Skyhigh Security Cloud Release Notes 6.4.2 (Sep 2023)
|
Legends used: General Availability |
Skyhigh Cloud Platform
Data Loss Prevention (DLP)
Unified Index Document Matching (IDM) 
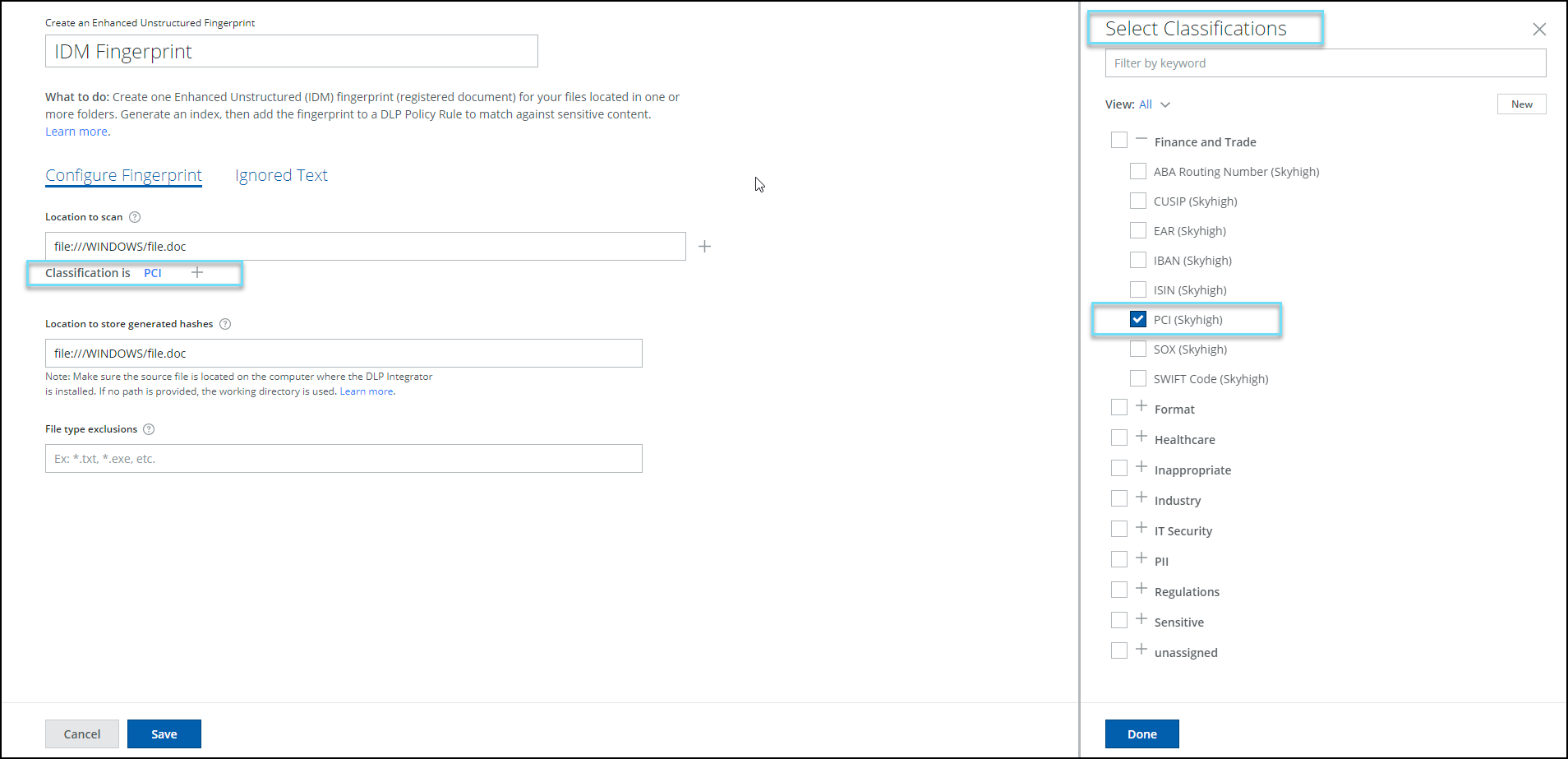
IDM or Enhanced Unstructured Fingerprints (found under Policy > DLP Policies > DLP Policies > Fingerprints) allows you to protect your organization’s sensitive data stored in Word, PDF, PowerPoint, Images, or CAD documents. The organization-identified potentially sensitive or confidential data is fingerprinted in the customer's environment and only the hashes are securely transferred to Skyhigh for use in classifications for Skyhigh CASB & Web DLP rules. IDM starts to extract, normalize, and secure the text and data using multiple overlapping hashes.
Now you can also further reduce false positives with the ability to define ignored text from document matches. The fingerprinting process can be fully automated to provide real-time protection of unstructured sensitive documents.
On the Fingerprints page, go to Create Fingerprint > Unstructured Data Fingerprint > Create Enhanced Fingerprint. For details, see About IDM.
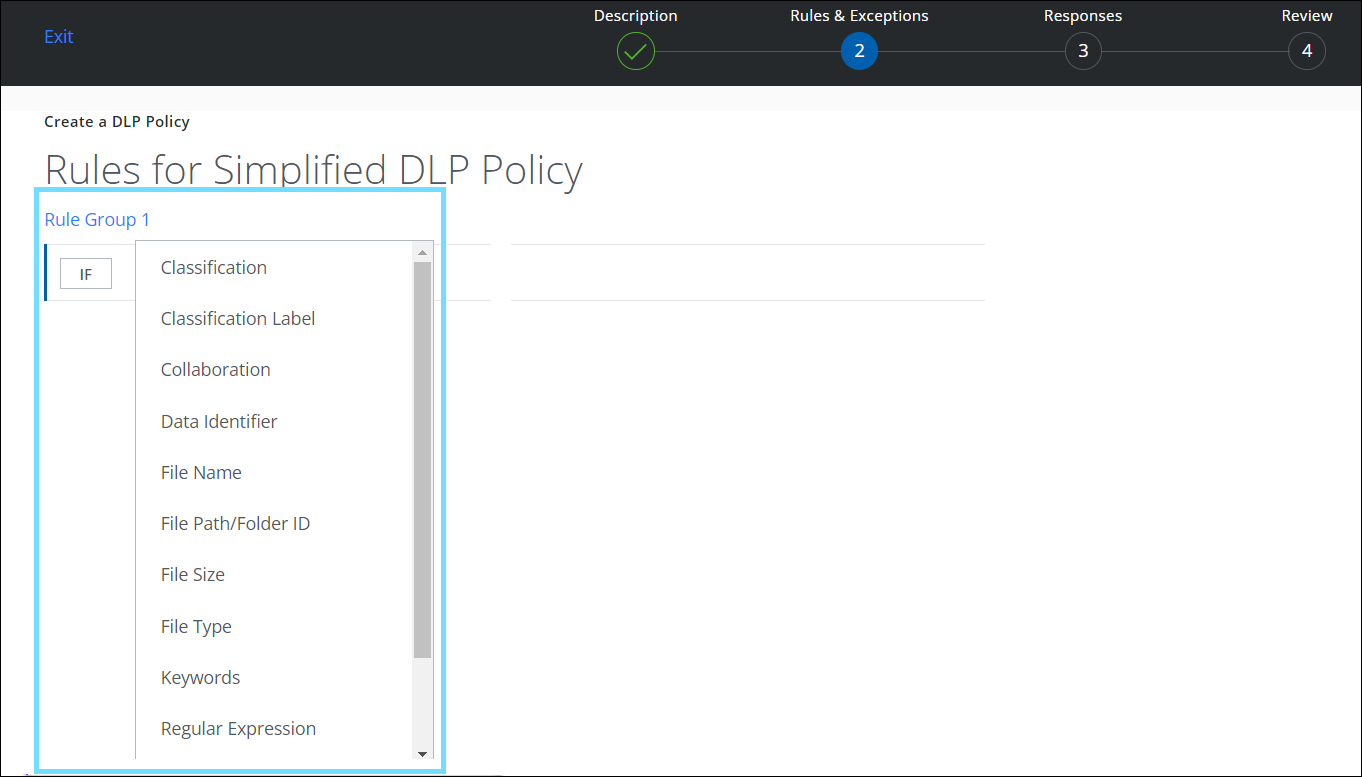
Simplified UI for Sanctioned DLP Policy Editor and Enterprise DLP 
To streamline user experiences, the Classification engine has been removed from the Sanctioned DLP Policy Editor (found under Policy > DLP Policies > DLP Policies > Create/Edit New Policy). Additionally, the option to select Services for Classifications has been removed from the Enterprise DLP (found under Policy > Policy Settings > Enterprise DLP). As a result of these changes, you can now manage your DLP policies more easily which allows you to use the same cloud service across more policies.
NOTE: The simplified user interface changes will not affect DLP Policy's or Enterprise DLP's functionality.
