Skyhigh Security Cloud Release Notes 6.4.0 (July, 2023)
Skyhigh Cloud Platform
Data Loss Prevention (DLP)
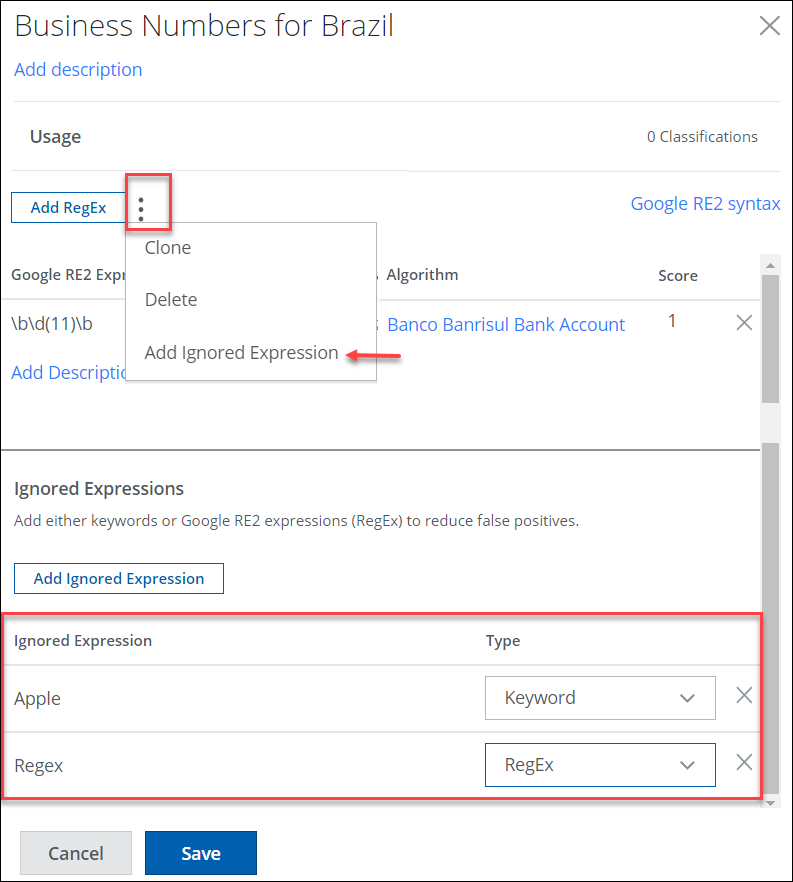
Reduce False Positives in DLP Advanced Patterns with the Ignored Expressions
You can now ignore certain expressions to reduce false positives in the Advance Patterns (found under Policy > DLP Policies > Classifications > Actions > Create Classification > Conditions). The Add Ignored Expression option allows you to add exceptions as ignored expressions in regular expression-based classifications.
This empowers organizations to finely customize DLP configurations by specifying exceptions that won't trigger matches. With these exceptions, data classification workflows can be controlled more precisely, reducing false positives and handling specific cases more accurately. Data protection strategies are optimized by enhancing precision and reducing disruptions. For details, see Create Custom Advanced Patterns.
