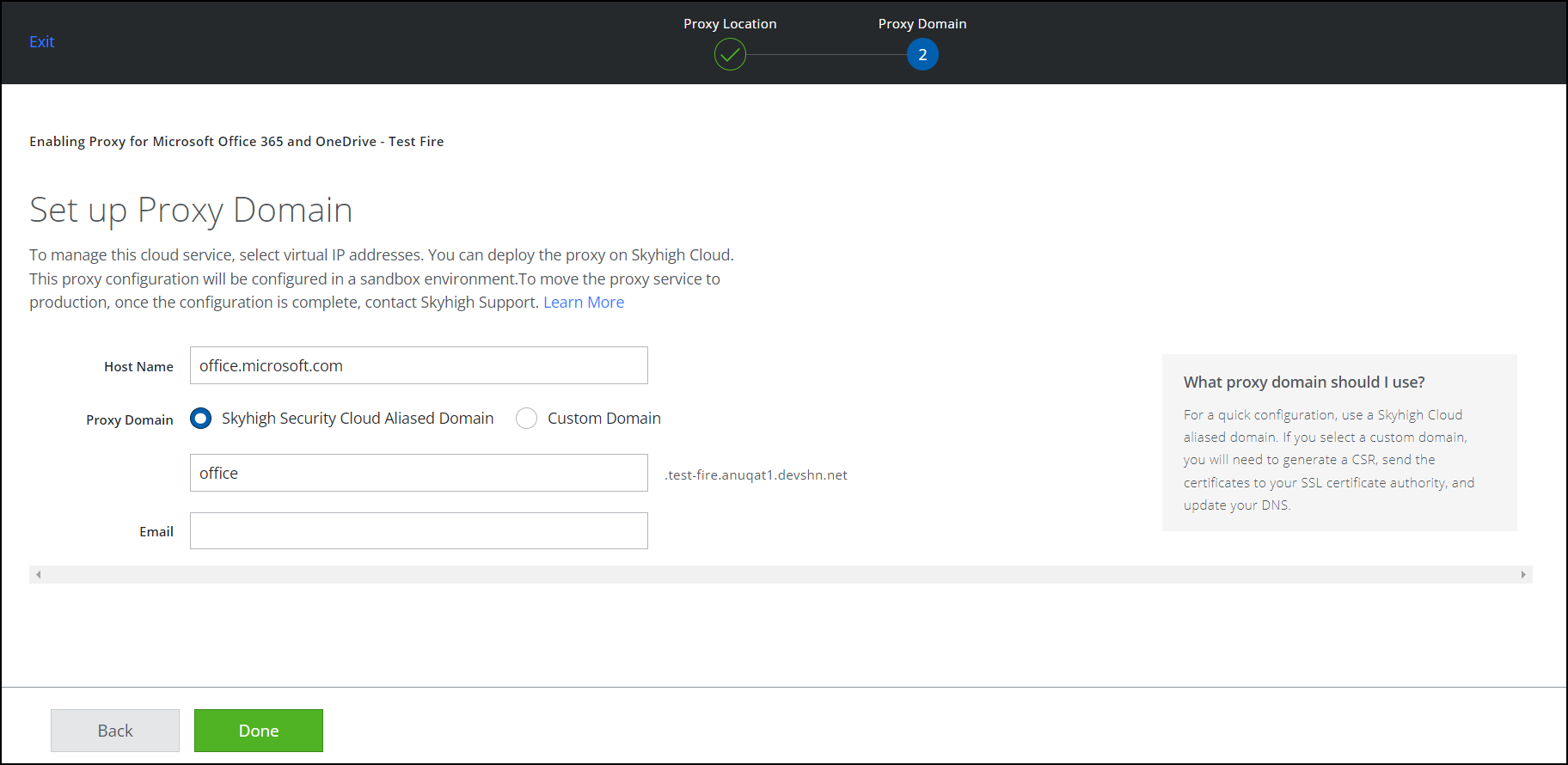
- Click Done.