A comparison of the old and the simplified UI can be found in the below table:
|
Old UI |
Simplified UI for SSE 6.4.2 |
|---|---|
|
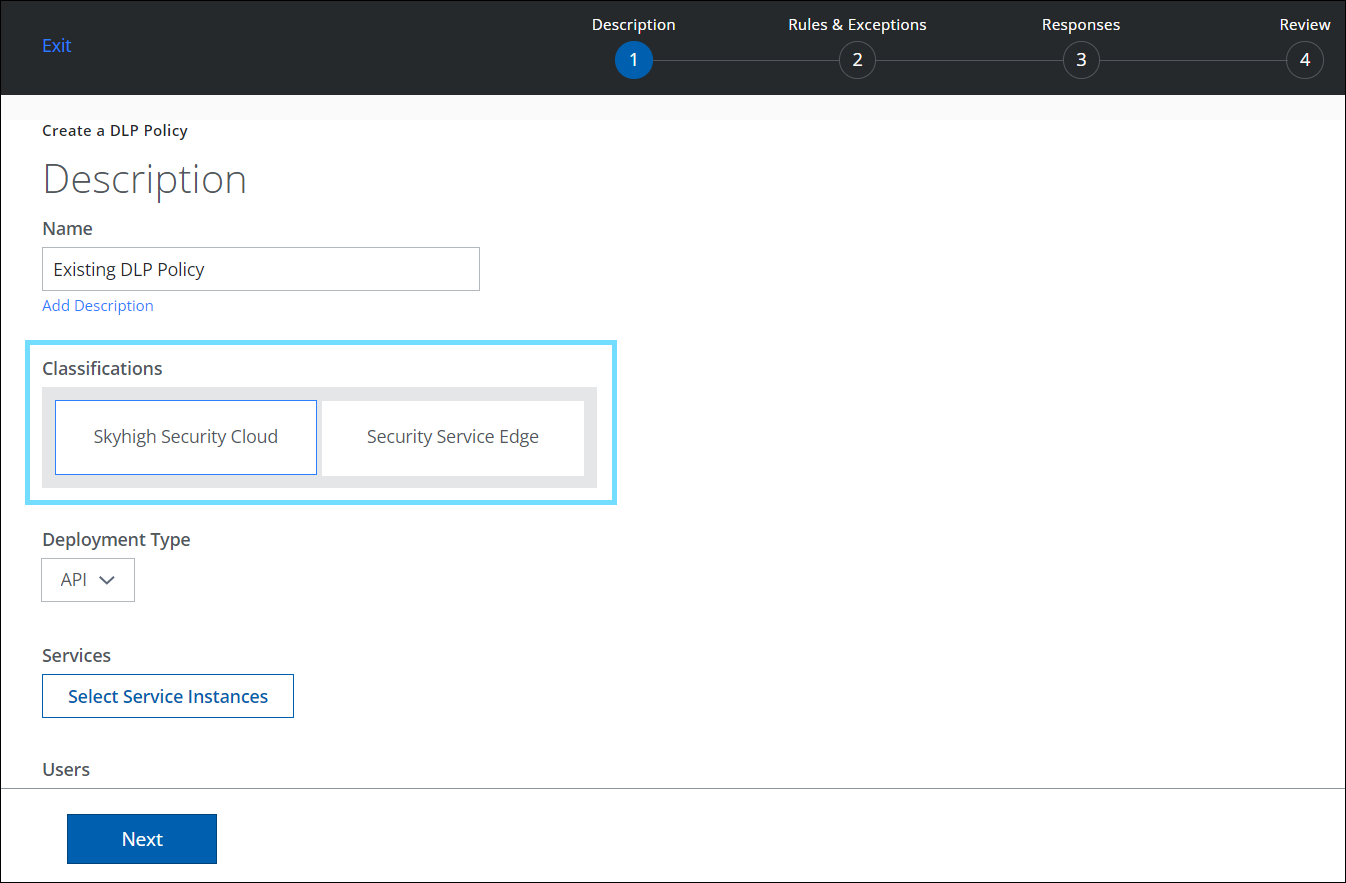
Navigation path: Policy > DLP Policies > DLP Policies > Create/Edit New Policy The Sanctioned DLP Policy editor provides a Classification engine to choose Classification types: Skyhigh Security Cloud (SSC) or Security Service Edge (SSE) /Trellix.
|
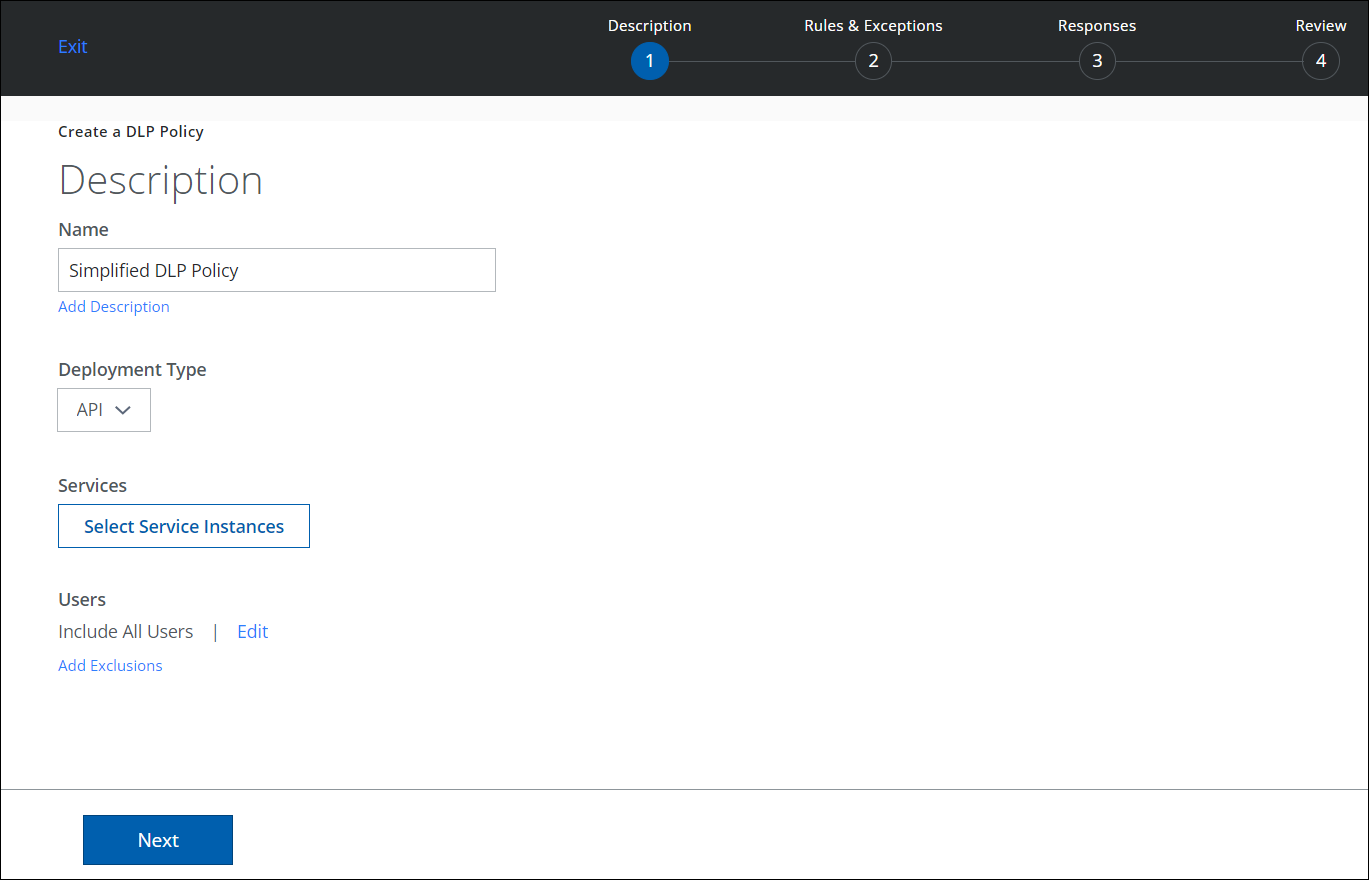
Navigation path: Policy > DLP Policies > DLP Policies > Create/Edit New Policy The Classification engine has been removed from the Sanctioned DLP Policy Editor. To create a DLP policy, see Create a Sanctioned DLP Policy.
