Configure SCP for Web Hybrid
Introduction
This document has been written in order to guide in the deployment of the Skyhigh Client Proxy (SCP). This document has been written primarily for Secure Web Gateway deployments but some of the content will include other products that are commonly used. For those unfamiliar, SCP is an application that is installed or deployed via Trellix ePO on the client workstations. SCP is used to force workstation traffic to the proxies defined in SCP's settings. SCP is also used to forward user authentication information. This authentication information is included in encrypted HTTP headers with each request.
Deployment options
SCP can be used in a multitude of different ways. Below are the most common scenarios for its use.
SCP always active/redirecting (SWG On-Prem and Cloud)
In this scenario, it is assumed that you have Secure Web Gateway On-Prem and Cloud. This will allow you to protect the users with the Secure Web Gateway On-Prem (in the network), and when they are off the network, they will be protected by the Secure Web Gateway Cloud. Note that this scenario could also apply if you always want to redirect to your Secure Web Gateway (whether the user is on or off premises) or always want to redirect to the Cloud Service
In network: SCP Active
Outside network: SCP Active
Network Detection settings: Always redirecting (Trellix ePO/Trellix ePO Cloud), Corporate Detection unchecked (Control Console)
SCP redirection only on-prem
In this scenario we assume a Secure Web Gateway (On-Prem) only scenario, you are not using Secure Web Gateway Cloud. SCP will only be active when the users are in the network and will redirect them to your local Secure Web Gateway. Outside of the network, SCP will stand down.
In network: SCP Active
Outside network: SCP Inactive
Network Detection settings: Always redirecting (Trellix ePO/Trellix ePO Cloud), Corporate Detection unchecked (Control Console)
SCP redirection only off-premises
SCP redirection only off-prem
In this scenario we assume that you are using SCP only to redirect users, when they are outside your network. For example to make sure that laptop users still get filtering when through the Secure Web Gateway Cloud when they take their laptops home. When the users are on-prem, they might be filtered by a Secure Web Gateway in your network, but you do not have SCP redirect the users to it.
In network: SCP Inactive
Outside network: SCP Active
Network Detection settings: Redirect network traffic when... (Trellix ePO/Trellix ePO Cloud), Corporate Detection checked (Control Console)
How SCP Works (Technical Details)
Below is a description of how the Skyhigh Client Proxy will check to see whether or not it should be redirecting traffic to the proxies specified in the configuration.
- Checks if a proxy server can be contacted, top down until it receives a first response.
- Checks if the corporate network can be reached. All servers are contacted at once, to prevent any long delays failing down the list.
- Checks if there is a captive portal, common in hotel rooms or Internet cafes, which requires user interaction prior to gaining Internet access.
Corporate detection / Traffic redirection settings
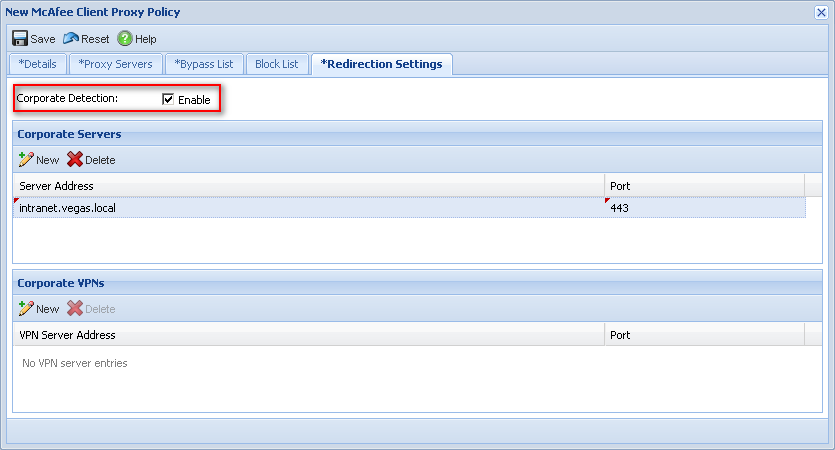
Corporate detection (as referred to in SaaS) or Traffic redirection settings (as referred to in Trellix ePO), specifies what resources SCP should check for to see if it should redirect traffic. Typically if you do enable corporate detection, you should specify your Trellix ePO server, or another server using a port other than 80 or 443.
Detection on
If corporate detection is on, then SCP will attempt to reach the listed network servers or ports. If SCP is able to reach these specified servers and ports, then SCP will stand down.
Below screenshots show equal settings between Trellix ePO and the SaaS console:
Detection off
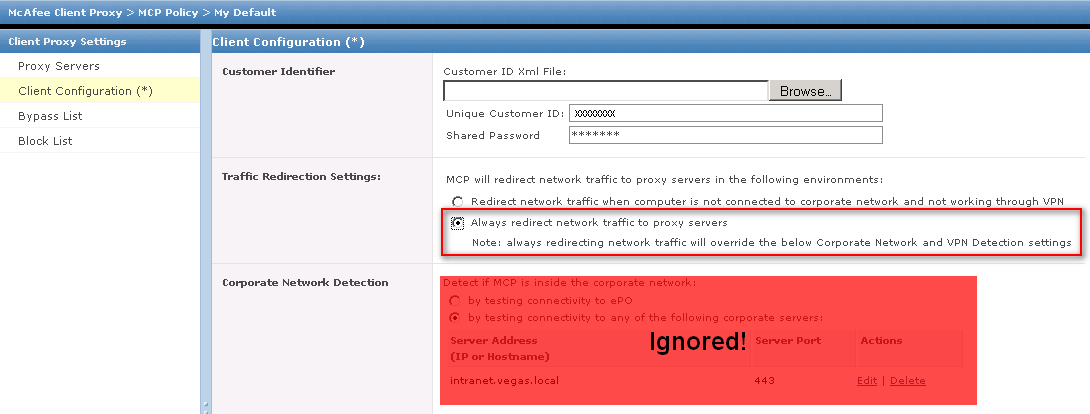
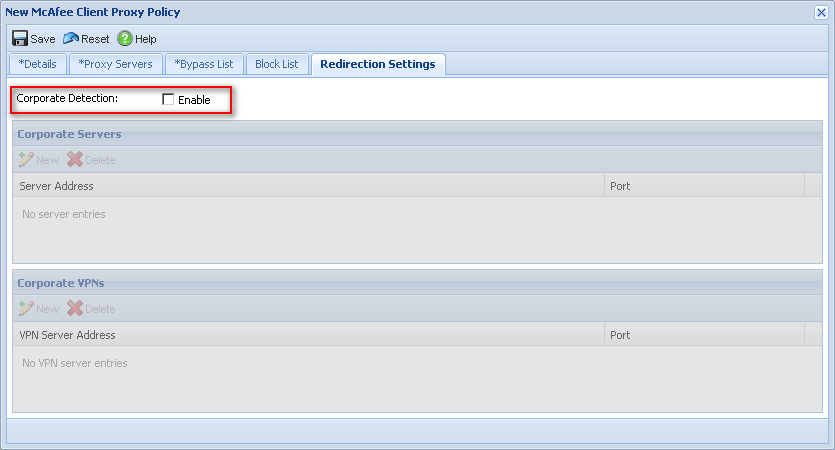
If corporate detection if off, then this means that SCP will always be attempting to redirect traffic to the specified proxy servers (assuming all health checks pass).
