Configure the Trellix Virtual Execution in SWG
NOTE: Before integrating IVX with SWG, you need to ensure that a cluster is configured on IVX and the node role is set to broker, even if there is only a single IVX server that requires integration. For more information about configuring an IVX cluster, see IVX Administration Guide.
Rulesets
You can configure the Trellix VX integration in SWG using the below two methods:
- Forward a web object depending on the additional scanning
- Forward a web object before the additional scanning
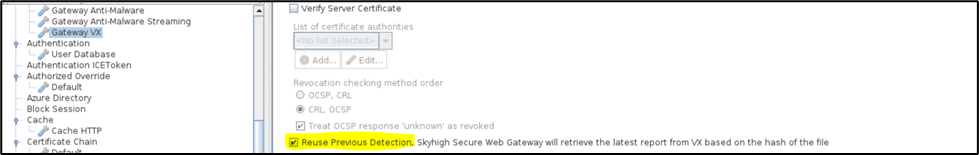
You can also configure that a web object is not scanned a second time by Trellix Virtual Execution if it has been scanned before. In this case, the existing report that was produced after the first scanning is evaluated once again. This can be configured in the Gateway VX setting:
Forward a Web Object Depending on the Additional Scanning
When this option is configured, the result of the additional scanning by Trellix VX determines whether a web object is forwarded to the user who requested it. If a web object is found to be safe, it is forwarded, otherwise, it is not.
The below information helps to understand the process that the SWG performs on additional scanning through Trellix VX to prevent the malicious object into your network.
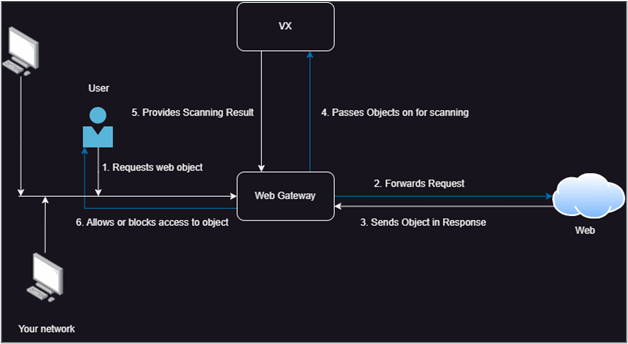
- A user sends a request to access a web object, for example, a file, from a system within your network that is a client of Web Gateway.
- If the request passes filtering according to the configured rules, Web Gateway forwards it to the appropriate web server. A progress page is sent to the client, telling the user to wait while the request is processed.
- The web server sends the object to Web Gateway.
- If the criteria for using Trellix VX are met, Web Gateway passes the object on for scanning. To retrieve information on the scanning progress, Web Gateway queries Trellix VX in regular intervals.
- When Trellix VX completes the scanning, it lets Web Gateway to know whether the object is malicious or not.
- Depending on this information, Web Gateway allows the user to access the requested object or sends a block page, which states that access is blocked and gives a reason for the blocking.
Configure Forward a web object depending on the additional scanning
- Import the Trellix VX rule set from the rule set library, present under Gateway Anti-Malware.
- A new setting will be added after import, called Gateway VX, in the settings tab under Engines -> Anti-Malware.
- Go to the Gateway VX setting and configure the appropriate values (for detailed information on configuring details in the Gateway VX setting, see settings below.
- This rule set implements the workflow that lets a web object additionally be scanned by Trellix VX and forwarded to the user depending on the scanning result.
- After importing this rule set, a list and settings are also implemented.
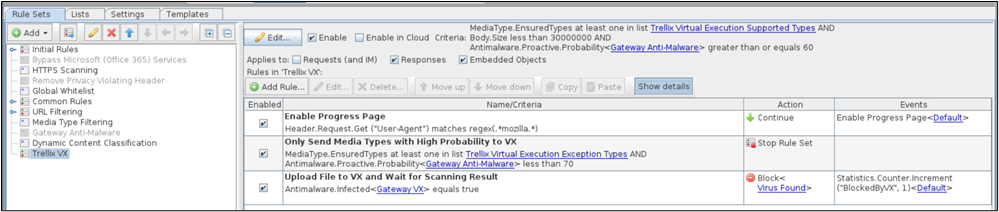
Trellix VX Ruleset (after unlocking view):
Gateway VX Settings
Forwarding a web object before the additional scanning
When this option is configured, a web object is forwarded to the user who requested it before the additional scanning by Trellix VX. If a web object is found to be infected, a warning message is sent to the administrator of the network that the user sent the request from.
Two rulesets are used here, and an explanation of the two nested rulesets within the main Trellix VX - Offline Scanning With Immediate File Availability ruleset will provide information on the process taken in this mode.
