Skyhigh Security Cloud Release Notes 6.6.0 (Feb 2024)
Legends Used
|
General Availability |
Skyhigh Cloud Platform
Skyhigh Data Loss Prevention (DLP)
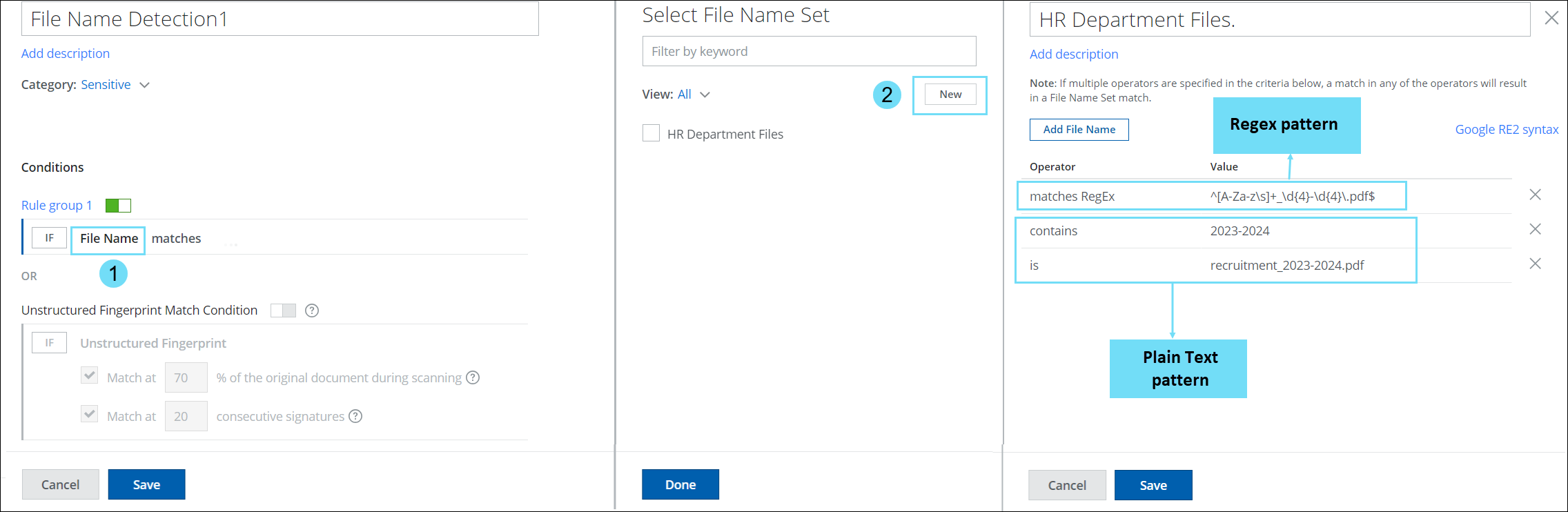
Create File Name Set Classification Condition with Text or Regex Patterns 
The File Name Set classification condition allows you to define the list of file names, which can be used to match, process, and protect sensitive data during the DLP policy evaluation. This condition helps to identify and manage sensitive files and protect sensitive data leaving your organization.
You can define file name set using plain text values with is and contains operators. These operators precisely identify specific files by either matching their exact names or by searching for contained values to trigger a match. Alternatively, you can define file name set using regular expressions, which gives you greater flexibility in matching complex file names. By using this condition, you can easily ensure the security of your data. For details, see Create a Classification using File Name Set.
Navigation Details
- To access the File Name Classification condition, go to Policy > DLP Policies > Classifications> Actions > Create Classification > Conditions > File Name.
- To access the text or Regex patterns operators, go to Select File Name Set cloud card > New.