Below screenshots show equal settings between Trellix ePO and the SaaS console:
Proxy check
SCP will attempt to contact the specified proxy servers in order to determine if it is reachable. If not, SCP will stand down.
Captive check
In some cases, the above health checks could be false positives. In certain cases users may be accessing the internet via their hotel room, which often require a login of sorts. This final check will help make sure that access to the internet is valid and the proxy redirection will occur properly.
Prerequisites
Prior to deploying SCP it is expected that you have the following setup and ready.
Existing Software
- Trellix ePolicy Orchestrator 4.6.1+ - This makes it easier for deploying the SCP software (via the Agent). This is optional if you are not deploying using Trellix ePO.
- Agent - If the Agent is installed on the workstation then this allows Trellix ePO to distribute the SCP software. This is optional if you are not deploying using Trellix ePO.
- Secure Web Gateway Cloud UI - This is optional if you are not using the Secure Web Gateway Cloud. This could be Trellix ePO Cloud (newer customers or migrated customers) or the legacy Control Console.
- Trellix ePO Cloud - Trellix ePO Cloud is used to manage components of the Secure Web Gateway Cloud, like the SCP shared key. It is available athttps://manage.mcafee.com
- Control Console (Legacy) - You must be able to access the Control Console via https://www.mcafeeasap.com/ or https://portal.mcafeesaas.com/, this will allow for downloading the "shared key".
- Skyhigh Client Proxy - You must be able to access the Secure Web Gateway user interface in order to add rules and also change settings.
- Supported workstation to run SCP - Supported environments for SCP - see System Requirements.
- Shared key/Secret key
- The shared key or secret key is used by SCP to encrypt the authentication information, which is then decrypted by the Secure Web Gateway (On-Prem) or Secure Web Gateway Cloud when it receives a users request.
- Where it's obtained:
- Secure Web Gateway Cloud UI (Trellix ePO Cloud/Control Console)
NOTE: If utilizing the Secure Web Gateway Cloud, the shared keyfile must be generated from within the Secure Web Gateway Cloud UI, not the Secure Web Gateway (On-Prem)UI. - Secure Web Gateway (On-Prem) UI
- Secure Web Gateway Cloud UI (Trellix ePO Cloud/Control Console)
- When it's needed: Depending on your deployment, the shared key file needs to be imported into Trellix ePO and/or Secure Web Gateway.
- Skyhigh Client Proxy aka SCP (extension and software)
- Components:
- Client - Piece that is installed on the client machine
- Server - Piece that is used on Trellix ePO to manage SCP related policies and software
- Where it's obtained:
- Download Portal (requires Grant #):https://secure.mcafee.com/apps/downl...aspx?region=us, then navigate to Secure Web Gateway > Messaging & Web Security > Client Proxy x.x
- Content Security Portal (requires login):https://contentsecurity.mcafee.com/, then navigate to Products > Secure Web Gateway 7 > Downloads > Tools
- Trellix ePO Cloud (requires login): https://manage.mcafee.com
- Control Console Portal (requires login): https://portal.mcafeesaas.com/,then navigate to Web Protection > Setup > Client Proxy, this package does not include the Trellix ePO extension.
- Why it's needed: To deploy and configure on the client workstations.
- Components:
- OPG file (if not using Trellix ePO, created in SaaS console): The OPG file is the configuration file for SCP. It tells SCP what proxies to use, as well as other settings.
Configure Secure Web Gateway Cloud
This section is optional if you do not use the Secure Web Gateway Cloud. All that is required is to obtain the shared key / secret key. This will be used in later steps to configure the SCP policy.
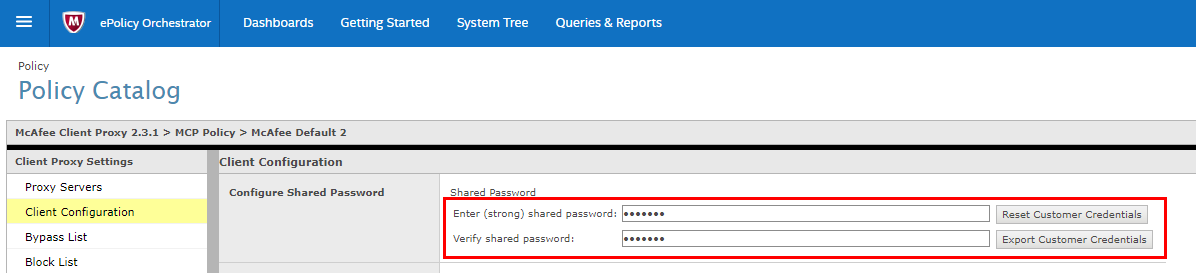
IMPORTANT: If you are configuring the secret key for the first time, it is important that you remember the password that you configure.
In Trellix ePO Cloud you'll need to duplicate the default SCP policy and set the shared secret in the Client Configuration:
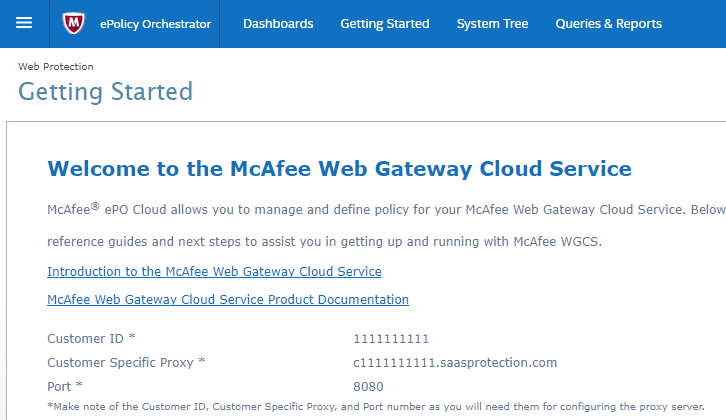
The customer ID in Trellix ePO Cloud is located on the Web Protection > Getting Started Page:
Configure Secure Web Gateway On-Prem
In Secure Web Gateway (On-Prem) we need to import the authentication ruleset and import the secret key (use the same credentials that were used in the Secure Web Gateway Cloud if you have it).
Import the ruleset
Go to Policy > Rule Sets > Add > Rule Set from Library > [Find "Authentication with Client Proxy"], import it. Disable it or modify the ruleset criteria to only apply to a specific test workstation.
Configure the shared key
Go to Policy > Settings > Engines > Authentication > SCP
If you have the Secure Web Gateway Cloud use the Customer ID and Secret Key as specified in the SaaS console. The SaaS Secret Key value should be placed in the Secure Web Gateway Shared password field.