|
|
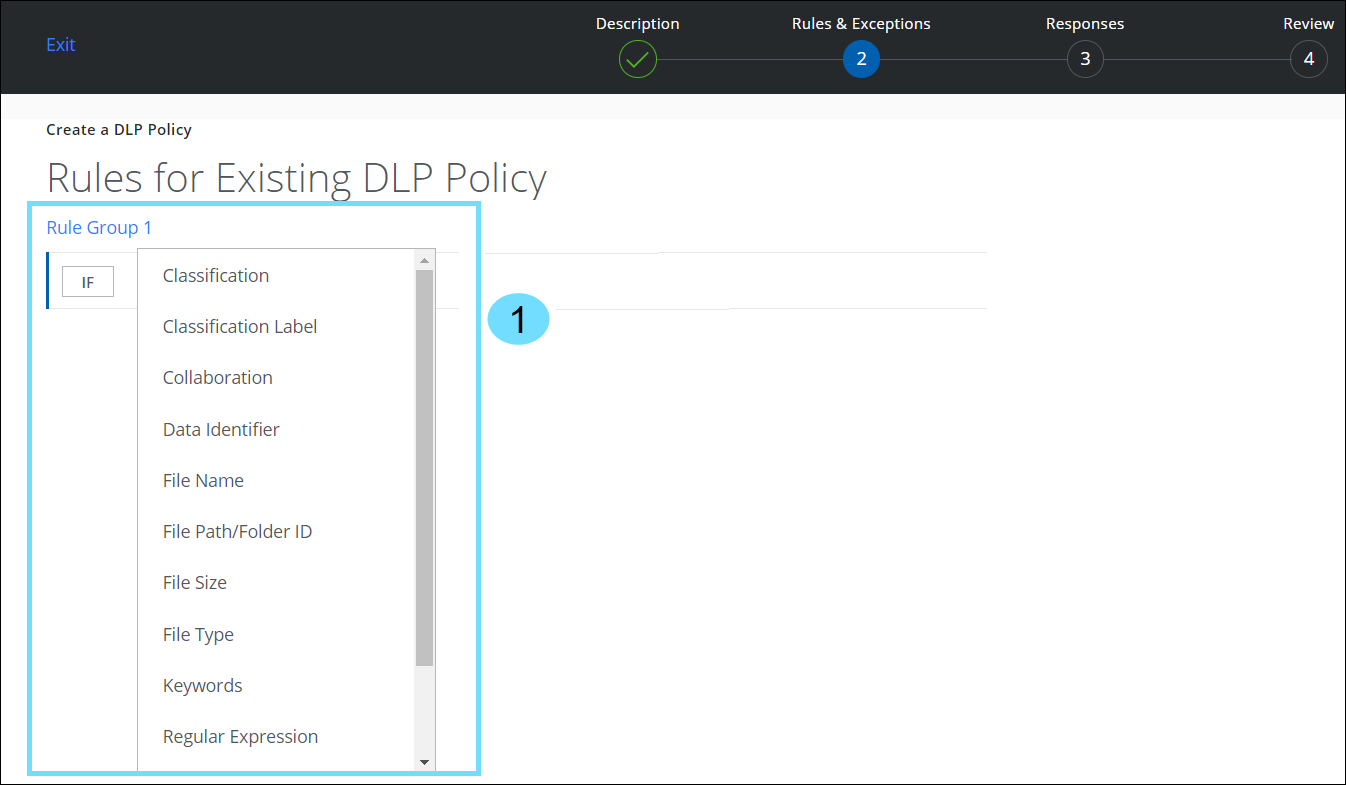
Navigation path: Policy > DLP Policies > DLP Policies > Create/Edit New Policy> Rules & Exceptions wizard The Rules & Exceptions page displays different Rule interfaces for each Classification Type: SSC and SSE/Trellix.
|
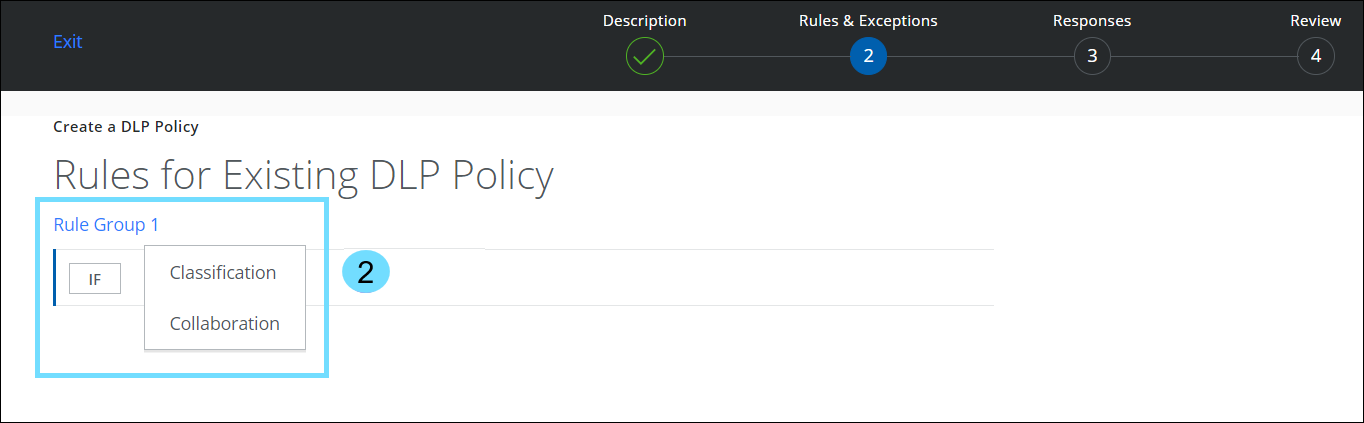
Navigation path: Policy > DLP Policies > DLP Policies > Create/Edit New Policy> Rules & Exceptions wizard The Rules & Exceptions page displays a unified rule interface for the Classification Types: SSC or SSE/Trellix. To define rules for your DLP policy, see Create a Sanctioned DLP Policy.
|
|
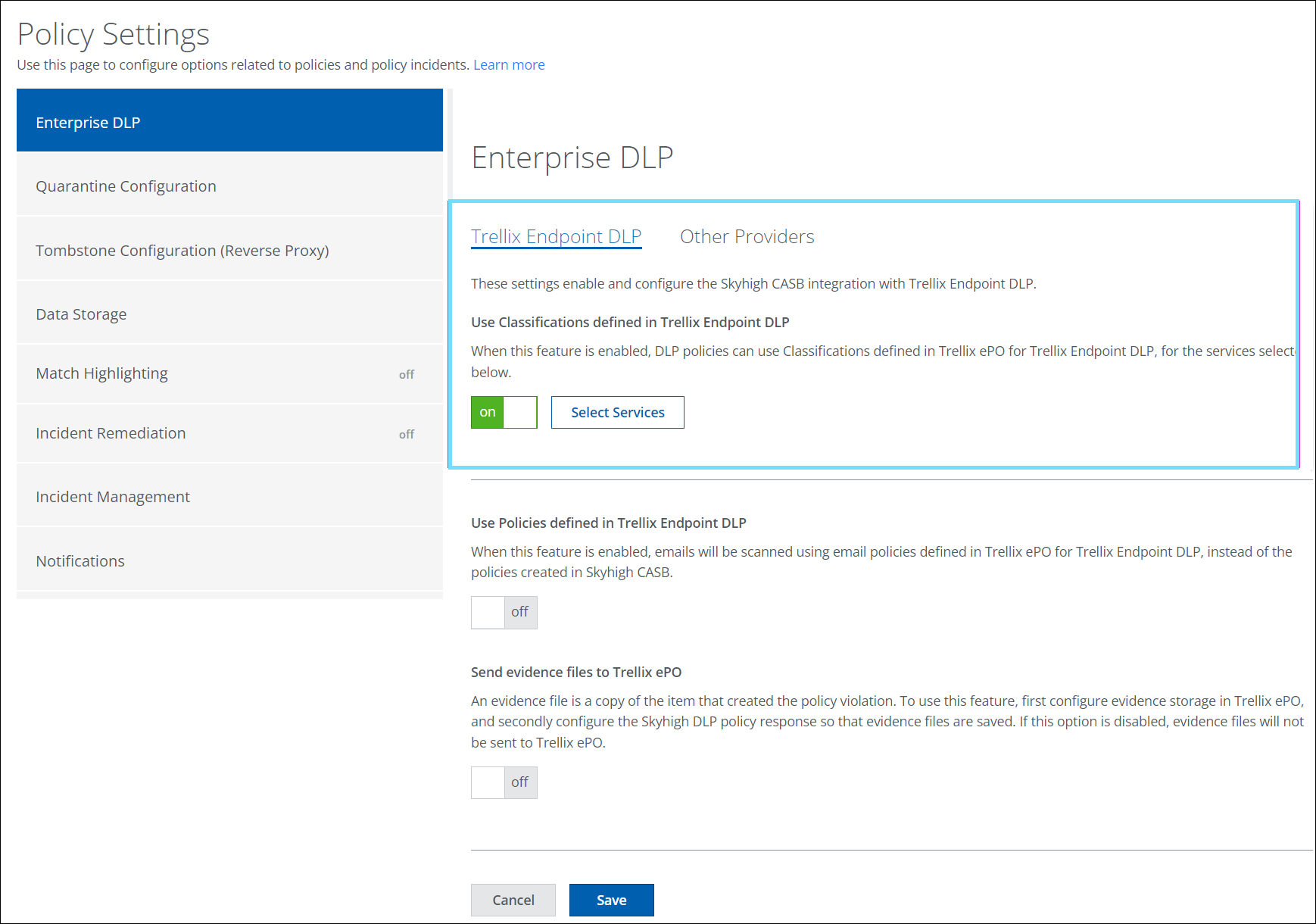
Navigation path: Policy > Policy Settings > Enterprise DLP The Enterprise DLP page allows you to select Services for SSC or SSE/Trellix Classifications. |
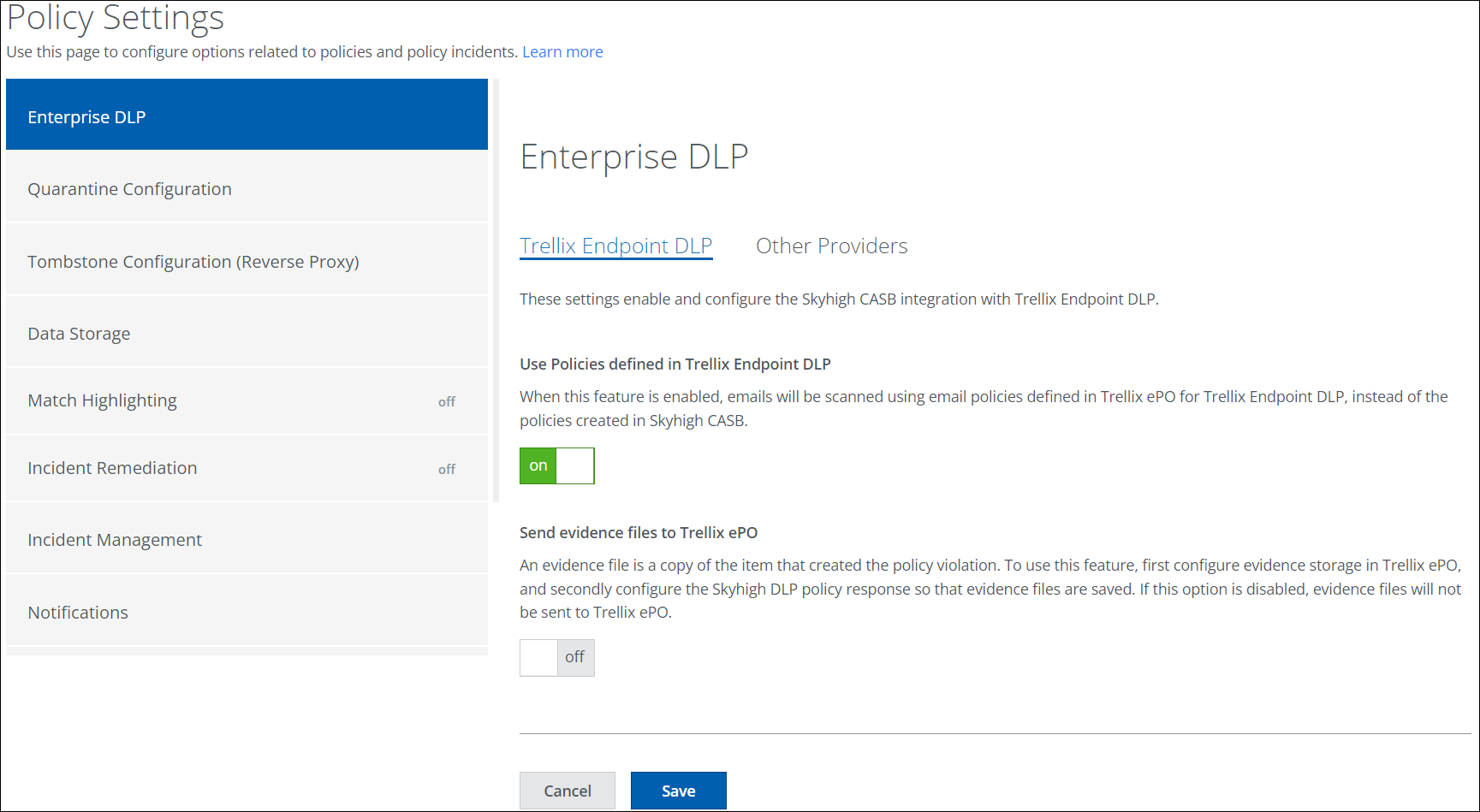
Navigation path: Policy > Policy Settings > Enterprise DLP The option to select Services for Classifications has been removed from the Enterprise DLP page. To configure Endpoint DLP, see Configure Enterprise DLP.