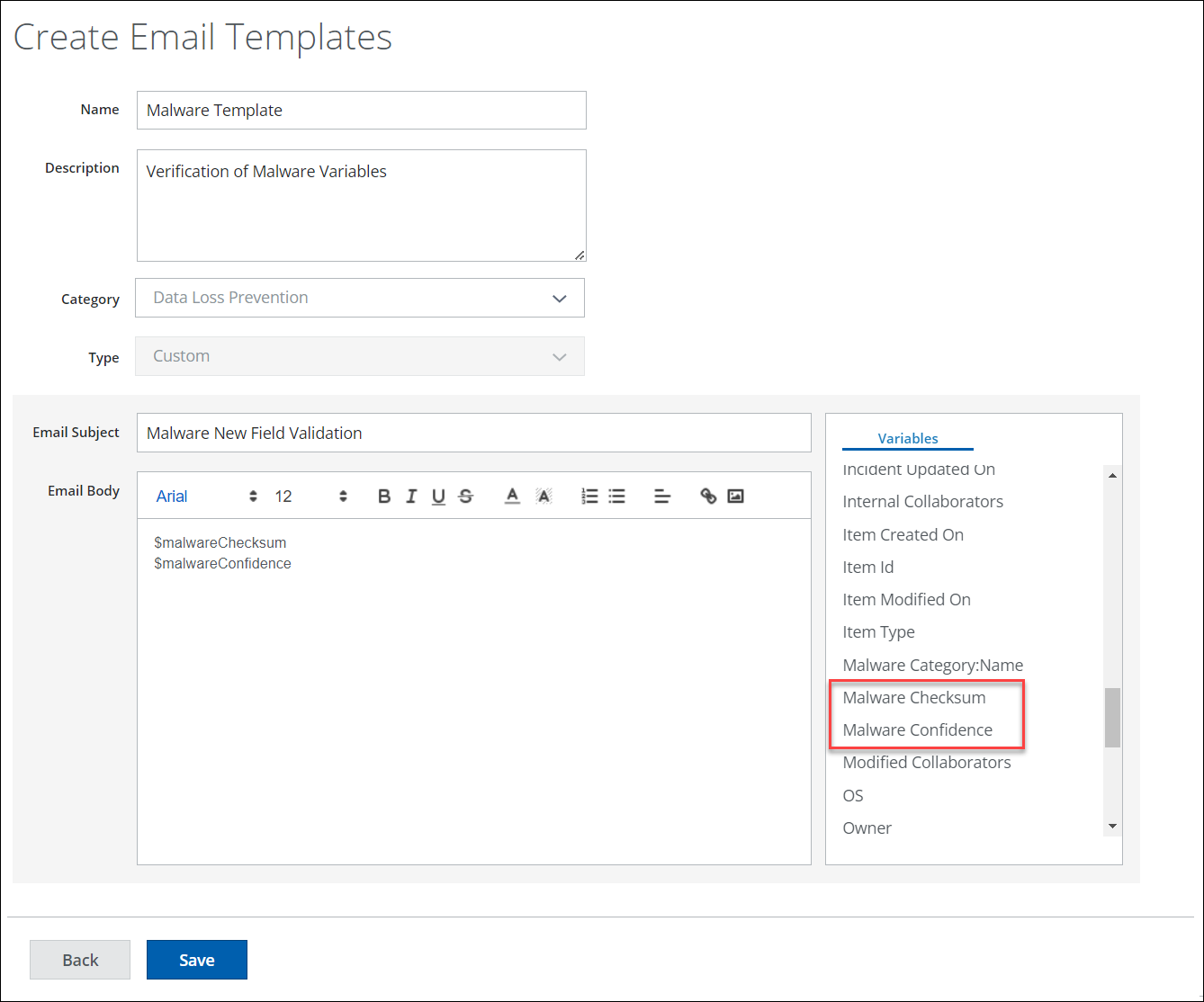
New Email Template Variables for Malware (Limited Availability)
The customizable email templates (under Policy > Policy Settings > Email Templates > Create Email Templates) now offer admins to take advantage of two new variables Malware Checksum and Malware Confidence. Custom Email Templates can be used with End User Remediation for Malware Verification. For details, see Create a Custom Email Template.
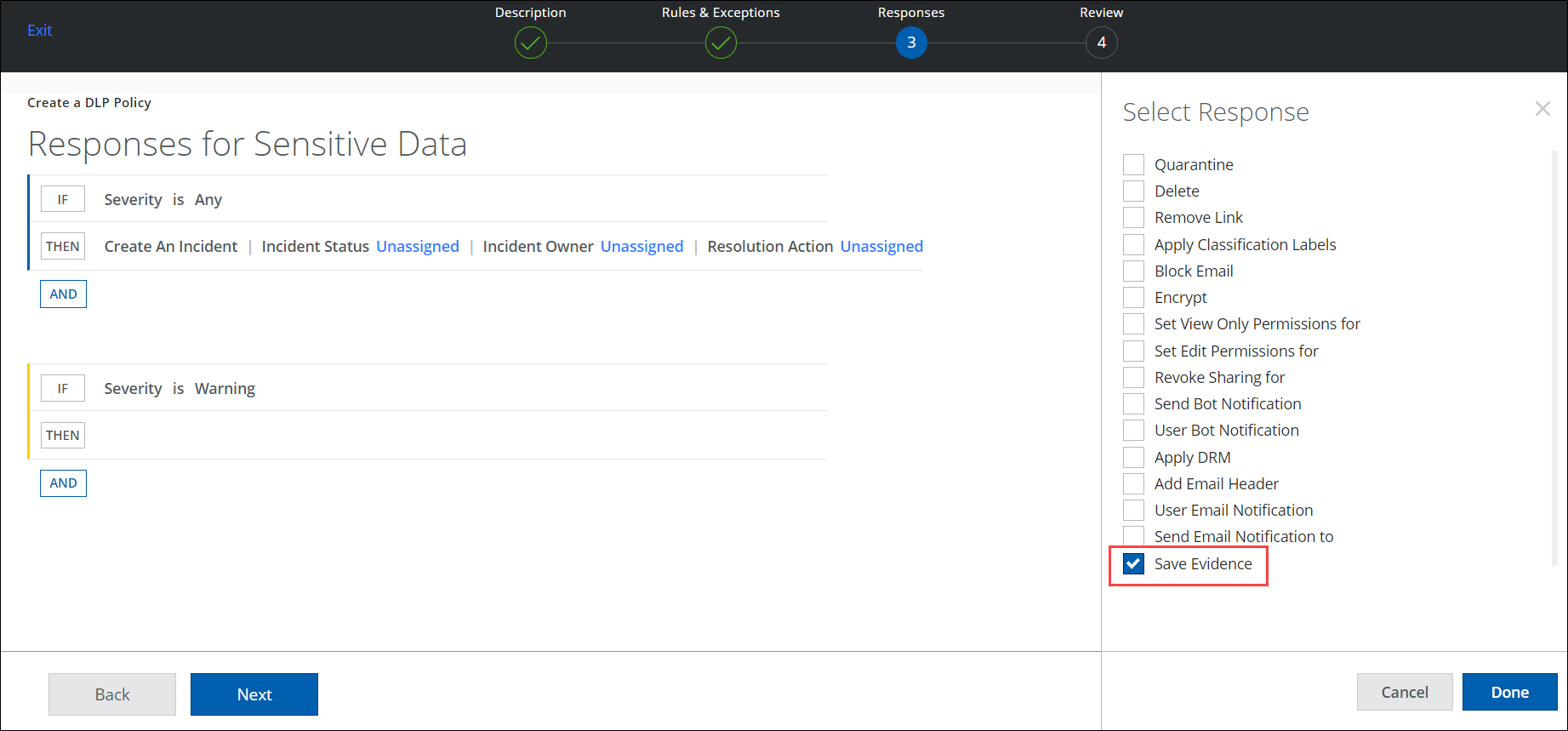
Flexible Cloud-to-On-Premise Evidence Synchronization: Empowering Customer Choice (Limited Availability)
When creating a new rule in Skyhigh CASB DLP Policy (found under Policy > DLP Policies > DLP Policies > Actions > Sanctioned Policy > Create New Policy), you can now access a new response named "Save Evidence." With this response, you can choose the significant policies to which evidence files should be retained for synchronization to