Shadow/Web DLP Incident Cloud Card
|
Advanced DLP: ML Auto Classifiers (an advanced DLP capability) require additional entitlement. Contact Skyhigh Support or your account manager for assistance. |
To learn more about the Policy Incidents page, see Policy Incidents Page.
On the Policy Incidents page > Incident Type filter, select the Shadow/Web DLP policy incident and click any incident on the table to view the Shadow/Web DLP Policy Incident Cloud Card.

Shadow/Web DLP Policy Incident Cloud Card Components
The Shadow/Web DLP Policy Incident Cloud Card provides the following information:
To address potential false positive incidents, review the details and update the required incident status as necessary. For instance, select the incident status as False Positive.
NOTE: To automatically classify incidents as potential false positives, you must toggle Enable Potential False Positives to On on the Incident Management page.
- ID. A unique identification number for the specific incident.
- Severity. A rating (e.g., high, medium, low, or Info) that indicates the level of risk associated with the incident. Severity is often based on the type of data involved, the user's action, and the specific policy that was violated.
- Incident Created On. The date and time when the policy violation first occurred and was logged by the system.
- Last Response. The date and time of the most recent action taken by an administrator or the system in response to the incident.
- Expected Response. This response action is configured during the DLP policy creation and defines the intended action when a policy violation occurs.
- ► Click to view the Expected Response in the cloud card
-

- Last Updated. The date and time when any part of the incident record was last modified, which could include status changes, added notes, or other administrative updates.
- Service Name. The name of the cloud service where the policy violation took place.
- User. The username or email address of the user who performed the action that violated the policy.
- Owner. Select to assign an owner. You can assign the incident to yourself or other users. The Owner assignment list is dynamically rearranged for each user, with your name (me) appearing at the top for easy self-assignment. To change the owner of multiple incidents, see Change the Owner of Multiple Incidents.
- Incident Status. Select to assign an Incident Status.
- Resolution Action. Select to assign a Resolution Action. Custom Resolution Actions can be assigned on the Policy > Policy Settings > Incident Management tab.
- Machine Learning Status. Provides details on the status of the incident, analyzed and classified using AI and ML models.
- Potential False Positive. Indicates that the Shadow/Web DLP incident is a potential false positive.
- URL Details
- Destination URL. The specific web address or online location to which the sensitive data was being sent or uploaded.
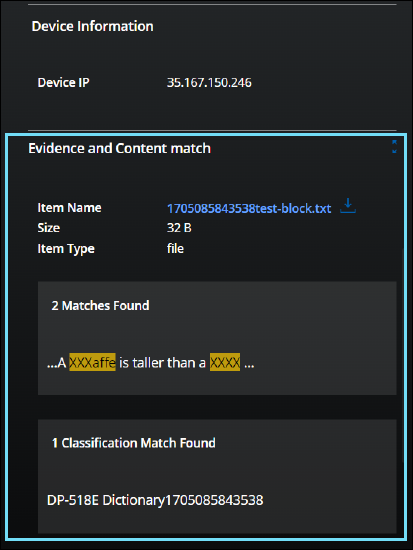
- Device Information
- Device IP. The IP address of the device used by the user when the incident occurred.
- Classifications. Number and names of the classifications that triggered the incident.
- ML Auto Classifiers. Provides details on the matches triggered for various ML Auto Classifiers. For details, see ML Auto Classifiers.
- ► Click to view ML Auto Classifier details in the cloud card
-

- ML Classifier. Displays the predefined category of the matched file, which was defined earlier during the creation of the classification (ML Auto Classifiers).
- Confidence. Displays the confidence percentage triggered for various ML Auto Classifiers based on Skyhigh predefined ML Auto Classifiers. The confidence percentage indicates the likelihood that the file belongs to a specific file category. The minimum threshold for triggering a ML Auto Classifier match is 50%, except for source code files, which have a higher threshold.
- Evidence and Content match. Click the box arrows (
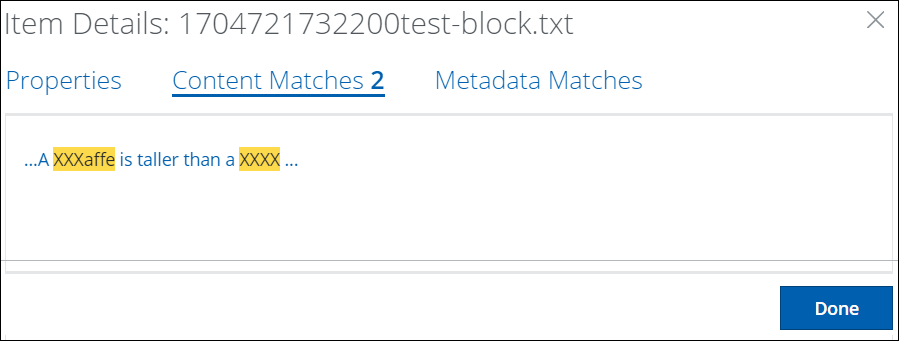
 ) to open the details dialog. Item details such as Properties, Content Matches, and Metadata Matches are displayed on separate tabs. The content and content metadata matches that violate any policy are listed in the Content and Metadata Matches tabs, along with the evidence file in the Properties tab.
) to open the details dialog. Item details such as Properties, Content Matches, and Metadata Matches are displayed on separate tabs. The content and content metadata matches that violate any policy are listed in the Content and Metadata Matches tabs, along with the evidence file in the Properties tab.
- Item Name. Evidence file that violated the policy. If a link is available, you can click to download it. For details, see Download DLP Evidence.
- ► Click to view Item Name in the Cloud Card
-
- Size. The size of the evidence file that was involved in the policy violation.
- Item Type. The classification of the data item involved, such as a PDF document, spreadsheet, image, or other file type.
- Content Matches Found. Allows you to find matches on content and content metadata such as author name, subject, and comments. Click the box arrows to open the details dialog. For details see Enable Match Highlighting. Contact Support for more information.
- Item Name. Evidence file that violated the policy. If a link is available, you can click to download it. For details, see Download DLP Evidence.
- Notes. Enter a note for the incident and click Add. Each note added is visible separately below the Notes field. For notes that you have added, you can Edit or Delete them. For notes written by other users, you might only view them. The default limitation is 10 notes per incident and 300 characters per note. To use the Incident Notes feature, you must use your own Data Storage. You can't use Skyhigh CASB Data Storage. For details about configuration, see Data Storage.
- Incident History. Lists any changes made (such as changed owner, status, response, or notes), the name of the user who made the change, and the time and date that the change occurred.
