Adaptive Access Control in Secure Web Gateway (SWG)
Overview
Adaptive access controls in Skyhigh Secure Web Gateway allow your organization's data to be protected by controlling access to websites and services based on user, device identity, locations, processes, applications, tags, etc.
Enforce Adaptive Policies based on Device and User risk
Configure your web policy to Adaptively control and secure access to applications. A web policy includes rules that specify criteria based on the application group, user name, user group, device profile, and location.
Configure Web Policy Rules
Configure the policy rules to enforce controlled access to websites and URLs. You can create web policy rules by applying Criteria, Operator, Value, and Actions. You can define up to five levels of nesting within a parent rule. You will see an error if you don't enter the rule name or when the rule name exceeds 200 characters. The nested rule can contain other nested rules, resulting in a hierarchy of rules.
SWG applies the access policy rules using the first-match principle and runs from top to down. The rule set evaluates to true or false based on the criteria, value, and action specified in each rule. So make sure to provide valid inputs in all these fields. Rules are triggered when all their conditions are evaluated to be true. Within a parent rule, you can use drag and drop to move a rule from one level to another level.
Note: Before creating a web policy rule, you should first configure the device profiles.
Configure Device Profile
SWG continuously assess the security posture of the connecting device. The connecting device can be enterprise-owned, a personal computer, a mobile device, or a BYOD device. There are two methods to configure Device Profile:
Create a Web Policy
You can create a rule set of your own by specifying values for each of the elements that are included in a rule set. For details, see Create a Rule Set.
To import a rule set from the library and add it to the existing rule sets. The rule set can serve as a branch of the policy tree, which means it embeds one or more other rule sets. Or it can be an embedded rule set. For details, see Import a Rule Set from the Library.
Create Custom rules with rule builder. For details, see Create a Rule with the Rule Builder.
Policy Criteria to Enforce Device and User Risk Restrictions
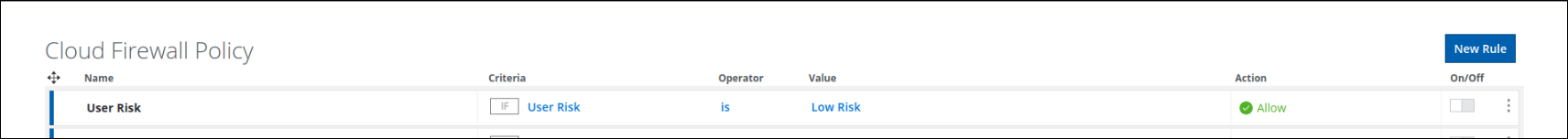
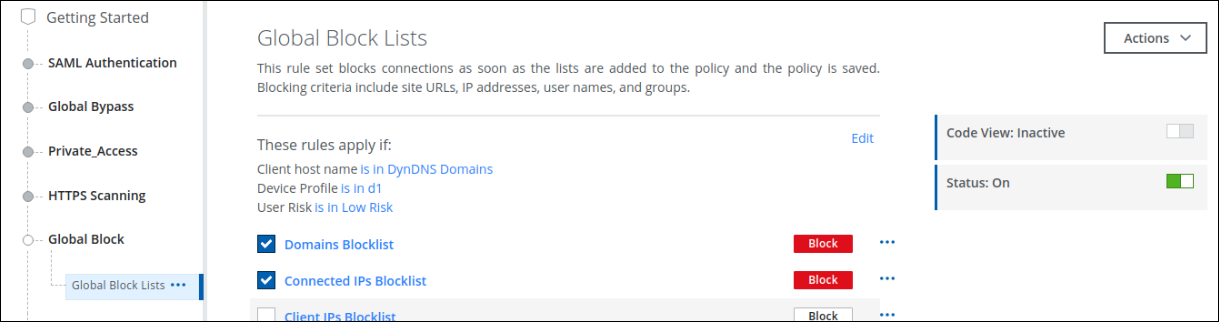
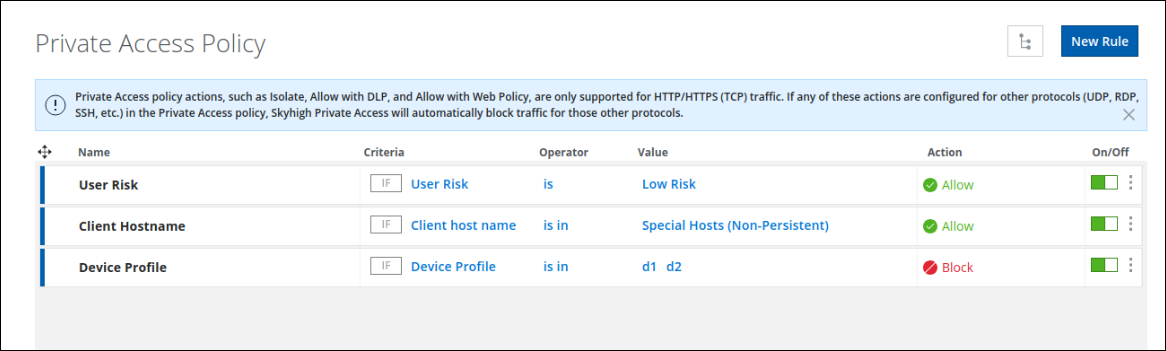
We have new criteria such as User Risk, Device Profile, and Client Hostname in the Web Policy builder to allow or block access.
- User Risk - In CASB, depending on the user's behavioral pattern, the user is marked as a high-risk, medium-risk user, and lower-risk user.
- Device Profile - You can configure different device profiles. For details, see Configure Device Profiles.
- Client Hostname - Host name of the end user.
Configuring Policies based on User Risk, Device Profile, and Client Hostname
Web Policy Builder
DLP Additional Responses
Private Access
Cloud Firewall