Risky Web — Use Browser Isolation for Websites Considered a Risk
You can use Remote Browser Isolation (RBI) when allowing a user's request to access a website is considered a risk. You can also configure exceptions and other settings.
The web security functions that are implemented under Secure Web Gateway determine whether access to a website is considered a risk.
Risky Web based browser isolation primarily evaluates a website based on its reputation and category. Skyhigh maintains, continuously reassesses and updates the URL database accordingly based on evolving risk factors.
To suggest any URL for categorization and reputation, you can submit the request. For more details, see Submit URL for Categorization and Reputation.
If a website is considered a risk at a given point in time, it does not mean that this evaluation is to remain forever. On the other hand, a website that is not considered a risk now might be considered one later.
This is because websites can change over time regarding their maliciousness. Also, the risk algorithm used to rate websites is continually getting better.
- On the user interface for Secure Web Gateway, select Policy > Web Policy > Policy.
-
From the policy tree in the navigation panel, select Browser Isolation > Risky Web.
The selected rule set appears in the configuration area on the right. -
Configure when this rule set should apply.
-
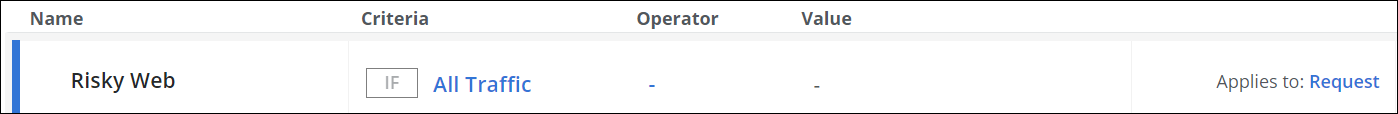
Under Criteria, leave the default All Traffic, as you want the rules in this rule set to apply to all web traffic.
- Next to Applies to, leave the default Request, as you want the rules in this rule set to be processed in the request cycle of web filtering on Secure Web Gateway.
-
-
To let some requests skip the remainder of this rule set, which means the browser isolation rules are not processed for these requests, configure lists for the skipping rules that are preset here. They are shown under Preset Rules.
You can configure entries for domains, IP addresses, URL categories, and reputation risk levels in these lists.
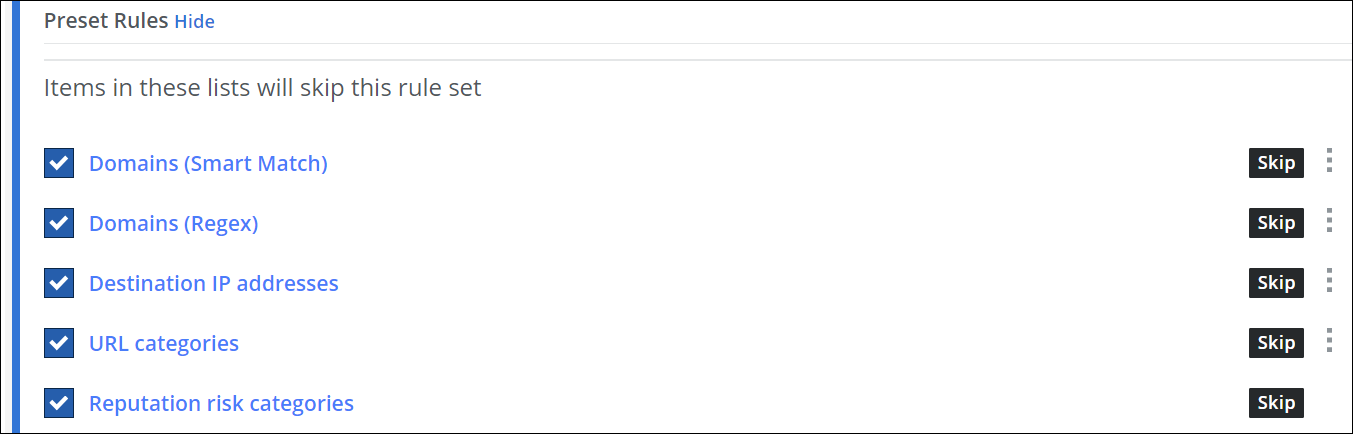
Click the three dots at the end of the row for a rule and work with the options for list handling that are provided. Or click the name of the list for a rule, for example, Domains (Smart Match), to work with these options.
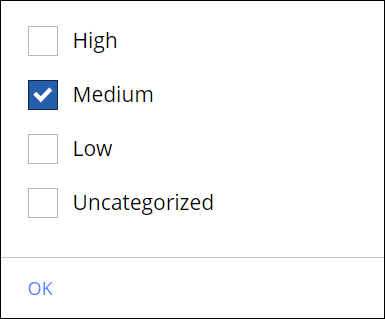
For the reputation risk levels, click the rule name and select a level, for example, Medium.