|
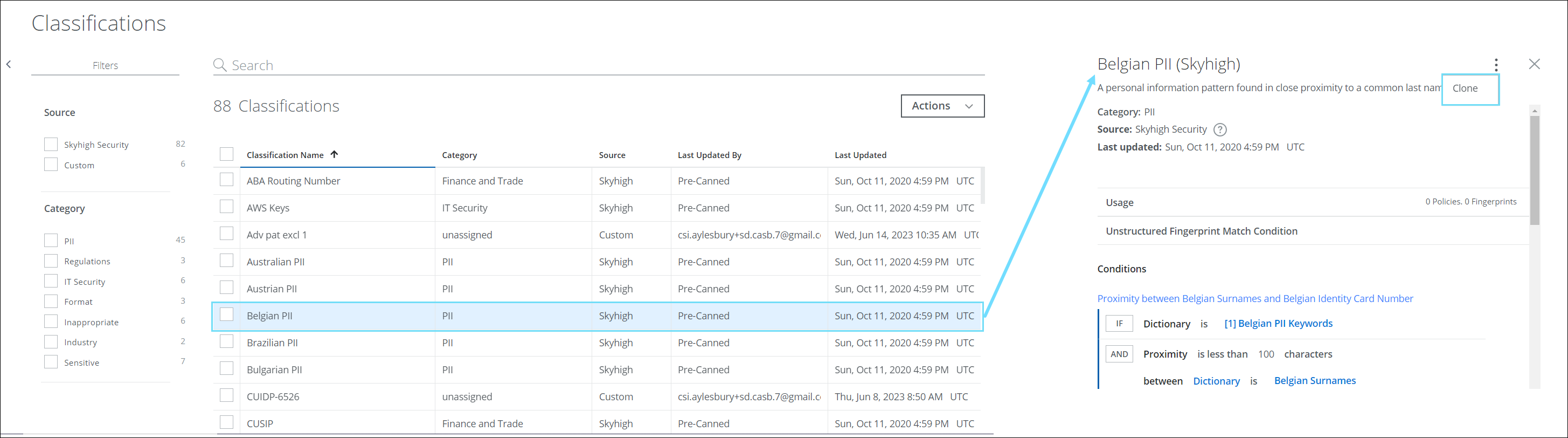
Clone Pre-Canned Classifications 
You can now clone the pre-canned classifications on the Classifications page (found under Policy > DLP Policies > Classifications). This allows you to modify the pre-canned classification policies to suit your specific needs, which will build more complex classifications with richer rules to protect data and reduce the occurrence of false positives. This feature also enables you to transition from legacy data identifiers by cloning pre-canned classifications. For details, see Clone Pre-Canned Classification.
AI Regular Expression Generator for Custom Advanced Patterns 
- The Advanced Patterns Classification method (found under Policy > DLP Policies > Classifications > Create Classification > Conditions > Advanced Patterns > New) now includes an AI-based RegEx Generator available for Custom Advanced Patterns.
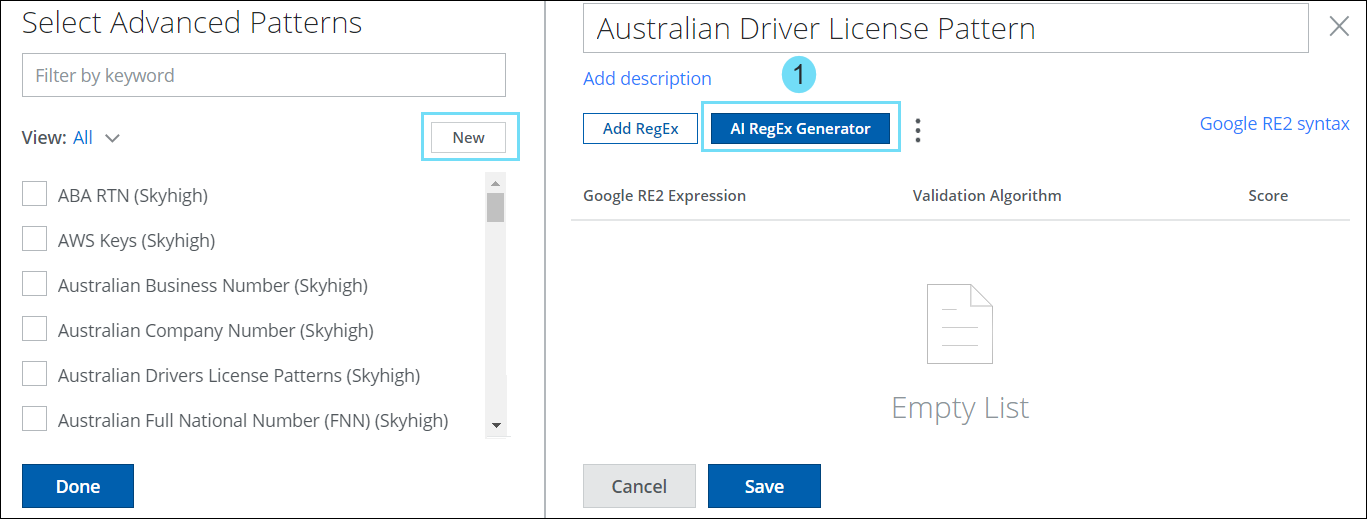
- It generates expressions for scenarios where Skyhigh’s predefined classifications are absent.
