Client Proxy 4.6.0 Release Notes
This release focuses on enhancements for Skyhigh Private Access, Cloud Firewall features, and resolves issues. For more information about Private Access, see Skyhigh Private Access.
- Some Client Proxy features require specific minimum versions of the Trellix Agent. For information about the minimum compatible versions, see Compatible Versions of Trellix Agent.
- To ensure a seamless experience while upgrading Client Proxy 4.6.0, see Upgrade Client Proxy to 4.6.0 and later.
Enhancements
macOS Silicon M1 and M2 Support
Client Proxy now supports macOS system with a native M1 and M2 chip. For information about seamless upgrade, see Upgrade Client Proxy to 4.6.0 and later.
Supports Cloud Firewall
Configure Client Proxy to support Cloud Firewall key capabilities. For more information, see Skyhigh Cloud Firewall.
- Perform a deeper level inspection of network traffic and protect against malicious traffic.
- Enforce Cloud Firewall policy based upon IP address, processes, ports, and domains to filter your network traffic
Logging Events in Human Readable Format
The Client Proxy events like connectivity check failures, redirection errors, auto-policy-download failures, policy change, network change, captive portal check are now logged in a scp.loglog file in a human readable text. The log files are located in the C:\ProgramData\Skyhigh\SCP\Logs\Scp.log folder. This is supported only for Windows.
User Group Header Validation
Client Proxy running on Windows and macOS now validates and logs a failure message if the group header exceeds the maximum limit. The maximum header limit for the traffic redirection is 7186 bytes.
Enforce Time-based Policy
You can enforce a policy for a specific time range on both Windows and macOS systems. This means you can restrict web access during a particular period of the day to efficiently monitor and manage network resources. For example, you can block all social media sites for all users across the world during work hours (9 a.m. to 4 p.m.).
Skyhigh Rebranding Changes
- Uninstall SCP Command (macOS) - The usr/local/McAfee/uninstall MCP command is now rebranded to usr/local/McAfee/uninstall SCP.
- Install SCP on macOS 11.0.1 and later - The McAfeeSystemExtensions dialog displayed while installing Client Proxy 4.6.0 and later is now rebranded to TrellixSystemExtensions. For information about installing silently using MDM, see Silently Installing SCP 4.6.x using MDM (macOS).
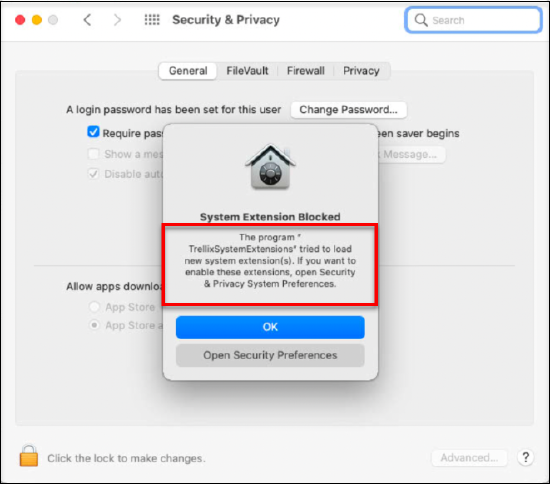
- User consent is required to install Client Proxy on macOS 11.0.1 and later. To allow extension to load:
- macOS below 13.0 - Go to System Settings > Security & Privacy > Allow
- macOS 13.0 and later - Go to System Settings > Privacy & Security > Allow
View Key Information about Client Proxy on macOS
You can now run the sudo /usr/local/McAfee/Scp/bin/scpcontrol.sh status command to view the following information about the Client Proxy software installed on the macOS systems:
- Policy Name
- Policy revision
- Policy Modified date
- Proxy Server
- Connectivity Status
- Alternate Proxy
- PA status
VSCore for DNS Interception
Replaced NTK drivers with VSCore for DNS interception to avoid network disruption while installing or uninstalling Client Proxy.
Resolved Issues
| Reference | Issue Description |
|---|---|
| MCP-4656 | Client Proxy now shows the status as Not Redirecting (Corporate Network) when connected over a corporate network on macOS as well. |
| MCP-4730 | You can access the private applications over RDP and SSH when their IP address is configured on macOS as well. |
| MCP-4807 | When the application or browser contains the standard port 80 with the host name, Client Proxy now removes the standard port 80 from the URL to normalize as per RFC 3986. |
| MCP-4839 | The sites configured in the alternate redirection bypass list were redirecting to the primary proxy instead of alternate proxy. This issue is now resolved. (macOS only) |
| MCP-5146 | Client Proxy now always performs connectivity check request for Cloud proxy policies. (macOS) |
| MCP-5184 | The About SCP Window now shows PA Status as Connected when secure channel is enabled on port 443. (Windows only) |
| MCP-5230 | Failed to delete the multiple catalogs that were generated within the Common Catalog under certain circumstances. This issue is now resolved. (Windows and macOS) |
| MCP-5231 | Do not start Captive portal check if the Egress IP prefixed Domain Name is NULL. (Windows and macOS) |
| MCP-5268 |
The web traffic from the processes configured on the bypass list failed to bypass. This issue is now resolved. (macOS only) Note: This issue was seen only in Client Proxy 4.5.0 version. |
| MCP-5301 | Client Proxy client failed to validate the Private Access policy and logged weird error messages. (Windows and macOS) |
Known Issues
| Reference | Issue Description |
|---|---|
| MCP-5629 | Client Proxy intermittently fails to redirect traffic when macOS system comes back from sleep. |
| MCP-5611 | Client Proxy fails to redirect traffic on a macOS client when it is shut down forcefully with the power button and powered up. Also the status of Client Proxy shows as Not Redirecting. |
