Cisco Webex Compatibility
Title: Cisco Webex Prerequisties and Maintained List IP
Category / Product: Mcafee Web Gateway
Summary:
This article is intended for Customers who want to support the 3rd Party application Webex Meetings Client and Video Collaboration Devices for use on their company's network using the Skyhigh Webgateway environment. The guide covers prerequisites and contains information regarding ports, IP ranges, and domains required by the meeting client, video collaboration devices, and Webex Edge audio.
Detailed Description:
Ports that need to be allowed in the webgateway network for the access of Webex Meetings:
| Webex website, Webex Desktop App/Productivity Tools, Webex Meetings for Android/iOS, Webex Web App | ||||
| Protocol | Port Number(s) | Direction | Access Type | Comments |
| TCP | 80 / 443 | Outbound | Webex Client Access port and Webex Events (Audio Streaming) | Webex client signaling port is used to exchange initial meeting setup information. Fall-back port for media connectivity when UDP ports are not open in the firewall. Webex Events Audio Broadcast transmission. |
| TCP/UDP | 53 | Outbound | DNS | Used for DNS lookups to discover the IP addresses of Webex servers in the cloud. Even though typical DNS lookups are done over UDP, some may require TCP, if the query responses cannot fit it in UDP packets. |
| UDP | 9000 | Outbound to Webex | Primary Webex Client Media (VoIP & Video RTP) | Webex client media port is used to exchange computer audio, webcam video, and content sharing streams. Opening this port is required to ensure the best possible media experience |
| TCP | 5004, 443, 80 | Outbound to Webex | Alternate Webex Client Media (VoIP & Video RTP) | Fall-back ports for media connectivity when UDP port 9000 is not open in the firewall |
| TCP/UDP | Operating System Specific Ephemeral Ports | Inbound | Return traffic from Webex | Webex will communicate to the destination port received when the client makes its connection. A firewall should be configured to allow these return connections through. |
| TCP | 443 | Inbound | Proximity | The connecting device must have an IPv4 route-able path between itself and the device using HTTPS. |
| UDP | 5004 | Outbound | Webex Client Media | The UDP port 5004 is used for out-of-meeting sharing to Cisco Video Collaboration Devices. |
Ports used by webex Edge Audio:
| Protocol | Port Number(s) | Direction | Access Type | Comments |
| TCP | 5061, 5062 | Inbound | SIP Signaling | Inbound SIP signaling for Webex Edge Audio |
| TCP | 5061, 5065 | Outbound | SIP Signaling | Outbound SIP signaling for Webex Edge Audio |
| TCP/UDP | Ephemeral Ports 8000 - 59999 |
Inbound and Outbound | Media Ports | On an enterprise firewall, pinholes need to be opened up for incoming traffic to Expressway with a port range from 8000 - 59999 |
IP Addresses
We are using this link also to check IP Ranges for WebEx:
https://help.webex.com/en-us/article/WBX000028782/Network-Requirements-for-Webex-Services#id_134142
https://help.webex.com/en-us/article/WBX264/How-Do-I-Allow-Webex-Meetings-Traffic-on-My-Network?#id_135011
So some of the IPs highlighted above to be removed because they aren't present in the link will not be removed because they are present in the first link above.