If you do not have the Secure Web Gateway Cloud, you can specify any Customer ID and Shared password (Ex Customer ID=1111111111). Be sure to remember the credentials you enter, these are used by SCP and Secure Web GatewayG to encrypt/decrypt header information.
Configure ePO and Deploy SCP
Skip this if you are not using Trellix ePO to deploy SCP. Prior to working with SCP you must deploy the software to the workstations you wish to have SCP do its thing.
Installing SCP extensions (ePO Package)
In the SCP download, there should be a number of folders, Client, Documentation, and Server. The "Server" folder contains the Trellix ePO extension that will allow us to manage the SCP software once its deployed. Without this installed Trellix ePO will not know how to manage the SCP software.
To install the extension login to Trellix ePO, navigate to Menu > Software > Extensions, then click"Install Extension" in the bottom left corner.
Installing SCP software into the Master Repository
The "Client" folder should contain a number of folders, underneath you should find one called "Signed_Package", this contains the software package we need to check-in to Trellix ePO.
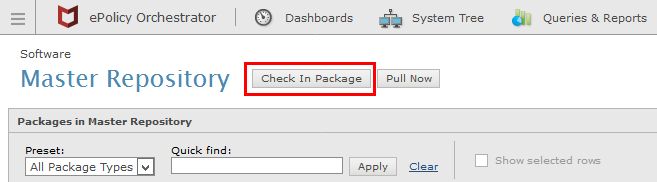
To check-in the package, login to Trellix ePO, navigate to Menu > Software > Master Repository, then click "Check In Package". Then browse for the file in the "Signed_Package" folder.
Create a deploy software task for SCP
In order to begin deploying the software you must have the agent installed on the workstations. This will assist in installing the software.
In order to install the software to the workstations in your environment, a software task will need to be created. This task can be applied to a group of workstations, or a single workstation.
Login to Trellix ePO, navigate to Menu > System > System Tree.
Select a workstation or group of workstations to apply a task.
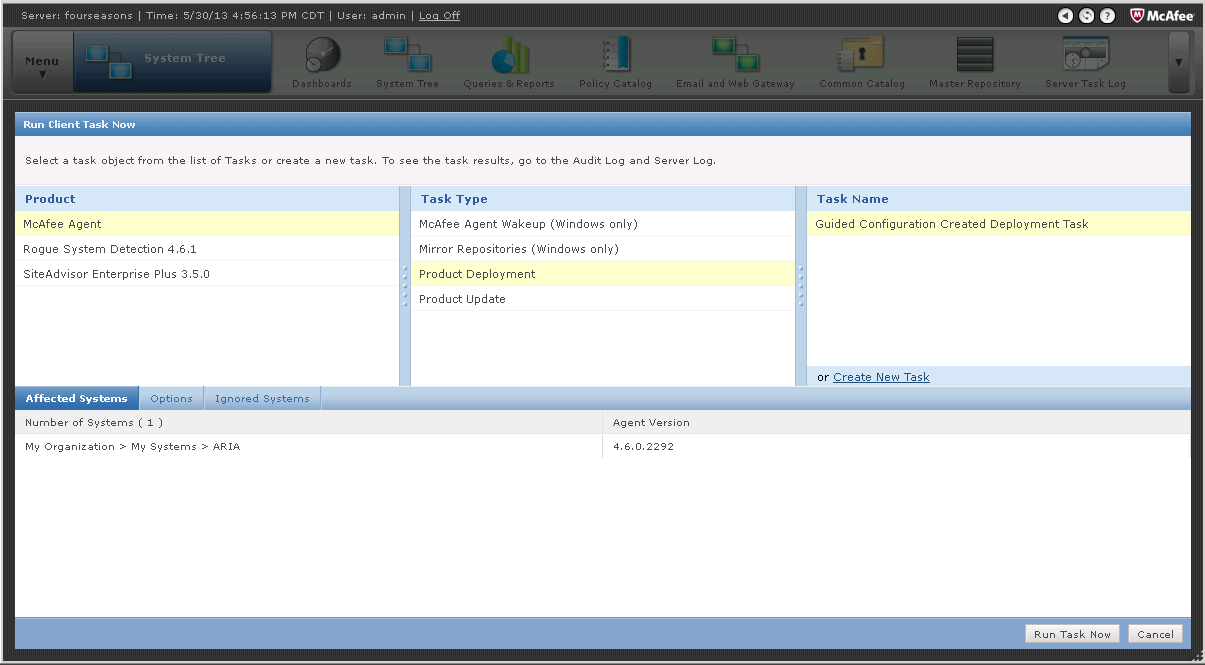
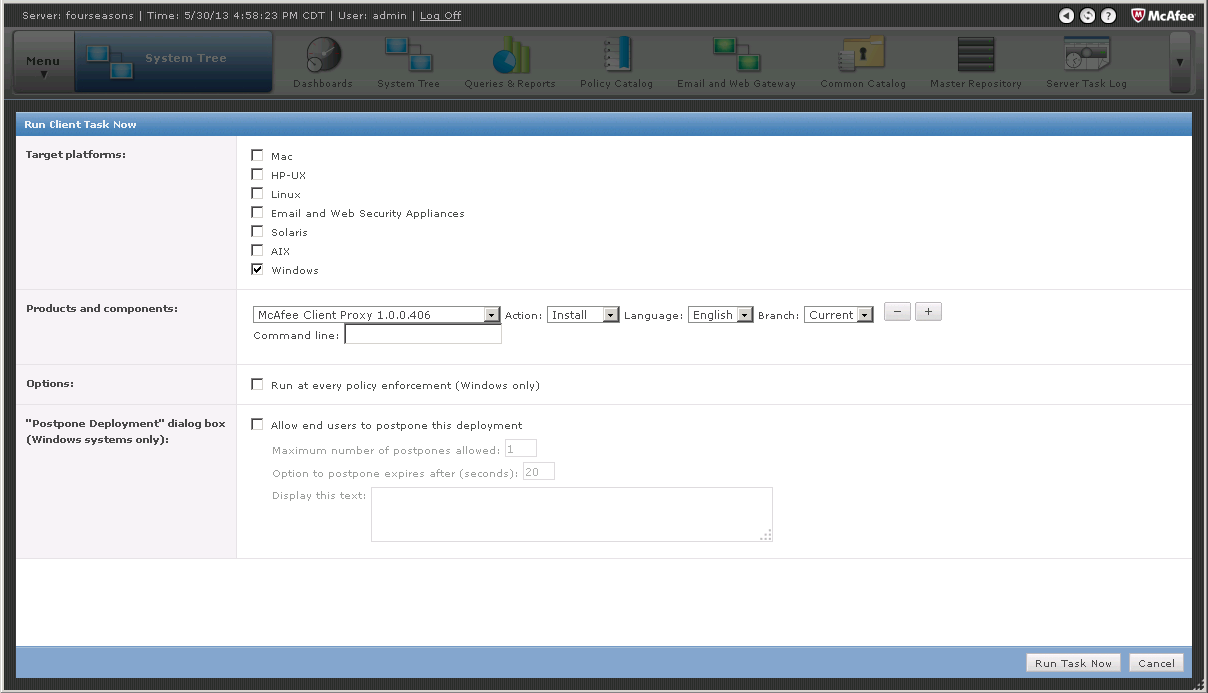
Once the workstations are selected, click Actions > Agent > Run Client Task Now, this will open a new dialog (see below).