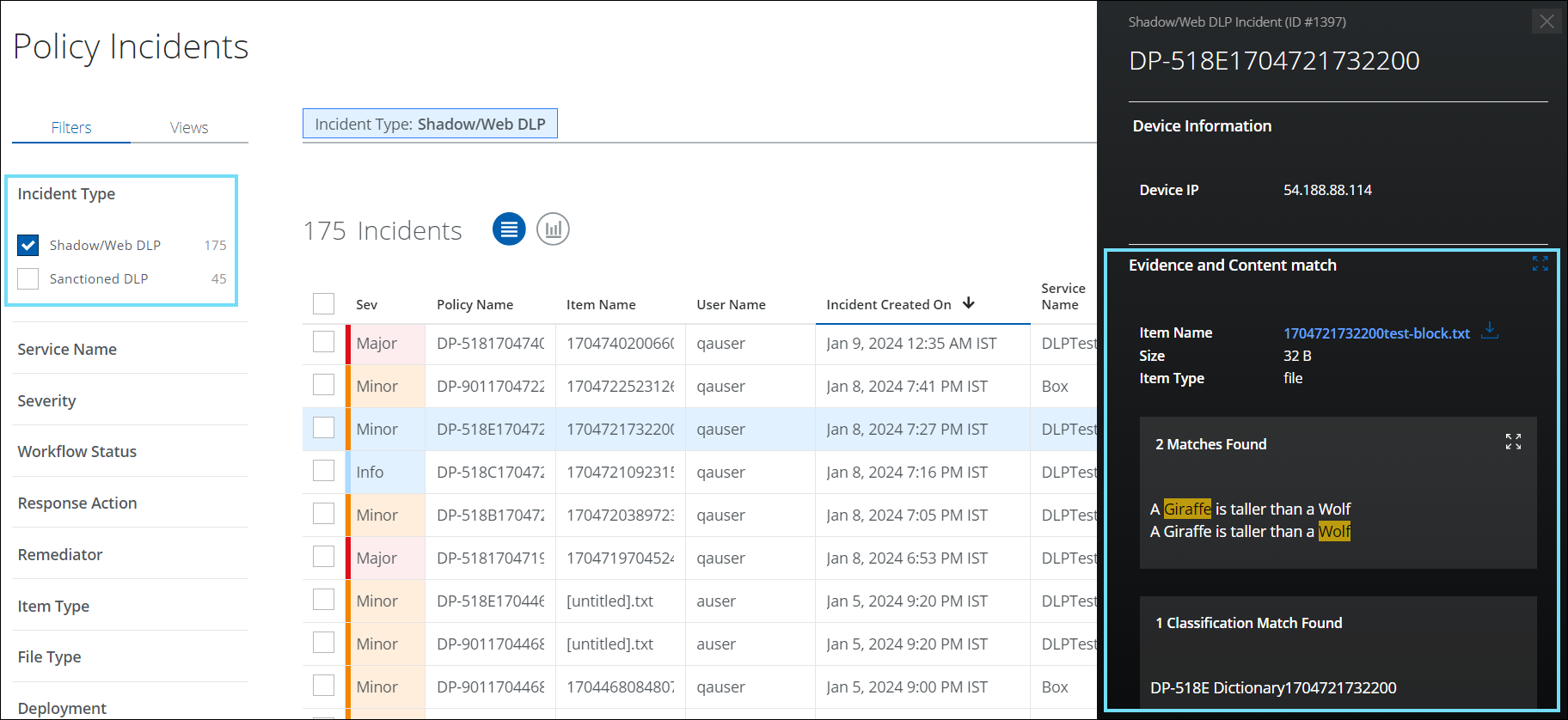
View Match Highlights via Shadow/Web DLP Incident Cloud Card 
You can now view match highlights that are linked to Shadow/Web DLP incidents on the Shadow/Web DLP Incident Cloud Card (found under Incidents > Policy Incidents > Policy Incidents page). Match highlights display the highlighted keywords that violated the DLP policy, along with surrounding text which can be used to identify false positives. Once match highlights are saved in your data storage provider, you can access the match highlights of violated DLP incidents and perform additional forensics on the generated incidents. For details, see View Match Highlights for Shadow/Web DLP Incidents.
The process of viewing match highlights from individual DLP incidents is made more secure and controllable by applying Role-Based Access Control (RBAC). RBAC ensures that only authorized users within a tenancy are granted access to view match highlights for DLP incidents, thereby providing an additional layer of security to the overall process. For details, see About User Roles and Access Levels.
For example, a Security Operations Center (SOC) can restrict access to view match highlights for DLP incidents on the Policy Incidents page to designated users only. To achieve this, the SOC must first create a Saved View Data Jurisdiction for the Policy Incidents page. Subsequently, the SOC can assign the Incident Management role and Display Match Highlights permission to specific users, granting them the ability to view match highlights for DLP incidents. This ensures that only authorized users can access sensitive information related to DLP incidents, minimizing the risk of data exfiltration.
