Coming Soon in our Next Release
- ► Click here to view the Skyhigh Security Service Edge 7.0.1 Release Timelines (GA on March, 05 2026 UTC)
-
Environment Skyhigh Products Release Date EU -
Skyhigh CASB
-
Skyhigh Data Loss Prevention
Feb 19, 2026 GovCloud
-
Skyhigh CASB
-
Skyhigh Data Loss Prevention
Feb 23, 2026
US
-
Skyhigh CASB
-
Skyhigh Data Loss Prevention
-
Skyhigh Private Access
-
Skyhigh Cloud Firewall
Mar 05, 2026
Skyhigh SWG Cloud Feb 16 - Mar 05, 2026 Skyhigh Infrastructure Releases
US Production PoC Point of Presence (PoP)
Skyhigh 7.0.1 Reverse Proxy (Skyhigh CASB)
Mar 12, 2026
US Production Prod Point of Presence (PoP)
Skyhigh 7.0.0 Reverse Proxy (Skyhigh CASB)
Mar 19, 2026
NOTE: The release dates are published to help you plan your schedule, and these dates may vary based on release readiness and other dependency status.
-
Legends Used
|
General Availability |
Skyhigh SSE Products
Skyhigh Secure Web Gateway
Enhanced Policy Control with Support for Parquet File Types 
The Skyhigh Secure Web Gateway now supports Parquet File Type as a valid media type and ensures these file types are scanned and secured. Parquet File Type is widely used in large‑scale data processing and analytics.
Key Benefits:
- Policy Control. Create rules to define actions when Parquet File Types are detected.
- Blocking Options. Configure policies to block downloads, uploads, archives, or transactions involving Parquet files.
This enhancement gives you greater control over data flows involving Parquet files, helping prevent unauthorized transfers and ensuring compliance with data protection policies.

Unified Policy Logic with Nested Boolean Operators 
Skyhigh Secure Web Gateway now supports nested AND and OR operators within the policy engine. Unlike earlier versions, nested boolean logic can now be used inside a single rule, providing full functional parity with SWG On‑Prem policy behavior.
Key Benefits
- Brings in parity between SWG Cloud and SWG On‑Prem policy logic.
- Build more expressive, fine‑grained policies without splitting rules.
This enhancement simplifies policy design by reducing rule sprawl, ensuring a consistent security posture across cloud and on‑premises deployments, and advancing Skyhigh toward a unified policy engine across the platform.

Enable ICAP-based DLP for Unified Data Protection 
Skyhigh now offers an Internet Content Adaptation Protocol (ICAP)-based DLP service that integrates Skyhigh DLP with third‑party proxies. This capability enables centralized inspection of data in motion without requiring changes to existing network infrastructure.
Key Benefits:
- Gain full visibility into data in motion across all web traffic from a single policy layer.
- Support ICAP servers with SWG acting as the inspection endpoint for third‑party proxies.
- Enforce centralized DLP policies consistently across cloud and on‑premises web traffic.
- Ensure secure, encrypted connectivity between proxies and the DLP service for safe content inspection.
This enhancement simplifies integration with existing proxy infrastructure, delivers consistent DLP enforcement across environments, and strengthens data protection through centralized visibility and control over sensitive information in motion.
Skyhigh CASB
Monitor User Activities, Threats, and Anomalies Using User UID 
The User Unique Identification (UID) number is a unique identifier assigned to each user within an organization. The Activities, Threats, and Anomalies pages now include a User UID column in their respective tables. The User UID consolidates all activities, threats, and anomalies under a single identifier across Sanctioned, Shadow/Web, and Private applications. This enhancement facilitates efficient tracking and analysis of user activities within the organization.
You can filter all activities related to a specific User UID using the Omnibar search and the Activities, Threats, and Anomalies Cloud Card.


Strengthen AI Security with Agentic AI Attribute 
Skyhigh Cloud Registry now offers support for the Agentic AI attribute, which detects and tracks services that utilize Agentic AI, enhancing visibility into risk assessment and improving overall AI security posture. By flagging Agentic AI in cloud services, organizations can identify the services capable of autonomous actions, implement appropriate security controls, and strengthen governance over AI-related risks.
Agentic AI refers to AI services that autonomously plan, decide, and act to achieve defined goals without direct instruction. Unlike traditional AI, which responds only to explicit prompts, agentic systems can use tools, access services, and carry out multi-step actions with minimal human involvement. If Agentic AIs are not identified within the services, organizations may struggle to pinpoint the root causes of AI-driven activities and incidents.
Key benefits of identifying Agentic AI in your cloud services:
- Classify the service as higher risk
- Apply enhanced monitoring and controls
- Make informed allow/block decisions
- Improve audit and compliance alignment
- Reduce exposure from autonomous actions