Configure SCP Policy
Now that SCP has been deployed to the workstation you can configure a policy for it.
With ePO
Login to Trellix ePO, navigate to Menu > Policy > Policy Catalog, then select "Client Proxy" from the "Product" dropdown.
Click edit for the "My Default" policy. This will be the policy that is pushed out to the clients.
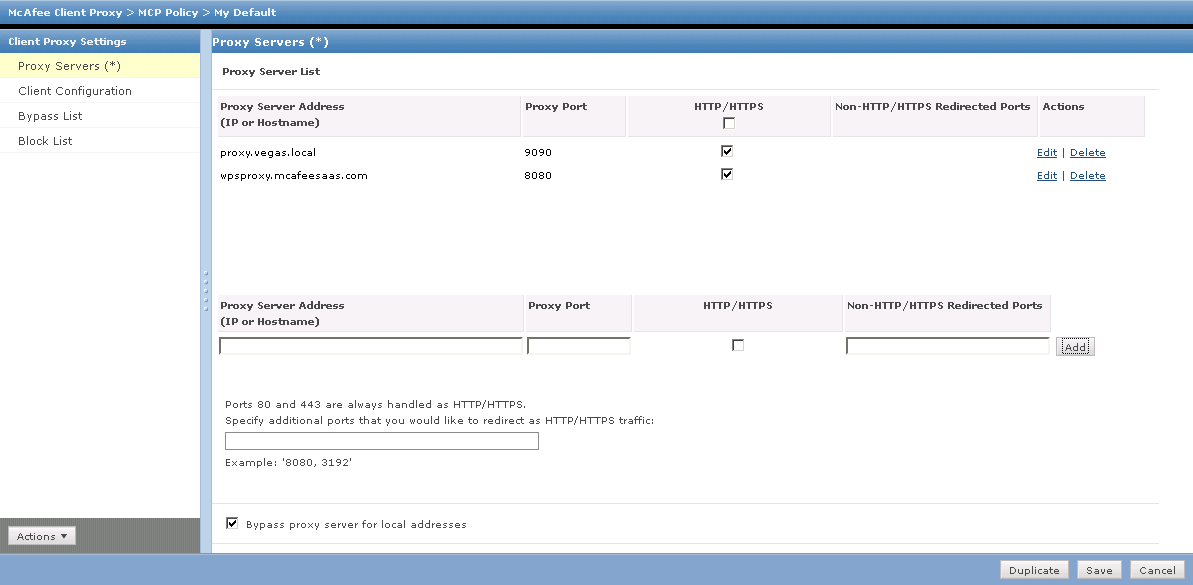
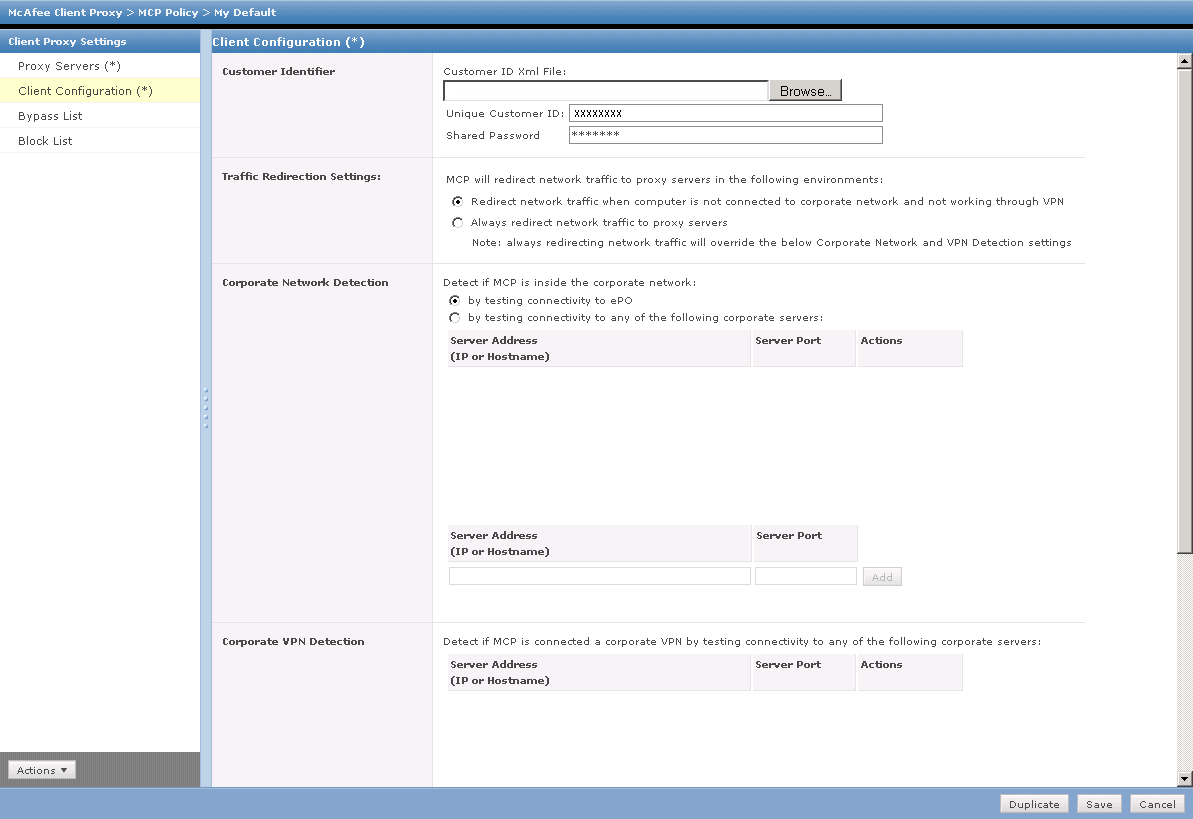
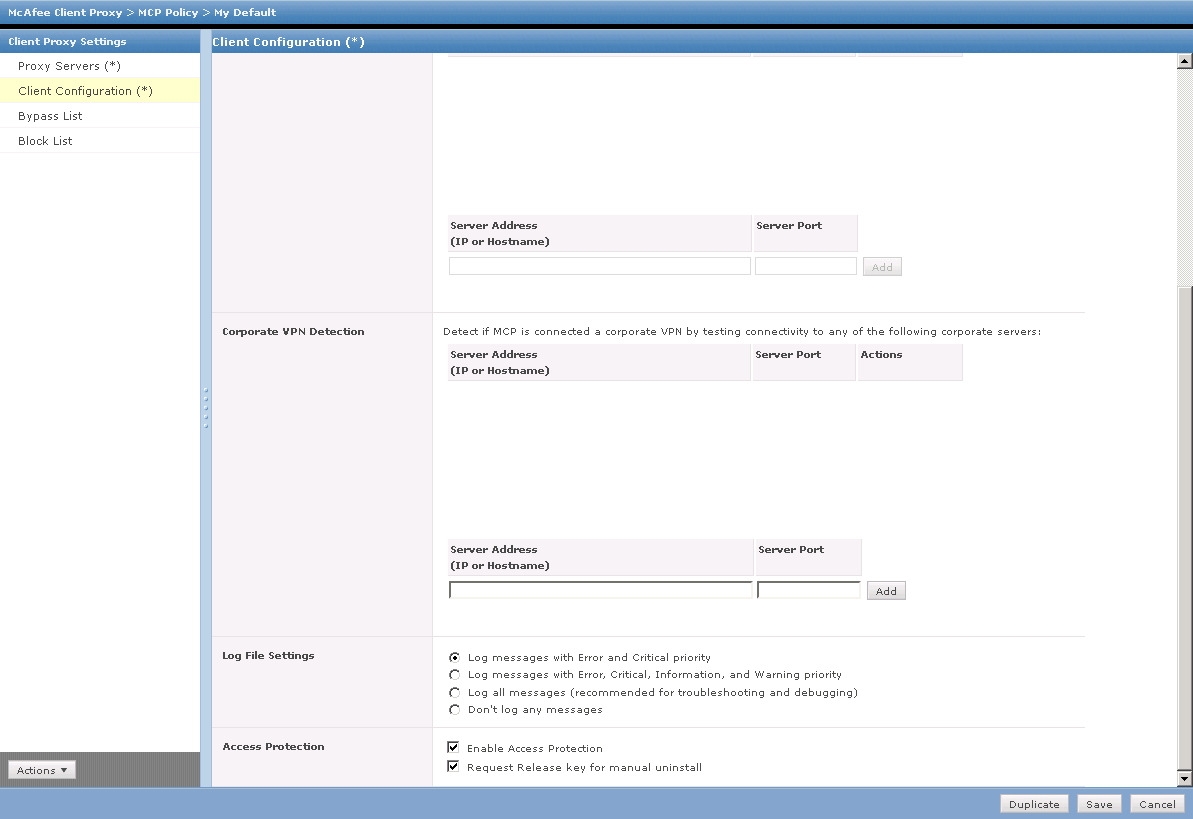
Without ePO (with Control Console)
