Skyhigh Security Cloud 6.5.2 Release Notes (Jan 2024)
Legends Used
|
General Availability |
Skyhigh Cloud Platform
Skyhigh Data Loss Prevention (DLP)
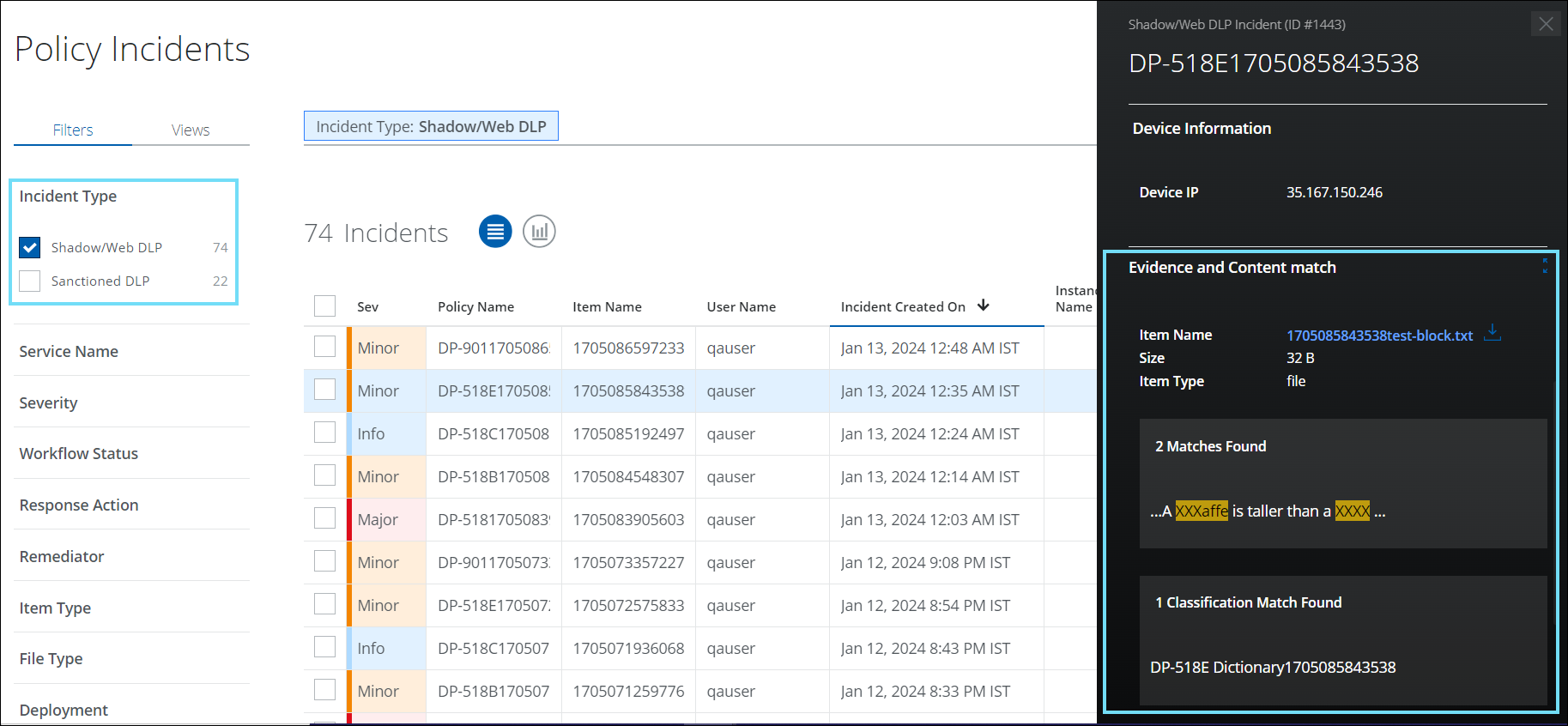
Download Web Evidence files via Shadow/Web DLP Incident Cloud Card 
You can now download web evidence files for DLP incidents individually from the Shadow/Web DLP Policy Incident Cloud Card (found under Incidents > Policy Incidents > Policy Incidents page). Once evidence files are downloaded, you can view the details of the violated DLP incidents and perform additional forensics on the generated incidents. For details, see Download DLP Evidence.
The process of downloading web evidence files from individual DLP incidents is made more secure and controllable by applying Role-Based Access Control (RBAC). RBAC ensures that only authorized users within a tenancy are granted access to download evidence files for DLP incidents, thereby providing an additional layer of security to the overall download process. For details, see About User Roles and Access Levels.
For example, a Security Operations Center (SOC) may want to limit the download of evidence files for DLP incidents on the Policy Incidents page to designated users only. To achieve this, the SOC can assign the Incident Management role and Download Evidence permission to specific users, granting them the ability to download evidence files for DLP incidents. This way, only authorized users can access sensitive information related to DLP incidents, minimizing the risk of data breaches.
Query Incidents API with Status 
You can now query the Incidents API using specific statuses. The Incidents API allows you to filter incident criteria fields based on the status. As a result, DLP SOC admins can quickly and efficiently retrieve incidents related to a specific status and take remediation action. This improves operational efficiency, reduces response time, and ensures incidents are identified and resolved promptly. Consequently, the risk of data breaches is reduced, and the impact on the organization is minimized. For details, see Incidents API Definitions.