VX - Init Offline Scan ruleset
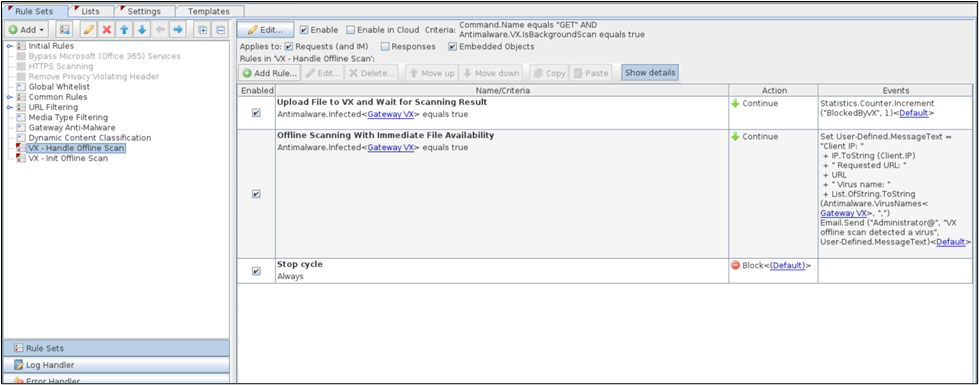
- This nested ruleset has the same criteria as the ruleset that forwards a web object to the user depending on the result of the additional scanning.
- The ruleset applies if previous scanning by Web Gateway has resulted in a configured degree of probability that a web object is infected, the web object is on the list of web objects that can be scanned, and a particular object size is not exceeded.
- The ruleset contains one rule that uses the Antimalware.VX.InitBackgroundScan property in its criteria.
- In this case, data for the current transaction is recorded. This includes all data that is related to a request for web access and the response to it from a web server, such as the IP address of the client, authentication information, the URL of the web server, and the requested web object that was sent as the body of the response message.
- An internal request is sent to initiate scanning by Trellix VX. When it completes, the requested web object is forwarded to the user while the scanning is performed later on, using the data that was recorded.
- If the value of the Antimalware.VX.InitBackgroundScan property is false, scanning by Trellix VX could not be initiated and a rule event is used to display an error message.
VX - Handle Offline Scan ruleset
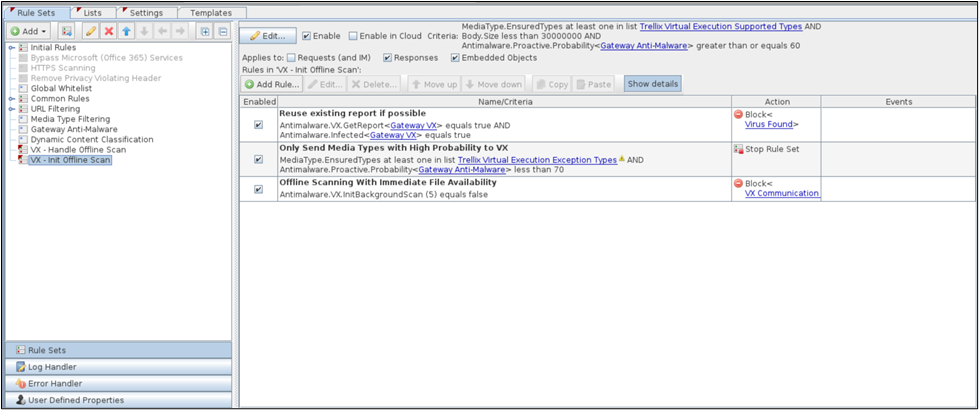
- This nested rule set has the Antimalware.VX.IsBackgroundScan property in its criteria
- In this case, if the above property is true, the data that was recorded by the rule in the Trellix VX - Init Offline Scan ruleset is used by Trellix VX to scan the web object specified by the data.
- The ruleset has the rules:
- that uses an event to increase a counter if a scanned web object is found to be infected
- that uses another event to create and send a message about the infected web object to the administrator
- that stops the processing cycle
Configure forward a web object before the additional scanning:
- Import the Trellix VX – Offline Scanning With Immediate File Availability ruleset from the ruleset library, present under Gateway Anti-Malware.
- Two rulesets called VX – Handle Offline Scan and VX – Init Offline Scan will be imported.
- The ordering of these rulesets must be maintained. The VX – Handle Offline Scan ruleset should always be present before the VX – Init Offline Scan ruleset.
- A new setting will be added after import, called Gateway VX, in the settings tab at Engines -> Anti-Malware.
- Go to the Gateway VX setting, and configure the appropriate values (for detailed information on configuring details in the Gateway VX setting, see settings below.
NOTE: The nested rule set has the same criteria as the rule set that forwards a web object to the user depending on the result of the additional scanning.