Skyhigh SSE Products
Skyhigh Secure Web Gateway
View List of Updated and New Rule Sets 
A What's New section has been added to the Web Policy page. It allows you to view a list of the updated and new rule sets that are available for use in your web policy.
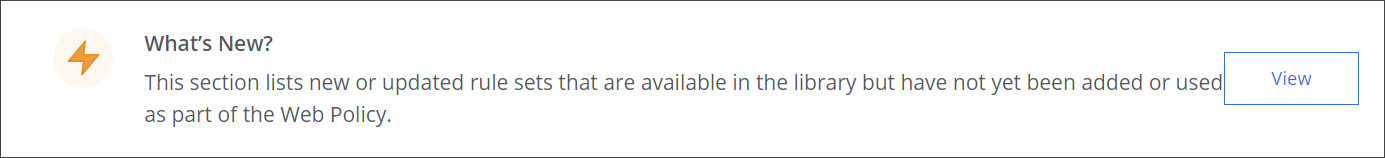
To go to the Web Policy page, select Policy > Web Policy > Policy on the user interface. Clicking View in the new section opens the list.
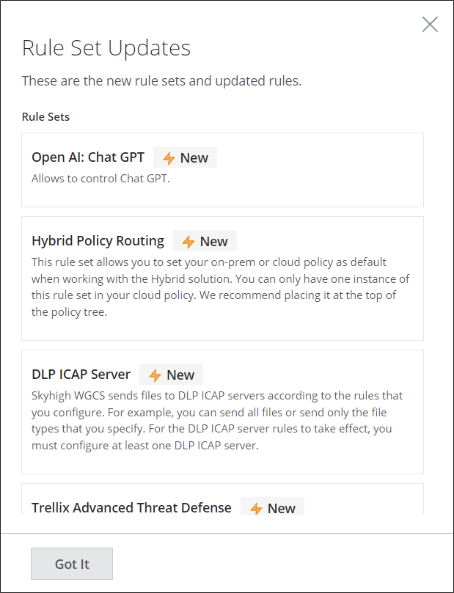
You can add each of these rule sets to your web policy by importing it from the rule set library. After you have imported a rule set, it is removed from the list.
