Create a Custom Email Template
Creating a custom email template for DLP policies enhances communication when a policy is triggered, informing users about potential data breaches or violations. These templates can be linked to specific DLP policies, ensuring timely and relevant alerts. You can design the template with images, links, and HTML uploads, while customizing fields like the subject line and body text. You can also enhance your template by adding available variables or custom attributes for personalized messages.
To create a custom Email Template:
- Go to Policy > Policy Settings > Email Templates.
- Click Create Email Template.

- On the Create Email Templates page, configure the following:
- Name. Enter a name for your template. This name must be unique for your tenant.
- Description. Enter a description for your template.
- Category. Select Data Loss Prevention or End User Remediation.
- Type. Custom is pre-selected by default.
- To. Click Add Additional Recipient to add the custom attributes.
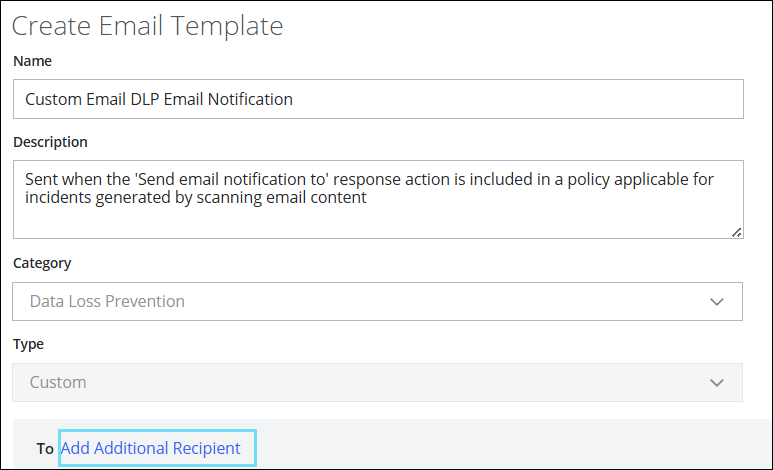
- From the Add Additional Recipient dialog, select the required recipient from the list.
- Click Save.

NOTE: The Add Additional Recipient field is visible only when the Custom Attribute feature is enabled in CC. To enable custom attributes, see Configure Custom Attributes in CC.
- Email Subject. Enter the text to appear in the subject line of your email notification.
- Email Body. Enter the text for the body of the email notification, and enhance the body of the text with these options:
- Template Builder. Using the Rich Text Editor, you can style your email text to emphasize important points. You can also enhance your content by adding links and images. Supported image formats include .jpg, .jpeg, and .png, with a maximum file size of 2 MB.

- Features of Template Builder. The Template Builder provides a defined set of formatting options for email templates, including:
- Font Customization. A limited selection of fonts and font sizes, along with options to bold, italicize, underline, and strikethrough text.
- Color Choice. A restricted range of fonts and background colors.
- List and Alignment. The ability to create numbered and bulleted lists and adjust text alignment.
- Media Integration. Support for adding hyperlinks and importing images.
- Features of Template Builder. The Template Builder provides a defined set of formatting options for email templates, including:
- Template Builder. Using the Rich Text Editor, you can style your email text to emphasize important points. You can also enhance your content by adding links and images. Supported image formats include .jpg, .jpeg, and .png, with a maximum file size of 2 MB.
If you are seeking to expand upon these native template builder capabilities or utilize your own custom HTML, it is recommended to use the Import HTML capability.
- Import HTML. To create an engaging and interactive email template, you can upload an HTML file with a maximum file size of 8 MB. Additionally, you can also enhance your template by adding available variables. Click the copy icon (
 ) to copy the variables and paste them into your HTML code.
) to copy the variables and paste them into your HTML code.