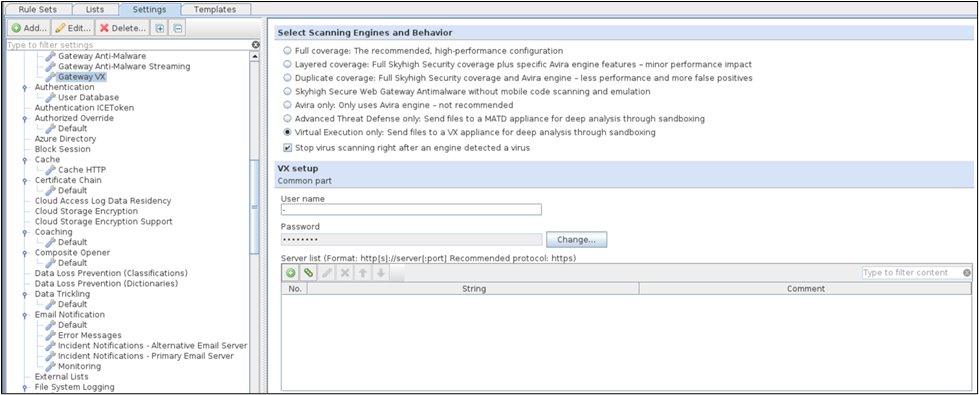
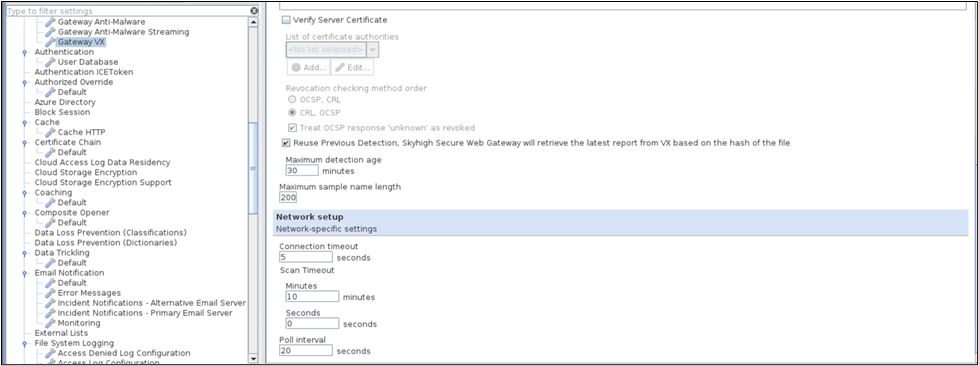
Gateway VX setting
This is a setting for the Anti-Malware module (or engine) on Web Gateway, which handles virus and malware filtering, including the additional use of Trellix Virtual Execution.
The ‘Gateway VX’ setting includes mainly options for configuring the following:
- Username and Password of VX appliance — Used for submitting objects for analysis. Communication between Web Gateway and the server that Trellix VX runs on.`
- Server list — Information of Server(s) can be configured under the Server list. This will follow round robin failover mechanism.
- Verify Server Certificate — The Server certificate can be added under Verify Server Certificate to perform CA verification.
- Reuse Previous Detection — If this option is enabled, then SWG will fetch the latest report from VX if it is already present, by using file hash.
- Maximum Detection Age — If this option is set to a configured value, then SWG will ensure that the report fetched is no older than the mentioned detection age.
- Maximum sample name length — This is the maximum length allowed for the file name.
- Network Setup — Under this option you can configure Connection Timeout which is the amount of time the connection with VX server needs to be kept alive and Scan Timeout to set the amount of time you are willing to wait for the scan result.
- Poll Interval — This option configures how often we send the Status requests to Trellix VX, asking for an update on the submitted object.
Trellix Virtual Execution Supported Types list
This list is used within the criteria of the library ruleset. Only web objects belonging to the media types on this list are passed on to Trellix VX for scanning. By default, the list contains several media types.
Criteria for Additional Scanning by Trellix Virtual Execution
- Web Gateway uses the functions of Trellix Virtual Execution for scanning a web object after the anti-malware engines on Web Gateway have scanned the object.
- The Trellix Virtual Execution library rule set uses this probability in its criteria. The default value that must be reached for the criteria to match is 60. This means that only if scanning a web object on Web Gateway results in a malware probability of 60 percent or more, is it passed on to Trellix Virtual Execution.
- When configuring Trellix Virtual Execution, you can increase or lower this value and consequently let this product support Web Gateway more or less frequently.
- It is therefore important that, on the rule sets tree, the rule set for Trellix Virtual Execution be placed after the rule set for the normal anti-malware functions on Web Gateway, which is usually the Gateway Anti-Malware default rule set.
- The Anti-Malware module (or engine) runs with two different settings when Web Gateway and Trellix Virtual Execution work together: one for the Web Gateway part and one for the part of the supporting product. The default names of the two settings are Gateway Anti-Malware and Gateway VX.