Trellix ePO and disregard other policies. This allows you to achieve greater control over data management and reduce synchronization time with ePO by removing large amounts of insignificant evidence files. For details, see Configure Save Evidence in Skyhigh DLP Policy.
Skyhigh SSE Products
Skyhigh Private Access
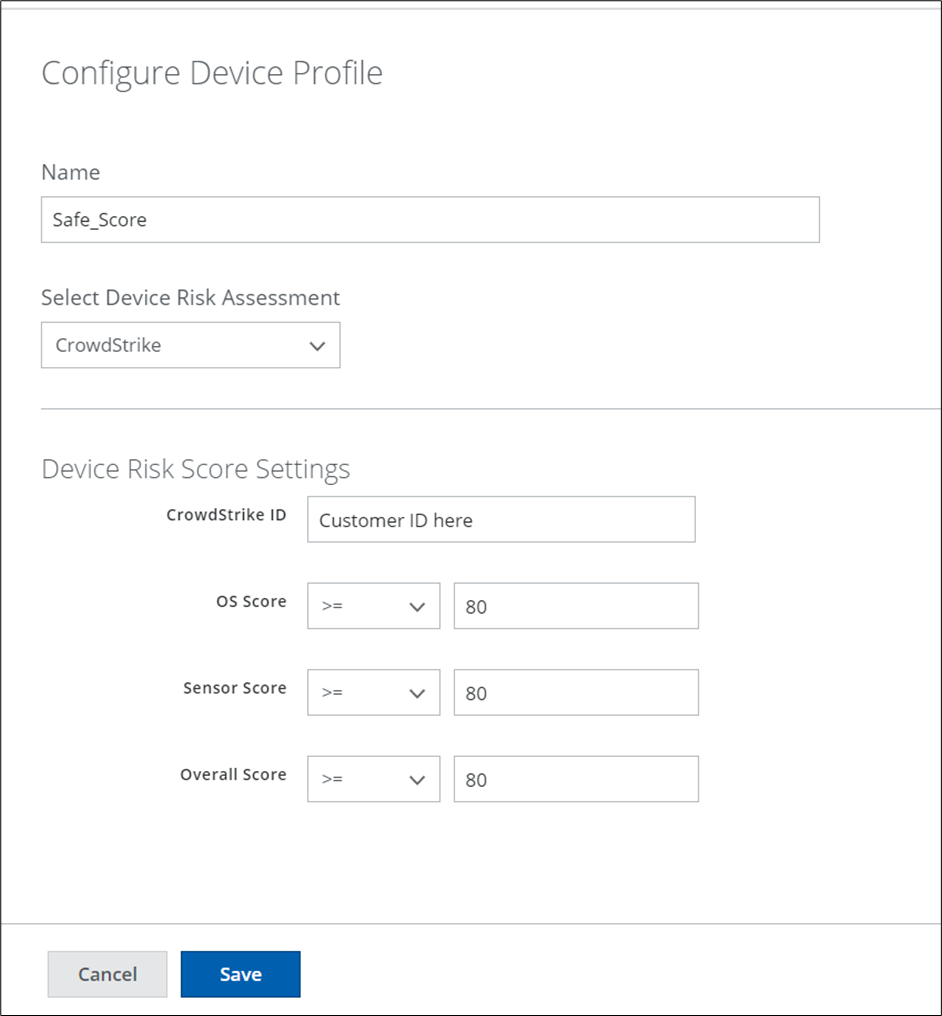
Configure Device Profiles - CrowdStrike
Skyhigh SSE platform enables customers to create Zero Trust device policies using a combination of native Zero Trust Assessments capabilities such as OS version, presence of registry key, Antivirus(On/Off), and more to assess device posture. CrowdStrike performs zero trust assessment and provides various scores such as OS score, sensor score, and an overall score of the client. By using a combination of these scores, you can enforce a powerful Zero Trust Assessment of devices before allowing access to private applications via Skyhigh Private Access.