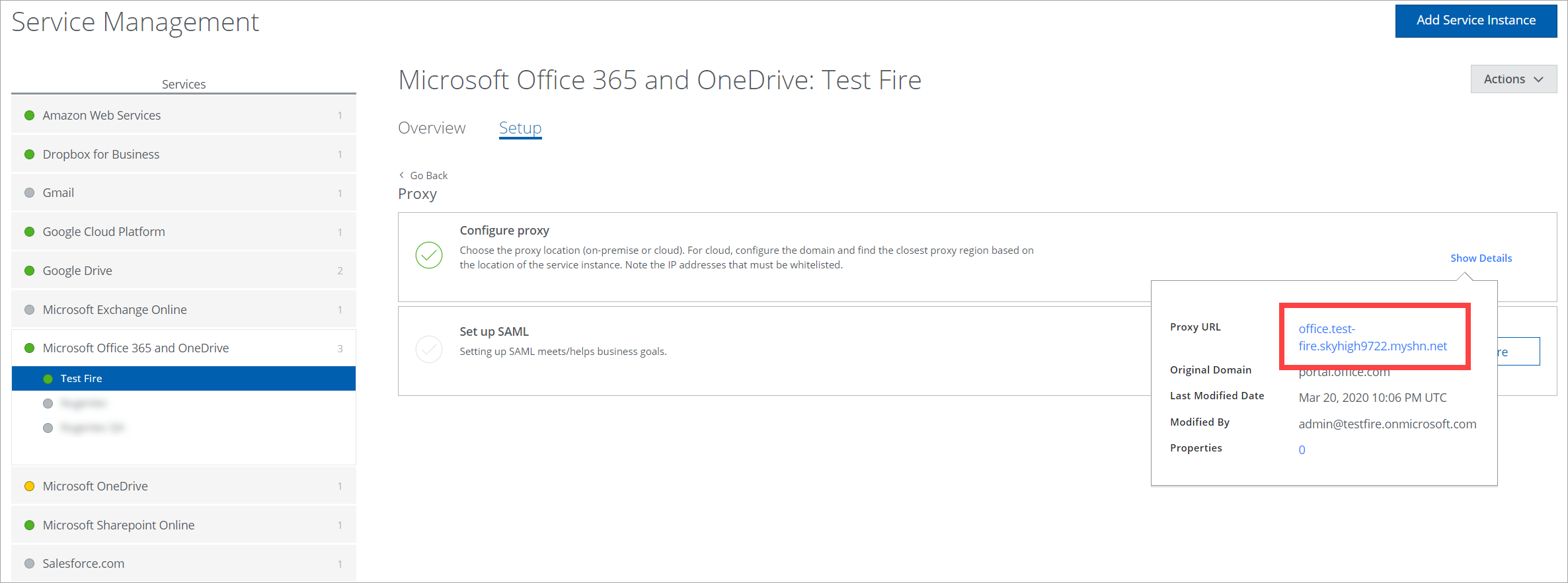
- Once the proxy is enabled, click Show Details to find the Proxy URL. You need this URL in the Validate Unmanaged Device Proxy Login section.
Step 3: Configure Skyhigh CASB Access Policy
This configuration manages proxy traffic from both managed and unmanaged devices.
To configure cloud access policy, perform the following activities:
- Login to Skyhigh CASB and configure device management through certificates. For details, see Manage Devices using Certificates.
- Go to Policy > Access Control > Access Policies and click Create Policy.
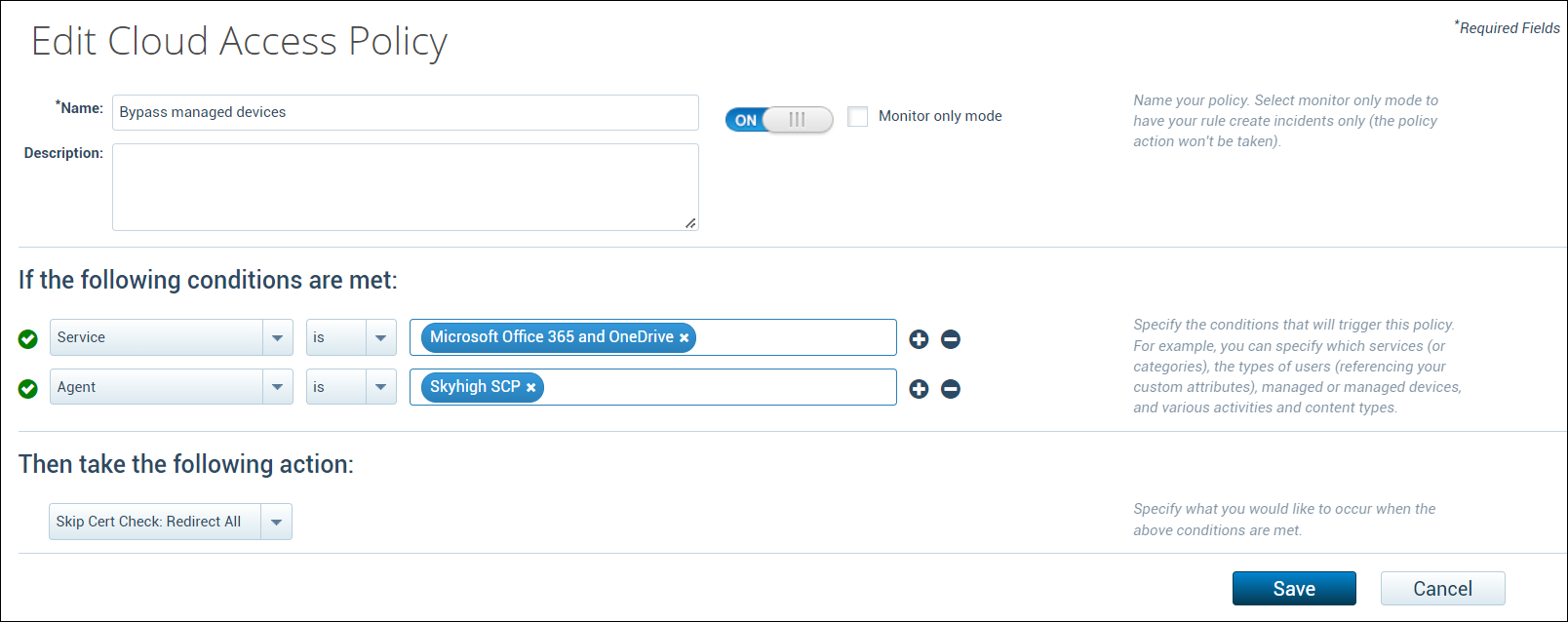
