Configure Private Access Policy Rules
Configure the policy rules to enforce controlled access on the private applications. You can create private access policy rules by applying criteria, operator, value, and action. You can define up to five levels of nesting within a parent rule. You will see an error if you don't enter the rule name or when the rule name exceeds 200 characters. The nested rule can themselves contain other nested rules, resulting in a hierarchy of rules.
Skyhigh Private Access applies the access policy rules using the first-match principle and runs from top to down. The rule set evaluates to true or false based on the criteria, value, and action specified in each rule. So make sure to provide valid inputs in all these fields. Rules are triggered when all their conditions are evaluated to true. Within a parent rule, you can use drag and drop to move a rule from one level to another level.
Note: Before creating an access policy rule, you should first configure the device profile and private applications.
To create a Private Access Policy:
- Go to Settings> Policy > Access Control > Private Access Policy.
- Click New Rule.
- Complete the following fields to create an access policy rule:
- Name — The name of the policy.
- Criteria — Select a criteria from the list and click OK. You can specify multiple criteria for a single rule. You can also view the logic used for the selected criteria.
- Application - A private application that has been created on the private app page. For more details see, Add Application
- Application Tag - A private application group that has been created on the private app page. For more details see, Add Application
- Device Profile - You can specify the device's attributes such as operating system, operating system version, firewall policy, antivirus software status, file path, and registry information (Windows devices). For more details see, Configure Device Profiles.
NOTE: Select the device profile as the criteria to validate the device posture. - Location - The location feature allows you to configure different authentication methods for different locations. A location can consist of one or more sites in a region or multiple sites across regions. For more details see, Location
- Process Name - Name of process running in a client machine.
- User Name - Enter a user from lists for which an action can be taken.
- User group - Enter a user or select a user group from lists for which an action can be taken.
Criteria For Client Based Access For Clientless Based Access Application 

Application Tag 

Device Profile 

Location 

Process Name 

User Name 

User Group 

- Operator — Specify the operator for the selected criteria.
- Value — Specify the value based on the set criteria.
- Action — Specify the action to be performed when a policy is enacted.
- Allow — Allows private application traffic.
- Block — Blocks private application traffic.
- Allow Web Policy — Applies the configured Web Policy rules to the private application traffic. For more information about Web Policy, see Web Policy.
- Allow with DLP — Applies web policy rules along with the DLP rules to the private application traffic. For more information about DLP, see Data Loss Prevention.
- Isolate — Applies Remote Browser Isolation policy to the private application traffic. For more information about RBI, see Remote Browser Isolation (RBI).
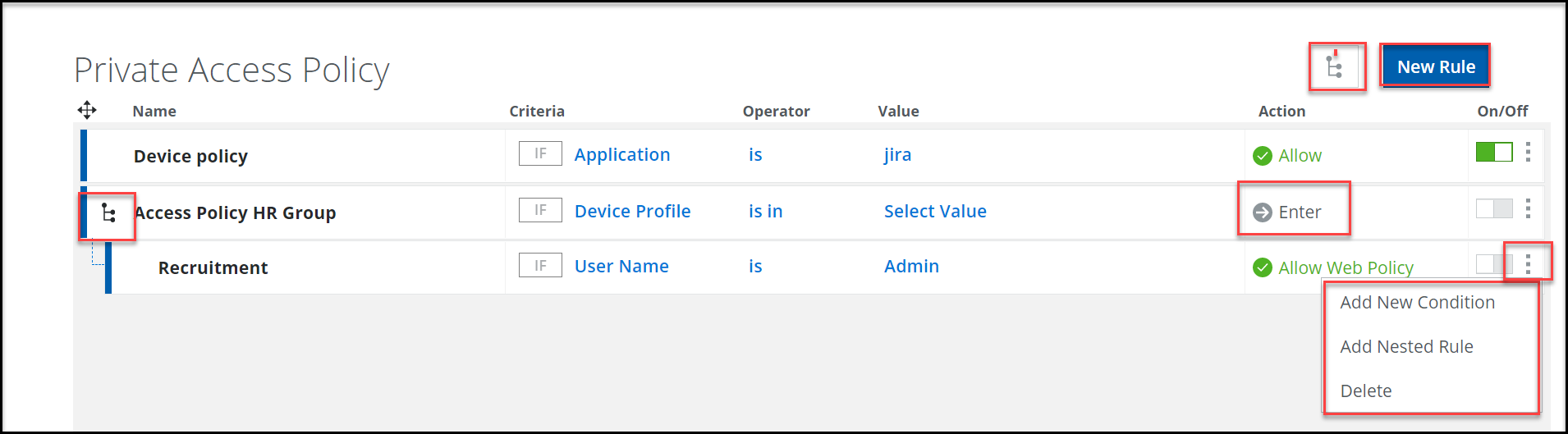
- Enter — Creates a new child rule.
NOTES:
- Private Access policy actions, such as Isolate, Allow with DLP, and Allow with Web Policy, are only supported for HTTP/HTTPS (TCP) traffic. If any of these actions are configured for other protocols (UDP, RDP, SSH, etc.) in the Private Access policy, Skyhigh Private Access will automatically block traffic for those other protocols.
- For UDP-based applications, only Allow action is supported. The other actions such as - Isolate, Allow with Web Policy, and Allow with DLP - the private access policy will automatically block traffic for these protocols.
- On/Off — Select On to enable a rule and Off to disable a rule. Click
 to view options such as Add New Condition, Add Nested Rule, and Delete.
to view options such as Add New Condition, Add Nested Rule, and Delete.
- Add New Condition — Adds a new condition (criteria). Select a criteria from the list and click OK. You can specify multiple criteria for a single rule. You can also view the logic used for the selected criteria.
- Add Nested Rule — The
 icon represents the nested rule. Click this icon to expand or collapse a nested rule. You can nest (up to four levels) rules inside a policy rule. You have to configure criteria, value, and action for this child rule. The Action option changes to Enter when you add a child rule. You can specify action to be performed for the child rules.
icon represents the nested rule. Click this icon to expand or collapse a nested rule. You can nest (up to four levels) rules inside a policy rule. You have to configure criteria, value, and action for this child rule. The Action option changes to Enter when you add a child rule. You can specify action to be performed for the child rules.
NOTES:
- If you test the SSH connection with PuTTY before authenticating to the Private Access Dashboard, your initialSSH connection will fail (Not Authenticated) and your browser will automatically launch forcing you to authenticate first. Once you complete the authentication, the next SSH connection you attempt will work.
- If for some reason you test and you can make the SSH connection without the SAML Authentication, then that means SCP Auth is being used to identify and authenticate the user.
- Publish the saved changes to the cloud now or keep working and publish later.
- Once the private access policy is published, you can access private applications using Skyhigh Private Access Dashboard / Launchpad - https://api.wgcs.skyhigh.cloud/ztna/dashboard
WARNING TO BE NOTED
Syhigh recommends not to disable the Private Access policy in the policy tree. If disabled, policy evaluation will be skipped, granting access to all Private Apps regardless of the configured rules.
When the status is Off

When the status is ON