To use the CrowdStrike integration option, enable the CrowdStrike toggle button (found under Settings > Infrastructure > Web Gateway Setup > Configure SCP > Manage SCP > Global Configuration > Device Risk Assessment Settings page).
For details, see Configure Device Profiles - CrowdStrike
Access Private Applications through Trellix ePO-OnPrem and Trellix ePO-SaaS with SCP 4.7.0
Skyhigh Client Proxy can now be deployed along with a PA policy file (OPG) using Trellix ePO. Earlier, this was done manually or via deployment tools.
To enable this feature, select the Download Policy From Skyhigh SSE checkbox. This pushes the policy to all endpoints, and the endpoints will synchronize with the SSE SCP policy. For details, see Access Private Applications through Trellix ePO-OnPrem and Trellix ePO-SaaS.
NOTE: Once SSE and ePO are synced, the endpoints are applied only with the SSE SCP policy. If you clear the checkbox, endpoints consider only the SSE SCP policy and not the ePO SCP policy.
Trellix ePO-OnPrem
.png?revision=1)
Trellix ePO-SaaS
.png?revision=1)
Skyhigh Cloud Firewall
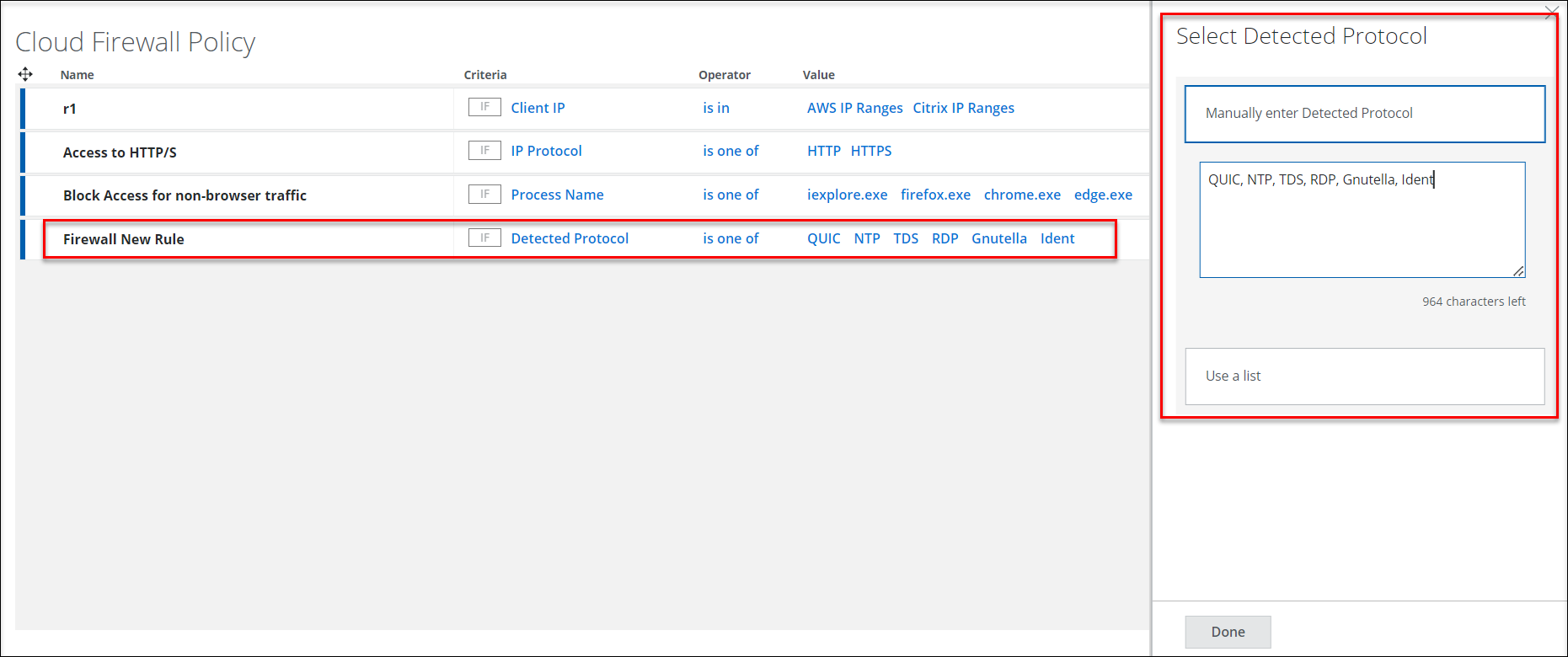
Support for Additional Protocols
The Cloud Firewall policy now supports these protocols: QUIC, NTP, TDS, RDP, Gnutella, and Ident. For more details, see Configure Firewall Policies.