In order to configure the SCP policy within the SaaS console, you must navigate to Web Protection > Policies > Client Proxy Policies, then click New/Edit to configure a policy for download and use within SCP.
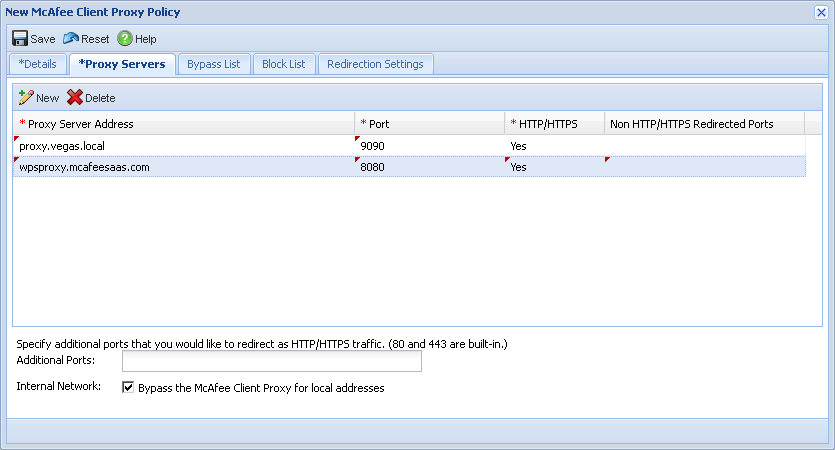
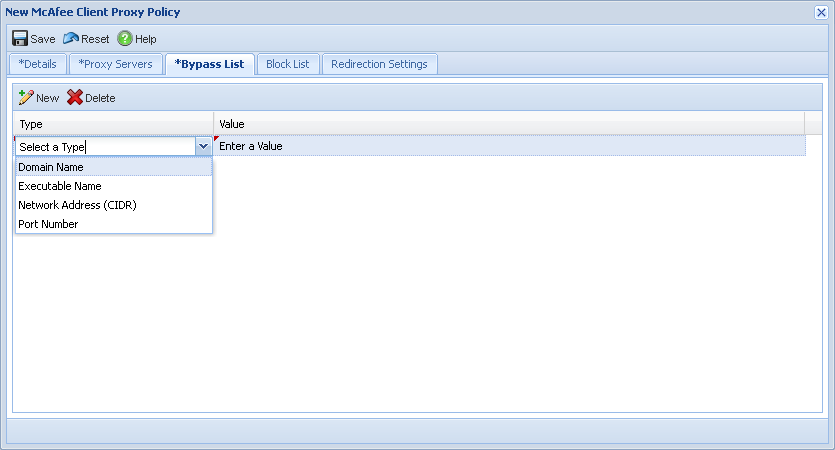
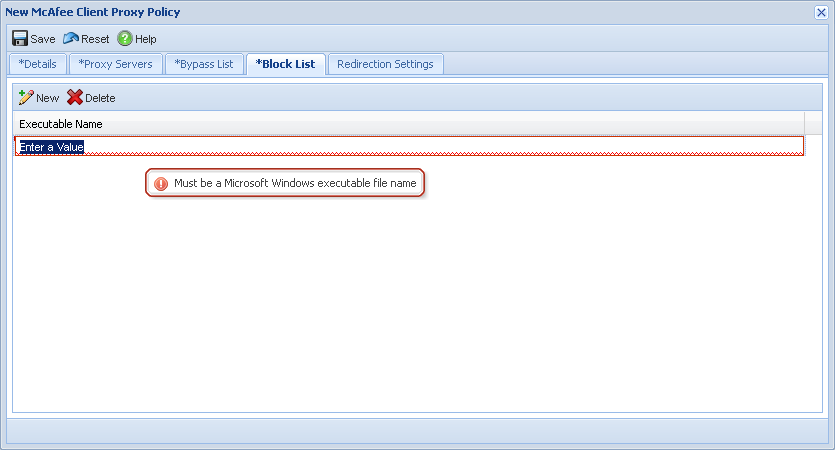
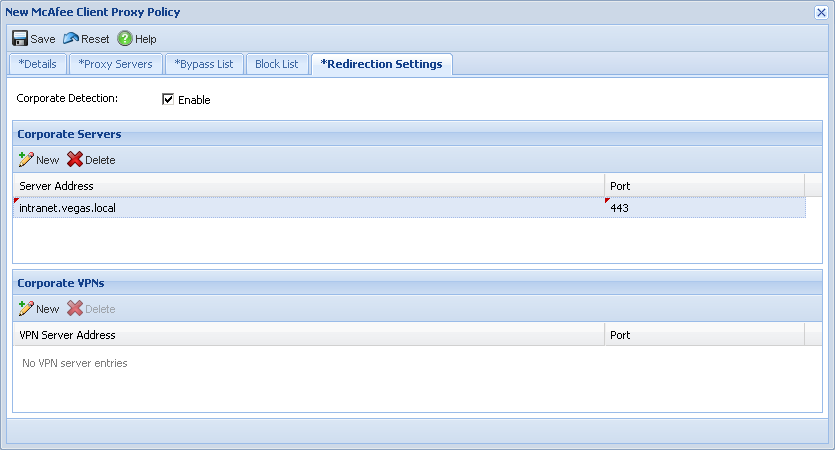
Deploy SCP Policy
In order for your settings to take effect on SCP you must push them to the client, this is easiest done with Trellix ePO.
