SSL Scanner Rule Examples
Where should the SSL Scanner be 'located' in the rule sets?
Typically, it is recommended that the SSL Scanner be placed near the top of the rule set list. It is usually recommend placing it just below your 'Global Allowlist' (if you've chosen to use it), and just above the Global Blocklist (allowing proper block pages to display if needed). See below:
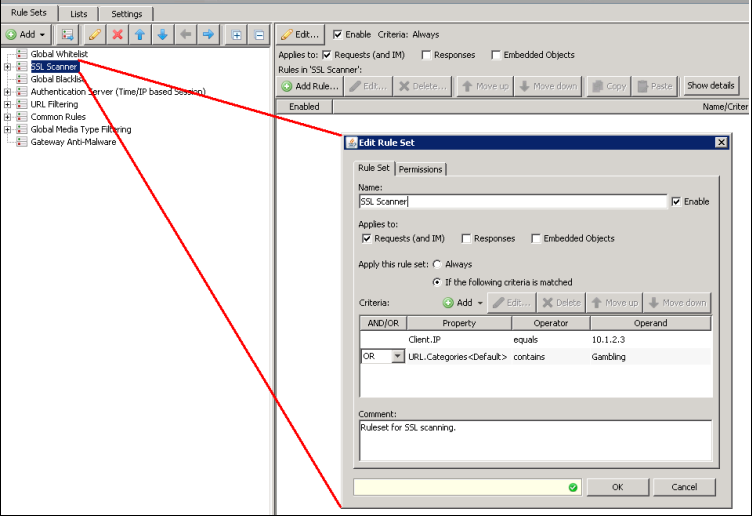
How do I limit the SSL scanner to a particular client IP, or a particular category?
You can limit who/what the SSL scanner is applied to by adding some rule set criteria. Below (as an example), you can limit the SSL Scanner to apply to just the particular client IP, or a particular category.
NOTE: In general, you will NOT be able to limit the SSL Scanner to a particular username or usergroup. The reason is that the SSL Scanner rule set occurs above where authentication occurs (which is expected/recommended). At the time the SSL Scanner ruleset is called, we do not yet have the username. You would need to move portions of the SSL Scanner 'after' authentication in order to limit to user or group. If you have a need, it is strongly recommended you work with support for assistance.
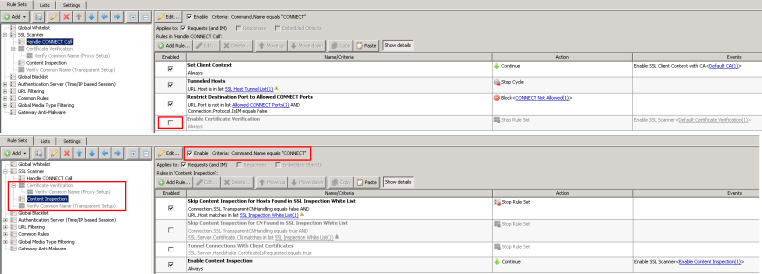
How do I enable the Handle CONNECT Call step, but not do Certificate Verification or Content Inspection?
- Starting with the default SSL Scanner rule set, you can select to disable the Certificate Verification rule set, the Content Inspection rule set, and the 'Verify Common Name (Transparent Setup) rule set.
- Next, within the 'Handle CONNECT Call' rule set, click to disable the rule 'Enable Certificate Verification
How do I enable Certificate Verification, but NOT Content inspection?
Explicit Proxy
- Within the 'Handle CONNECT Call rule set, enable the 'Enable Certificate Verification' rule.
- Click to 'enable' the 'Certificate Verification' rule set. Here, you can determine a variety of elements you may to filter.
- The 'Verify Common Name (Proxy Setup)' rule set should also be enabled.