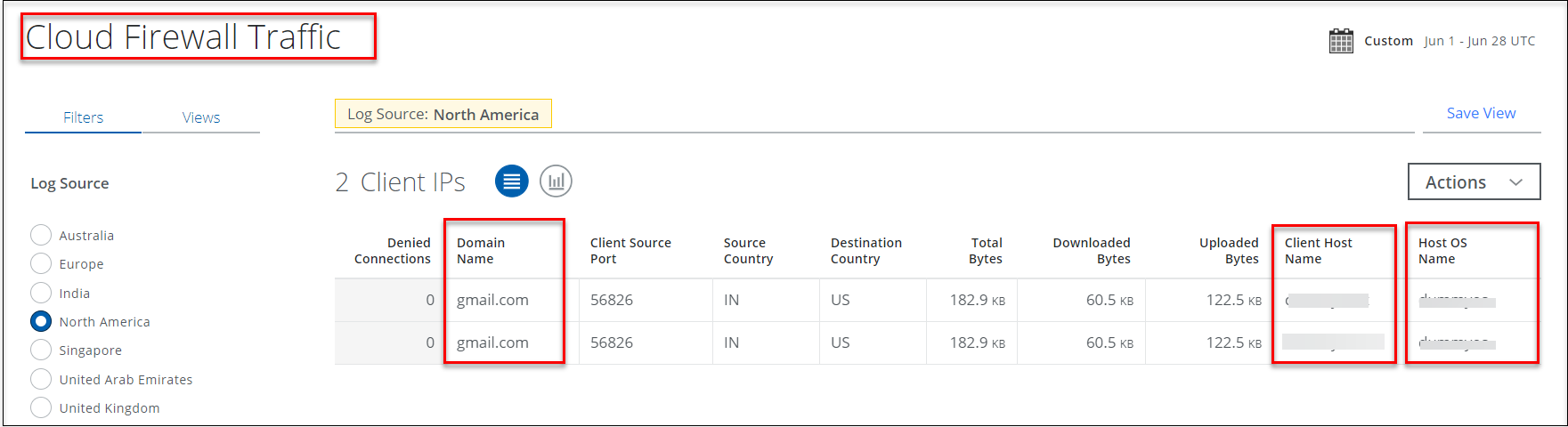
Cloud Firewall Traffic and Users Reports Enhancements
The Cloud Firewall Traffic and Cloud Firewall Users reports are enhanced with the following fields:
- Domain Name. Displays the domain names of the applications accessed by the user. Click the count link to view the list of domain names accessed.
- Client Host Name. Displays the name of the client host. The count is displayed in the case of multiple host names.
- Host OS Name. Displays the host OS details (OS name and OS version) of the client system. The count is displayed in the case of multiple operating systems running on a host.
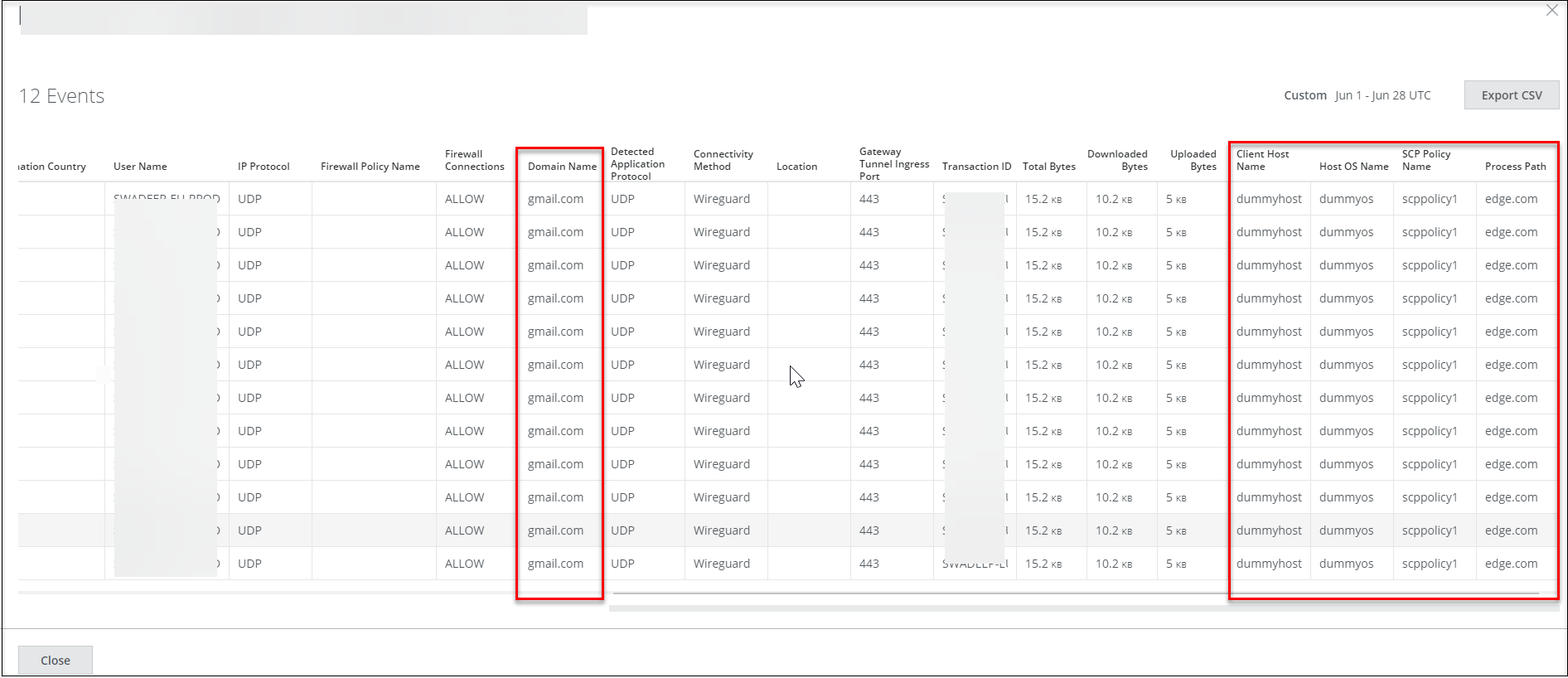
In addition to the Domain Name, Client Host Name, and Host OS Name fields, the Events Data page is enhanced with the SCP Policy Name and Process Path for the Cloud Firewall Traffic and Cloud Firewall Users reports. For more details, see Cloud Firewall Traffic and Cloud Firewall Users.