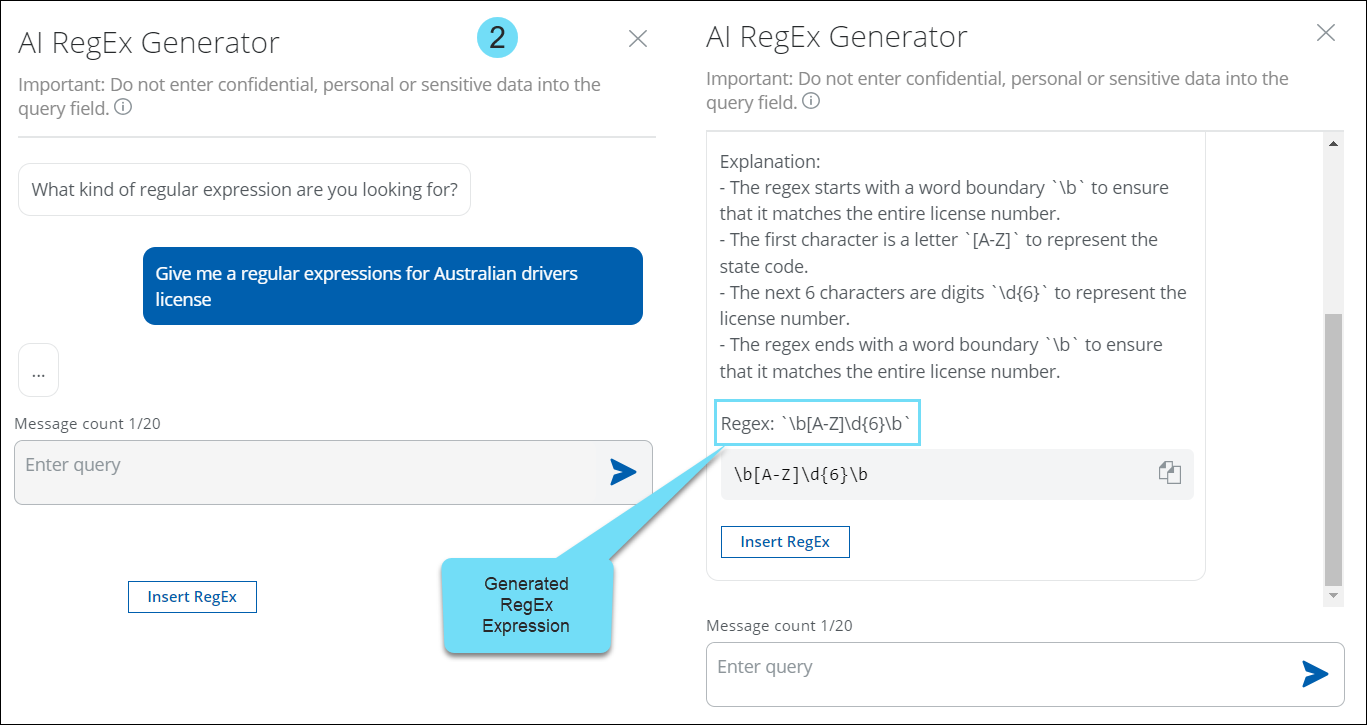
- The AI-based regular expression generator simplifies the task of building complex expressions by providing the following benefits. For details, see AI RegEx Generator for Custom Advanced Patterns.
| AI Regex Generator Benefits |
|---|
| AI-Powered Expression Building. Harness the power of AI to create intricate expressions effortlessly |
| Conversational Approach. Seamlessly construct and comprehend complex expressions through a conversation-based interface |
| Rapid Expression Generation. Quickly produces expressions for scenarios where Skyhigh's predefined classifications are absent |
| Tailored Regular Expression Assistance. Specialized in addressing queries solely related to regular expression |
| Precise RE2 Format Suggestions. Provide customers with accurate expression recommendations, exclusively in the Google RE2 format |
| Risk Reduction. Minimize the risk of inaccurate expressions, preventing false positives/negatives |
| Mitigate App Blockages. Overcome organizational app restrictions, boosting the data administrators' productivity |
Skyhigh SSE Products
Skyhigh CASB
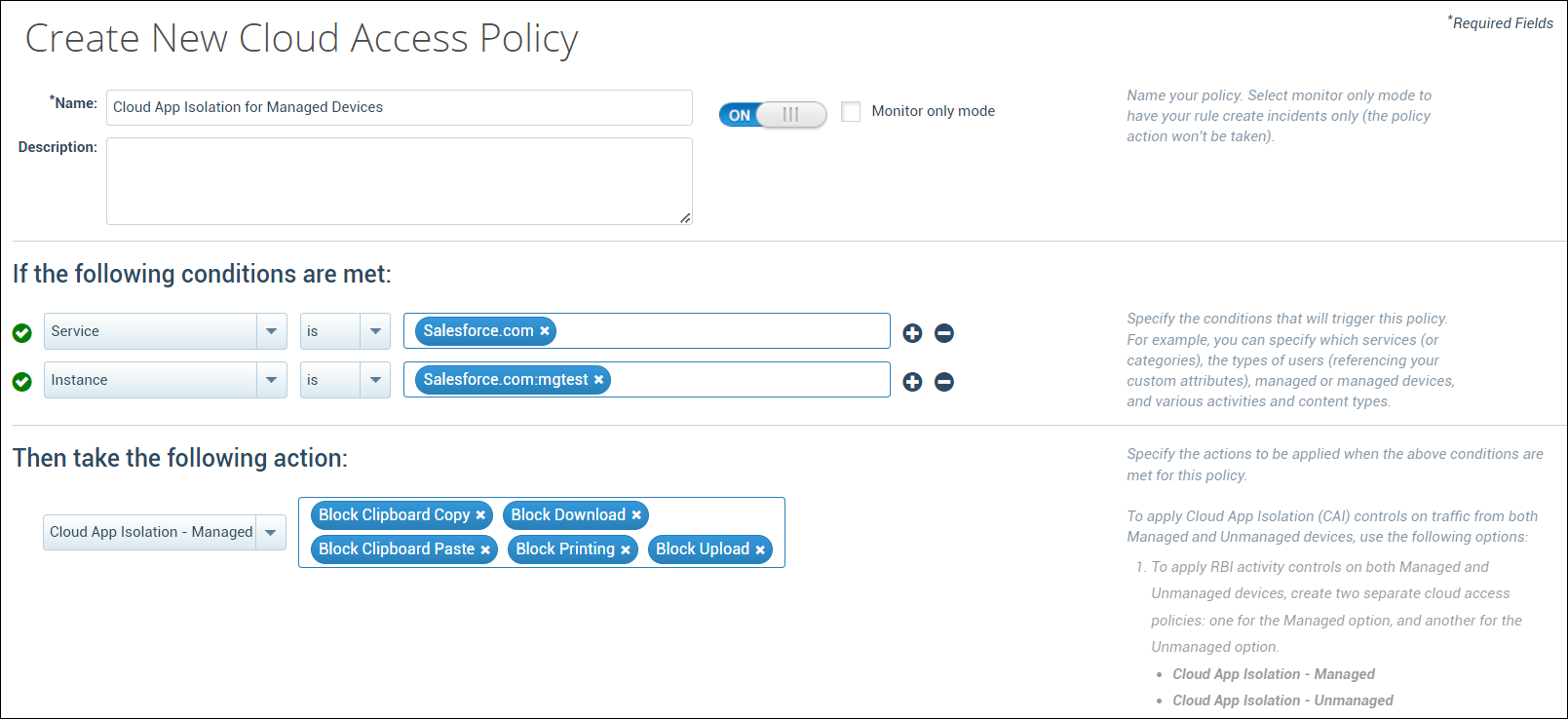
Cloud App Isolation (formerly RP-RBI) for Managed Devices 
Skyhigh CASB now supports Cloud App Isolation (CAI) for managed devices, which allows frictionless onboarding of longtail SaaS applications and prevents data exfiltration by implementing a Cloud Access Policy (CAP) for traffic originating from managed devices. CAP policies then allow or block activities on managed devices, such as uploads, downloads, clipboard copy, clipboard paste, and printing. For details, see Cloud Activity Controls with CAI. You can further define a web DLP policy to restrict the transfer (upload/download) of sensitive data to and from cloud services on managed devices. For details, see Create Web DLP Policy for CAI. CAI for managed devices requires an additional license, which is a standalone SKU named Cloud App Isolation SKU (RP-RBI Managed).