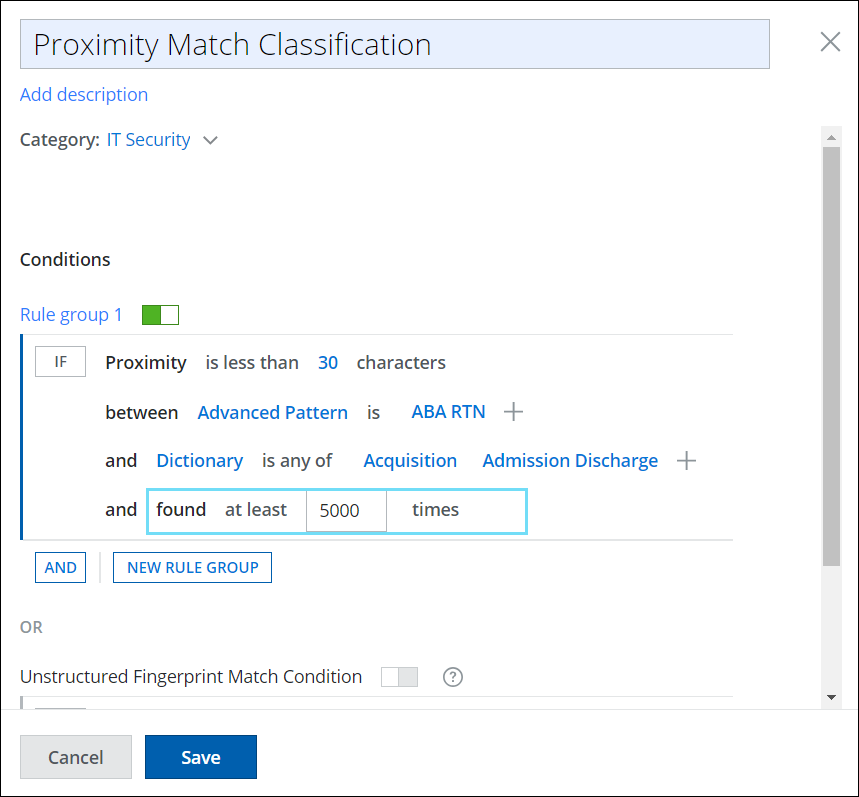
Extended Proximity Rule Limit in Classification 
The limit for classification-based proximity rules has been increased from 99 to 5000, allowing users to create more complex rules for identifying sensitive data in large documents. Additionally, the proximity rule limit is consistent across EDM fingerprints. You can find the Proximity Rules by navigating to DLP Policies > Classifications > Create/Edit Classification > Conditions > Select Criteria > Proximity. For details, see Create a Classification using Proximity.
Enhanced Classifications UI with IDM Criteria as distinct Rule Group 
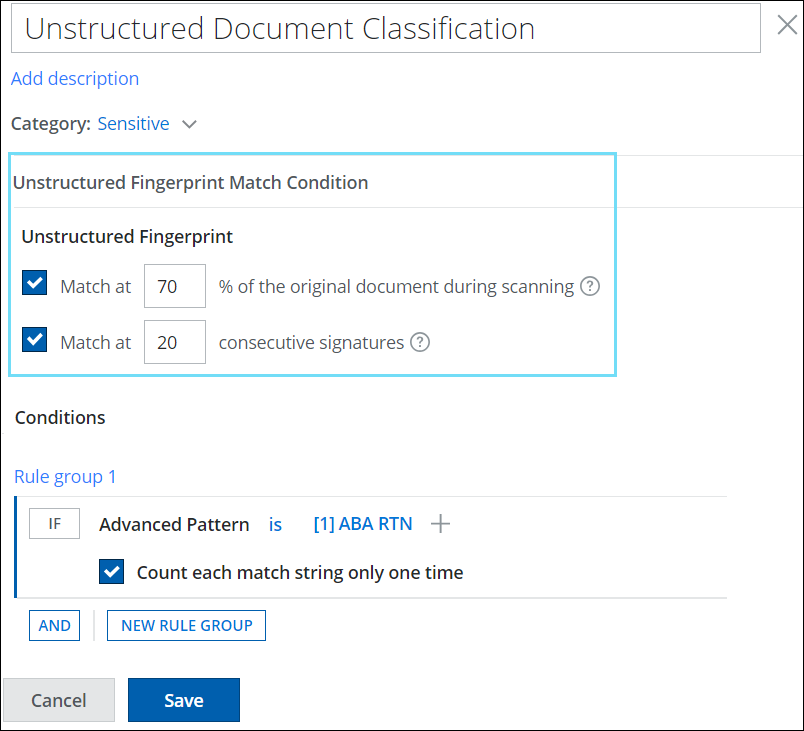
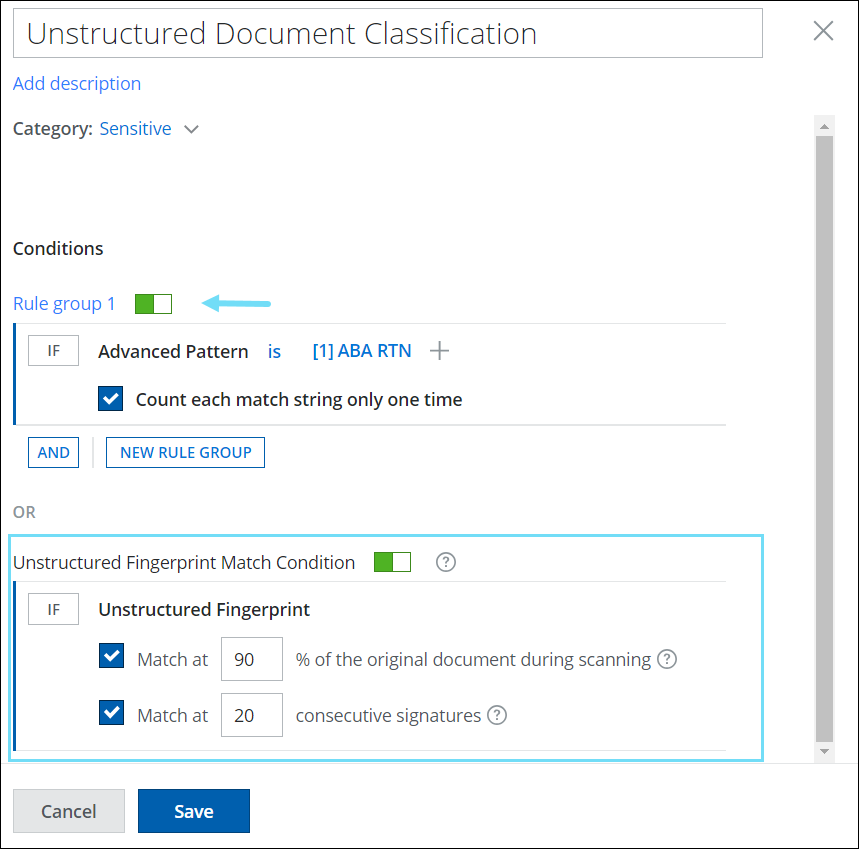
The Classification UI has been improved to support IDM classification as an independent criterion. You can now define IDM match criteria (percentage, consecutive signatures) and content match criteria (dictionaries, keywords, advanced patterns, etc) as distinct rule groups in the classification. This allows you to control the active state of individual rule groups independently. This new enhancement provides greater flexibility and consistency in creating and defining IDM-only classifications and furnishes an effective way to classify and organize your unstructured data. For details, see Create Unstructured Match Condition (IDM) Classification.
