Certificate Verification — Verify Certificates and Configure Exceptions
You can configure exceptions to the process on Secure Web Gateway for decrypting web traffic that uses secure connections under the HTTPS protocol. For this purpose, you fill web objects you want to exempt from decryption in lists for use by suitable rules.
- On the user interface for Secure Web Gateway, select Policy > Web Policy > Policy.
-
On the policy tree in the navigation panel, expand HTTPS Scanning and select Certificate Verification.
The selected rule set appears in the configuration area on the right. -
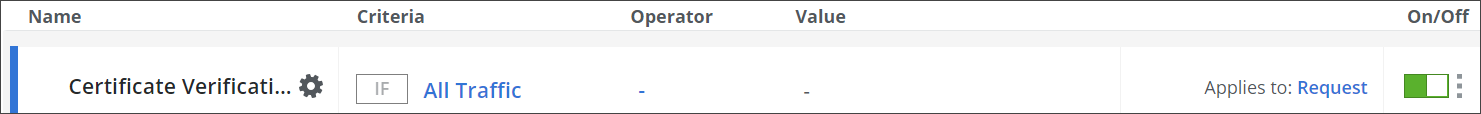
Configure when this rule set should apply.
-
Under Criteria, leave the default All traffic, as you want the rules in this rule set to apply to all types of traffic.
-
Next to Applies to, leave the default Request, as you want the rules in this rule set to be processed in the request cycle of web filtering on Secure Web Gateway.
-
-
Click the settings icon to configure settings for this rule set in a panel that is inserted on the right. The settings that are currently in use are shown as selected on the panel.
When configuring these settings, you can specify how to handle certificate chains and provide a certificate for a native browser Certificate Authority (CA). -
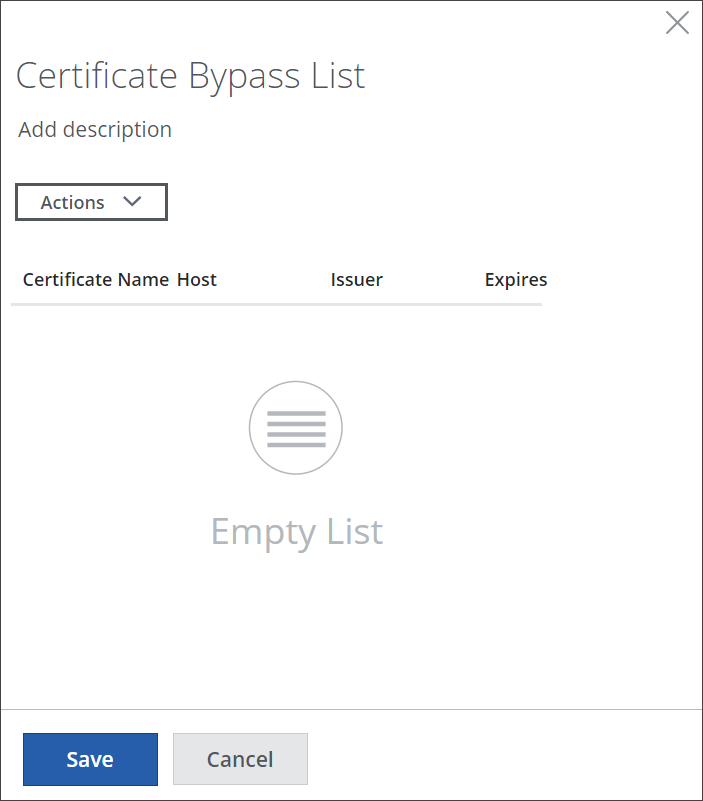
To allow requests for accessing some websites to skip certificate verification, set up a list of certificates for the rule that is preset here for this purpose. The rule is shown under Preset Rules.

-
Click the rule name, which is marked in blue, or click the three dots at the end of the line with rule and select Edit from the menu that is provided.
A panel for setting up a list of certificates is inserted on the right.
-
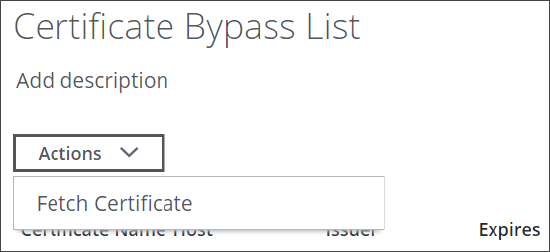
Click Actions and select Fetch Certificate.
-
In the window that opens, enter the name of the domain where you want to fetch the certificate from. Then click Fetch.
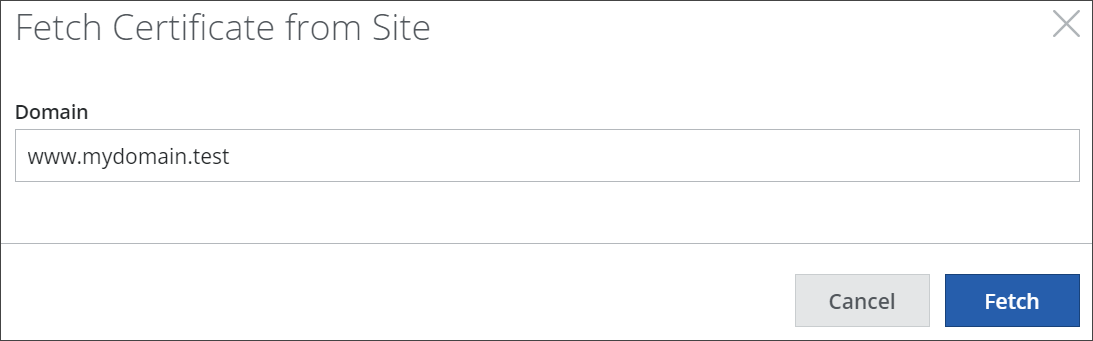
The certificate is entered with its name and other parameters in the list.
Repeat substeps b and c if you want to add more certificates. -
Click Save to save the list and close the panel.
-
-
Configure the preset rule that verifies certificates for Private Applications if they are in a list that you set up.
You can only use this rule if you have purchased a Private Access license from Skyhigh Security.

