Anti-Malware — Block Access to Infected Web Objects
You can block access to web objects, for example, domains or hosts, if these prove to be infected by viruses or other malware. You can also configure exceptions. For this purpose, you fill these objects in lists for use by the anti-malware filtering rules.
When a request for web access or a response to a request is received on Secure Web Gateway, the web object that is involved, for example, a file, is scanned. If an infection is found, the request or response is blocked. Timeouts are implemented for the scanning process, which you cannot configure, see Timeouts for Malware Scanning.
If the web object is on one of the lists with exceptions, anti-malware filtering is skipped, which means no scanning is performed.
- On the user interface for Secure Web Gateway, select Policy > Web Policy > Policy.
-
On the rule set tree in the navigation panel, expand Threat Protection and select Anti-Malware.
The selected rule set appears in the configuration area on the right. -
Configure when this rule set should apply.
-
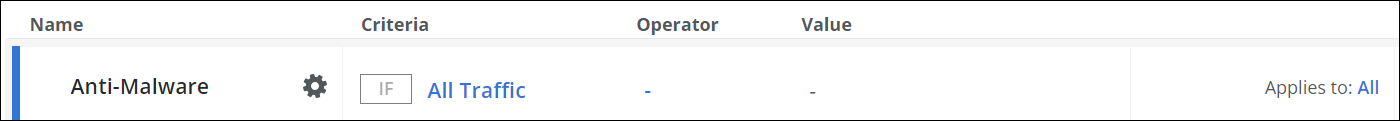
Under Criteria, leave the default All Traffic, as you want the rules in this rule set to apply to all types web traffic.
- Next to Applies to, leave the default All, as you want the rules in this rule set to be processed in all cycles of web filtering on Secure Web Gateway.
-
-
Click the settings icon to configure settings for this rule set in a panel that is inserted on the right. The settings that are currently in use are shown as selected on the panel.
When configuring these settings, you can, for example, choose whether to run the Gateway Anti-Malware (GAM) engine together with the Anti-Malware engine when scanning web objects or use the latter alone.
You can also set a threshold value for the likelihood of a scanned web object to be malicious that will lead to blocking access to it. -
Configure the rules that are preset in this rule set as needed. They are shown under Preset Rules.
a. Enable or disable any of these rules. Use the toggle checkbox at the beginning of the row for a rule to do this.
There are two preset rules that allow you to skip malware filtering for web objects of the following types:-
User agents
-
Domains, hosts, and URLs

-
b. Enter user agents, domains and other web objects in lists for use by these rules. Click the three dots at the end
of the line with a rule and work with the options for list handling that are provided.
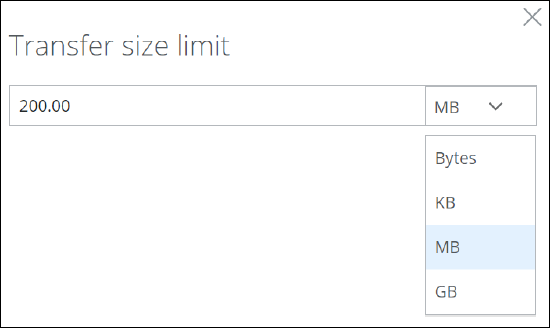
c. Configure the rule for skipping malware filtering if a web object is to be accessed that exceeds a given size.
.
Click the rule name to open a panel on the right where you can set this size.
d. Configure the rule that skips malware filtering for access to Private Applications.
You need a Private Access license to work with this rule. With this license, you can add applications that malware
filtering should be skipped for to a list.
A window informs you about the license requirement if you click the question mark next to the rule. Contact Skyhigh
Security support for more information.
You can also create rules of your own and add them to this rule set. Click the three dots at the end of the top row and select the option for creating a new rule from the drop-down menu.
This menu also includes an option for reviewing the underlying code for a rule set.
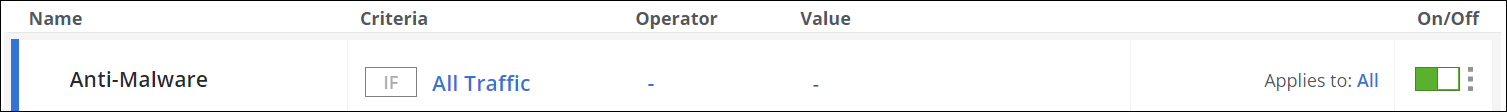
To enable or disable the complete rule set, use the On/Off toggle.
You have now configured the process that is performed on Secure Web Gateway for anti-malware filtering.