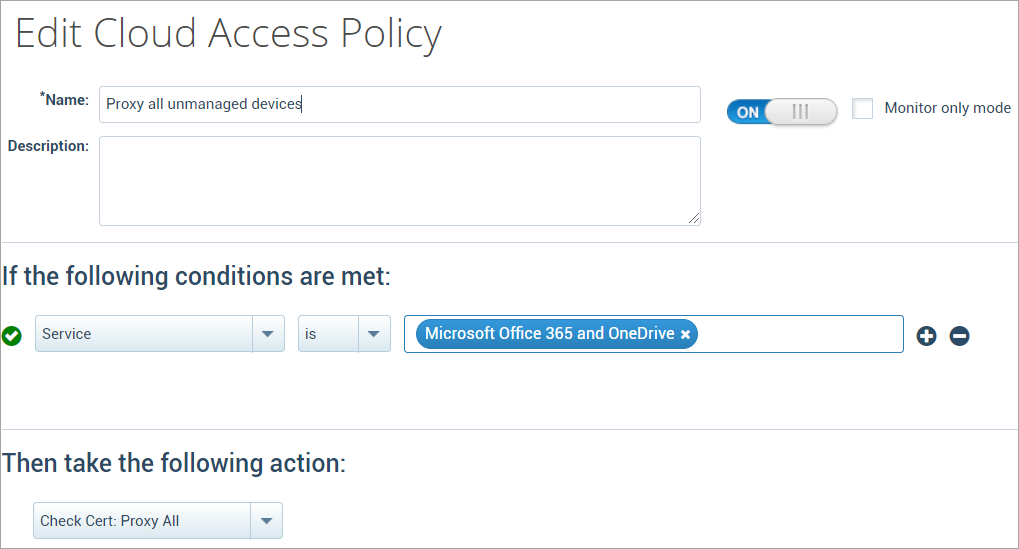
- Create a new cloud access policy to redirect managed devices directly to Office 365 using the following configuration.
- Under conditions, select:
- Service: is Microsoft Office 365 and OneDrive.
- Agent: is Skyhigh Security SCP.
- Under action, select Skip Cert Check: Redirect All.
- Click Save.
- Under conditions, select:
- Create another new cloud access policy to proxy the traffic from unmanaged devices to Office 365 using the following configuration.
- Under conditions, select Service: is Microsoft Office 365 and OneDrive.
- Under action, select Cert Check: Proxy All.
- Click Save.
