Overview
Prior to this features, SWG sends live traffic to Next Hop Proxies to determine its health. This resulted in delayed response in case Next Hop Proxy is not healthy. With this feature, SWG will have knowledge of the health of the Next Hop Proxies beforehand.
- The health checks will always be happening in the background for the NHPs configured under Configuration > Cluster > Health Check.
- This is irrespective of the Next Hop Proxy being used in the policy. For Example, NHP1 is configured for health checks. But this NHP1 is not used in the policy. In this case, health checks will be happening at periodic intervals for NHP1.
SWG will send live traffic to Next Hop Proxies only if it is healthy, this results in better response time for the live traffic. this would help you to take any corrective actions in case of any potential network issues.
SWG periodically checks the health of the configured Next Hop Proxies based on the result of the TCP 3-way handshake. If TCP 3-way handshake is successful, the Next Hop Proxy is considered healthy.
Next Hop Proxy can be anything like an external web proxy, web server, socks proxy, etc.
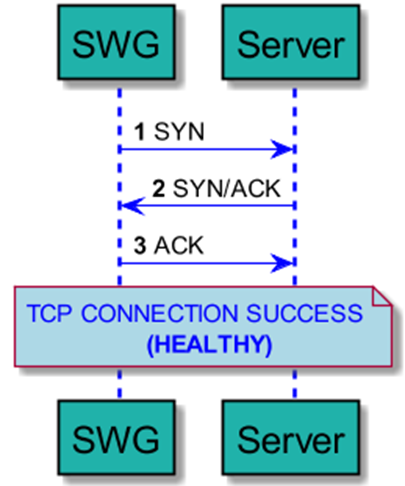
‘Server’ in the above diagram means Next Hop Proxy.
- Based on the health of the NHP, SWG decides where to route the traffic. If NHP is unhealthy, SWG will not forward the traffic to this NHP.
- To enable a health check for NHP, it must be configured under Configuration > Cluster > Health Check.
- If NHP is not configured under Configuration > Cluster > Health Check health checks will not happen. In this case, the default old handling for live traffic to NHP will come into effect.
Note: If Next Hop is a web server, the 'Proxy Style Requests’ option in the Next Hop Proxy settings must be disabled.
