Secure App Connector V2 CLI
Connector V2 CLI enables admins to know the status, manage, run diagnostics, and troubleshoot their secure app connectors by connecting to the host using SSH (secure shell)
- Log on to the connector host using SSH (Secure Shell) and execute the required commands to troubleshoot a connector.
- If you are a root user or a non-root user, execute
pa_connectorthe script from anywhere on the host.
About Secure App Connector
Select the About option to know the Secure App Connector version.
Enter 0 to exit from the command console.
.png?revision=1)
Secure App Connector V2 CLI for TCP Applications
Verification of Secure App Connector V2 for TCP Applications
Provides the list of commands you can execute:
- Run the Status option to verify the status of the connector deployment.
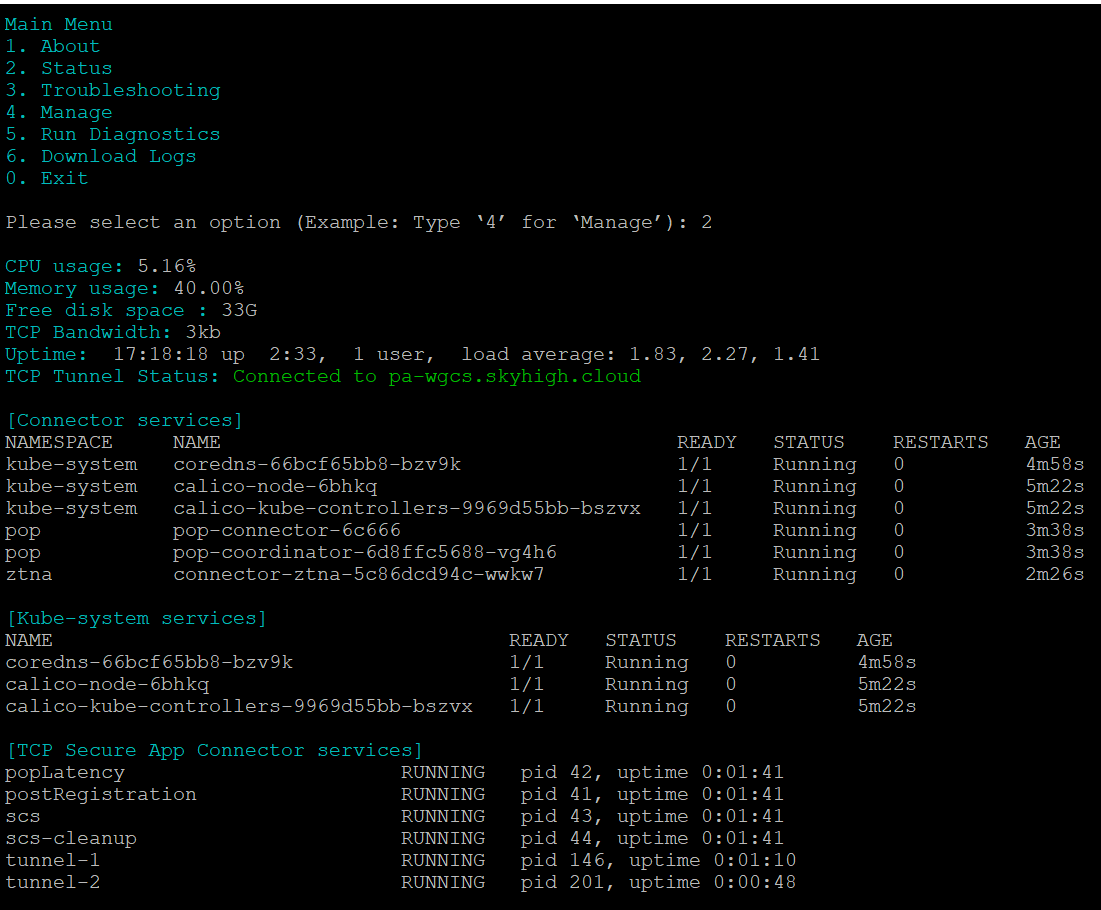
Check tunnel status:
- The connector shows the status as Normal when the TCP tunnels are up.
- The connector shows the status as Critical when TCP tunnels are down.
- Run the Diagnostics tests option to verify the connector setup.
