Data Classifications
Data Classification is the process of organizing data based on specific criteria such as Advanced Patterns, Keywords, Document Properties, etc, and categorizing data with predefined categories such as PII, regulations, sensitivity, and more. It involves assigning labels, tags, or metadata to organize and manage data effectively. Categorizing data makes it easier to locate and retrieve data, allowing organizations to control data more efficiently and manage security, compliance, and risk within or outside your organization.
How do Data Classifications and DLP Work?
A data classification and data loss prevention (DLP) system works together to monitor and protect critical data, eliminate insider threats, and prevent unauthorized access or transmission of confidential or sensitive data. A robust data security strategy can be implemented by combining data classification with a DLP solution.
To enhance data classification within your organization, data classification collects details such as the creation date of a document, its storage format, and sharing methods. A DLP policy engine then utilizes these details to make informed decisions and implement appropriate measures for safeguarding sensitive data as per the defined response actions in the DLP policy. For details on the various response actions, see Sanctioned DLP Policy Response Actions and Shadow/Web DLP Policy Response Actions.
Unified Data Classifications in Skyhigh SSE
Skyhigh Security allows unified data classification across its Skyhigh SSE products, such as CASB (Sanctioned/Cloud & Email DLP), SWG (Web/Mobile DLP), CNAPP (IaaS DLP), Private Access, and Endpoint & Network DLP. The unified Data Classification promotes consistent data protection rules and improved operational efficiency for users. Data Classification provides a range of built-in classifications for standard requirements, and you can use them to comply with required regulations. You can also create custom classifications to suit your organization's needs. Both built-in and customized classifications are consistent and can be used across your Skyhigh SSE data protection policies.
.png?revision=2)
The following are several ways of organizing data using the key classification components:
- OCR. Find and prevent data loss in screens and images.
- Advanced EDM. Fingerprint and secure organization data.
- Advanced IDM. Fingerprint and secure custom documents.
- Unified AIP. Apply labels to secure documents and emails.
- Advanced Patterns. Use built-in advanced patterns or custom regular expressions to secure sensitive data.
Unified DLP Engine Use Cases