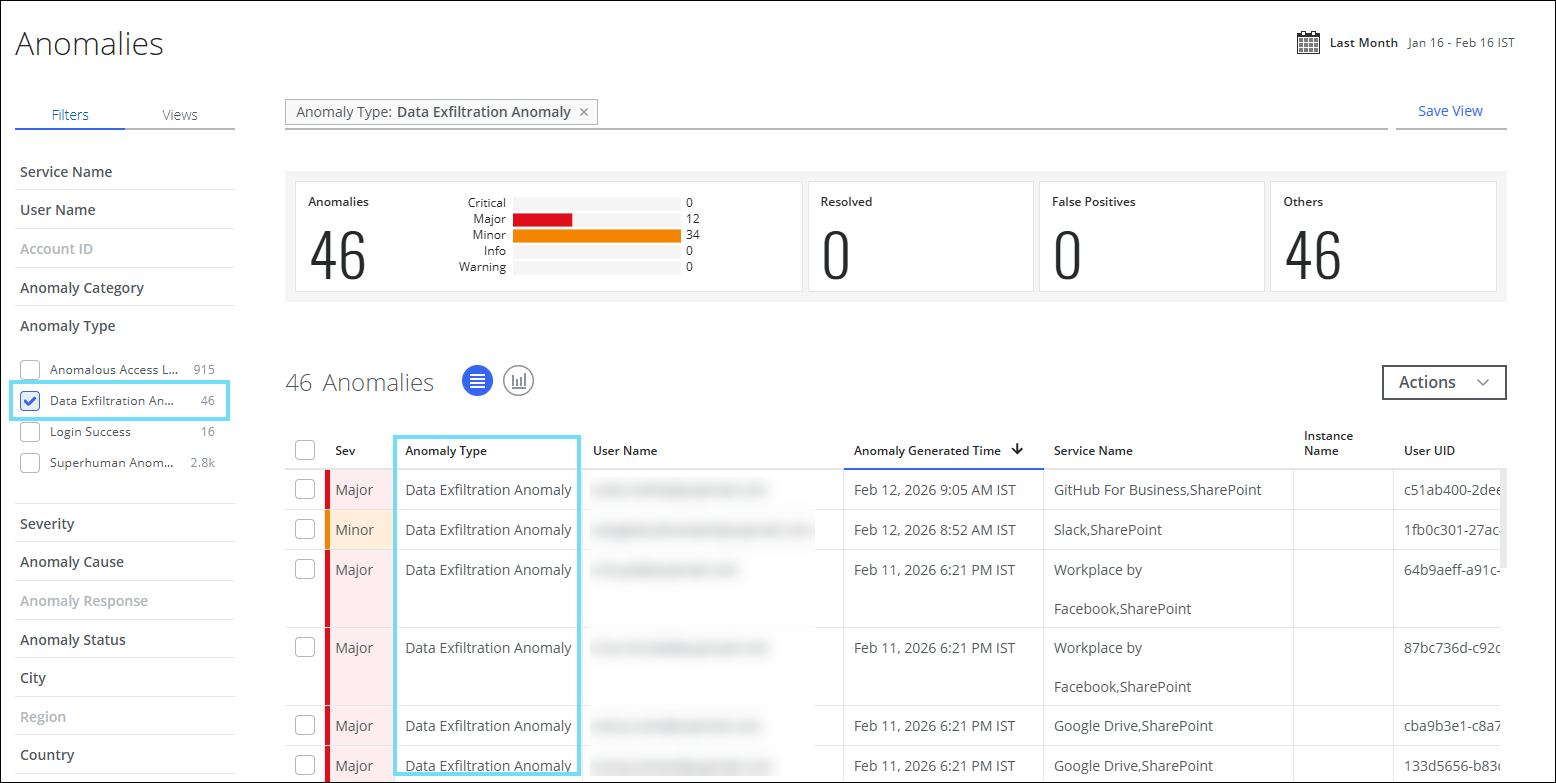
Identify Data Exfiltration Anomalies for a Unified User 
Skyhigh CASB now supports a new Data Exfiltration Anomaly category for unified users. Data Exfiltration Anomalies refer to activities involving the unauthorized or unusual transfer of data from an organization to external destinations. This includes instances such as downloading data from sanctioned services and uploading it to shadow services. Additionally, it detects abnormal activities within the organization, such as mass downloads from sanctioned services or access to data that contradicts a user's role, particularly when sensitive or classified files are involved.
Key Benefits
- Dynamic Detection. Moves beyond static thresholds by identifying sudden spikes in activity, role-inconsistent access, cross-domain transfers, and low-and-slow patterns that may indicate an intent to circumvent security controls. Proactive detection of data loss, clearer investigation context, and faster, risk-aligned response across cloud, web, and user activity.
- Increased Detection Accuracy. By focusing on behavioral patterns rather than fixed criteria, the detection capabilities significantly enhance signal quality, helping you pinpoint genuine threats while minimizing false positives. Unified UEBA intelligently compares a user's current activity against their historical behavior and that of their peers, ensuring a comprehensive understanding of normal operations.
This sophisticated approach allows your security team to respond proactively to potential data exfiltration attempts, ensuring the integrity of your sensitive information.
Additional Enhancements to Unified User Risk tab 
The Unified User Risk tab is enhanced to provide more detailed metrics on user activity and improved insights into risk attributes.
The User Risk tab has enhanced with the following capabilities:
- Clear visibility into the scores for each risk attribute that contributes to the overall risk category score.
- Risk scoring is applied at the category level, with distinct scores for Sanctioned and Shadow categories. This structure enables organized and actionable risk analysis.
- More precise and narrowly focused results. When a risk category is selected, the results show only the attributes that contributed to the risk score, rather than all available attributes.
- Improved accuracy of user risk scores, resulting in fewer false positives.
These enhancements boost the unified user risk experience by providing a clearer view for analysts and executive-ready visualizations of risk, facilitating faster investigations and more effective communication of risk-related information.