-
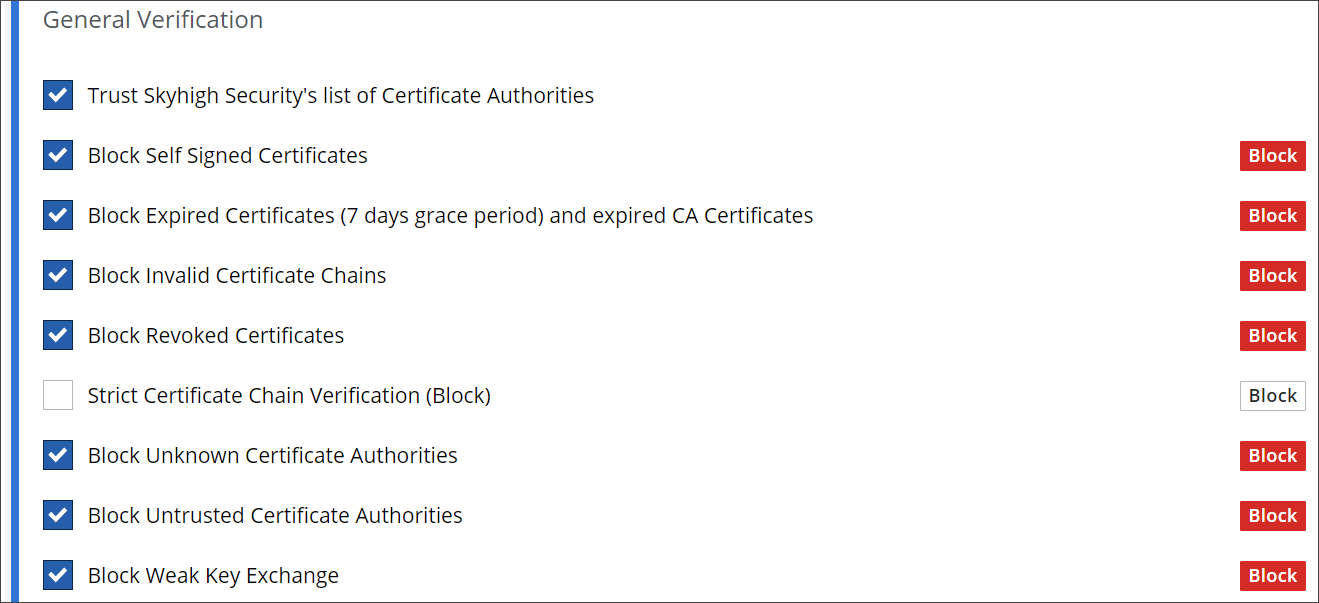
Under General Certification, configure the preset rules for trusting and blocking certificates. Use the checkboxes at the beginning of the lines with the rules to enable oder disable them as needed.
-
Enable or disable the rule for trusting the certificates for Certificate Authorities (CAs) in a list that is maintained by Skyhigh Security.
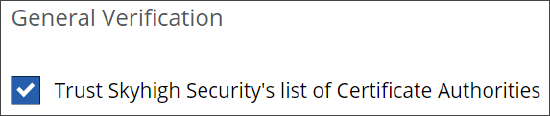
-
Enable or disable any of the rules that block certificates for different reasons. You can:
-
Block self-signed, expired, and revoked certificates
There is a rule for each of these three block reasons. -
Block invalid certificate chains
-
Configure blocking for strict certificate chain verification
-
Block certificates for unknown and distrusted Certificate Authorities (CAs)
There is a rule for each of these two block reasons. -
Block weak key exchange
-
-
-
Under Native Browser CA, enable or disable the preset rule for allowing the use of a native browser with native certificate handling.
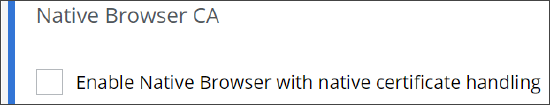
-
Under Signature Verification, configure the preset rule for blocking unsafe certificate signatures.

-
Under Common Name Verification, configure the preset rule for blocking a certificate if there is a Common Name mismatch.

To enable or disable the complete rule set, use the On/Off toggles at the end of the line with the rule set name.
You have now configured how to handle certificate verification on Secure Web Gateway.