Skyhigh CNAPP
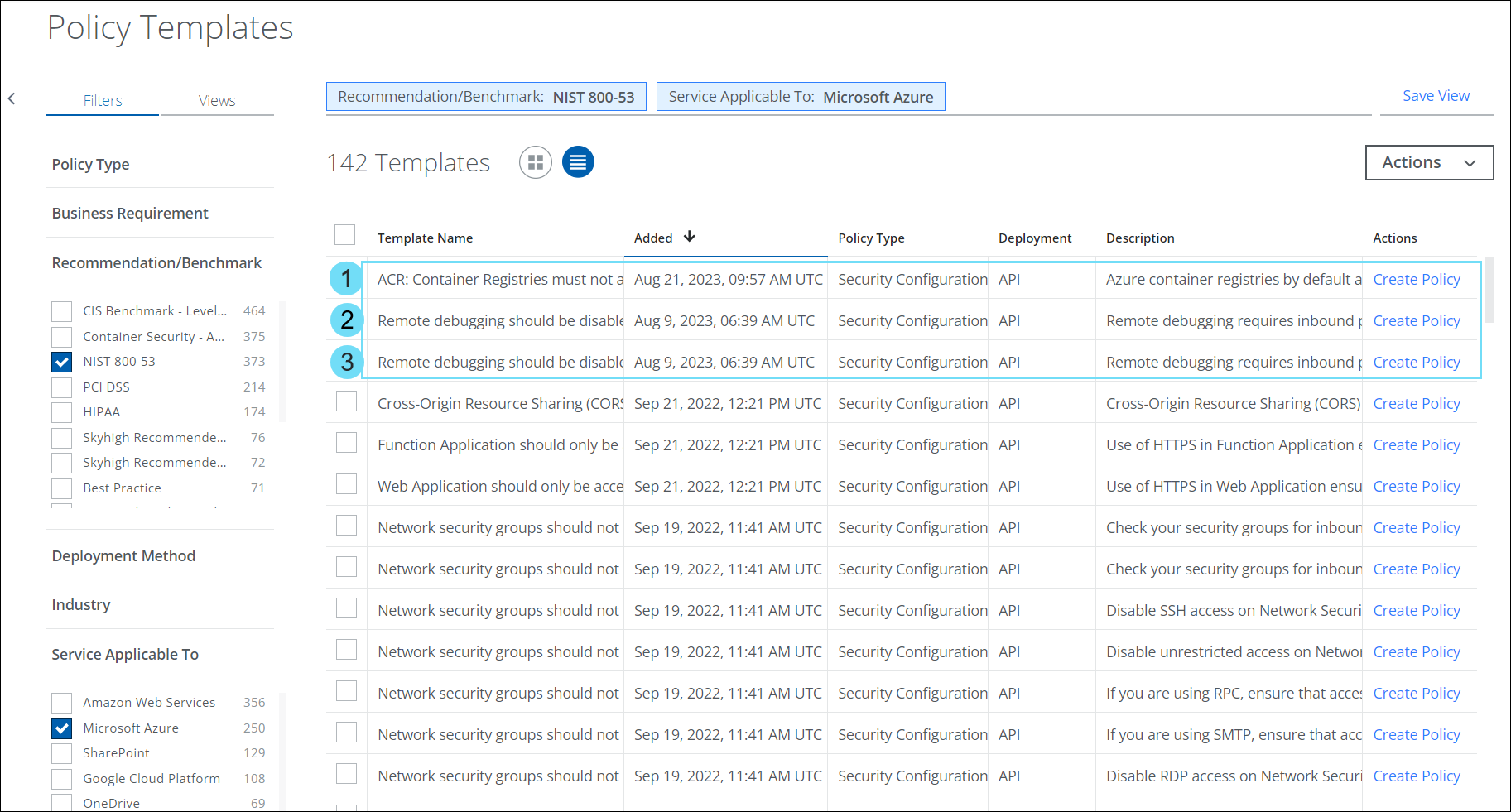
Updated Azure NIST 800-53 Templates 
The NIST 800-53 is a cybersecurity standard and compliance framework developed by the National Institute of Standards in Technology. NIST 800-53 provides a foundation of guiding elements, strategies, systems, and controls, which can agnostically support an organization's cybersecurity needs and priorities. In this release, 3 existing Azure NIST 800-53 Templates are renamed as below:
- ACR: Container Registries must not allow unrestricted network access
- Remote debugging should be disabled for Web Applications
- Remote debugging should be disabled for Function Application
These updated Policy Templates can be found under Policy > Policy Templates. For details, see Policy Templates for Azure and Policy Templates for ACR.
Skyhigh Secure Web Gateway
Configuring an IPsec Tunnel to Protect Any Subnet in Your Network 
An option named Any subnet has been added for use in protecting subnets when configuring locations as part of the setup procedure for Secure Web Gateway. If you enable it, an IPsec tunnel can be built between any subnet (0.0.0.0/0) in your network and the cloud service.
To work with this option, click the settings icon on the user interface for Secure Web Gateway, then navigate to Infrastructure > Web Gateway Setup. On the setup main page, scroll down to Configure Locations and click New Location.
On the page that appears, select IPsec Mapping, then scroll down again until you see the new option.
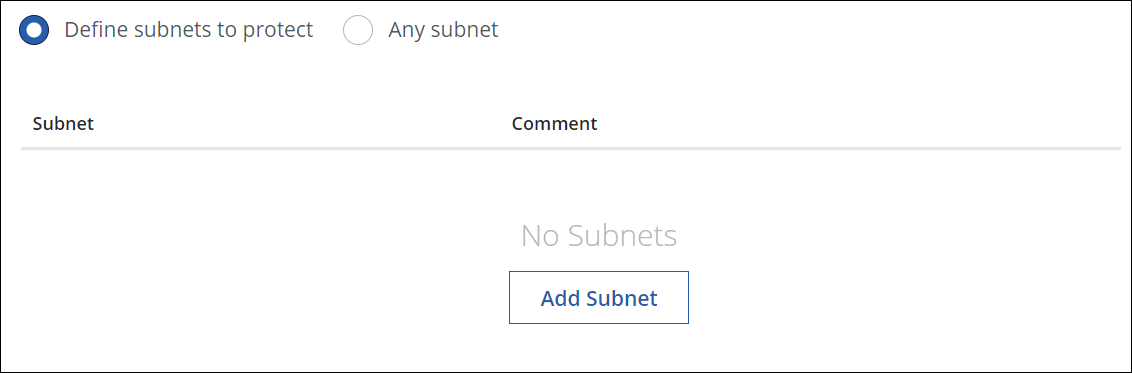
For more information about how to use the Any subnet feature when configuring IPsec mapping, see Configure an IPsec Tunnel on Secure Web Gateway.
New Item in List of Criteria for Creating Rules 
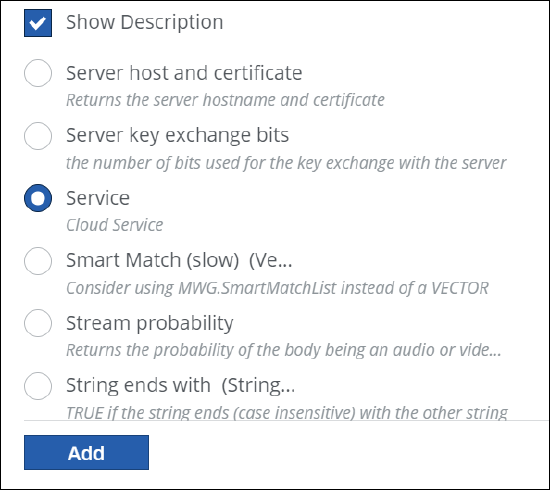
An item named Service has been added to the list of criteria where you select criteria for web policy rules that you create on your own with the Rule Builder. It allows you, for example, to let a rule apply if a particular cloud service is found to be included in a list of cloud services.
To work with the new item, navigate to Policy > Web Policy > Policy on the user interface for Secure Web Gateway. On the Web Policy page, select a rule set, then click the three dots next to a rule, and under Add Custom Rule in the menu that appears, select Via Rule Builder.
When you build the rule and click Select Criteria to configure the rule criteria, the list that appears offers you a new item.
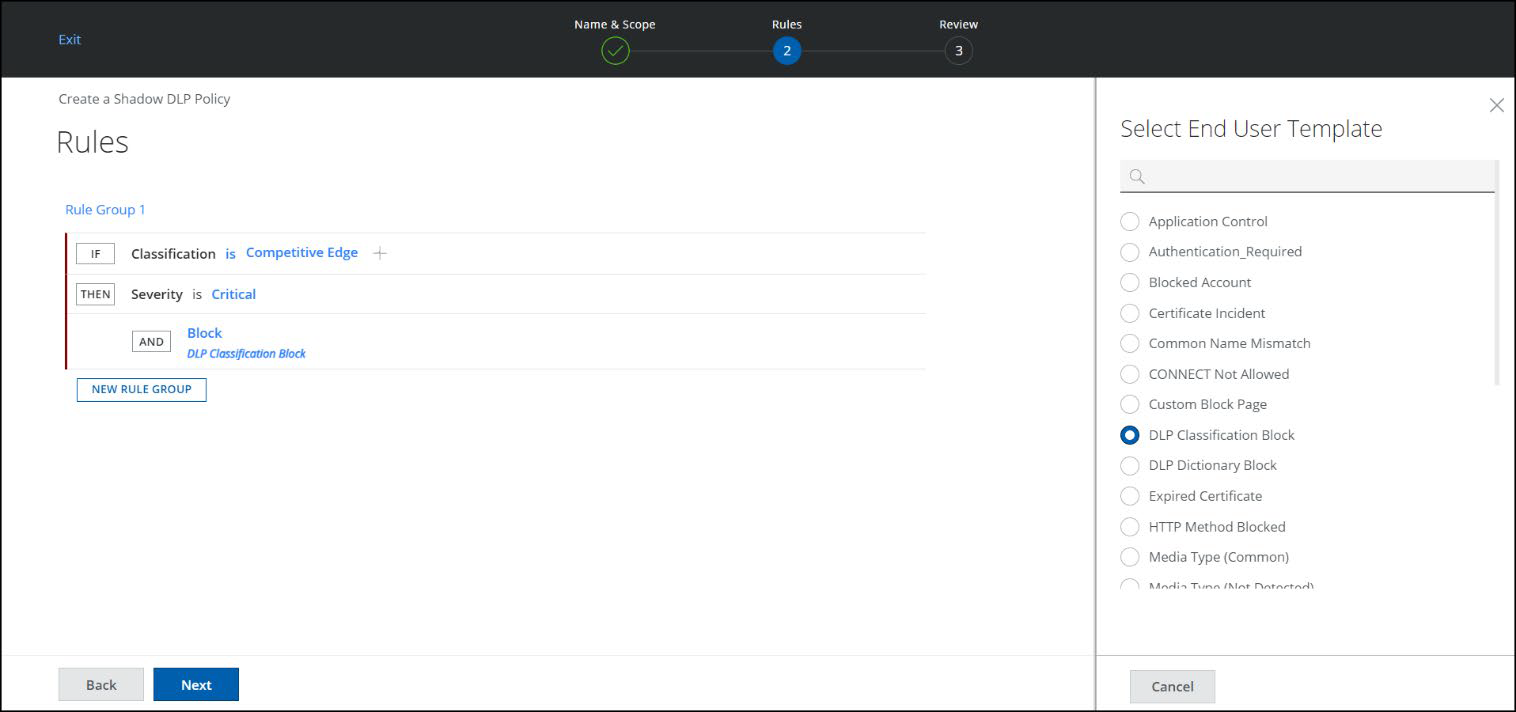
Apply End User Notification Template to a DLP Policy 
You can apply the Custom End User Notification Template for the Block option on the DLP Policy page. For more details, see Apply End User Notification Template to a DLP Policy
Skyhigh Private Access
Deploy Secure App Connector V2 
Using OVA Package
The Skyhigh connector group includes one or more Secure App Connectors, which enables end users to securely connect to their organization's private application via Skyhigh SSE.
