Work with a Hardware Security Module
Complete these high-level steps to enhance private key security with a Hardware Security Module. Different administrators can be responsible for different steps.
- Implement a solution for using a Hardware Security Module on a Secure Web Gateway appliance.
- Generate private keys on the Hardware Security Module.
For information about how to generate these keys, see the following documentation:- If you have installed a module card or an additional appliance, see the documentation of the Skyhigh Security partner who provides these devices (Entrust).
For more enhanced security, this documentation also provides information on creating a Security World and an Operator Card Set. - If you have set up a remote server, see the documentation of the Skyhigh Security partner who provides this server (Thales).
If you use an emulation, generate private keys on the user interface of Secure Web Gateway.
- If you have installed a module card or an additional appliance, see the documentation of the Skyhigh Security partner who provides these devices (Entrust).
- Store private keys on the Hardware Security Module.
For information on storing these keys, see the documentation of the Skyhigh Security partners if you are working with a module card or appliance (Entrust) or a remote server (Thales).
You can also store private keys on a module card, appliance, or remote server that you have generated on the user interface of Secure Web Gateway.
If you use an emulation, store the private keys in a directory that is provided within the Secure Web Gateway appliance system. The path to this directory is: /opt/mwg/data/hsmagent.
- Make private keys available for use on Secure Web Gateway.
This is done by entering them in a list on the user interface. - Reference private keys on a Hardware Security Module for use on Secure Web Gateway.
If you have protected the keys using an Operator Card Set, you must unlock them first.
For information about how to unlock keys, see the documentation of the Skyhigh Security partner who provides the Operator Card Set (Thales).
Implement an HSM solution on an appliance
To implement an HSM solution on a Secure Web Gateway appliance, complete some preparatory activities. Then use the options of the user interface to select and configure a solution.
NOTE: The following steps can be in the responsibility of different administrators.
Prepare a Secure Web Gateway appliance for running an HSM solution.
- If using a module card:
- Install the module card on the appliance.
- For information about how to install the module card, see the Skyhigh Security Secure Web Gateway Installation Guide.
- If using an additional appliance:
- Install the appliance.
- For more information, see the documentation of the Skyhigh Security partner who provides the appliance (Entrust).
- If using a remote server:
- Set up the remote server and connect it to the Secure Web Gateway appliance.
- For more information, see the documentation of the Intel partner who provides the remote server (Thales).
- Using an emulation requires no preparatory activities.
- On the user interface of Secure Web Gateway, configure the HSM solution for the appliance that you have prepared.
- Select Configuration | Appliances.
- On the appliances tree, select the appliance and click Hardware Security Module.
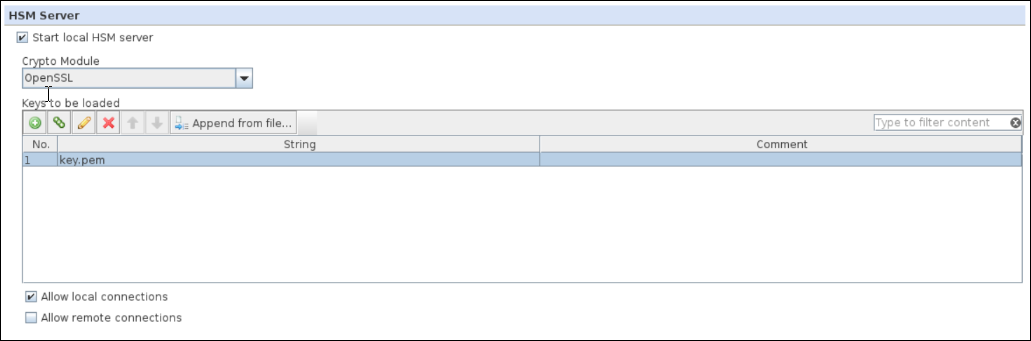
The Hardware Security Module settings appear in the configuration pane. - Under HSM Server, select Start local HSM server.
- From the Crypto module list, select one of the following HSM solutions according to what you have prepared:
- Entrust nShield Solo/Connect — Enables use of the module card or the appliance
- SafeNet Network HSM (formerly Luna SA) — Enables use of a remote server (Thales)
- OpenSSL — Enables use of an emulation
- In the Keys to be loaded list, add entries for the private keys that you want to be available for loading. For every key, enter its key ID in string format.
- Make sure that Allow local connections is selected.
- Click Save Changes.
You can now reference private keys when importing certificates for SSL-secured communication on the user interface of Secure Web Gateway.
You can also configure other Secure Web Gateway appliances that have no HSM solution of their own implemented to use the functions of the solution on this appliance.
Enable the nShield Connect appliance solution
When using an nShield Connect appliance, you must start the nShield daemon, also known as hardserver daemon, manually to enable this solution.
The daemon is started within the MLOS operating system of the Web Gateway appliance that you are using for the solution.
- Log on to the MLOS shell.
- Run a command like the following to add a line for enabling a start script to the appropriate configuration file:
echo NFP_ALWAYS_ENABLED=1 >> /etc/nfast.conf
The NFP_ALWAYS_ENABLED parameter enables or disables the /etc/init.d/nfast script, which is used for starting the daemon. - Start the daemon:
/etc/init.d nfast start
Whenever the appliance system is restarted in the following, the daemon is also started.
To stop the daemon, run /etc/init.d nfast stop.
To disable the daemon permanently, set NFP_ALWAYS_ENABLED to zero or remove the line with this parameter from the configuration file.