Skyhigh CASB
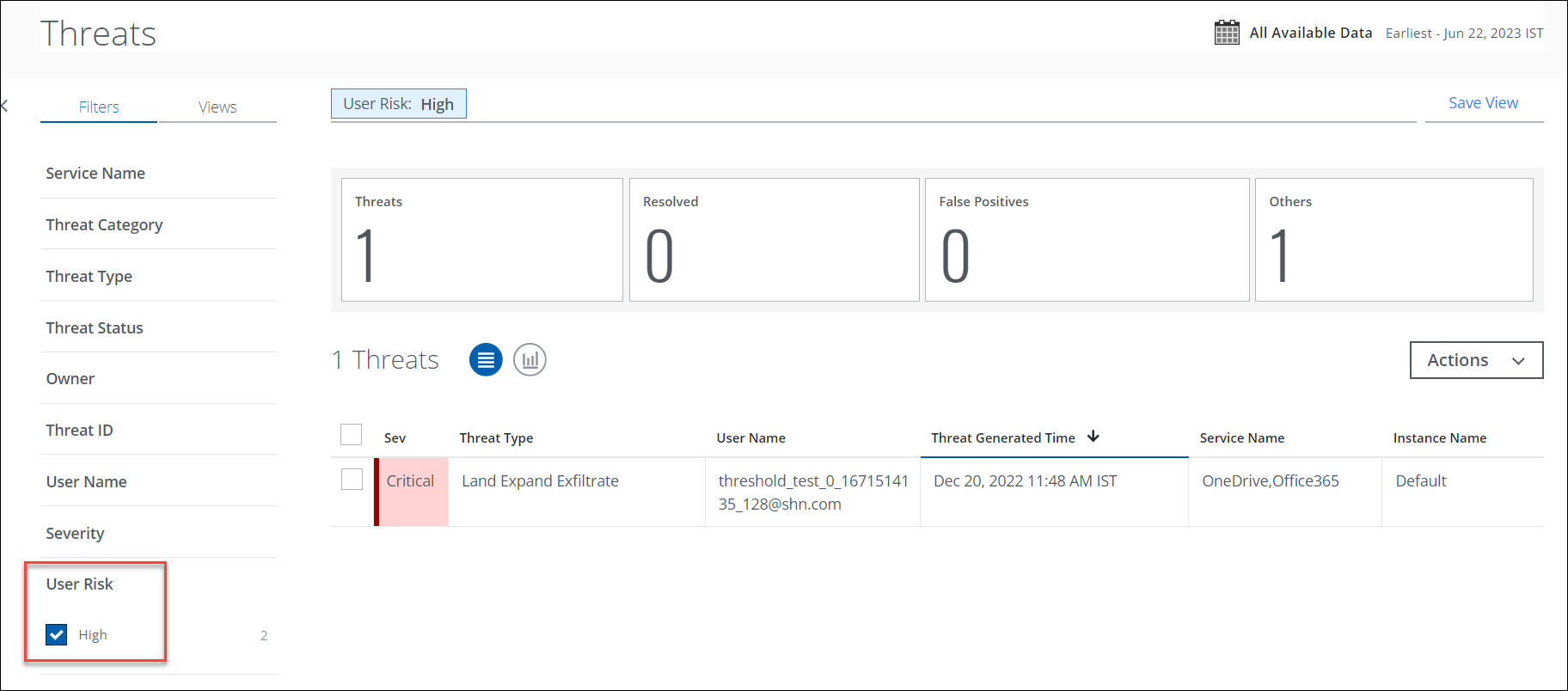
Filter for User Risk on Threats and Anomalies Page
You can now filter and categorize your search by User Risk score for High-risk activities on the Threats (found under Incidents > Threats) and Anomalies page (found under Incidents > Anomalies > Anomalies). If there are no high-risk users in your tenant, the User Risk filter can’t be seen on the Threats and Anomalies page.