The following tests were executed as listed below. A check mark (✓) indicates a successful result, while a cross (✗) indicates that the endpoint is not reachable.
Status Test Description 
PA TCP Gateway https://de.pa-wgcs.skyhigh.cloud:443 is reachable. 
ZTNA TCP pod is up and running. 
ZTNA UDP pod is up and running. 
PA TCP Gateway https://de.pa-wgcs.skyhigh.cloud:443 is reachable from ztna pod 
PA Registration endpoint https://api.wgcs.skyhigh.cloud/pa/v1/connector-registration is reachable from ztna pod. 
PA List endpoint https://api.wgcs.skyhigh.cloud/pa/v1/private-applications is reachable from ztna pod 
IP Forwarding is enabled 
Squashfs fileystem is enabled 
Host DNS is configured with 10.213.154.101 
ZTNA pod is configured with DNS: 10.213.154.101 
Number of CPUs are 8. VM CPU configuration is proper 
Harddisk configuration is 76G. VM harddisk configuration is proper 
Memory configuration is 11938MB. VM Memory configuration is proper 
Microk8s service is running. 
Microk8s node is in Ready state 
Microk8s dns plugin is enabled 
NTP service is enabled and synchronized. 
Public ECR is reachable 200 
Registration url https://iam.skyhigh.cloud/iam/v1.2/registration is reachable 
IAM Base Url https://iam.skyhigh.cloud/iam/v1.1 is reachable 
IAM Base Url https://iam.skyhigh.cloud/iam/v1.1 is reachable from ztna pod 
MVC Base Url https://dashboard-eu.ui.skyhigh.cloud/ is reachable 
TLS tunnel is up. 
Wireguard is connected. 
Docker is running. 
No error logs in healthUpdate. 
No openvpn error logs.
Troubleshooting Secure App Connector V2 for TCP Applications
Provides the list of commands you can execute:
- Run the Troubleshooting option to help you troubleshoot the Secure App Connector-related issues.
.png?revision=1)
- Select Download Logs to download all logs and configuration details to a temp (/tmp/) folder on the host once diagnostics tests are completed.
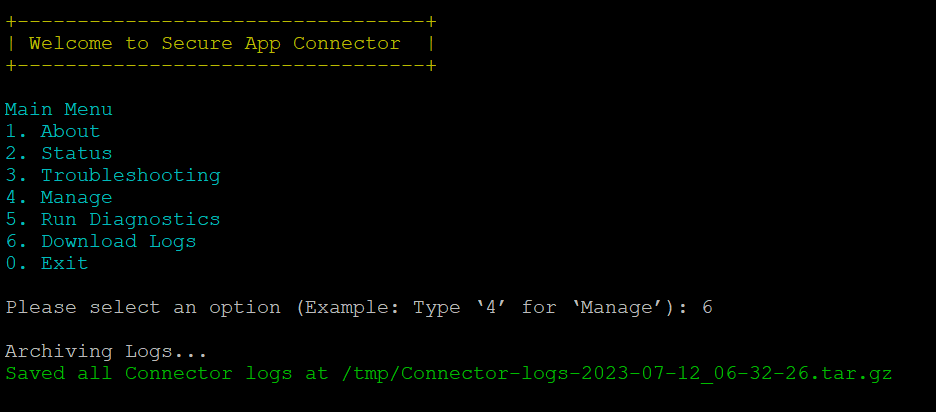
Download Logs
You can download all logs and configuration details to /tmp/Connector-logs-2023-07-12_06-32-26.tar.gz
- Log on to the connector host using SSH.
- Execute pa_connector > enter 6.
Downloads/tmp/Connector-logs-2023-07-12_06-32-26.tar.gzfile to the temp (/tmp/) folder once the command is executed completely. -
You can upload the latest file
/tmp/Connector-logs-2023-07-12_06-32-26.tar.gzto the support portal for review.
