Client Proxy Metadata
When the Client Proxy software redirects HTTP/HTTPS traffic, it adds metadata to the requests.
Other products, such as Web Gateway and Skyhigh Security WGCS, use the metadata (for example, group membership) when applying web protection policies.
- Authentication tokens — Tokens containing identity information about the user making the web request.
- Authentication version — Version of the metadata that Client Proxy is sharing.
- Client IP address — IP address of the endpoint where the traffic originated.
- Original destination IP address — Saved IP address of the server where the traffic is destined.
- Customer ID — Uniquely identifies the customer's organization.
- User ID — Uniquely identifies the user making the web request.
- User groups — Names of any groups where the user is a member.
- Tenant ID — ID shared by the nodes in a cluster (Trellix ePO Cloud or Trellix ePO).
- Process name — Name of the process that generates traffic.
- Process Executable Path — Path of the process that generates traffic.
- Timestamp — Timestamp when the request is generated.
- System Information — System information such as host operating system name (Windows, Mac), local time (seconds since 1/1/1970), Mac address, system name, local time, process uptime, time zone, user language and Client Proxy policy name. For the endpoints running Windows, it also displays the process details (uptime, absolute path, hash, signing information), and antivirus details (antivirus installed, its status, and whether it is up to date).
When you integrate CrowdStrike with Skyhigh Private Access, along with the above-mentioned metadata, the system will display the following system header:
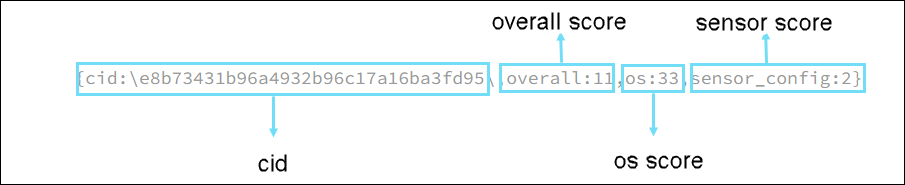
- CrowdStrike Key — The CrowdStrike key includes the customer ID (cid) and the three individual scores (overall score, os score , and sensor score) that are sent to the SWG for evaluation of the CrowdStrike device profiles.
- CrowdStrike Score — Security score from 1 to 100 for each host.
- OS, Sensor, and Overall scores — The CrowdStrike scores that are specific to unique configurations of the host environment. A higher score indicates a better security posture of the host.
For example,
- Matched Profile — The matched profiles key provides the list of native Skyhigh device profiles that have successfully passed device risk assessment (DRA) for parameter configuration on the client machine.
- If device profile matches, it shows the device profile names as a list. All the matching attributes of the device profile are shown, and the format is
<device_profile1,device_profile2>. If no device profile matches, it showsNone. - Process — Process name or the path that runs on the device. When the process is validated, the format is
all_test_231213.isrunning. - File path — File path found on the users' device.
When there is a valid file, the format is<dp_name>.isfound, here, dp_name is the device profile name. - Active Directory domain — Name of the active directory domain associated with the device.
- Company CA certificate Validity — Company CA certificate present on the client.
The format is<dp_name>.companycacert.isvalid, here, dp_name is the device profile name, companycert is the company certificate. - Client CA certificate validity— Client CA certificate present on the client.
The format is<dp_name>.clientcacert.isvalid, here, dp_name is the device profile name, clientcert is the client certificate.
- If device profile matches, it shows the device profile names as a list. All the matching attributes of the device profile are shown, and the format is