Once you have imported all updated and new rule sets, the What's New section is not shown on the Web Policy page anymore.
For more information, see Web Policy Page.
Search and Sort Lists in the List Catalog 
You can now search and sort the lists that are provided in the list catalog for use in the rules of your web policy.
To go to the list catalog, select Policy > Web Policy > List Catalog on the user interface. On the left of the List Catalog page that appears, expand a list type and select a list, for example, expand Media Type, and select the Audio List.
The list is displayed with its items on the right.
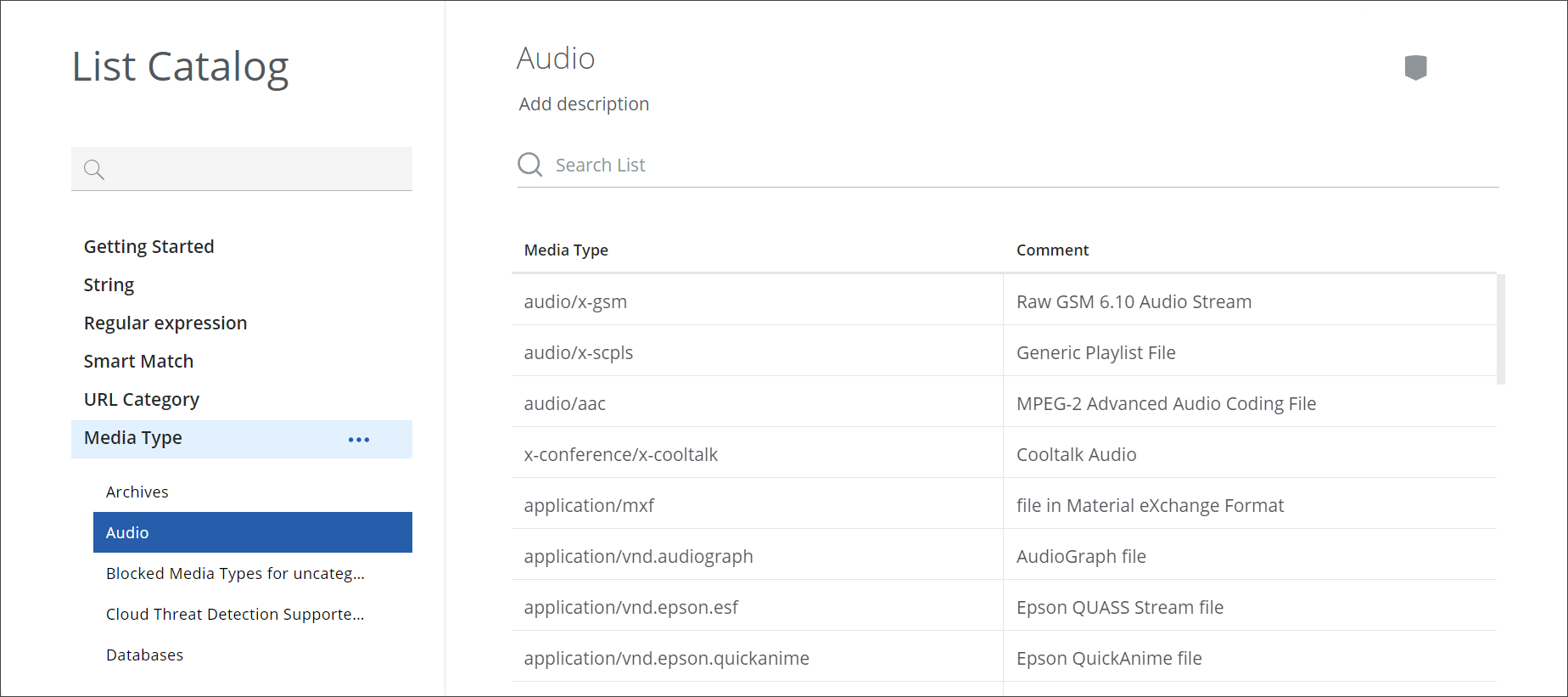
To search this list, you enter a suitable search term in the search field at the top. For example, to search for all audio file types that have wave in their names, enter wave.
The file types with names that match the search term completely or in parts are shown. If there is a match in the comment on a file type, it is also shown. The search is not case-sensitive.
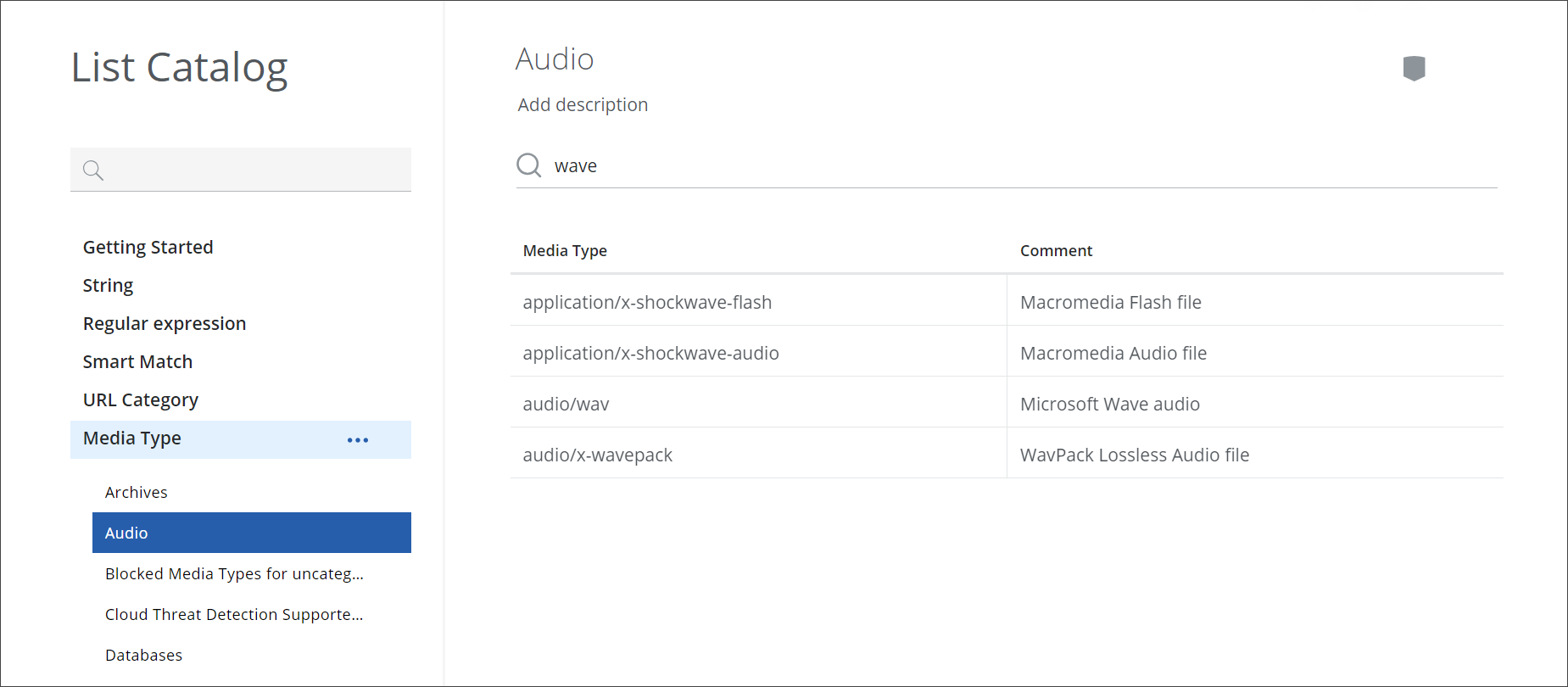
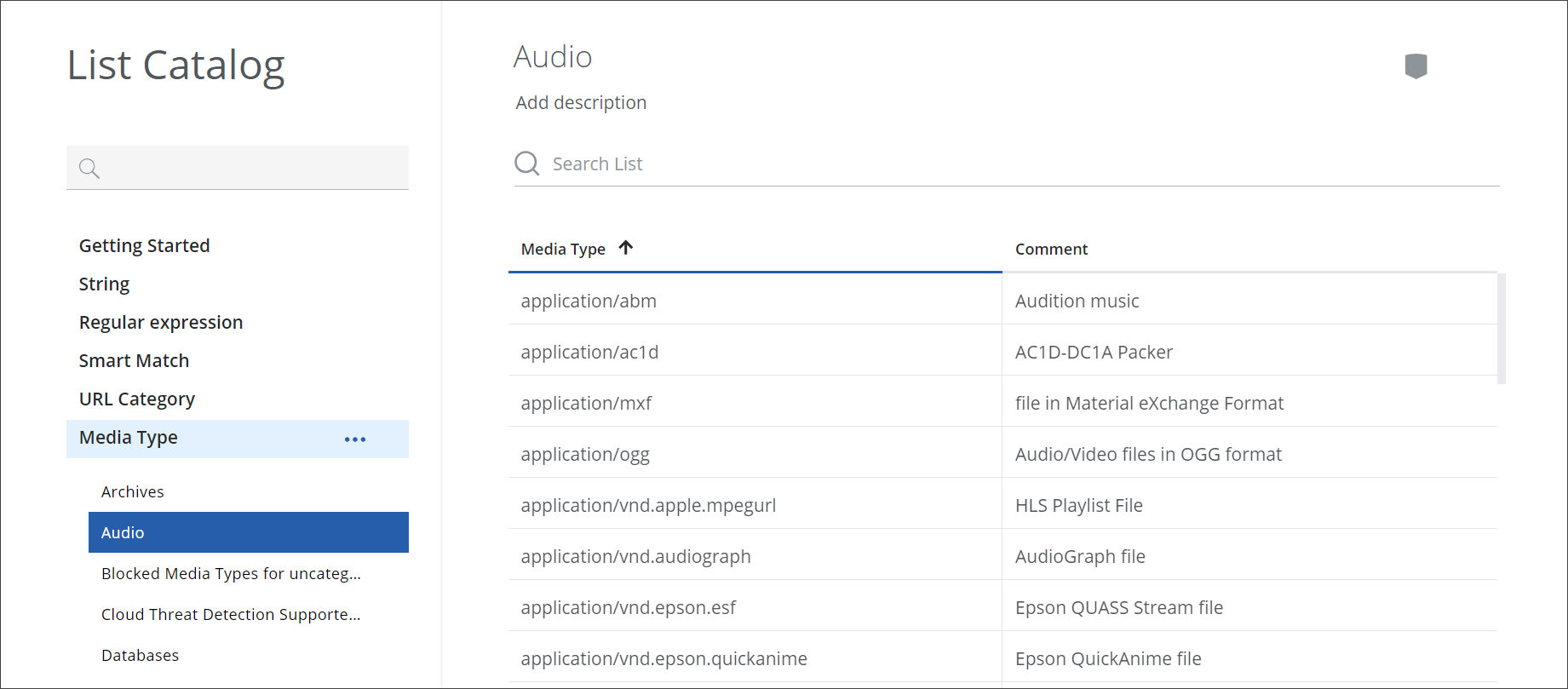
To sort the list, you place your mouse pointer over the line at the top of the Media Type column and click the upward arrow that appears.