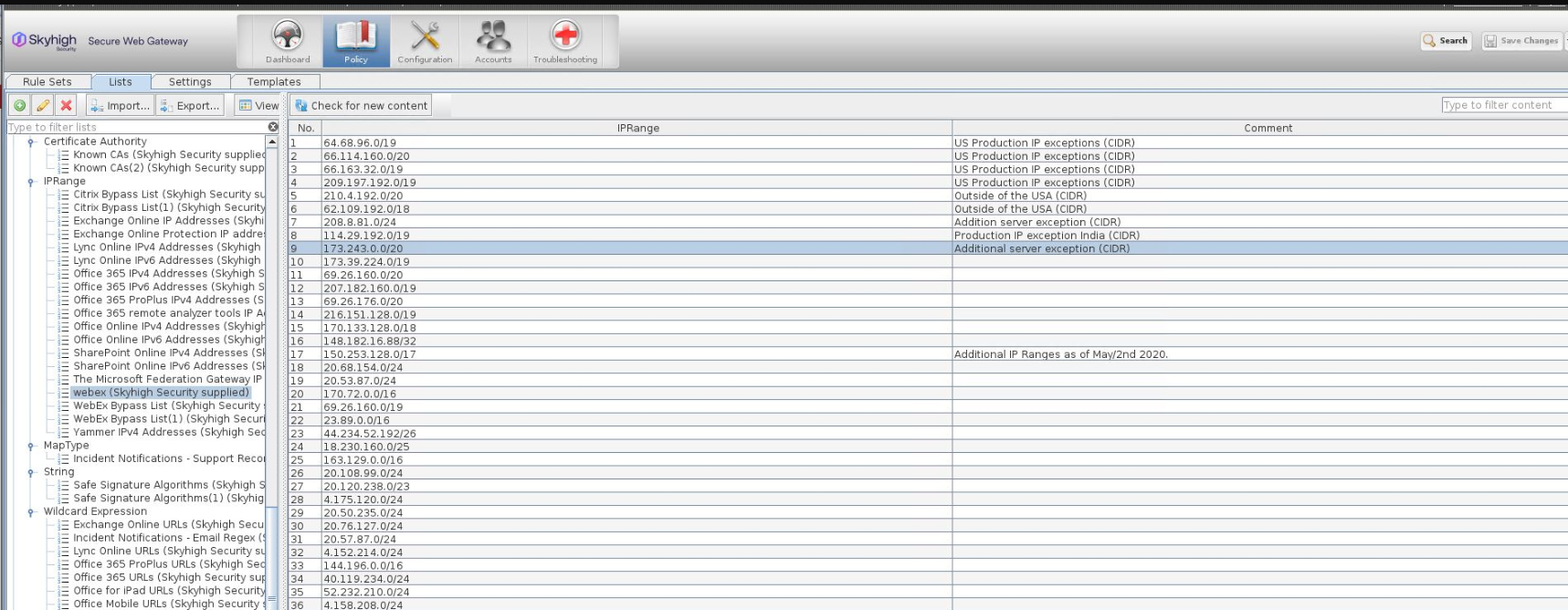
We have to verify webex managed list from the GUI of the webgateway.
Under Policy >> Lists
Cisco will continue Windows 7 support on Mozilla Firefox, Google Chrome, and Microsoft Edge. Cisco will continue to provide bug fixes and updates for Windows 7 wherever possible. (as per https://help.webex.com/en-us/article...tion-for-Webex? as of November 28, 2023)
Common Issue:
Problem
You get a WebEx Meeting Manager notification similar to the following when you try to access a WebEx meeting over SWG SSL Scanner:
You are no longer connected to the meeting.....
Cause
It's not possible to access or attend a WebEx meeting when SSL Scanning is enabled on SWG.
The reason is that SSL Scanning breaks into the encrypted traffic. WebEx encapsulates their proprietary protocol (which isn't HTTP traffic) inside HTTPS. So, when the WebEx HTTPS traffic gets broken into by SWG, it breaks the connection because SWG expects HTTP traffic.
Solution
Add a bypass to your SSL Scanner.
Add a McAfee-Managed list to your Subscribed lists:
This list contains the list of WebEx IP addresses to add to a bypass of the SSL Scanner. You need to verify that your engine is up-to-date. Select your appliance from the list in Configuration and select Manual Engine Update.
- Log on to the SWG UI.
- Select Policy.
- Right-click Subscribed Lists and select Add.
- For the name, type Webex IP Ranges.
- Select the List content is managed remotely option.
- Select the McAfee Maintained List option.
- Click Choose.
- From Application URL Lists, select Webex IP Ranges.
- Click OK and OK again.
Use the list in a rule to bypass the SSL Scanner:
- Click Policy and find your SSL Scanner ruleset.
- Select the top ruleset, usually SSL Scanner if using the default ruleset.
- Click Add Rule, name it SSL Scanner Whitelist, and click Next.
- Select If the following criteria is matched.
- Click Add and from the drop-down list, select URL/Host Criteria.
- From the list on the left, select URL.Destination.IP.
- From the list in the middle, select is in range list.
- From the list on the right, select the list created in the previous set of instructions. In this example, the name is Webex IP Ranges.
- Click OK.
- Click Next.
- For the action, select Stop Rule Set.
- Review the summary of the rule for errors and then click Finish.
- Click Save Changes at the top right.