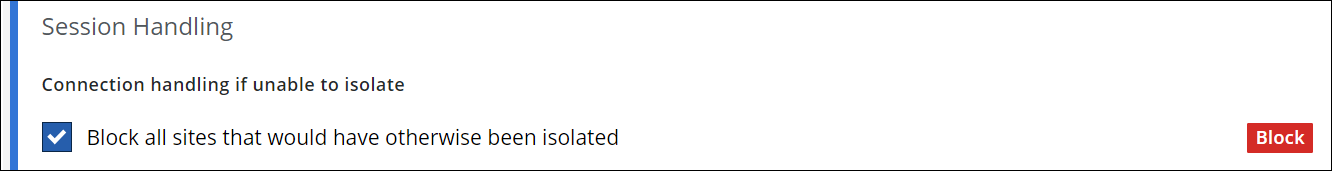
- Under Session Handling, configure what to do when browser isolation cannot be applied.
Leave the preset Block all sites that would otherwise have been isolated rule enabled or disable it. If you disable it, users can access these websites without browser isolation.
-
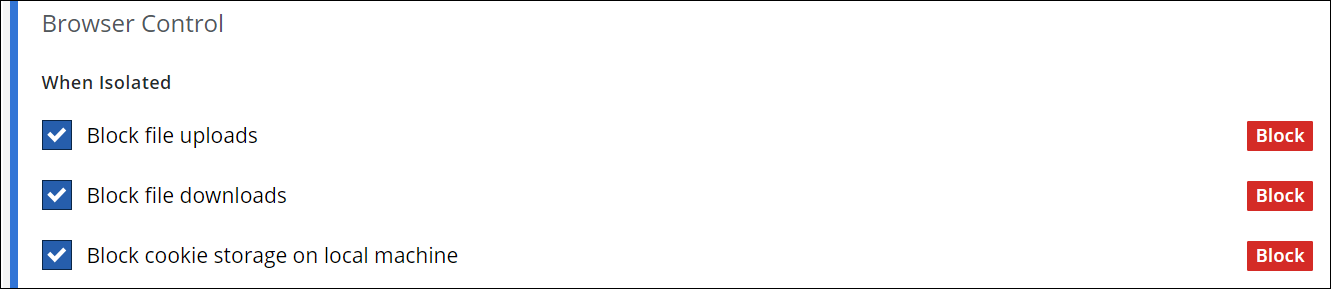
Under Browser Control, configure how to handle file uploads and downloads as well as cookie storage on a user's system when browser isolation is applied.
-
Block or allow file uploads.
-
Block or allow file downloads.
- Block or allow storing cookies on a user's system.
-
-
Under Browser Settings, configure whether browser isolation is indicated in a user’s browser by a colored border and a message, and disable the indicator pop-up as needed.

-
Disable browser isolation loading experience
A loading message appears whenever you browse a website to enhance your browsing and webpage viewing experience. This message informs you that the webpage will load shortly. If disabled, Skyhigh provides an indefinite loading bar at the top, allowing you to stay informed while the page loads.
-
Select Disable Browser isolation indicator to hide the visible indicator around the webpage while keeping browser isolation active.
-
A lime green indicator (2 pixels) appears around the web page to indicate that browser isolation is protecting your web browsing.
You can customize the browser isolation indicator with a preferred color and width (up to 5 pixels) that will be displayed around a web page in the end user's browser when full browser isolation is applied. Additionally, you can use the Preview option to view how the browser session appears with the selected border settings. The presence of the browser indicator signifies that browser isolation is active and safeguarding your web browsing -
Select Disable Browser isolation pop-up to disable this pop-up as needed.
A pop-up message appears in the user's browser by default at the beginning of a session when full browser isolation is applied to it. It informs the user that this web security measure is being taken.
If you do not select this option, the pop-up message appears to indicate that browser isolation is applied. -
Select Customize Branding of RBI popup prompts to customize the brand as needed.
The headers and descriptions in the RBI popup prompts use Skyhigh Remote Browser Isolation as their default branding.
You can select Customize Branding of RBI popup prompts to customize the headers and descriptions in the popup prompts.

The custom name must be between 3 and 60 characters long. You can click Restore to Default to reset it to the default name: Skyhigh Remote Browser Isolation.
You can also view a sample to see how the popup will appear in the isolated window.

-
Select Disable Skyhigh logo near the browser address bar to remove the logo as needed.