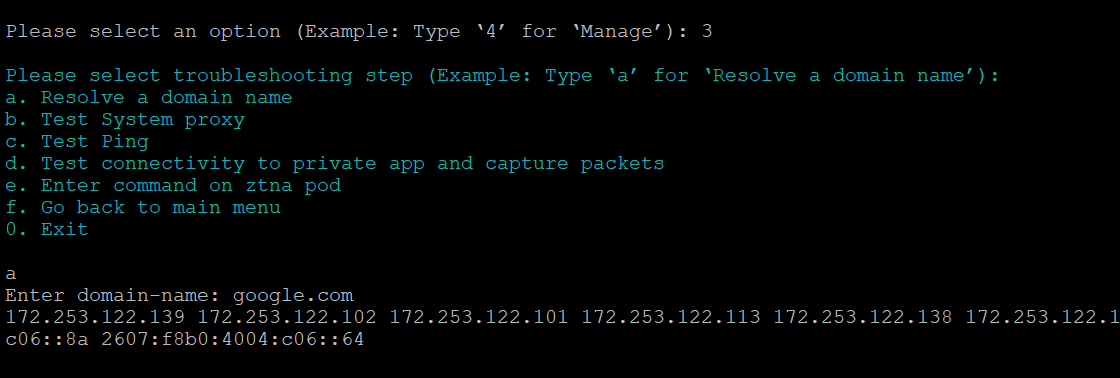
Resolving Host Names
For a Connector to function, the system Domain Name Service (DNS) should be able to resolve both Skyhigh Security URLs and Private Application URLs. You can do the following to resolve host names using the system DNS:
Perform the following to check if the system DNS is resolving both Skyhigh Security and Private Application URLs:
-
Log on to the connector host using SSH (Secure Shell).
-
Execute pa_connector > enter 3 > enter a > enter the domain name.
Test the system proxy
Perform the following to test if a private application connection is established with the connector via the system proxy:
-
Log on to the connector host using SSH.
-
Execute pa_connector > enter 3 > enter b > enter the system proxy address.
Displays if the private application connection is established with the connector via system proxy.
.png?revision=1)
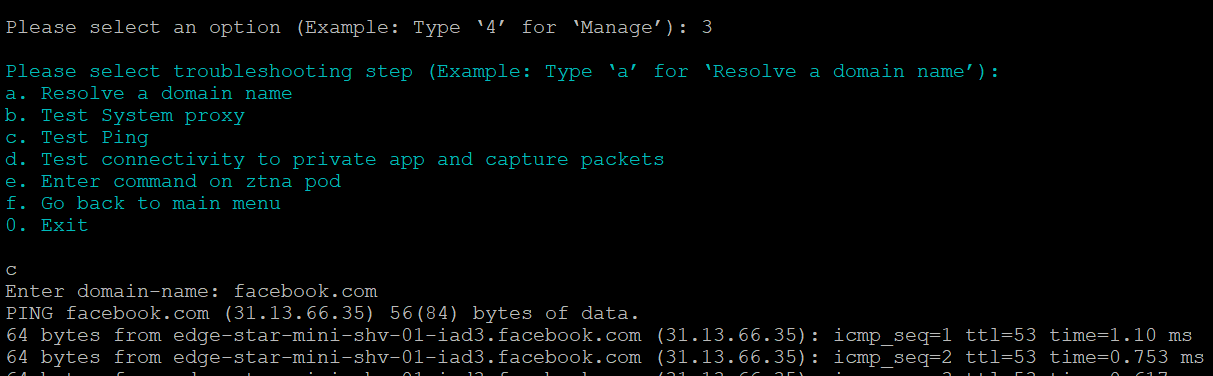
Test Ping
Perform the following to test ping:
-
Log on to the connector host using SSH.
-
Execute pa_connector> enter 3 > enter c.
.png?revision=1)
Test Connectivity to Private App and Capture Packets
Perform the following to check the private application connectivity:
-
Log on to the connector host using SSH.
-
Execute pa_connector > enter 3 > enter d.
Downloads.pcapfile to the temp (/tmp/) folder once the command is executed completely. -
You can upload the latest file
pa_capture-currentdate.pcapto the support portal for review.