To view the enhanced classification UI for IDM, go to DLP Policies > Classifications > Create/Edit Classification > Conditions > Unstructured Fingerprint Match Condition.
| Old UI | Enhanced UI |
|---|---|
|
Unstructured Fingerprint or IDM match criteria (percentage and consecutive signatures) are defined with content match criteria (dictionaries, keywords, advanced patterns, etc.).
|
|
Skyhigh SSE Products
Skyhigh CASB
Dashboard Card for Sanctioned Services 
Skyhigh CASB now includes a default dashboard card that provides real-time visibility into the volume of data associated with unsecured sanctioned cloud services used within your organization. This dashboard card enables you to monitor the number of users for each top unsecured sanctioned cloud service. Based on this information, you can take remediation actions such as allowing or denying these unsecured sanctioned services. For details, see Dashboard Card for Sanctioned Services. 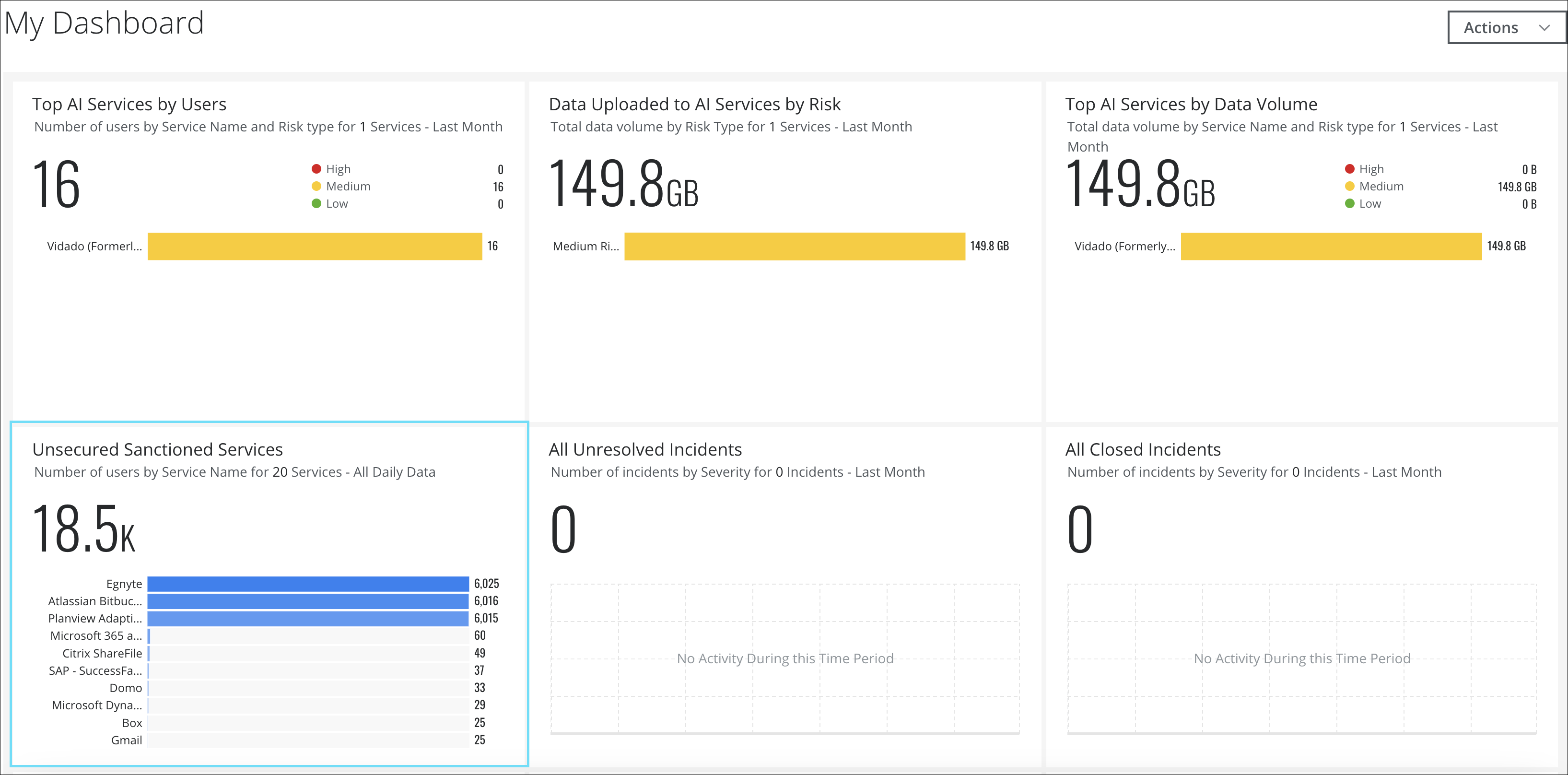