With ePO
To deploy the policy, you will need the Agent installed on the workstation as well as the SCP software. Assuming all of the prerequisites are met, then it is just a matter of waking up the agents.
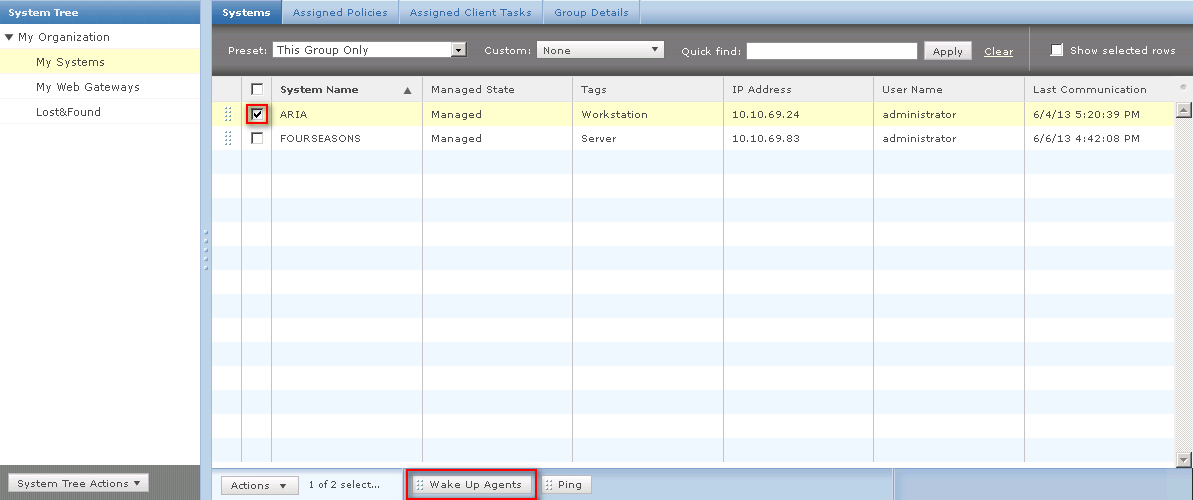
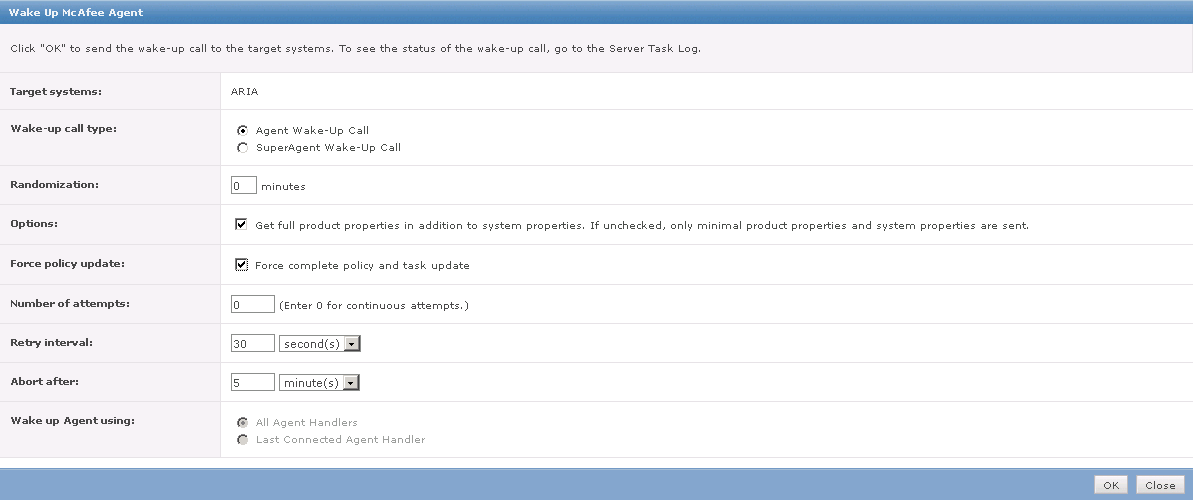
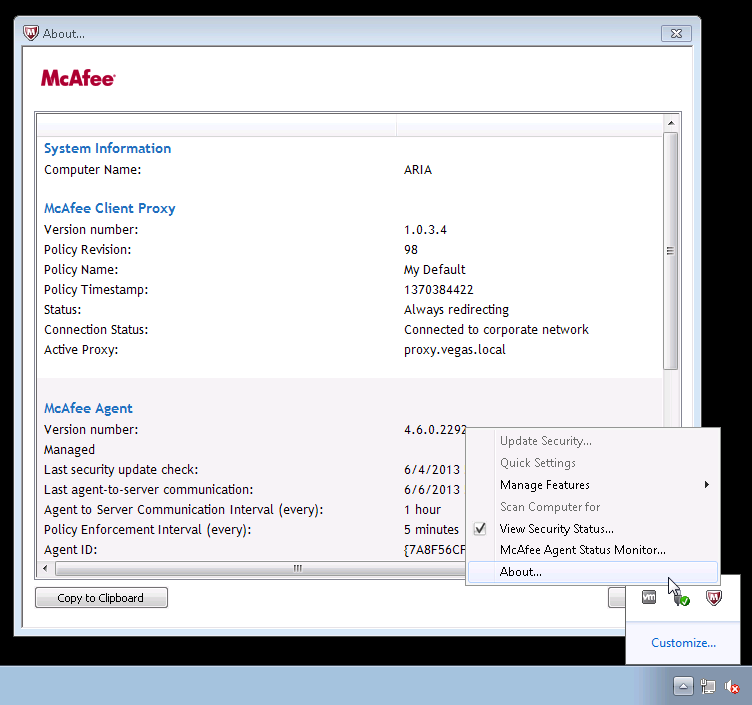
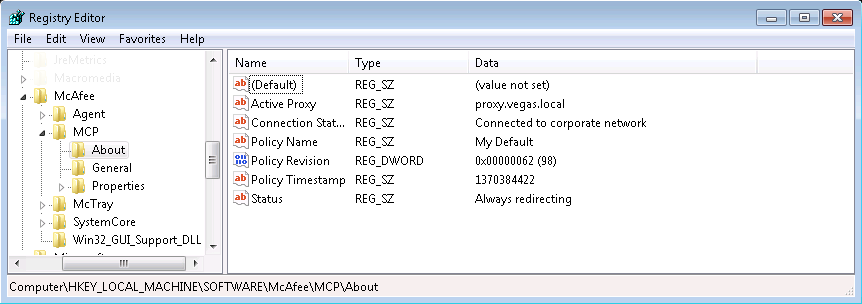
The SCP policy file should now be on the workstation, and the configuration should be active. To verify, check you can check the Agent page or registry:
Troubleshooting
Below is a list of common items that you may want to check for when using SCP.