The names of the Audio file types are then sorted in forward alphabetical order.
To sort these names in reverse alphabetical order, you place your mouse pointer over the upward arrow, which will turn it into a downward arrow.
Clicking this downward arrow sorts the names in reverse alphabetical order.
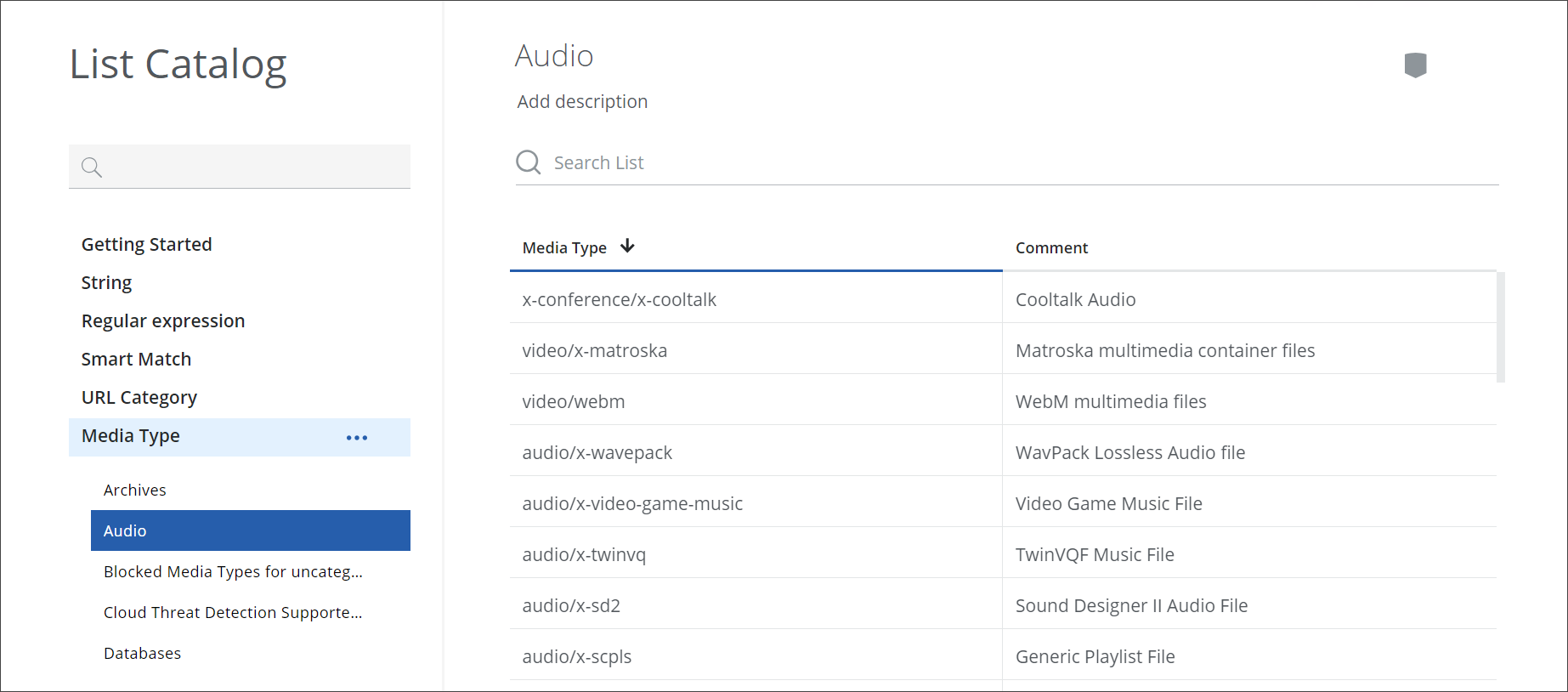
You can also sort the items under Comment in this way.