Dictionary Support for Custom Anomaly 
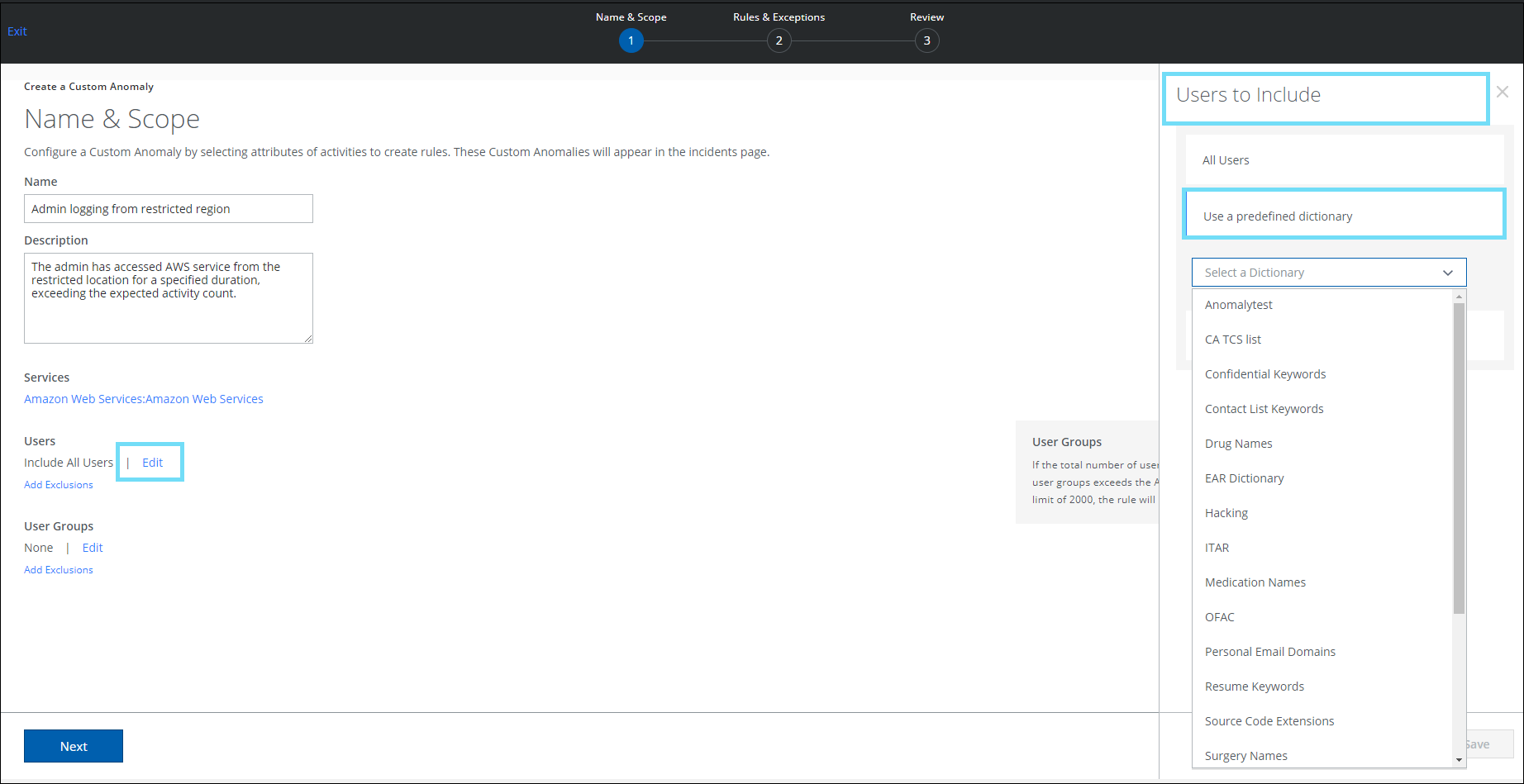
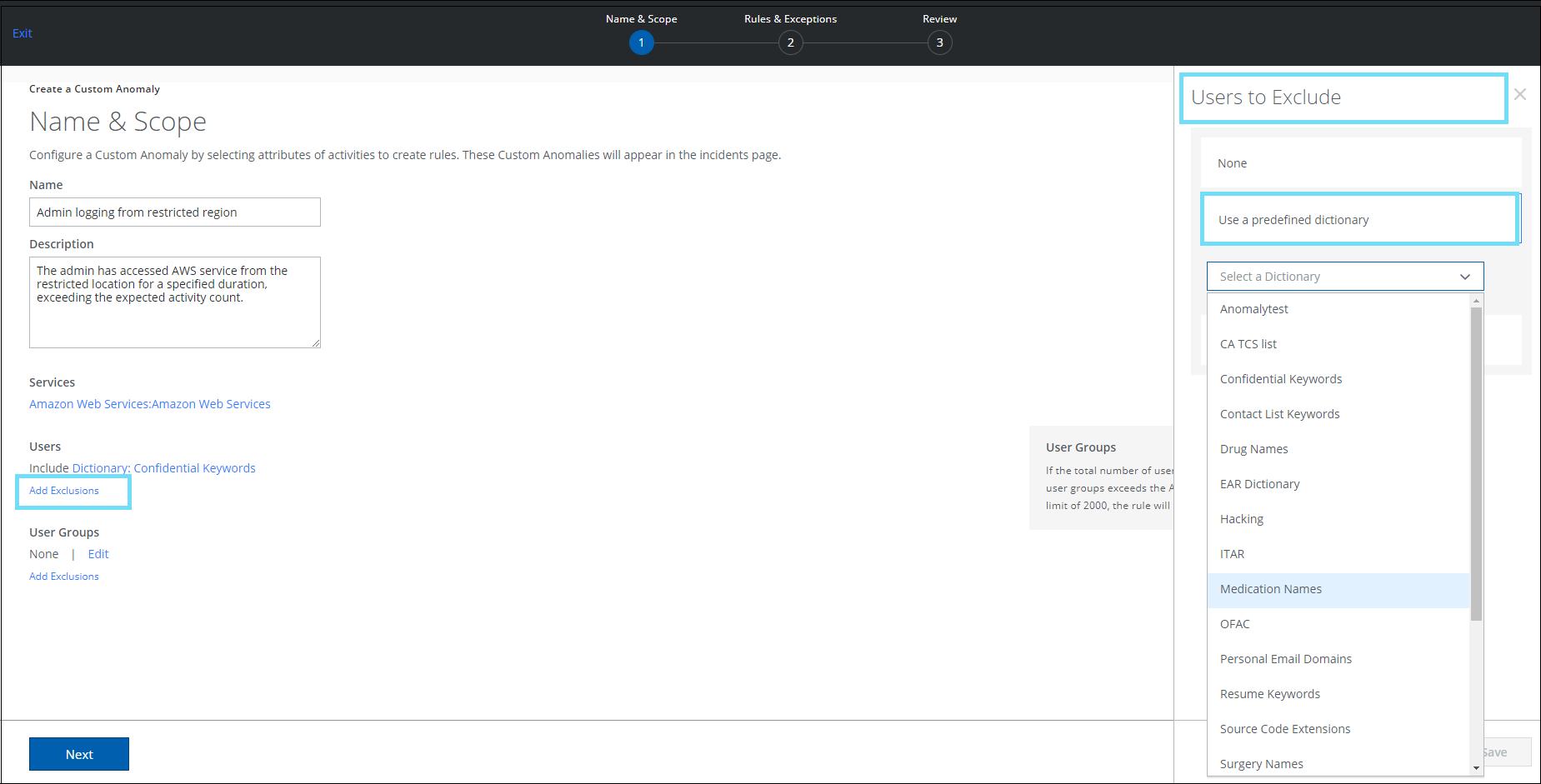
On the Create a Custom Anomaly page (found under Incidents > Anomalies > Anomaly Settings > Actions > Create a Custom Anomaly > Name & Scope), a new option called Use a predefined dictionary has been added. This allows you to include or exclude dictionaries to a custom anomaly rule. The use of a predefined dictionary eliminates the need for manual intervention of adding individual email addresses to a list each time a custom anomaly rule is created. A dictionary contains a list of unique users. For details, see Create a Custom Anomaly.
NOTES:
- The Custom Anomaly Policy rules only support the Free Form Text dictionary types.
- From the list of predefined dictionaries, only one dictionary can be selected for inclusion and exclusion.
