Challenge-response Protocol
The challenge-response protocol allows users whose endpoints are protected by Client Proxy software to perform restricted tasks when a business need exists.
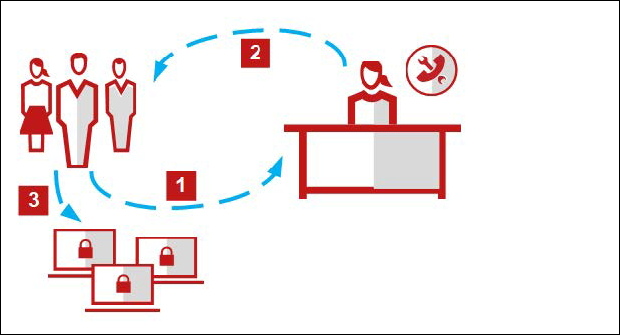
How the challenge-response protocol works
The user and administrator can communicate by email, phone, or text messaging.
- The user sends the administrator a user name and email address, a business reason for the request, the policy name and revision number, and a challenge code.
- The administrator enters the information provided in the Help Desk interface, authenticates the user, generates a release code, then sends it to the user. The release code is also called the release key, uninstall key, or bypass key.
- The user enters the release code, enabling Windows uninstall of Client Proxy or suspending policy enforcement for the time period set by the administrator.