By default, the Skyhigh logo is displayed near the browser address bar. To disable the logo, you must enable the check box.
-
Select Enable Webpage as Read-only to set the webpage to read-only mode when required.
By default, the webpage is in edit mode and not read-only.
NOTE: The read-only functionality should be executed within the Web.Response trigger. However, the current version of the ruleset does not support this policy execution. Therefore, your admin must manually add the Web.Response trigger to existing policies for Risky Isolation. -
Select Disable RBI Password Manager to hide the RBI password manager pop-up allowing you to store the login credentials
By default, the RBI Password Manager is enabled, allowing you to store login credentials for easy access in future sessions. Site administrators can disable this feature, which will also delete any passwords stored by users in existing sessions. When the feature is disabled, isolated sites will no longer prompt you to save passwords. - Select Block Webpage Printing to prevent the page from being printed and to block screen capture of the webpage in Windows.
By default, printing is allowed. To block printing (Ctrl+P, Save as PDF) and screen capture of webpages (F10 on Windows), enable the checkbox.
If printing is blocked, you will see one of two block notifications depending on the type of block:- When printing from a webpage is blocked, the block message displayed is: Printing has been blocked by policy.
- When the print screen function is blocked, the block message displayed is: Webpage Printing has been blocked by policy.
-
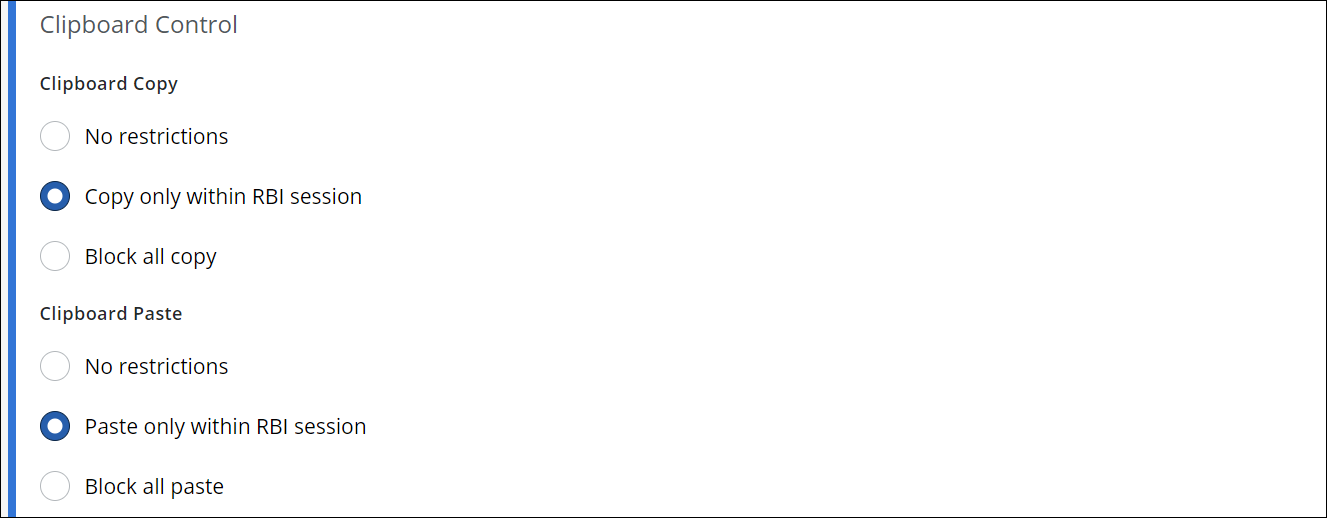
Under Clipboard Control, configure how to handle copying and pasting clipboard data when browser isolation is applied.
-
Configure copying: Impose no restrictions on it, allow it only within the same browser isolation session, or block it completely.
-
Configure pasting: Impose no restrictions on it, allow it only within the same browser isolation session, or block it completely.
-
You have now configured browser isolation for websites that are considered a risk, including exceptions and other settings.
Submit URL for Categorization and Reputation
To submit a URL for categorization and reputation, please follow these steps:
- Click Check Single URL to submit the URL.
- Select the product from the dropdown menu.
- Enter the URL you want to categorize.
- Click Check URL.
- URL categorization and reputation details will appear if already exist in our database. If you wish to update the categorization and reputation you can optionally suggest a categorization along with the comment.
- Click Submit URL for Review.
Skyhigh team will review the site and its risk properties to determine its category and reputation in 3-5 business days.
You can track the status of your submission. Once the URL is categorized, the site's category and reputation will be displayed. These may change based on the site's content. If you disagree with the assigned category, you can submit the URL for review along with your suggested category.
