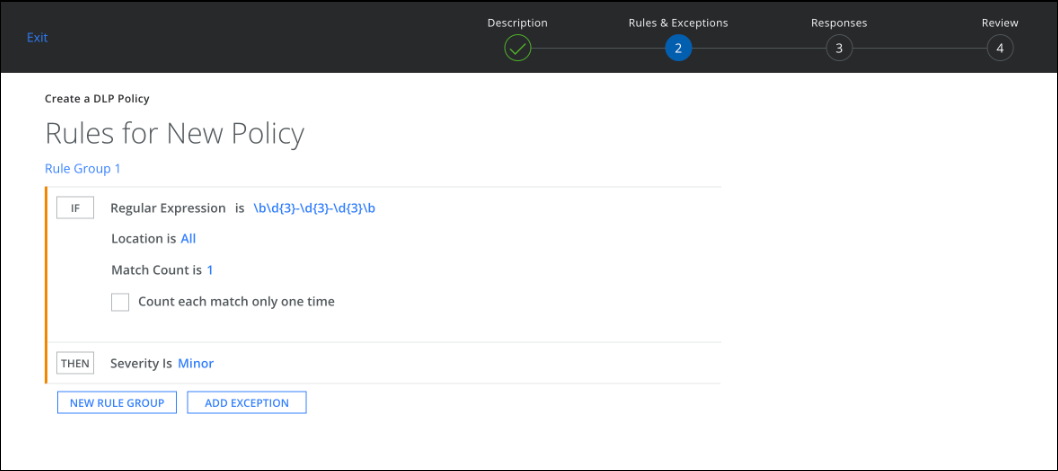
Regular Expression Rules
NOTE: From SSE 6.6.2 release, the Regular Expression rule is available if you have already defined DLP policies using this rule. It will not be available to other users. Skyhigh recommends using classifications to define rules with regular expressions in your DLP policies. For details, see About Classifications.
To create a Regular Expression rule, enter:
- Regular Expression. Regular expression rules allow you to define custom regular expression patterns to match arbitrary text. We strongly suggest that you use a tool like RegexBuddy to develop and test your regular expression before deploying your Skyhigh CASB policy. For DLP support Skyhigh CASB uses RE2 regex. We do not support negative look ahead and negative behind. For more information about RE2 syntax, see https://github.com/google/re2/wiki/Syntax.
IMPORTANT: Match-highlight text captured by individual matches of regular expression rules are limited to 2,000 characters. Otherwise, unbounded regular expression quantifiers (ex: .* or .+) may inadvertently capture full documents as part of the match highlights. Nevertheless, during policy evaluation, the regular expression is still processed in its entirety. No truncation is performed.
- Location. Specify if the match is in:
- All
- Email Subject and File Metadata
- Email Subject, Body, Attachments, and File Content
- Match Count. Specify the number of unique matches and perform extra keyword validation.
- Count each match only one time. Activate or deactivate the checkbox to count the matches only one time or multiple times.