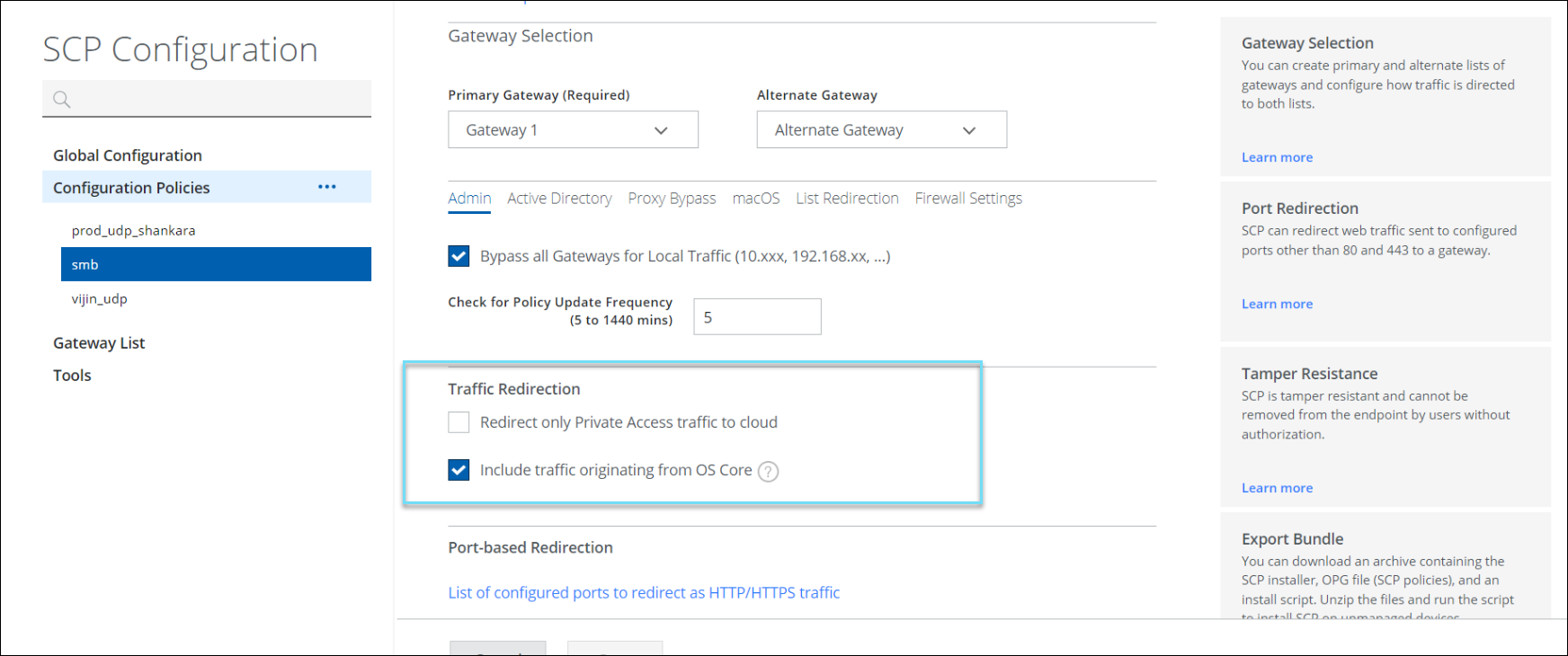
Traffic Redirection
Redirect only Private Access Traffic to Cloud
You can redirect only selected traffic (traffic from the private application) and bypass other internet traffic. By default, this option is enabled for private access only policies. The traffic destined for the Internet or the Web is not logged or processed but will be accessed directly.
- Go to Settings > Infrastructure > Client Proxy Management.
- In the policy tree, select Configuration Policies.
- Do one of the following:
- Click the highlighted menu icon (...) next to the branch, then select Create New Policy.
- Select a policy from the policy tree.
- In the Traffic Redirection section, select the Redirect only private access traffic to cloud checkbox. You can select or uncheck this option when you have both the Skyhigh SSE and Skyhigh Private Access licenses. When you uncheck this option, all internet traffic is redirected to Skyhigh SSE, and end users can access private and public applications through web browsers.

Note:
- This option is selected by default when you have installed only the Skyhigh Private Access license. You cannot edit (disable) this checkbox.
- A warning message stating Traffic from other sources will not be redirected to the cloud is displayed when the checkbox for Redirect only private access traffic to cloud is selected.
The traffic from the private application is securely redirected to Skyhigh SSE.
You can publish saved changes to the cloud or keep working and publishing later.
Include Traffic Originating from OS Core
By default, Client Proxy bypasses traffic from the OS Core component. Enable this setting to redirect this traffic to the gateways. OS Core traffic primarily involves Windows updates, such as large file downloads, which are usually bypassed to prevent overloading the Skyhigh gateway and causing unnecessary redirection. This setting is essential for redirecting OS-generated traffic. The traffic originating from the OS core includes:
- Windows Authentication: NTLM (TCP ports 445, 135, 136), Kerberos (TCP port 88), and NetBIOS (TCP/UDP ports 137, 138, 139)
- HTTP: Windows Update service
- Print Spooler Services
- File Sharing Services: SMB (Server Message Block)
- DNS Client Services: UDP port 53
- LDAP: TCP and UDP port 389
- RPC Protocol: TCP port 593
- AD Join
NOTE: This option is applicable only for Windows.
- Go to Settings > Infrastructure > Client Proxy Management.
- In the policy tree, select Configuration Policies.
- Do one of the following:
- Click the highlighted menu icon (...) next to the branch, then select Create New Policy.
- Select a policy from the policy tree.
- In the Traffic Redirection section, select the Include traffic originating from OS Core checkbox. When you check this option, Client Proxy redirects all the traffic originating from the OS components.
The traffic from the OS component is securely redirected to Skyhigh SSE.
You can publish saved changes to the cloud or keep working and publishing later.
