Global Bypass Lists — Allow Global Access to Web Objects
You can allow access to web objects, for example, domains or IP addresses, globally without restricting it by anything. For this purpose, you fill these objects in lists for use by suitable web policy rules.
When a request for web access is received on Secure Web Gateway where one of these objects is involved, for example, a request to access a particular domain, filtering is bypassed for all the rules in the rule sets that follow, which means they are not processed anymore.
This ensures that users can access the web objects you configure here, regardless of any other rule that might still block this access.
- On the user interface for Secure Web Gateway, select Policy > Web Policy > Policy.
-
From the policy tree in the navigation panel, select Global Bypass > Global Bypass Lists.
The selected rule set appears in the configuration area on the right. -
Configure when this rule set should apply.
- Under Criteria, leave the default All Traffic if you want the rules in this rule set to apply to all web traffic.
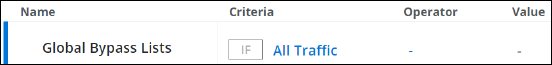
Or click All Traffic and select criteria from the drop-down menu that opens to limit this scope. If you select criteria, you must also select an operator and value for it.
- Next to Applies to, leave the default Request if you want the rules in this rule set to apply to the request cycle of web filtering on Secure Web Gateway.
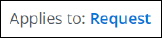
Or click Request and select other cycles from the drop-down menu.
- Under Criteria, leave the default All Traffic if you want the rules in this rule set to apply to all web traffic.
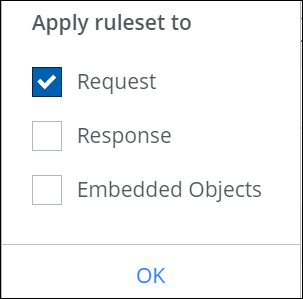
You can configure any combination of the filtering cycles.
-
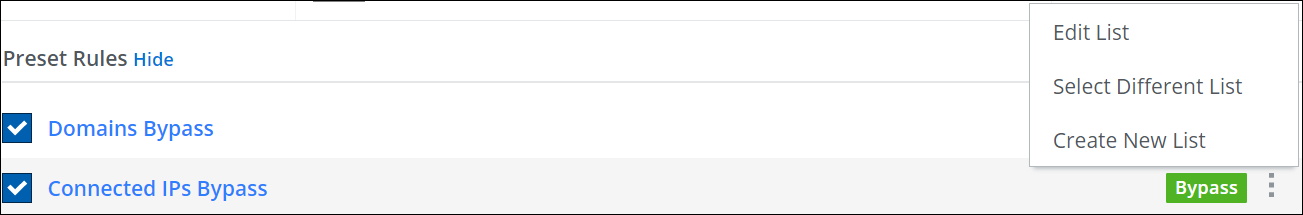
Configure the rules that are preset in this rule set as needed.
These rules are shown under Preset Rules. Most of them are for allowing web traffic to bypass filtering on Secure Web Gateway if particular web objects are involved.
For example, there is a rule named Domains Bypass, which allows users to access particular domains without having their requests for accessing them filtered.

a. Enable or disable any of these rules. Use the toggle checkbox at the beginning of the row for a rule to do this.
There are preset rules that allow bypassing for web objects of the following types:
-
Domains
-
Connected IP addresses
-
Client IP addresses
-
Destination IP addresses
-
User groups
-
User names
-
Processes
b. Enter domains and other web objects in lists for use by these rules. Click the three dots at the end of a the line for a
rule and work with the options for list handling that are provided.
c. Configure the Enable Mobile Access to Sites Using Certificate Pinning rule if needed. Click the three dots
and work with the options for list handling to add websites that this rule should apply to.
You can also create rules of your own and add them to this rule set. Click the three dots at the end of the top row and work with the options of the drop-down menu to create a new rule.
This menu also includes an option for reviewing and working with the underlying code for a rule set.
To enable or disable the complete rule set, use the On/Off toggles.
The filtering process now follows what you have configured for the rules that allow global bypassing.