For more information, see Search a List in the List Catalog and Sort a List in the List Catalog.
Skyhigh Private Access
Deploy Secure App Connector V2 on AWS using CloudFormation Template 
Secure App Connector V2 is now available as an AMI (Amazon Machine Image) which enables it to be deployed on AWS Cloud using CloudFormation Template. For deployment steps, see Deploy Secure App Connector V2 on AWS using CloudFormation Template
.png?revision=1)
.png?revision=1)
Skyhigh Cloud Firewall
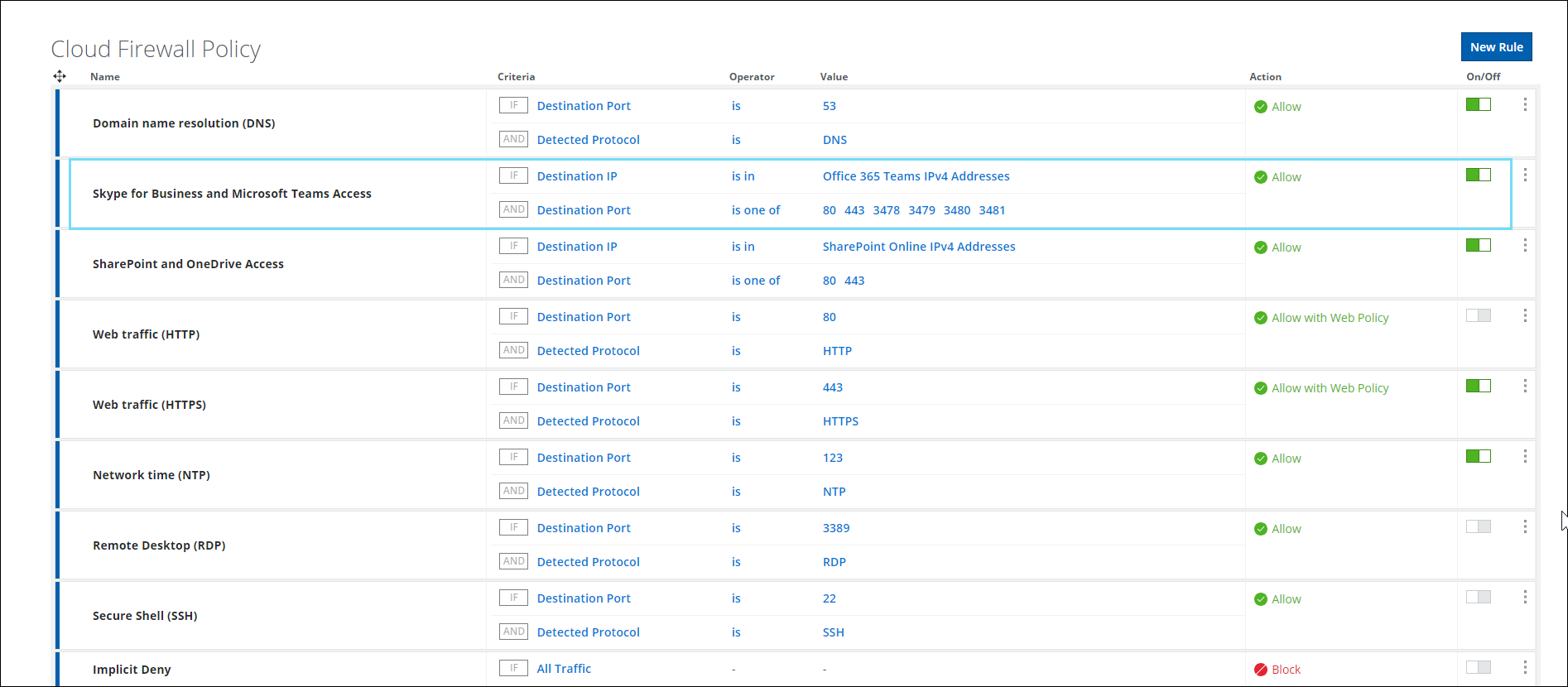
Enable Microsoft O365 Access in Default Cloud Firewall Policy 
Microsoft Office 365 access is enabled on the default policies in the Cloud Firewall Policy page (found under Policy > Cloud Firewall > Policy) when provisioning a new tenant. Existing tenants can replicate this policy using rule builders.