Checking policy version
It is always a good idea to check the policy version in Trellix ePO, to make sure it is the same version that is on the client. If the client is not receiving the most up-to-date policy file, then they could be being directed to old proxies, or bypasses may not take effect as expected.
In ePO
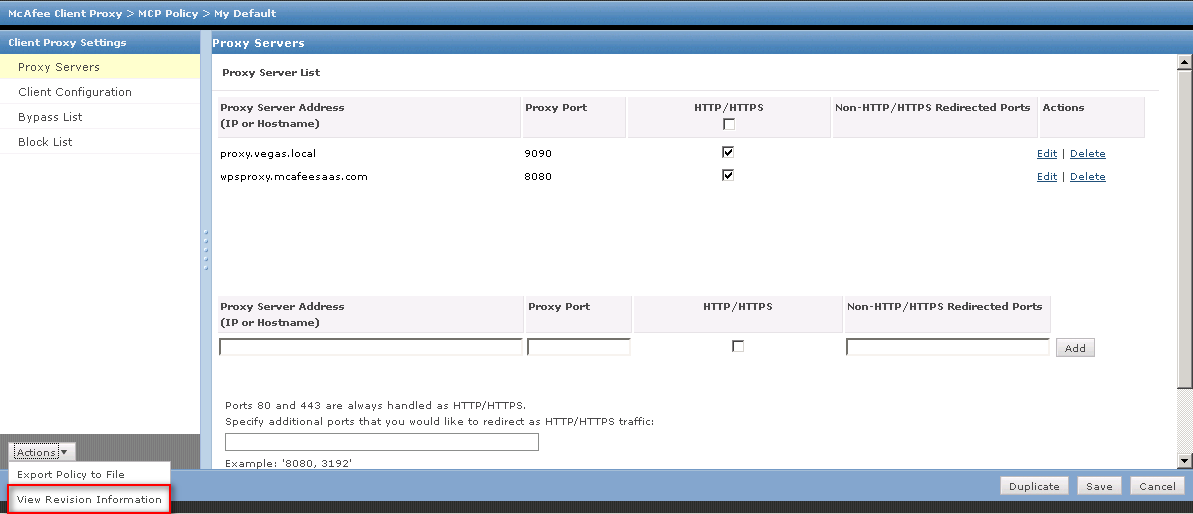
To check the version information in Trellix ePO simply navigate to the SCP policy. This can be found by navigating to Menu > Policy > Policy Catalog, then select "Client Proxy" from the "Product" dropdown, then select your policy. In the bottom left corner there is an "Actions" button, this will allow you to export the policy or view the version. See screenshots below:
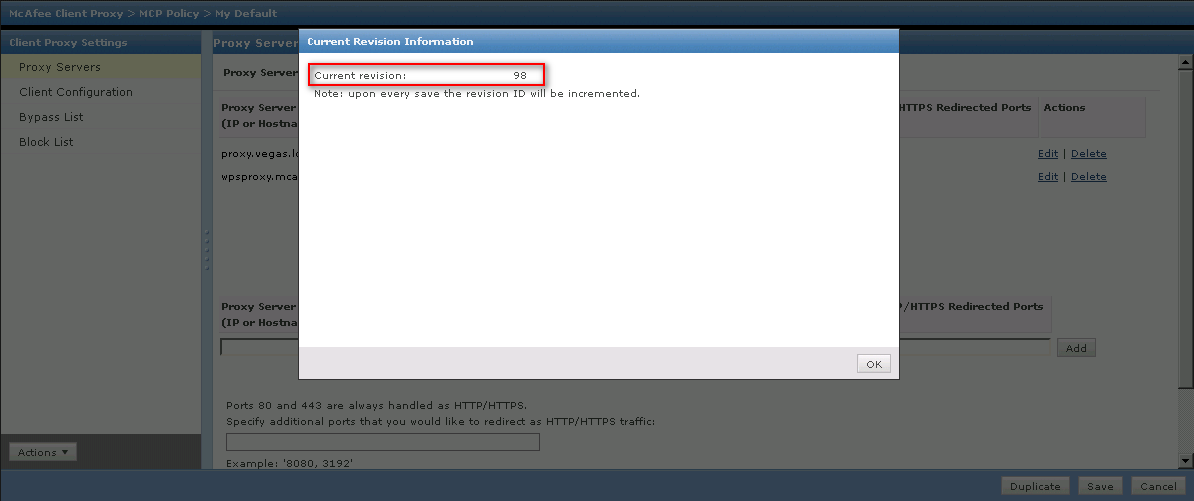
On the client
Once you have checked the policy version in Trellix ePO, you should check the version on the client. This can be done in the Agent about page, or from the registry. See screenshots below:
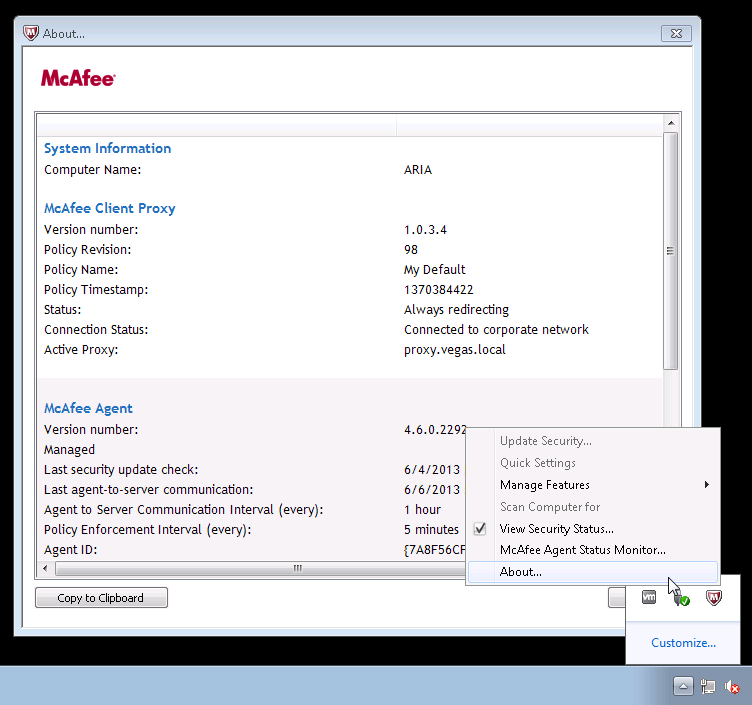
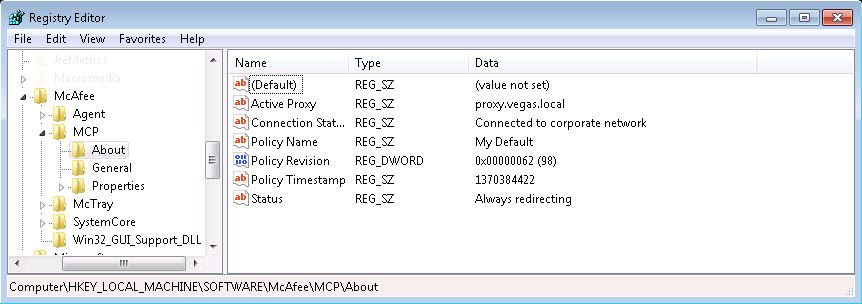
Log locations
# SCP Log Files:
-Scp.log (Client Proxy main log file):
%ALLUSERSPROFILE%\McAfee\MCP\Logs (WinXP/Vista/Win7)
C:\Documents and settings\All Users\Application Data\McAfee\MCP\Logs (WinXP)
C:\ProgramData\McAfee\MCP\Logs (Vista/Win7)
-Mcp.log.1 (Client Proxy rollover log file):
%ALLUSERSPROFILE%\McAfee\MCP\Logs (WinXP/Vista/Win7)
C:\Documents and settings\All Users\Application Data\McAfee\MCP\Logs (WinXP)
C:\ProgramData\McAfee\MCP\Logs (Vista/Win7)
# SCP Policy Files (from client and ePO):
-MCPPolicy.opg (Current policy file (protected by access protection))
%ALLUSERSPROFILE%\McAfee\MCP\Policy (WinXP/Vista/Win7)
C:\Documents and settings\All Users\Application Data\McAfee\MCP\Policy (WinXP)
C:\ProgramData\McAfee\MCP\Policy (Vista/Win7)
-MCPPolicy.opg (Temporary policy file (protected by access protection))
%ALLUSERSPROFILE%\McAfee\MCP\Policy\Temp (WinXP/Vista/Win7)
C:\Documents and settings\All Users\Application Data\McAfee\MCP\Policy\Temp (WinXP)
C:\ProgramData\McAfee\MCP\Policy\Temp (Vista/Win7)
Group related features and off-network problems
SCP sends group information to the proxy it is communicating to. In some cases a user may be a part of a large number of groups (which are not important for web filtering) OR SCP may not be able to determine the groups.