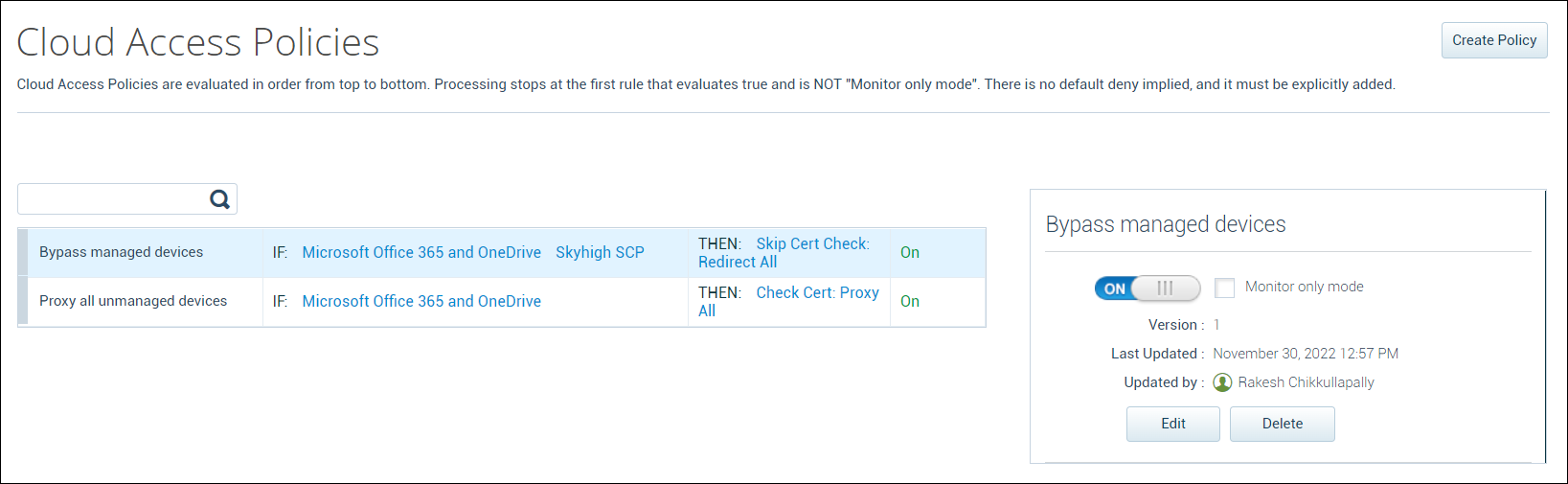
- Make sure your policies are created on the Cloud Access Policies page.
About Skyhigh Security Client Proxy (SCP) Configuration
In general, the SCP Policy can be configured in multiple interfaces. In this case, SCP bypasses any Microsoft domains or hosts such as office.com, office365.com, or sharepoint.com. This way, Skyhigh Security is not sending proxy traffic to Office 365 and not violating Microsoft's service agreement that would affect the user experience. However, only the login URL (login.microsoftonline.com) is proxied to meet the Conditional Access policy requirements.
About Vanity URL Configuration
The proxy URL provided by Skyhigh CASB is not user-friendly. So a vanity URL helps users remember it and shares information on how to log in to Office 365.
The user on the unmanaged device directly logs in to Office 365 (office.com) and gets a blocked page from Azure AD Conditional Access that does not specify why the user was blocked or the solution to fix it. A vanity URL helps to provide the correct process for users. For example, remembering to login to office.skyhighsecurity.com is easier than office.skyhighsecurityprod.skyhighsecurityprod.myshn.net.
There are many ways to configure a vanity URL in the user’s domain, but you can only do it on the user's side. Remember, it cannot be configured with a customer name (CNAME) record, but requires URL redirect to the Skyhigh CASB proxy URL. For example, office.testfire.me should provide a redirect to office.testfire.skyhigh9722.myshn.net.
The steps to configure Reverse Proxy for Office 365 via Azure AD is completed.
Step 4: Validate Reverse Proxy for Office 365 via Azure AD
To verify the outcome of the reverse proxy for Office 365 via Azure AD, perform the following validation scenarios:
Validate Unmanaged Device Direct Login
SCP is not installed for Unmanaged Device direct login.
- Login to Office 365 URL (login.microsoftonline.com).
- You are redirected to the Microsoft block page.