- Variables. To add variables to the email body or email subject, select available items from the Insert Variable list. Separate variables with a line break, space, or by punctuation, such as a comma.
- ▶ Click to view the available variables
-
Variables are placeholders that can be used in the email templates to dynamically populate the emails with specific details about an incident. Each variable represents a different piece of information related to the incident, allowing the email notifications to be highly detailed and context-specific. You can use Skyhigh Recommended Variables or Additional Variables for your email notification.
NOTE:
- Available Variables are displayed based on your policy template, and not all variables are available for all policy templates.
- If the value for your variable is unavailable, the string "N/A" will be displayed in the email.
- Use only the available variables shown in your selected policy template. Do not copy and paste other variables from another template.
The available variables include:
Skyhigh Recommended Variables Additional Variables - Activity.The action that caused the incident to trigger.
- Date Time. The date and time of the incident
- Email Recipients. The list of recipients is displayed in the email.
- Email Subject. The list of email subjects is displayed in the email.
- First Name. The first name of the user involved
- Incident ID. A unique ID for the matched incident.
- Instance Name. The specific instance of the service.
- Item Name. The name of the file or data item involved.
- Matched File Names. The names of the files that matched the policy.
- Path. The location of the matched file.
- Policy Name. The name of the policy that was triggered
- Service Name. The name of the service involved; "N/A" if unavailable.
- Total Match Count. The number of matches found.
- User IP. The IP address of the involved user.
- User Name. The username of the involved user.
- Account ID/Account Name. Information about the user's or entity's account involved in the incident.
- Activity. The specific action or activity that triggered the incident.
- Blocked Collaborators/External Collaborators/Internal Collaborators. Details about who was involved in the file or activity, specifically whether they were internal or external to the organization, and those who are blocked.
- CIS Level. The Center for Internet Security (CIS) benchmark level associated with the incident, potentially related to compliance checks.
- Classification. The classification of the data that triggered the incident (e.g., confidential, public).
- Comments. Any notes or remarks related to the incident.
- Destination URL. The web address where the data was going, if applicable.
- Device ID/Device IP/Device Managed/Device Type. Information about the device used in the incident (ID, IP address, managed or unmanaged device, and device type).
- End User Response. Any action taken or response provided by the end user.
- Event ID. A unique identifier for the specific event or incident.
- External Collaborators Count. The number of external collaborators involved.
- File Size/File Type. Details about the file that triggered the incident.
- Incident Created On/Incident Updated On. Timestamps indicating when the incident was created and last updated.
- Incident ID. A unique identifier for the incident.
- Incident Response/Incident Status/Incident Type. Information about how the incident was handled, its current state, and what type of incident it was.
- Instance Name. The specific instance of the cloud service or application where the incident occurred.
- Item Created On/Item Id/Item Modified On/Item Name/Item Type. Details about the specific data item (e.g., file, document) involved.
- Malware Category: Name. The category name of any malware involved.
- Malware Checksum. The unique identifier is used to detect any malware involved.(e.g, SHA-256, MD-5)
- Malware Confidence. The level of certainty for the involved malware threat.
- Modified Collaborators. Details of collaborators who modified the file.
- OS. The operating system of the involved device.
- Owner. The owner of the data or file involved.
- Path. The location or path of the file or data.
- Policy Name. The name of the triggered policy.
- Primary Rule Group. The primary rule group within the policy that triggered the incident.
- Quarantine Status. The status of any quarantine action taken.
- Recipient Domains. The domains of the recipients of the data.
- Remediation Response/Remediation Status. Information about the actions taken to resolve or remediate the incident and its current state.
- Resolution Action. The specific action taken to resolve the incident.
- Scan Name/Scan Run Date. Details about any scan that detected the incident.
- Service Name. The specific service or application involved (e.g., Box, SharePoint).
- Sev. The severity level of the incident.
- Shared Link. The link to the shared file, if applicable.
- Source. The source of the data or incident.
- Total Match Count/Unique Match Count. Statistics about the number of matches that triggered the policy.
- User Agent. The user agent string of the client involved.
- User Name/User UID. Information about the user involved.
- Vulnerabilities. Vulnerabilities associated with the incident.
- Custom Attributes. To add Custom Attributes to the email body or email subject, select available items from the Custom Attributes list. This option is only visible when the Custom Attribute feature is enabled in CC.
NOTE: The Custom Attributes field is visible only when the Custom Attribute feature is enabled in CC. To enable custom attributes, see Configure Custom Attributes in CC.
- Click Save.

Once your Custom Email Template is created, you can link it to a DLP Policy.
Delete Email Templates
IMPORTANT: If a Custom Email Template is linked to a DLP policy, it cannot be deleted. You must unlink it first.
To delete a custom email template :
- On the Email Templates page, click the name of the template link that you want to edit from the Name column.
- On the Edit Email Template page, click Delete Template.

- On the Delete Template confirmation dialog, click Delete.

Once the template is deleted, the action cannot be undone.