.png?revision=1)
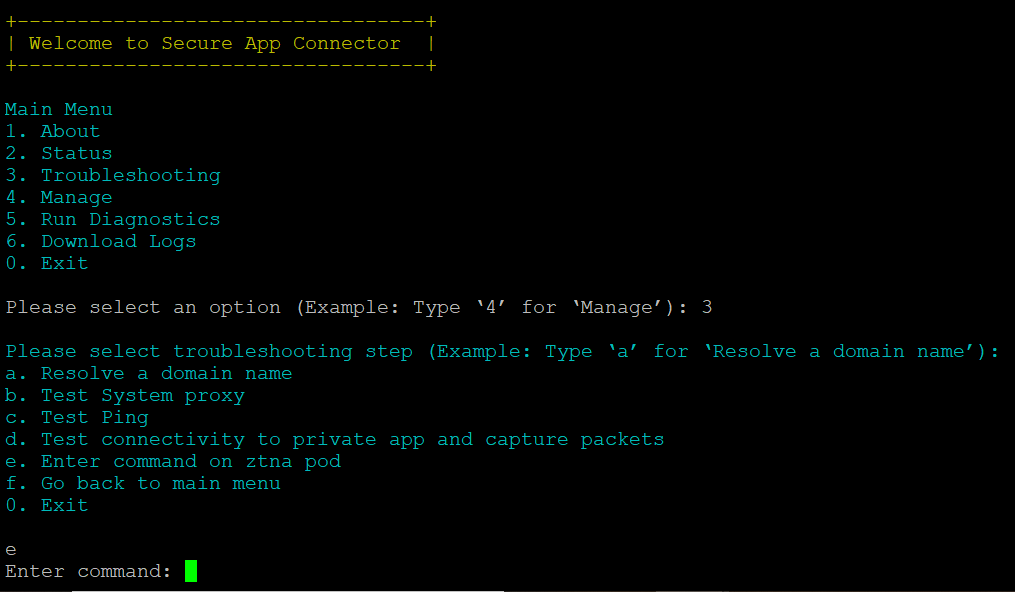
Enter command on ztna pod
Perform the following to execute command on ztna pod:
1. Log on to the connector host using SSH.
2. Execute pa_connector > enter 3 > enter e.
Manage Secure App Connector V2 for TCP Applications
Perform the following to manage connectors:
-
Log on to the connector host using SSH.
-
Execute pa_connector > enter 4 > enter <g or h or i or j>.
.png?revision=1&size=bestfit&width=733&height=394)
Stop health update
-
Log on to the connector host using SSH.
-
Execute pa_connector > enter 4 > enter g.
Note: Stopping health updates will stop any PA app traffic coming to this connector. Effectively, the connector will be offline/standby.
Start health update
Perform the following to start all connector services:
-
Log on to the connector host using SSH.
-
Execute pa_connector > enter 4 > enter h.
Note: This action will bring the connector back online, and traffic will restart being directed to this connector
Restart connector services
Perform the following to restart all services that run in a connector:
-
Log on to the connector host using SSH.
-
Execute pa_connector > enter 4 > enter i.
Update host DNS
Perform the following to update host DNS:
-
Log on to the connector host using SSH.
-
Execute pa_connector > enter 4 > enter j.
Update NTP server
Perform the following to update the NTP (Network Time Protocol) server:
-
Log on to the connector host using SSH.
-
Execute pa_connector > enter 4 > enter k.
.png?revision=1&size=bestfit&width=626&height=493)
Revert connector to local available version
If connector pods enter an invalid state, select the Revert connector to local available version CLI option to revert them to the locally available version.
-
Log on to the connector host using SSH.
-
Execute pa_connector > enter 4 > enter l.
.png?revision=1&size=bestfit&width=601&height=471)
Verify NTP service is enabled and synchronized
Perform the following to verify if the NTP service is enabled and synchronized:
-
Log on to the connector host using SSH.
-
Execute pa_connector > enter 5.
.png?revision=1&size=bestfit&width=644&height=446)
Power OFF Connector VM
- Run the sudo command
microk8s stop. - Switch OFF VM.
Power ON Connector VM
- Switch ON VM.
- Run the sudo command
microk8s start.
Secure App Connector V2 CLI for UDP Applications
Verification of Secure App Connector V2 for UDP Application
Provides the list of commands you can execute:
- Run the Status option to verify the status of the connector deployment.

Check tunnel status:
- The connector shows the status as Normal when the TCP and UDP tunnel is up.
- The connector shows the status as Critical when the TCP and UDP tunnel is down.
- Run the Diagnostics tests option to verify the connector setup.
The following tests were executed as listed below. A check mark (✓) indicates a successful result, while a cross (✗) indicates that the endpoint is not reachable.