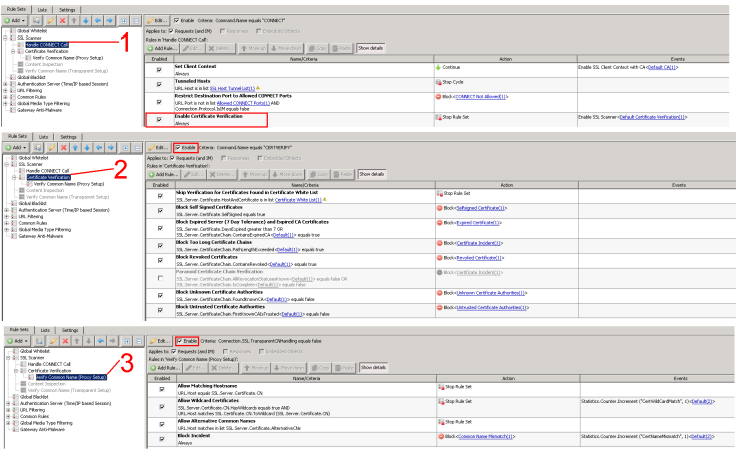
Transparent Proxy
- Within the 'Handle CONNECT Call rule set, enable the 'Enable Certificate Verification' rule.
- Click to 'enable' the 'Certificate Verification' rule set.
- The 'Verify Common Name (Proxy Setup)' rule set should also be disabled.
- The 'Verify Common Name (Transparent Setup) rule set should be enabled.
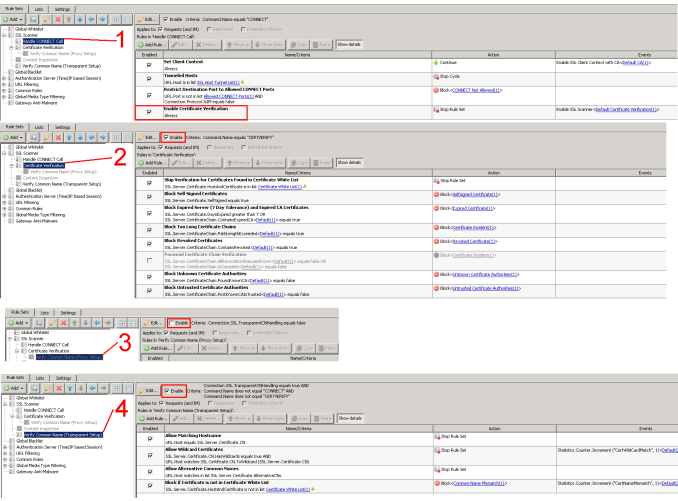
How do I enable Content Inspection without Certificate Verification? - (Illustration ONLY - not recommended)
NOTE: This is for illustrative purposes only. In a production environment, it is NOT recommended that Content Inspection be performed if Certificate Verification is not also performed. This could potentially leave your environment vulnerable to phishing of sensitive data.
Option 1
- Within the 'Handle CONNECT Call rule set, disable the 'Enable Certificate Verification' rule.
- Disable the 'Certificate Verification', 'Content Inspection', and 'Verify Common Name (Transparent Setup)' rule sets.
- Within the 'Content Inspection' rule set (which is now disabled, click to select the 'Enable Content Inspection' rule, and click 'Copy'.
- Paste that rule within the 'Handle CONNECT Call', just below the disabled 'Enable Certificate Verification' rule.
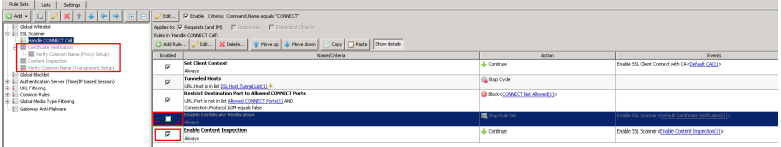
Option 2
- Within the 'Handle CONNECT Call rule set, disable the 'Enable Certificate Verification' rule.
- Disable the 'Certificate Verification' rule set, and the 'Verify Common Name (Transparent Setup) rule set.
- The 'Content Inspection' rule set should be enabled.
- Update the 'Content Inspection' rule set criteria to be "Command.Name equals CONNECT"