User Risk is also supported in Saved View, Chart View, Dashboard Cards, and Generate Reports for Business Report (PDF), CSV, XLS, and Schedule Reports. For details, see, Threats and Anomalies.
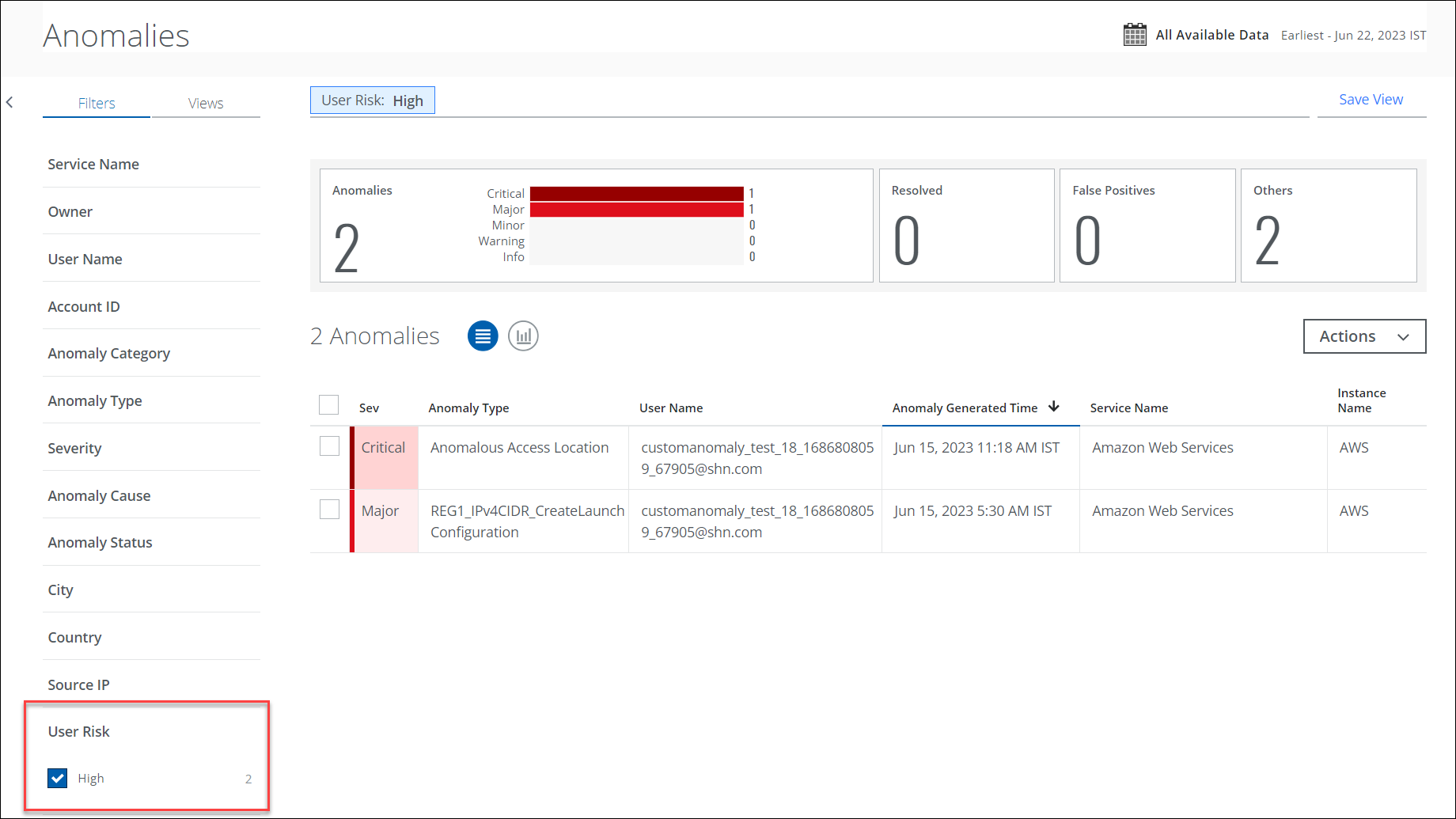
Support for Slack Non-Enterprise (Pro/Business+) Licenses (Limited Availability)
Skyhigh CASB now supports Slack’s granular bot permissions framework for API integration of Non-Enterprise (Pro/Business+) licenses. For details, see About Skyhigh CASB for Slack Non-Enterprise. Slack Non-Enterprise API integration requires a client ID and a secret key to enable API access in Skyhigh CASB. You can use a manifest file to create a Custom OAuth application for Slack Non-Enterprise licenses. For details, see Integrate Skyhigh CASB with Slack Non-Enterprise.