Sample procedure for configuring a remote server (Thales)
Configure the remote server (Thales) by running suitable commands from a system console.
For information about how to configure this remote server, you should generally refer to the partner documentation (Thales).
The following procedure provides some sample steps and commands for completing this configuration.
- From a system console, connect to the remote server (Thales), then run the following commands to configure the server for connecting to the Web Gateway appliance.
client register -c <label> -ip <IP address of the {{webg}} appliance>
client register -c <label> -ip <IP address of the {{webg}} appliance>
- Connect to the Secure Web Gateway appliance, then complete these substeps.
- Verify the connection to the remote server.
/opt/gemato/lunaclient/bin/vtl verify - Create a client certificate for connecting to the remote server.
/opt/gemato/lunaclient/bin/vtl createCert -n <IP address of the {{swebg}} appliance - Copy the client certificate to the remote server.
scp/opt/gemato/lunaclient/cert/client/<IP address of the {{swebg}} appliance>.pem admin@<domain name>
- Verify the connection to the remote server.
- On the remote server, copy a server certificate to the Secure Web Gateway appliance.
scp admin@<domain name>:server.pem
Configure an HSM Server using OpenSSL
Configure an HSM Server by performing the following steps from OpenSSL.
- Under HSM Server, select OpenSSL from the Crypto Module drop-down:

-
Example to generate private key and certificate using OpenSSL for testing purpose:
> openssl genrsa -out key.pem 2048
> openssl req -new -x509 -key key.pem -sha256 -days 365 -out testcert.pem - Copy the private key to directory path /opt/mwg/data/hsmagent from the SWG backend via SSH.
Sample Output:
=================================================================================
[root@mwgappl20225027 ~]# cd /opt/mwg/data/hsmagent
[root@mwgappl20225027 hsmagent]# ls -lrt
total 12
-rw-r--r-- 1 root root 3619 Dec 12 06:46 hsmagent.conf.bak
-rw-r--r-- 1 root root 3619 Dec 12 06:46 hsmagent.conf
-rw------- 1 root root 1679 Dec 12 06:46 key.pem
================================================================================== - Add the private key file name under Keys to be loaded section and save changes:
The ownership of the private key changes automatically:
-rw------- 1 hsmagent mwg 1679 Dec 12 06:48 key.pem
- Verify that the key has been loaded successfully by executing below commands:
============================================================================
[root@mwgappl20225027 ~]# /opt/mwg/bin/hsmagent -c
configuration is updated
--- process key key.pem ---
key was already loaded by the daemon
[root@mwgappl20225027 ~]# /opt/mwg/bin/hsmagent -Q
key.pem
[root@mwgappl20225027 ~]#
============================================================================
Verify key is loaded successfully. - The loaded key can be further used in SSL Client settings with certificate and private key loaded from the HSM.
Configure an HSM solution by multiple appliances
Configure Secure Web Gateway appliances that have no individual HSM solution implemented as clients of a Secure Web Gateway appliance with an HSM solution. These appliances can then use the functions of the solution.
- Select Configuration | Appliances.
- On the appliances tree, select a Secure Web Gateway appliance that has an HSM solution implemented, then click Hardware Security Module.
The Hardware Security Module settings appear in the configuration pane.
- Under HSM Server, configure this appliance to act as a server allowing clients to use a Hardware Security Module remotely.
- Click Allow remote connections.
- In the HSM server port definition list, add one or more ports that listen to client requests.
- Under Server identification, generate or import a certificate for the server. Then export it to a location where you can import it from when configuring the clients.
- Click Save Changes.
- Complete the following substeps for every appliance that you want to configure as a client.
- On the appliances tree, select an appliance that has no HSM solution implemented, then click Hardware Security Module.
- Under HSM Client, select Use remote HSM server.
- In the Remote server list, add a host name with a listener port and import the server certificate.
You can add entries for more than one server to allow this client the use of Hardware Security Modules on different servers. - Under Client identification, generate or import a certificate for the client. Then export it to a location where you can import it from when configuring the list of appliances that are permitted as clients of the server.
- Add the clients of the server.
- On the appliances tree, select the appliance that you have configured as server, then click Hardware Security Module.
- In the Permitted clients list under HSM Server, add a host name and import a certificate for every appliance that you have configured as client.
- Click Save Changes.
Make private keys available on an appliance
Make private keys available for referencing in a list on a Secure Web Gateway appliance that has an HSM solution implemented.
- Select Configuration | Appliances.
- On the appliances tree, select an appliance that has an individual HSM solution implemented and click Hardware Security Module.
The Hardware Security Module settings appear in the configuration pane.
- Under HSM Server, add entries for private keys in the Keys to be loaded list.
For every key, enter its key ID in string format.
- Click Save Changes.
The private keys are now available for referencing.
Reference a private key on a Hardware Security Module
Reference a private key on a Hardware Security Module to make the key information available for enabling the use of a certificate.
Certificates are involved when settings for filtering SSL-secured communication are configured. This sample procedure describes one scenario for referencing a private key.
- Select Policy | Settings.
- On the Engines branch of the settings tree, expand SSL Client Context with CA and select the Default CA settings.
Under Define SSL Client Context, click Import next to Certificate Authority.
- The Import Certificate Authority window opens.
- Click Browse next to Certificate, then locate and import a certificate file.
- Select HSM next to Private key source.
A list with the IDs for the available private keys opens.
- Select a key ID, then click Import to import the certificate with its key information.
- Click Save Changes.
