Configure an Egress IP Address for Use in Exiting Secure Web Gateway
When running Secure Web Gateway, you want to have control over how web traffic is routed. This includes the use of a particular IP address that web traffic should be routed through as egress IP address when exiting Secure Web Gateway.
NOTE: The feature that is documented in the following is only available to a limited number of our customers.
Using a particular egress IP address is easily possible in an on-prem configuration, but causes a problem for the multi-tenant cloud solution Secure Web Gateway offers when running under Security Service Edge (SSE). IP addresses are shared across different users here, so routing options are limited.
The problem arises when a destination expects a connection to a particular IP address, but under SSE, Secure Web Gateway sends an IP address out of a pool of shared IP addresses using a GRM-based routing scheme.
You can, however, still configure the following:
-
Use of a particular IP address as your egress IP address. This IP address is preconfigured for you on several major Points of Presence (PoPs). When Secure Web Gateway is run on one of these PoPs, web traffic will exit it using the preconfigured IP address.
To enable use of this IP address, you create a rule with an event that enforces its use. Because it is preconfigured, you cannot specify this address on your own. - What to do when the configured IP address is not available. You can block web traffic then to prevent it from exiting or configure the use of a shared IP address.
Proceed as follows:
-
On the user interface for Secure Web Gateway, select Policy > Web Policy > Policy.
-
On the policy tree in the navigation panel on the left, select a rule set that will include the rule with the event for using the configured egress IP address. Select, for example, the SAML Authentication rule set in the SAML Authentication branch of the policy tree.
You can also create a separate rule set to include this rule. -
In the Preset Rules line, click Add Custom Rules, then select Via Rule Builder from the drop-down menu that opens.
Options for creating a rule appear after the last of the preset rules. -
Work with these options as follows to create a rule that, in addition to serving a particular purpose, enforces the use of a particular IP address to egress.
a. Under Name, enter an appropriate rule name, for example, Use egress IP address.
b. Under Criteria, select All Traffic. No operator or value is required then.
c. Click Add Event and select Egress by Custom IP Address from the list on the side panel that opens, then click Done.
Your rule will look like this now:

To enable it, make sure the toggle button at the very right is set to show a green field. -
Create a rule to specify what should happen if your configured egress IP address is not available. Insert this rule next to the rule that enforces the use of this address. Work with the Rule Builder options as follows:
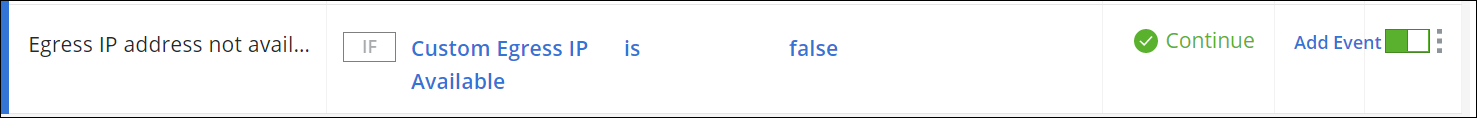
a. Under Name, type an appropriate rule name, for example, Egress IP address not available.
b. Under Criteria, select Custom Egress IP Available. Under Operator, select is, and under Value select false.
c. Under Action, select one of the following, depending on how you want to handle it:-
Block request — Web traffic is blocked and thus prevented from exiting. Click Select Template below the action name to select a block page that is sent to the user with information about the blocking.
-
Continue — Web traffic is allowed to exit using a shared IP address.
-
The rule will look like this if you have chosen to let web traffic exit through a shared IP address.
You have now configured an IP address for use as your egress IP address. If this IP address is not available, web traffic will be handled according to what you configured for this situation.