Status Test Description 
PA TCP Gateway https://de.pa-wgcs.skyhigh.cloud:443 is reachable. 
ZTNA TCP pod is up and running. 
ZTNA UDP pod is up and running. 
PA TCP Gateway https://de.pa-wgcs.skyhigh.cloud:443 is reachable from ztna pod. 
PA Registration endpoint https://api.wgcs.skyhigh.cloud/pa/v1/connector-registration is reachable from ztna pod. 
PA List endpoint https://api.wgcs.skyhigh.cloud/pa/v1/private-applications is reachable from ztna pod 
IP Forwarding is enabled 
Squashfs fileystem is enabled 
Host DNS is configured with 10.213.154.101 
ZTNA pod is configured with DNS: 10.213.154.101 
Number of CPUs are 8. VM CPU configuration is proper 
Harddisk configuration is 76G. VM harddisk configuration is proper 
Memory configuration is 11938MB. VM Memory configuration is proper 
Microk8s service is running. 
Microk8s node is in Ready state 
Microk8s dns plugin is enabled 
NTP service is enabled and synchronized. 
Public ECR is reachable 200 
Registration url https://iam.skyhigh.cloud/iam/v1.2/registration is reachable 
IAM Base Url https://iam.skyhigh.cloud/iam/v1.1 is reachable 
IAM Base Url https://iam.skyhigh.cloud/iam/v1.1 is reachable from ztna pod 
MVC Base Url https://dashboard-eu.ui.skyhigh.cloud/ is reachable 
TLS tunnel is up. 
Wireguard is connected. 
Docker is running. 
No error logs in healthUpdate. 
No openvpn error logs.
Troubleshooting Secure App Connector V2 for UDP Applications
Provides the list of commands you can execute:
- Run the Troubleshooting option to help you troubleshoot the Secure App Connector-related issues.
- Select Download Logs to download all logs and configuration details to a temp (/tmp/) folder on the host once diagnostics tests are completed.
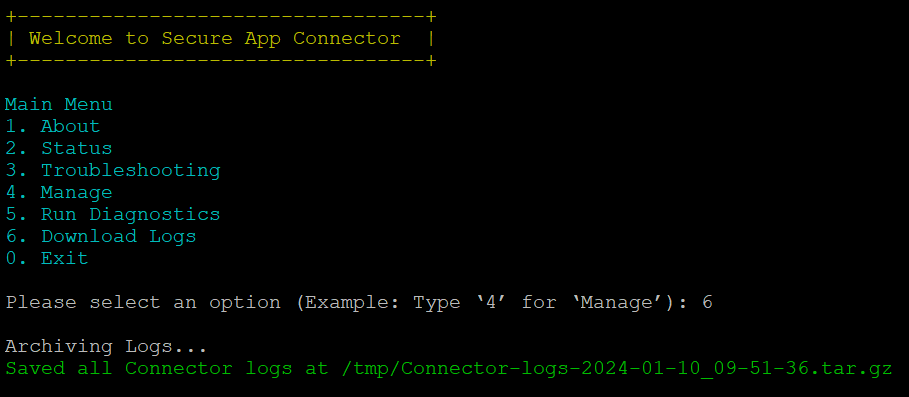
Download Logs
You can download all logs and configuration details to/tmp/Connector-logs-2024-01-10_09-51-36.tar.gz
- Log on to the connector host using SSH.
- Execute pa_connector > enter 6.
Downloads/tmp/Connector-logs-2024-01-10_09-51-36.tar.gzfile to the temp (/tmp/) folder once the command is executed completely. -
You can upload the latest file
/tmp/Connector-logs-2024-01-10_09-51-36.tar.gzto the support portal for review.
Resolving Host Names
For a Connector to function, the system Domain Name Service (DNS) should be able to resolve both Skyhigh Security URLs and Private Application URLs. You can do the following to resolve host names using the system DNS:
Perform the following to check if the system DNS is resolving both Skyhigh Security and Private Application URLs:
-
Log on to the connector host using SSH (Secure Shell).
-
Execute pa_connector > enter 3 > enter command a > enter the domain name.