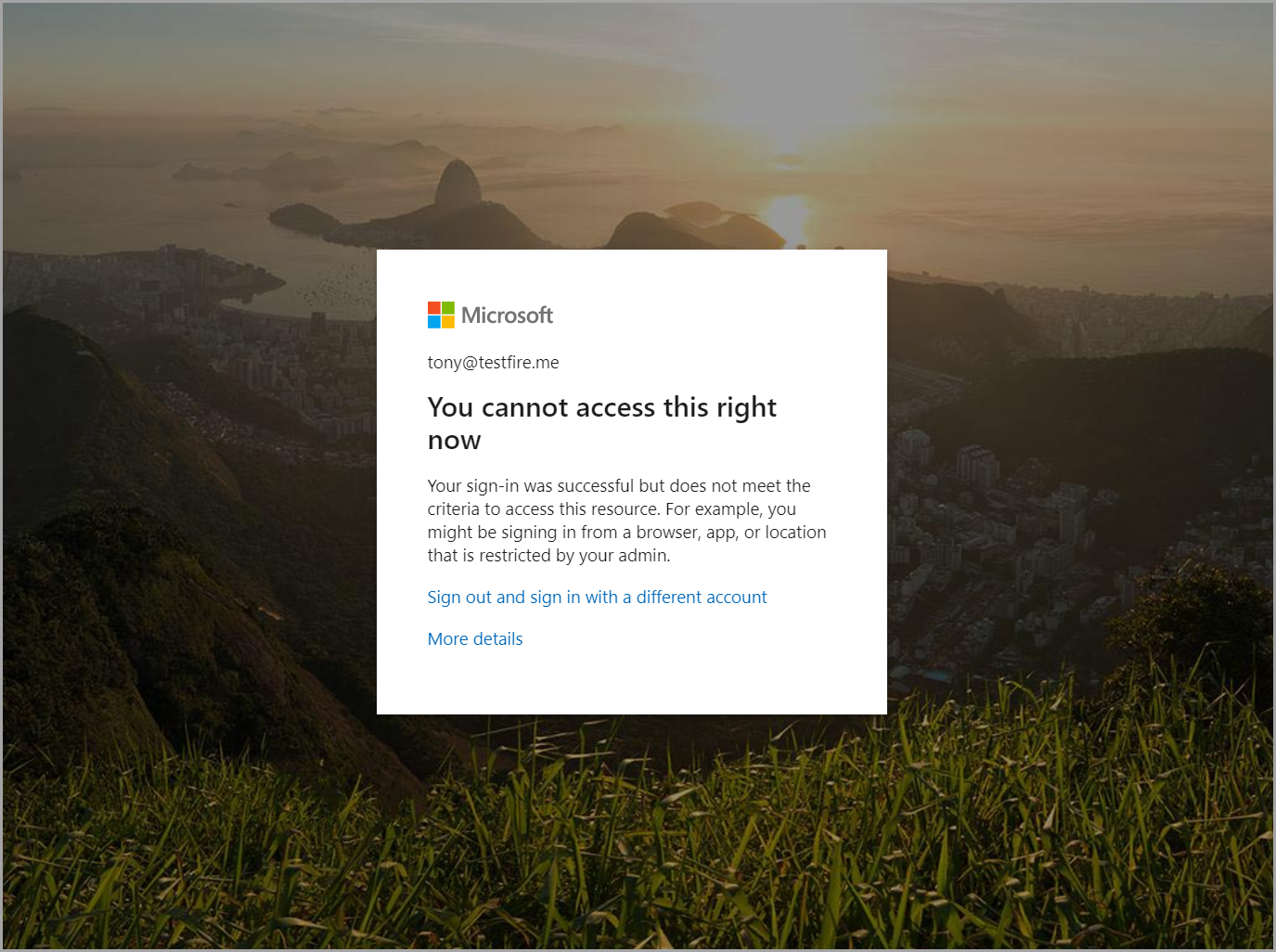
This shows that you have successfully configured Conditional Access in Azure AD.
Validate Unmanaged Device Proxy Login
SCP is not installed for Unmanaged Device direct login.
- Login to Office 365 either through the proxy URL obtained in the Skyhigh CASB Reverse proxy or via the Vanity URL.
- You are redirected successfully to Office 365 via proxy URL.
This shows that you have successfully configured Skyhigh CASB Access policy and Reverse Proxy.
Validate Managed Device Login
SCP is installed for Managed Devices, and it redirects Office 365 to WCGS or
Callstack:
at (Skyhigh_CASB/06_Skyhigh_CASB_Sanctioned_Applications/01_Skyhigh_CASB_Native_Sanctioned_Apps/Skyhigh_CASB_for_Office_365/Reverse_Proxy_for_Office_365_via_Azure_AD), /content/body/div[7]/div[4]/div/p/span, line 1, column 1
- Login to Office 365 URL (login.microsoftonline.com) or the proxy URL obtained in the Skyhigh CASB Reverse proxy or the Vanity URL.
- You are redirected successfully to Office 365.
This shows that you have successfully configured Managed Device login via Azure AD.
Solution for Non Skyhigh CASB Forward Proxy Users
If you are not using Skyhigh CASB's WCGS or Skyhigh Security Service Edge (SSE) for a forward proxy, perform the following activities:
- In the Configure New Location section, replace the WGCS IP ranges with your forward proxy IP ranges or public IPs.
- In the Configure Skyhigh CASB Cloud Access Policy section, replace the condition Agent: is Skyhigh Security SCP with your forward proxy IP ranges or public IPs.
The only prerequisite is to provide predictable IP ranges, and they should determine all the traffic from managed devices. Managed devices should pass from these known IPs. This forward proxy solution is for your public egress IP ranges.