The OVA packages are available for the following environments:
- Secure app connector V2 OVA on VMWare VSphere Hypervisor (ESXi)
- Secure app connector V2 OVA on VMWare vCenter
Skyhigh Security provides a new UI workflow to create a connector configuration file required in the connector v2 deployment. Download the OVA package and use the connector configuration file to complete the connector deployment process. For deployment methods, see Deploy Secure App Connector V2 VM. For details on creating a connector configuration file, see Configure Secure App Connector V2
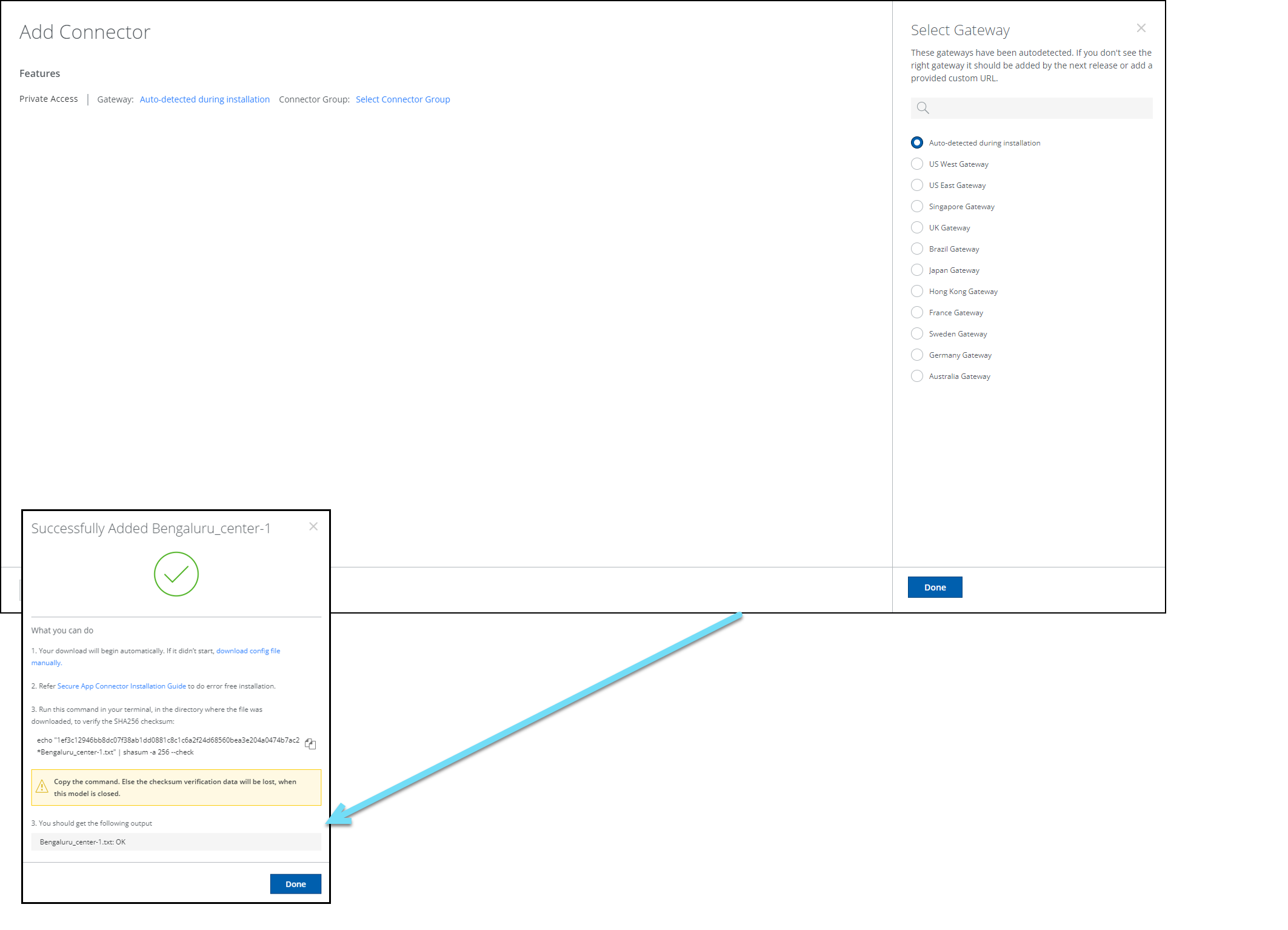
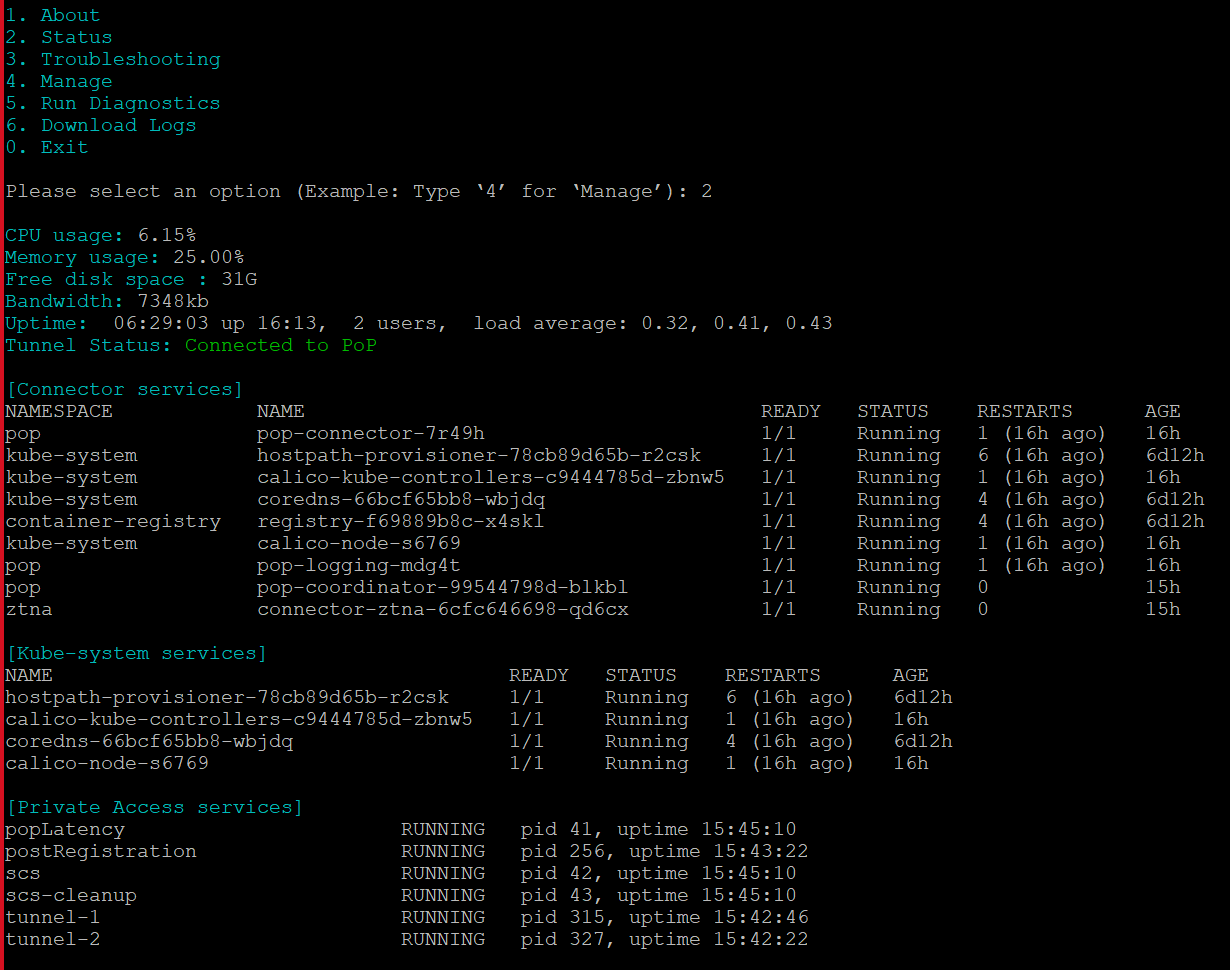
CLI Commands
Connector V2 CLI commands enable you to manage, check the status, run diagnostics, and troubleshoot your secure app connectors.