Skyhigh CASB's API Integration for Slack Non-Enterprise licenses includes the following features:
Supported Remediation Actions and Channel Types in Slack
| Remediation Actions | Channel Types | Supported |
|---|---|---|
|
Delete Files |
Slack Public/Private Channels and DMs (Direct Messages) | Yes |
| Slack Shared Channels | No | |
|
Delete Messages |
Slack Public/Private/Shared Channels | Yes |
| Slack DMs (Direct Messages) | No | |
|
Quarantine Files |
Slack Public/Private Channels and DMs (Direct Messages) | Yes |
| Slack Shared Channels | No | |
| Quarantine Messages | Slack Public/Private/Shared Channels and DMs (Direct Messages) | No |
Supported DLP Policy Rules and Response Actions in Slack
| DLP Policy Rules | Supported |
|---|---|
|
Yes |
| Collaboration | No |
| DLP Policy Response Actions | Supported |
|---|---|
|
Yes |
Skyhigh CNAPP
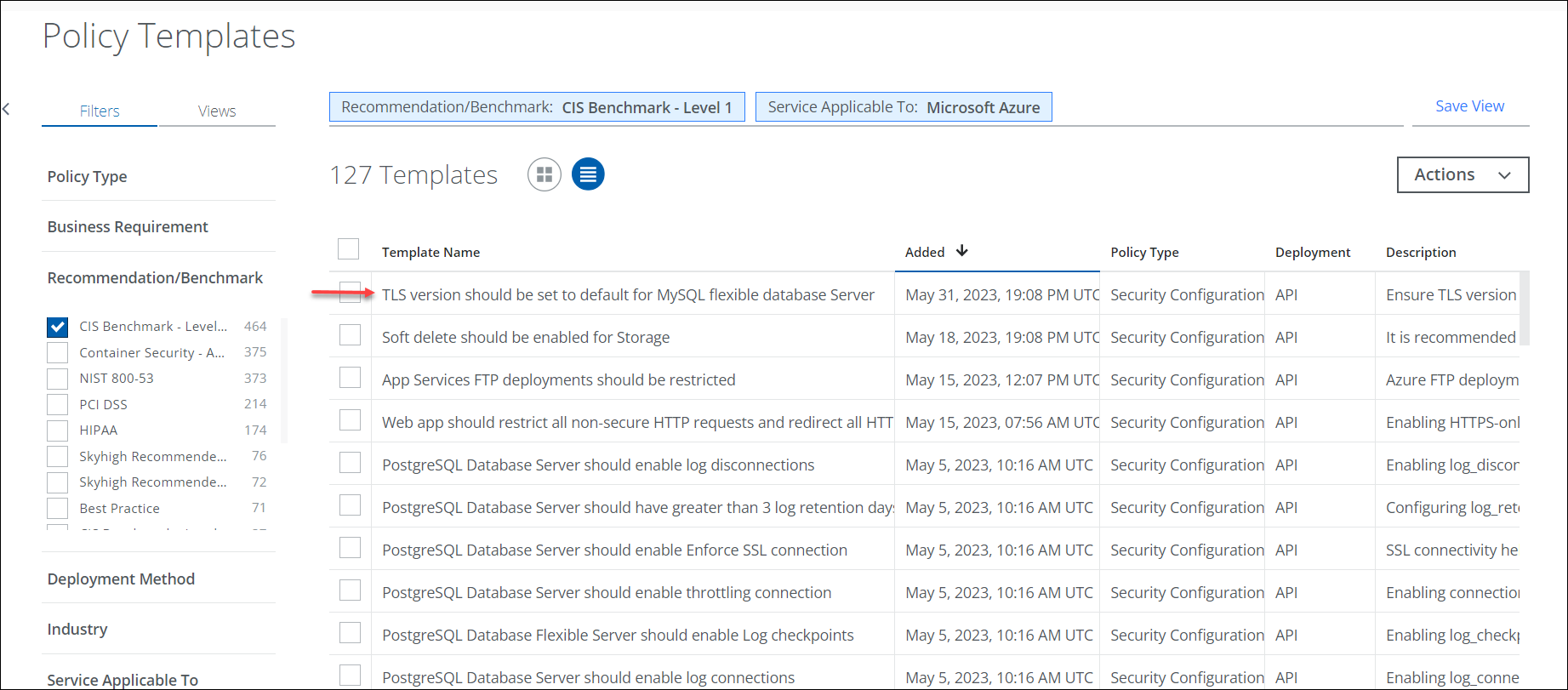
New Azure CIS v2.0 Policy Templates
CIS Benchmarks are based on technical configuration settings used to maintain and increase enterprise security, especially when used in conjunction with other essential cyber hygiene tasks. In this release, 1 new Azure Policy template (TLS version should be set to default for MySQL flexible database Server ) is added for the CIS v2.0.0 Level 1 benchmark. The new Policy Template can be found under Policy > Policy Templates. For details, see Policy Templates for Azure.
 Click here to view Skyhigh Security Cloud Resolved and Known Issues
Click here to view Skyhigh Security Cloud Resolved and Known Issues- For details, see Skyhigh Security Cloud Bug Fixes and Known Issues.