.png?revision=1)
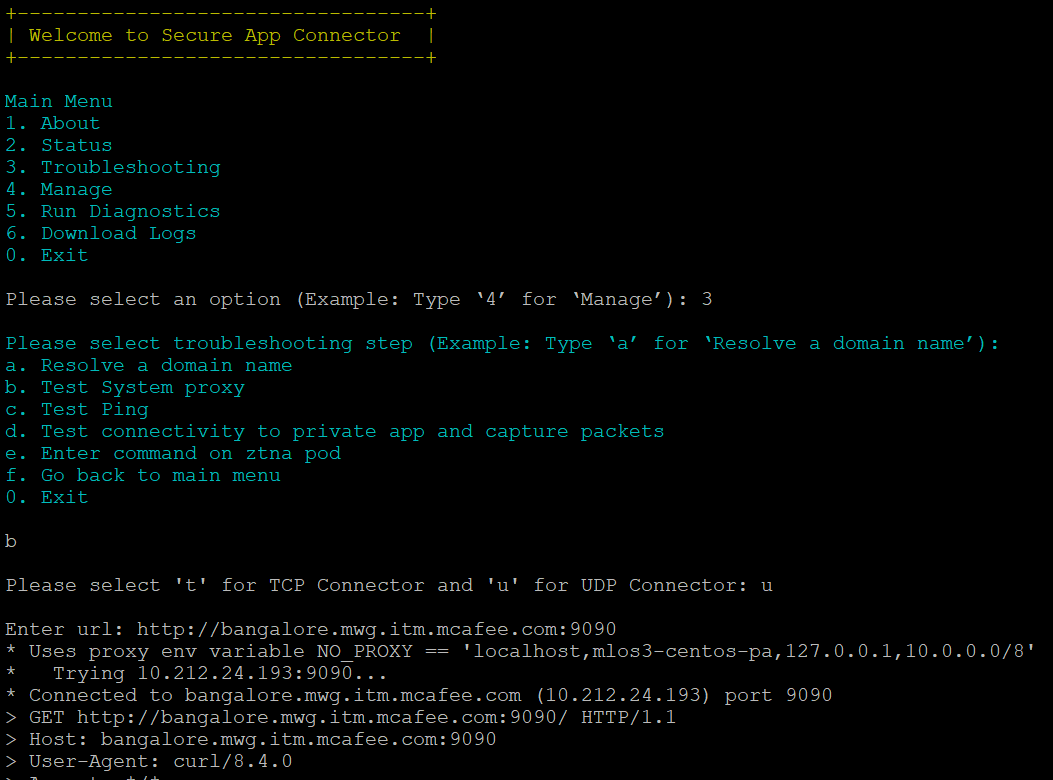
Test the system proxy
Perform the following to test if a private application connection is established with the connector via the system proxy:
-
Log on to the connector host using SSH.
-
Execute pa_connector > enter 3 > enter b > enter the system proxy address.
Displays if the private application connection is established with the connector via system proxy.
Test Ping
Perform the following to test ping:
-
Log on to the connector host using SSH.
-
Execute pa_connector > enter 3 > enter c.
.png?revision=1)
Test Connectivity to Private App and Capture Packets
Perform the following to check the private application connectivity:
-
Log on to the connector host using SSH.
-
Execute pa_connector > enter 3 > enter d.
Downloads.pcapfile to the temp (/tmp/) folder once the command is executed completely. -
You can upload the latest file
pa_capture-currentdate.pcapto the support portal for review.