Group inclusion/exclusion
SCP has options to include important groups, or discard insignificant groups. This is configured in the "Client Configuration" section of the policy.
Some companies create special group memberships which grant you specific types of access to the internet. So if "jsmith" is a part of "Internet Relaxed Users", then he receives different filtering from "jdoe" who is a part of "Internet Strict Users".
To check the groups of a user one can run the command "whoami /groups" or"gpresult /R /SCOPE USER":
>whoami /groups
GROUP INFORMATION
Group Name
============================================
Everyone
BUILTIN\Administrators
BUILTIN\Users
BUILTIN\Certificate Service DCOM Access
BUILTIN\Pre-Windows 2000 Compatible Access
NT AUTHORITY\REMOTE INTERACTIVE LOGON
NT AUTHORITY\INTERACTIVE
NT AUTHORITY\Authenticated Users
NT AUTHORITY\This Organization
LOCAL
VEGAS\Internet Relaxed Users <------------- INTERESTED GROUP
VEGAS\Group Policy Creator Owners
VEGAS\Domain Admins
VEGAS\Enterprise Admins
VEGAS\Schema Admins
VEGAS\Denied RODC Password Replication Group
The below screenshot shows an example of inclusion, whereby we instruct SCP to only send groups which start with "VEGAS\Internet", using the regular expression"VEGAS\\Internet.*" in the filter.
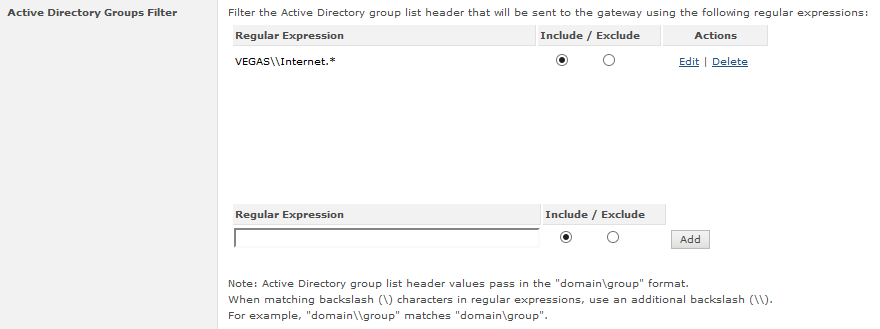
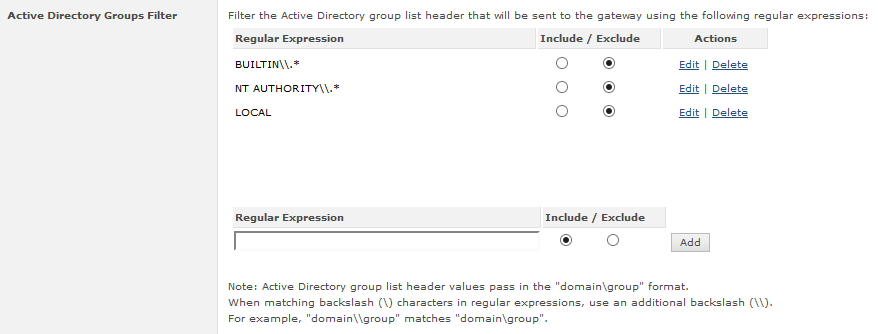
The below screenshot shows an example of exclusion, whereby we instruct SCP to discard groups which start with "BUILTIN\", "NT AUTHORITY\", and "LOCAL", using the regular expressions of "BUILTIN\\.*", "NT AUTHORITY\\.*", and "LOCAL" in the filter.
Groups are not sent by SCP
As stated, SCP will forward group membership information to the proxies that are configured in the policy. If the user has not logged into the corporate network recently,then SCP may not be able to resolve the users' group memberships. This can cause issues for the relying proxy if it performs filtering based on group membership.
To resolve this, one must perform a group lookup based on the username given by SCP. See the following modified SCP ruleset from.
Conclusion
By reading this article you should now understand the use cases for SCP, how to deploy and configure the policy and troubleshoot SCP.