- Include and Exclude options must not have the same predefined dictionary in the rules.
Refer to the below table to include or exclude users for the Custom Anomaly Policy rule:
| Users to Include | Users to Exclude |
|---|---|
|
To include a group of users in a rule, select a predefined dictionary from the list of Free Form Text dictionaries. |
To exclude a group of users in a rule, select a predefined dictionary from the list of Free Form Text dictionaries. |
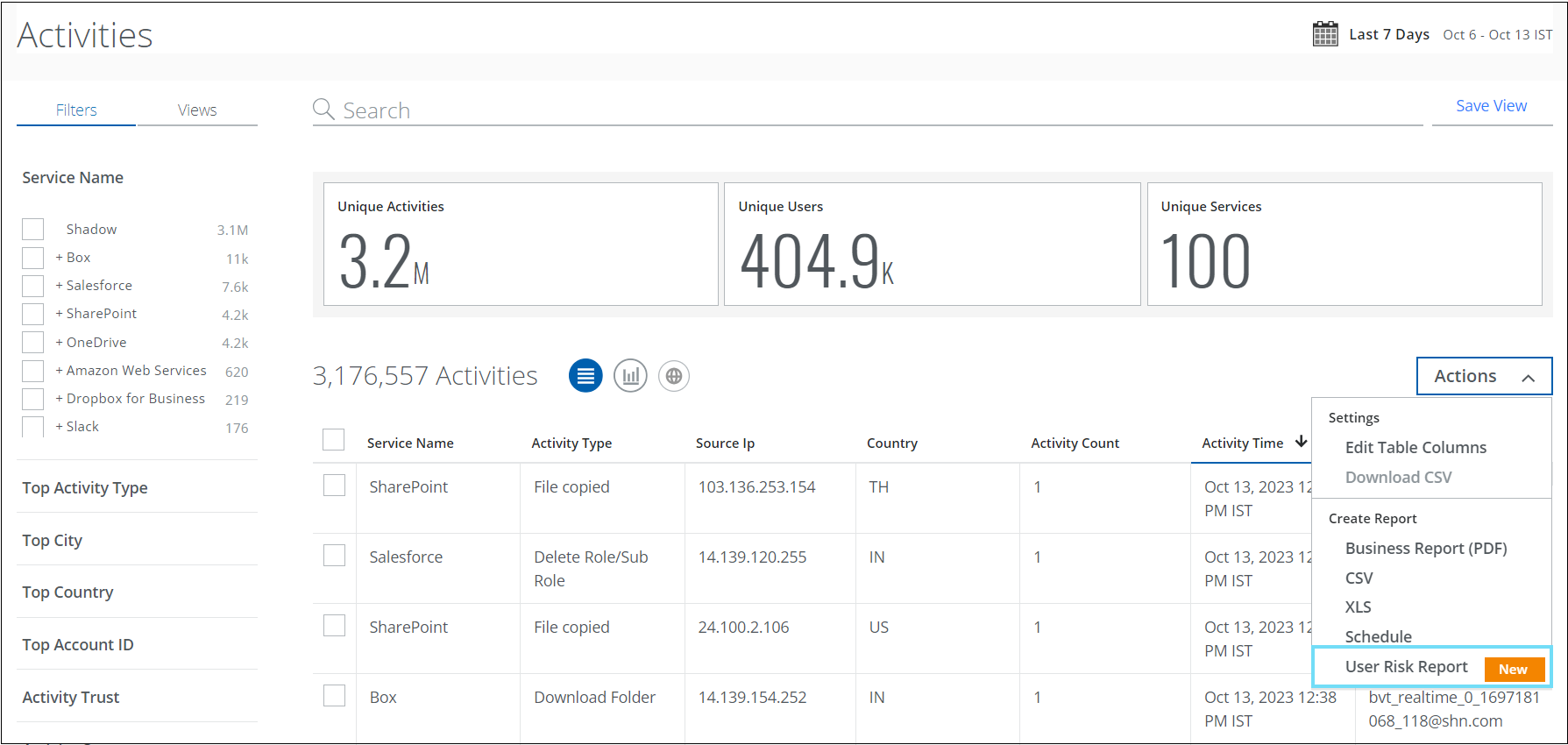
Sanctioned User Risk Report 
You can now generate and download the User Risk Report for sanctioned cloud services in the CSV or XLSX format from the Policy Incidents, Activities, Threats, and Anomalies pages. This report allows you to identify high, medium, and low-risk users in your organization. You can generate a report or schedule a frequency to run the report.