- Log on to the connector host using SSH (Secure Shell) and execute the required commands to troubleshoot a connector.
- If you are a root user or a non-root user, execute the
pa_connectorscript from anywhere on the host.
For details, see Connector V2 CLI
Skyhigh Cloud Firewall
Device Profile-based Cloud Firewall Policy 
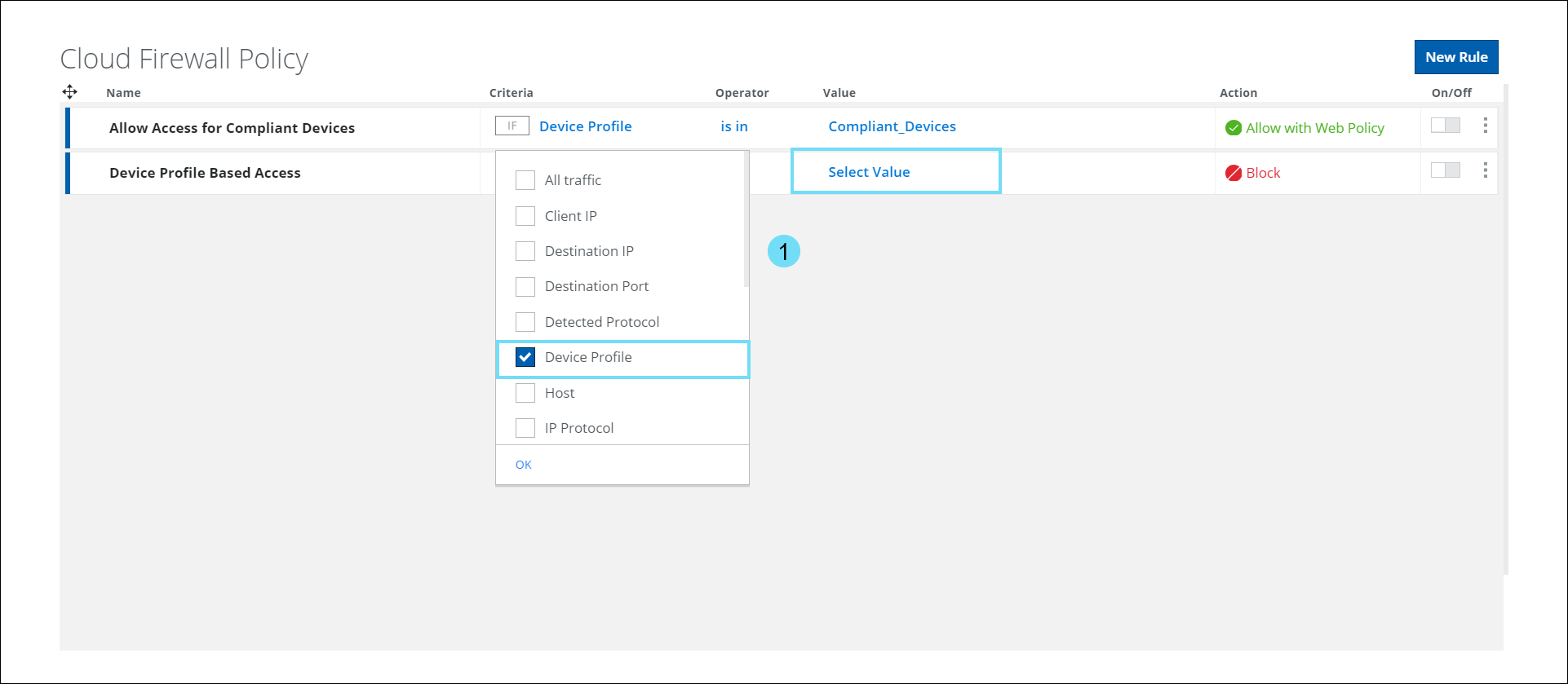
The option to choose Device Profile as a criteria (found under Policy > Cloud Firewall > Policy > New Rule) is now available in the Cloud Firewall Policy page. The Select Device Profile panel on the Cloud Firewall Policy page provides a list of configured device profiles. You can use this criteria to restrict IP traffic from non-compliant devices and allow traffic only from compliant devices. For example, you can now choose to allow traffic only originating from devices that are running operating systems higher than Windows 10. For details, see Configure Cloud Firewall Policy.
NOTE: Whenever you modify the device profile, make sure to update the SCP policy to apply the changes.
- Select Device Profile as the criteria and click Select Value to view the Select Device Profile side panel.
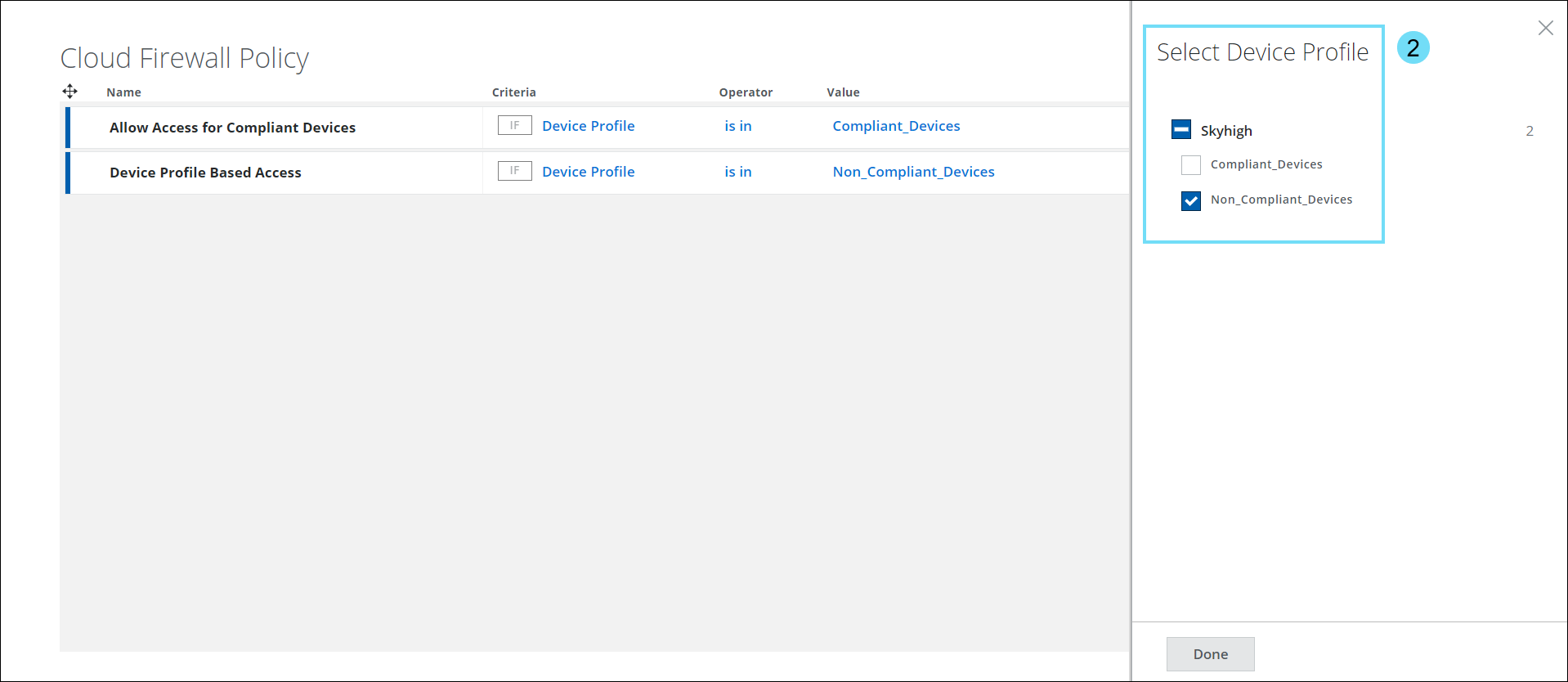
- The Select Device Profile panel displays a list of configured device profiles. Use the checkbox to select the required Device Profile in the Cloud Firewall Policy.
Resolved and Known Issues
 Click here to view Resolved and Known Issues
Click here to view Resolved and Known Issues- For details, see Skyhigh Security Cloud Bug Fixes and Known Issues.