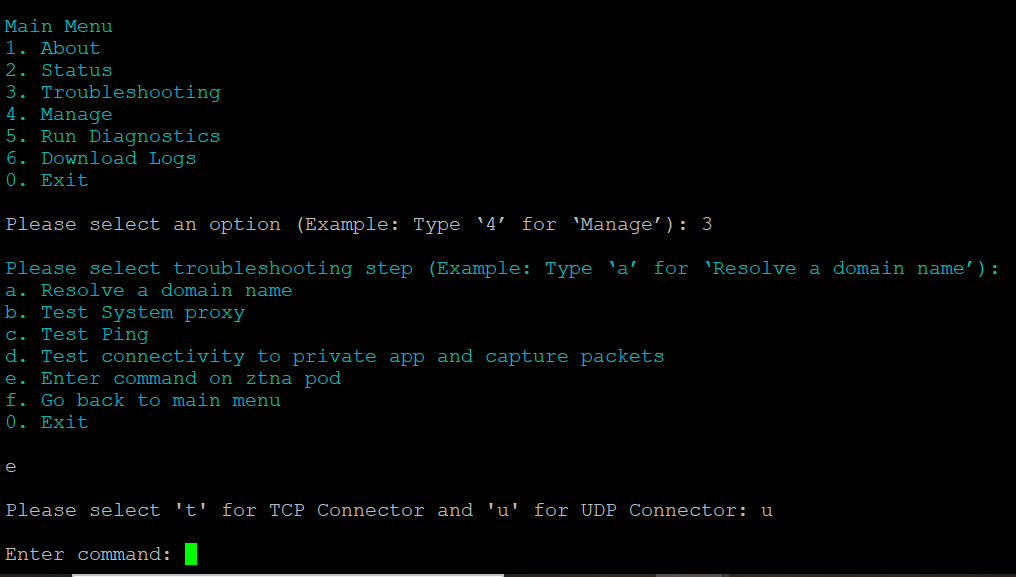
Enter command on ztna pod
Perform the following to execute command on ztna pod:
1. Log on to the connector host using SSH.
2. Execute pa_connector > enter 3 > enter e.
.png?revision=1)
Manage Secure App Connector V2 for UDP Application
Provides the list of commands you can execute:
- Run the Manage option to manage (start or stop) Secure App Connector.

Stop health update
-
Log on to the connector host using SSH.
-
Execute pa_connector > enter 4 > enter g.
Note: Stopping health updates will stop any PA app traffic coming to this connector. Effectively, the connector will be offline/standy.
Start health update
Perform the following to start all connector services:
-
Log on to the connector host using SSH.
-
Execute pa_connector > enter 4 > enter h.
Note: This action will bring the connector back online, and traffic will restart being directed to this connector
Restart connector services
Perform the following to restart all services that run in a connector:
-
Log on to the connector host using SSH.
-
Execute pa_connector > enter 4 > enter i.
Update host DNS
Perform the following to update host DNS:
-
Log on to the connector host using SSH.
-
Execute pa_connector > enter 4 > enter j.

Update NTP server
Perform the following to update the NTP (Network Time Protocol) server:
-
Log on to the connector host using SSH.
-
Execute pa_connector > enter 4 > enter k.
.png?revision=1&size=bestfit&width=479&height=377)
Revert connector to local available version
If connector pods enter an invalid state, select the Revert connector to local available version CLI option to revert them to the locally available version.
-
Log on to the connector host using SSH.
-
Execute pa_connector > enter 4 > enter l.
.png?revision=1&size=bestfit&width=477&height=374)
Verify NTP service is enabled and synchronized
Perform the following to verify if the NTP service is enabled and synchronized:
-
Log on to the connector host using SSH.
-
Execute pa_connector > enter 5.
.png?revision=1&size=bestfit&width=531&height=368)
Power OFF Connector VM
- Run the sudo command
microk8s stop. - Switch OFF VM
Power ON Connector VM
- Switch ON VM
- Run the sudo command
microk8s start.
Tips
Note: For any new /etc/hosts entries, the connector must be restarted.
-
Proxy to private applications: Check
/skyhigh/mount/logs/debug.logto ensure that an application is reachable and not blocked by the policy. Ensure that the DNS configured on the connector can access private applications and resolve their URLs.
Common Errors and Workaround
| Task | When | Error | Workaround |
|---|---|---|---|
| Private Application is not reachable |
Run the command on the connector pod:
If curl also fails, then ensure that the IP of the connector pod and host IP are not on the same subnet (10.254.254.x) |
||
| Accessing Private Application | Able to access Private Application using Firefox browser, but failed to access the same application on the Chrome browser | Google Chrome - Taking Too Long to Load |
Disable the Use secure DNS option on Google Chrome. The Use secure DNS option should be disabled to access private applications. Go to Chrome browser > Settings > Privacy and Security > Disable the Use Secure DNS option. |
| Dual stack VMs/Hosts | Connector installation in a dual stack VM/host | Pods don't come to running state | If the VM/host is enabled for both IPv4 and IPv6, ensure that it gets proper IP addresses for both the IPv4 and IPv6 interfaces. If IPv6 is disabled in the network, then the IPv6 interface on the host should also be disabled. |