Sanctioned User Risk Report can be accessed through the various pages of the Skyhigh CASB user interface. The table below lists the Skyhigh CASB user interface pages and their navigation path:
| User Risk Report on Skyhigh CASB UI Pages | Navigation Path |
|---|---|
| Policy Incidents | Incidents > Policy Incidents > Policy Incidents > Actions > User Risk Report (Policy Incidents Page) |
| Activities | Incidents > User Activity > Activities > Actions > User Risk Report (About Activities) |
| Threats | Incidents > Threats > Actions > User Risk Report (Threats Page) |
| Anomalies | Incidents > Anomalies > Anomalies > Actions > User Risk Report (About Anomalies) |
After report generation, an email is sent to the recipients with the attached report. A report is attached to the email only if the file size is less than 25 MB, else a link will be provided with the email to download the report from the Report Manager. The report includes user details such as username, user email, user risk score, number of incidents, threats, anomalies, activities, Active Directory (AD) attributes, and more.
For details, see Policy Incidents Page, About Activities, Threats Page, and About Anomalies.
NOTE: User Risk Report includes data from the last 100 days.
Support for AI Sub-Categories on Cloud Registry 
For better classification of AI services, the Skyhigh CASB has now introduced 17 new sub-categories under the AI services for shadow IT users (found under Governance > Cloud Registry). The AI sub-categories allow you to differentiate the AI services within the Cloud Registry. These AI sub-categories cater to specific needs such as Machine learning, Natural language processing, Health care and Medical diagnosis, Financial trading, HR/Job assistance, and more. This categorization enables you to generate more meaningful reports and insights related to Saved Views, and Dashboard cards. You can integrate these AI sub-categories into your applications to enhance your application with AI capabilities. For details, see Cloud Service Categories.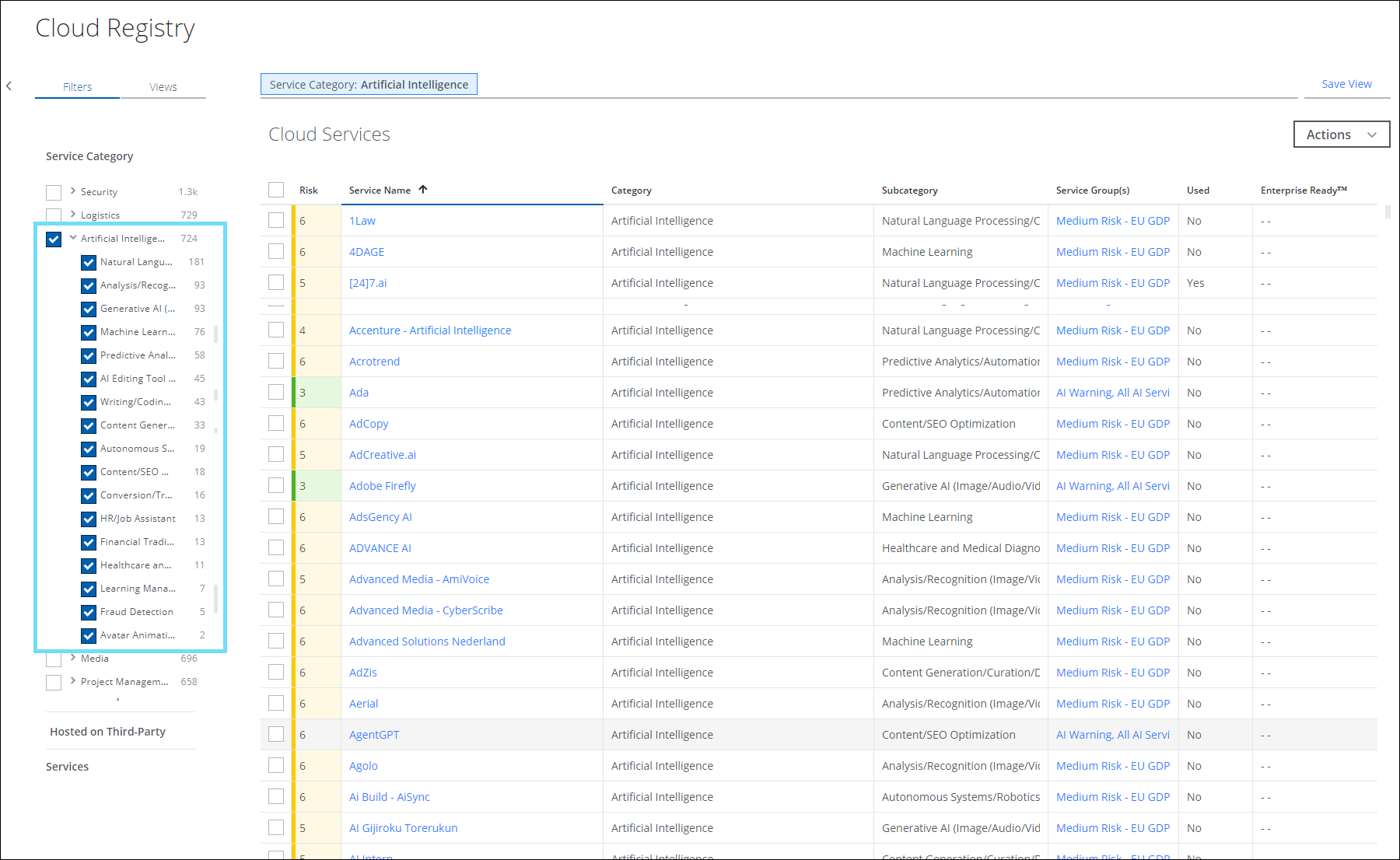
Audit Logs on the Skyhigh SAML Configuration Page 
The SAML Configuration operates from two different places, one from the Trellix Identity Provider (found under the product selection) page and the other from the User Management section within the Skyhigh dashboard (found under Settings > User Management > SAML Configuration).