Skyhigh SSE promotes consistent policy enforcement across its products through Unified Data Classifications and common DLP engines.
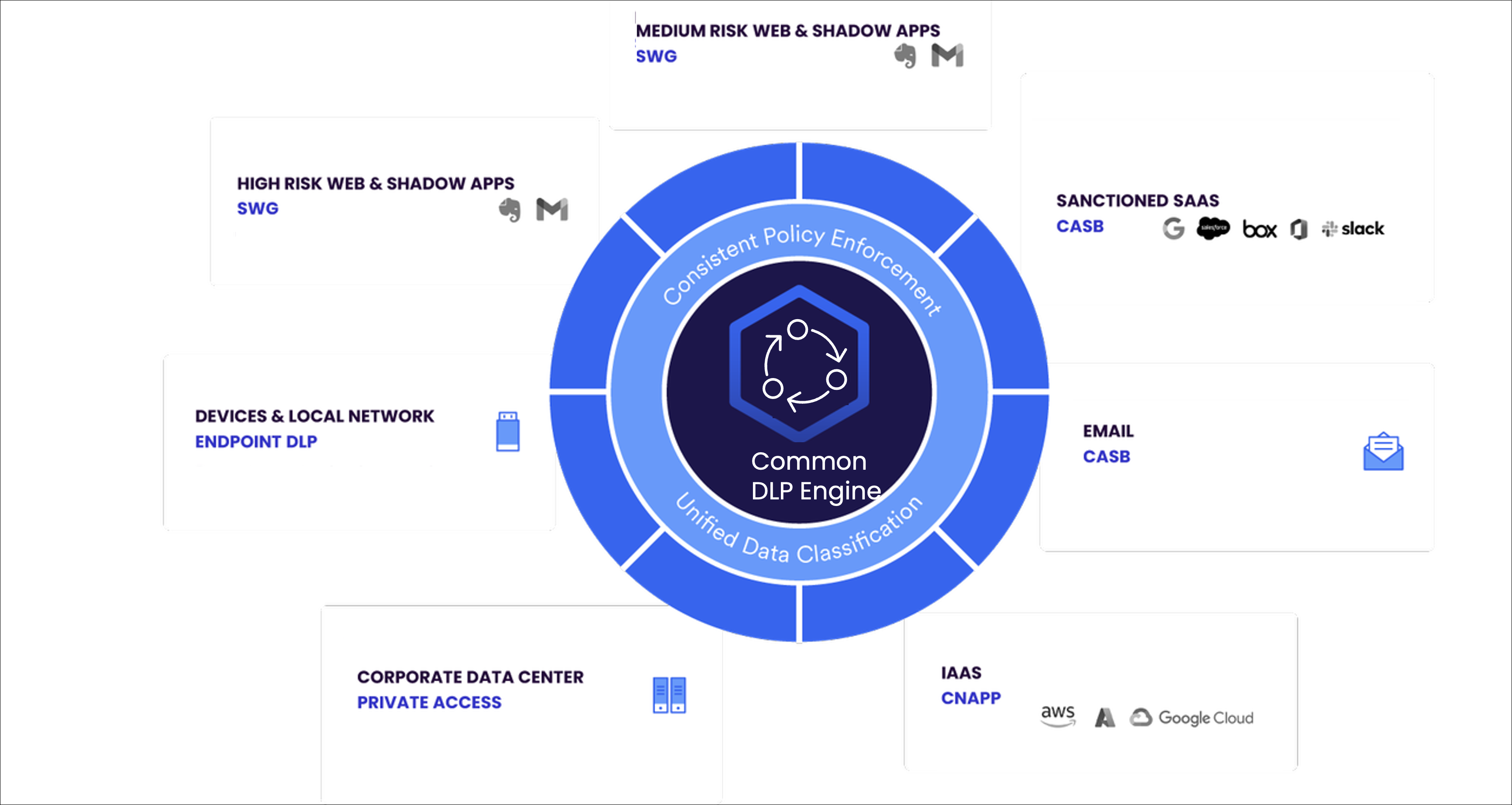
The following table outlines different DLP products and their typical use cases:
| Products | DLP Use Cases | |
|
CASB (Sanctioned Cloud DLP, Email DLP) |
Enforcing Cloud DLP for Sanctioned SaaS applications such as Box, Salesforce, and Slack allows you to:
Enforcing DLP for Email (Email DLP) allows you to :
|
|
| CNAPP (IaaS DLP) | Enforcing DLP policies for IaaS applications such as AWS, Azure, and GCP enables in-tenant scans and prevents malware and data loss. | |
| Private Access | Enforcing DLP policies for corporate data center protect data in private applications and restrict sharing of sensitive data when needed. It works with managed or unmanaged devices. | |
| Endpoint and Network DLP | Enforcing DLP policies for Devices and Local Network prevent copying to cloud personal apps, USB, print, screen capture etc. | |
|
SWG (Web and Mobile DLP) |
Enforcing Web DLP policies for :
|
|
DLP Policies Methods and Actions
DLP Policy Methods
Data Classification classifies data on multiple levels. Classified data can be seen on the DLP rules interface to apply the data protection rules. The DLP rules identify sensitive data using these various methods:
| DLP Policy Methods | Description |
|---|---|
| Classification Label | Classification Label rules allow you to categorize files based on their confidentiality and apply the unique label identification to configure the policy. |
| Dictionaries | Dictionaries are collections of related keywords and key phrases used to compare the dictionary entries where each entry is assigned a score. |
| Regular Expression | Regular expression rules allow you to define custom regular expression patterns to match arbitrary text. |
| Fingerprints |
The Fingerprint rules identify Structured and Unstructured content (EDM and IDM). |
| Keyword | The keyword is a specific word or phrase. The related keywords can be added to the keywords list to classify the content and identify the sensitive data. |
| Metadata | The rules can also be used to identify the file-level metadata which includes file conditions such as File Name, File Path/Folder ID, File Size, File Type, Document Properties, and File Encryption Type. |

DLP Actions
Once the data is classified, data can be monitored for activity or controls through DLP to prevent content from entering or leaving the cloud service by applying specified remediation actions in the DLP policy. For details, see Sanctioned DLP Policy Response Actions and Shadow / Web DLP Policy Response Actions.