The Skyhigh SAML Configuration page has now been enhanced to capture the audit logs for the modifications that occur on the Trellix Identity Provider page. If a new SAML configuration is created, or an existing configuration is updated or deleted on the Trellix Identity Provider page, the events are recorded within the audit log (found under Settings > Audit Log). You can monitor, track, and record the activities performed on the configuration page and also identify potential security issues to mitigate the risks if any. For details, see Primary User - Identity Provider.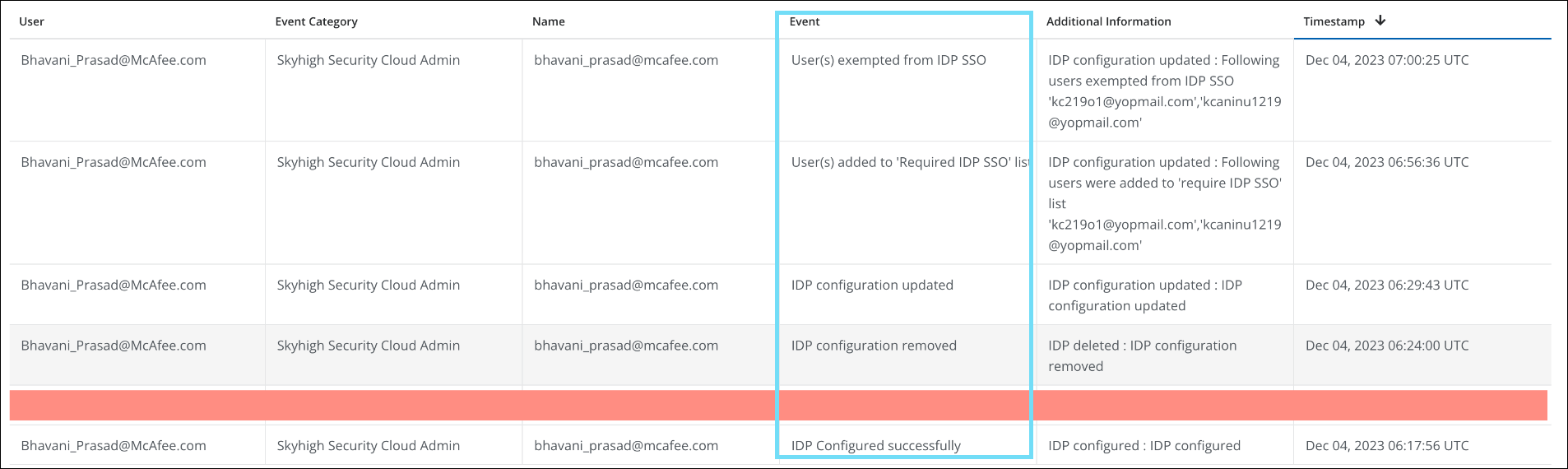
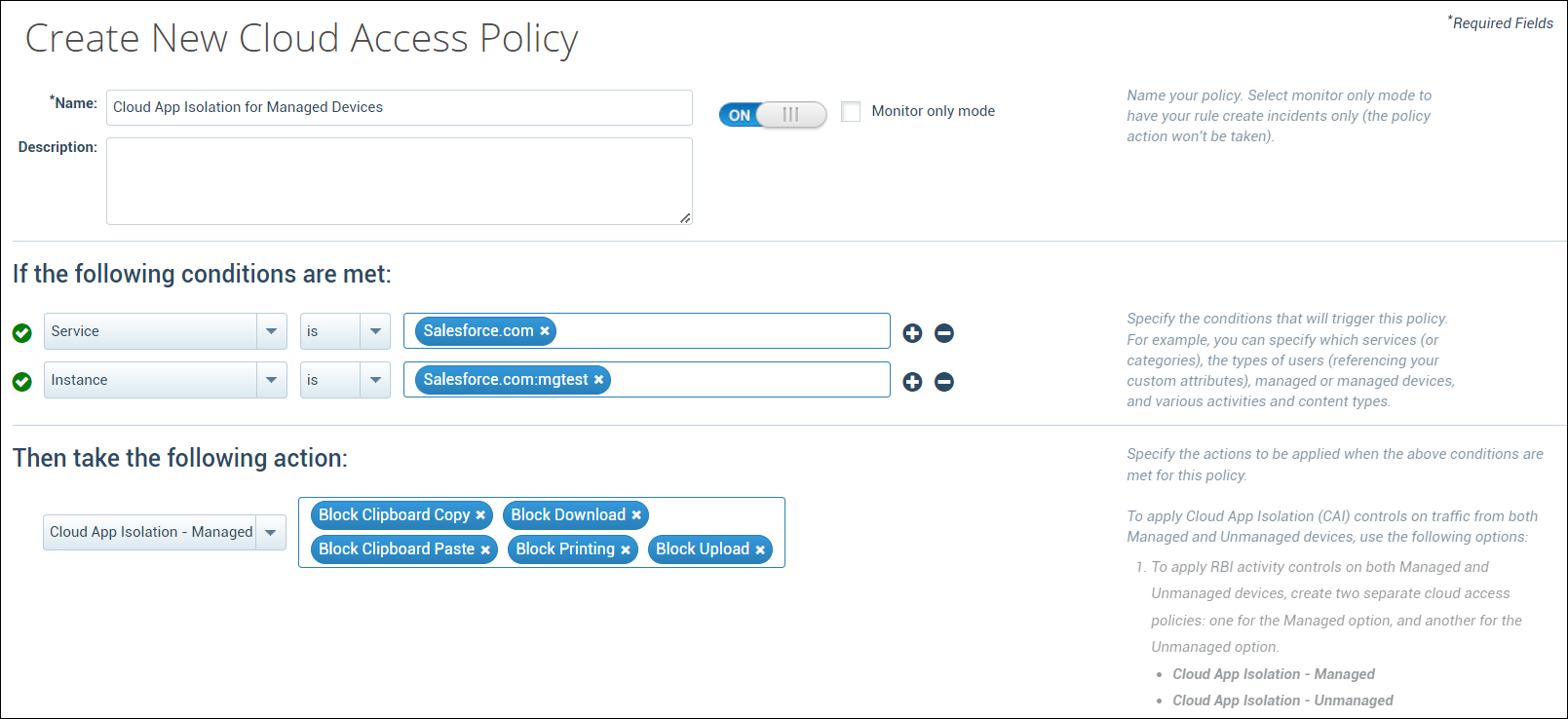
Support for Cloud App Isolation (Managed Devices) 
Skyhigh CASB now provides support for traffic originating from managed devices via Cloud Application Isolation (CAI) controls. You can use the add-on SKU named Cloud App Isolation – Unmanaged Addon to apply CAI controls only on unmanaged devices, or the standalone SKU named Cloud App Isolation SKU (RP-RBI Managed) to apply CAI controls on both managed and unmanaged devices. For details, see Cloud Activity Controls with CAI.
Enhanced User Risk Filter on Threats and Anomalies page 
The User Risk filter has been enhanced with two more options, Low and Medium in addition to the existing filter (High) for sanctioned users to display all the users with potential risks. You can now filter and categorize your search by User Risk score for Low, Medium, and High-risk users on the Threats (found under Incidents > Threats) and Anomalies (found under Incidents > Anomalies > Anomalies) page. For details, see the Threats Page and About Anomalies page.
For example, on the Anomalies page, to display the anomalies associated with low-risk users, select Low on the User Risk filter. If there are no anomalies for the low-risk users in your tenant, then no anomalies will be displayed.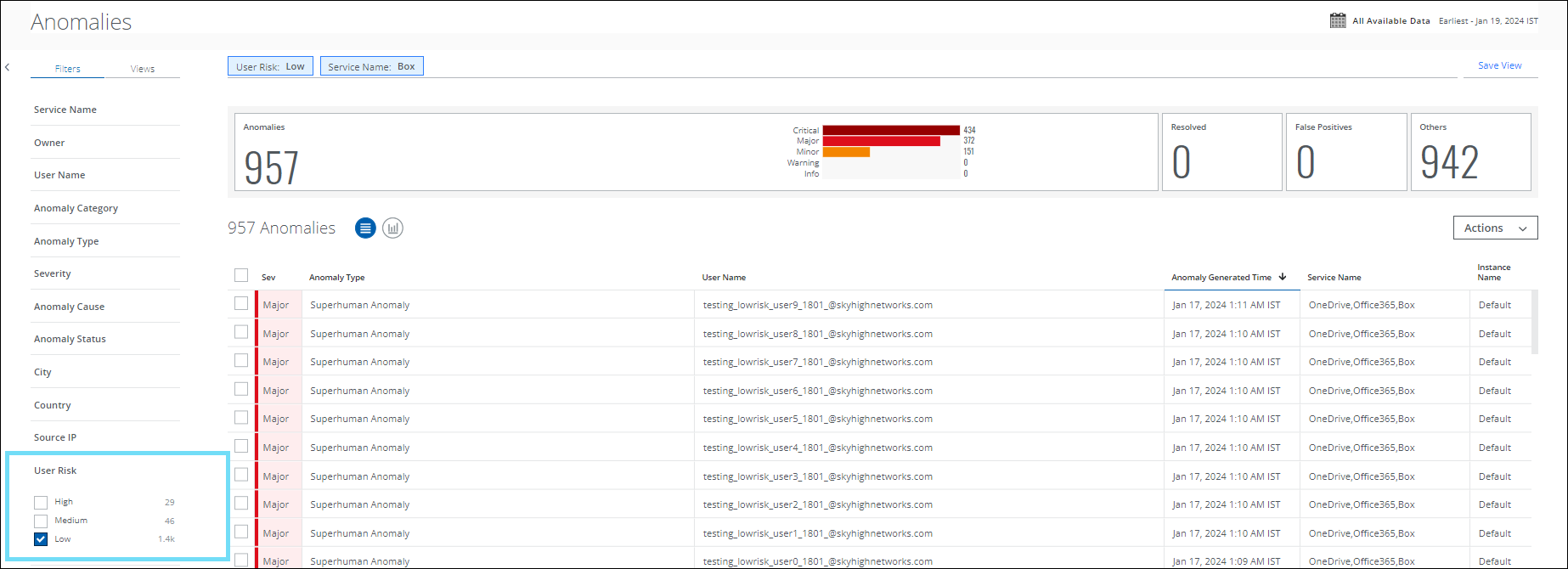
Resolved and Known Issues
 Click here to view Resolved and Known Issues
Click here to view Resolved and Known Issues- For details, see Skyhigh Security Cloud Bug Fixes and Known Issues.