By adding Microsoft O365 access to the default policy, users can enable Cloud Firewall policy without impacting their access and ensure a seamless user experience from the first day of using Skyhigh Cloud Firewall. For details, see Configure Cloud Firewall Policy.
Skyhigh CASB
Salesforce Spring 2024 Support 
Skyhigh CASB now supports the latest Salesforce Spring 2024 version. For details, see Supported Versions of Structured Apps.

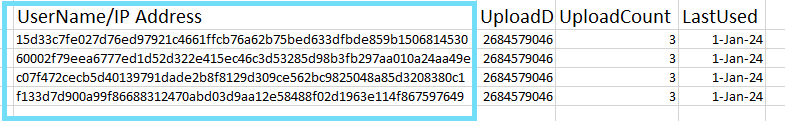
Detokenize UserNames and IP Addresses for Shadow IT Services 
Unmatched uploads list the users associated with each domain or IP address. You can now download the detokenized report of the users on the unmatched uploads. Use Detokenize Report (found under Analytics > Unmatched Uploads > Users > Detokenize Report) to view usernames or IP addresses in clear text. Restoring the original usernames or IP addresses facilitates data analysis, security, and system compliance. For details, see Detokenize Report.
NOTES:
- The supported file format for detokenizing a report is CSV.
- You must have the Detokenization Privilege to detokenize the report.
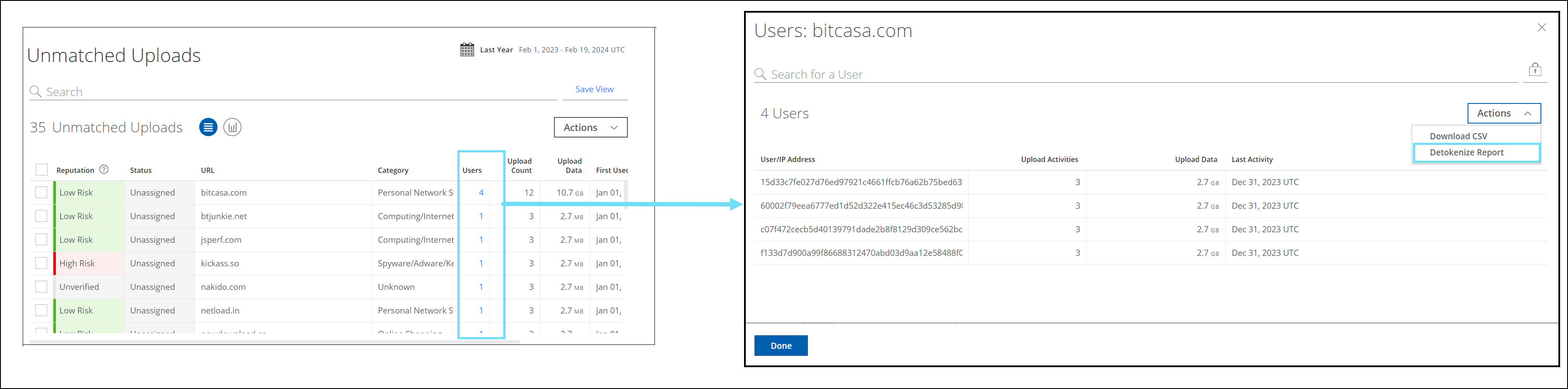
The table below represents the tokenized and detokenized reports:
| Tokenized Report | Detokenized Report |
|---|---|
|
|
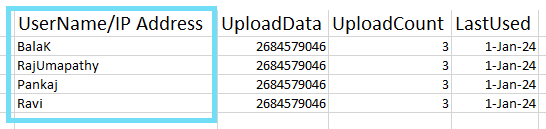 |
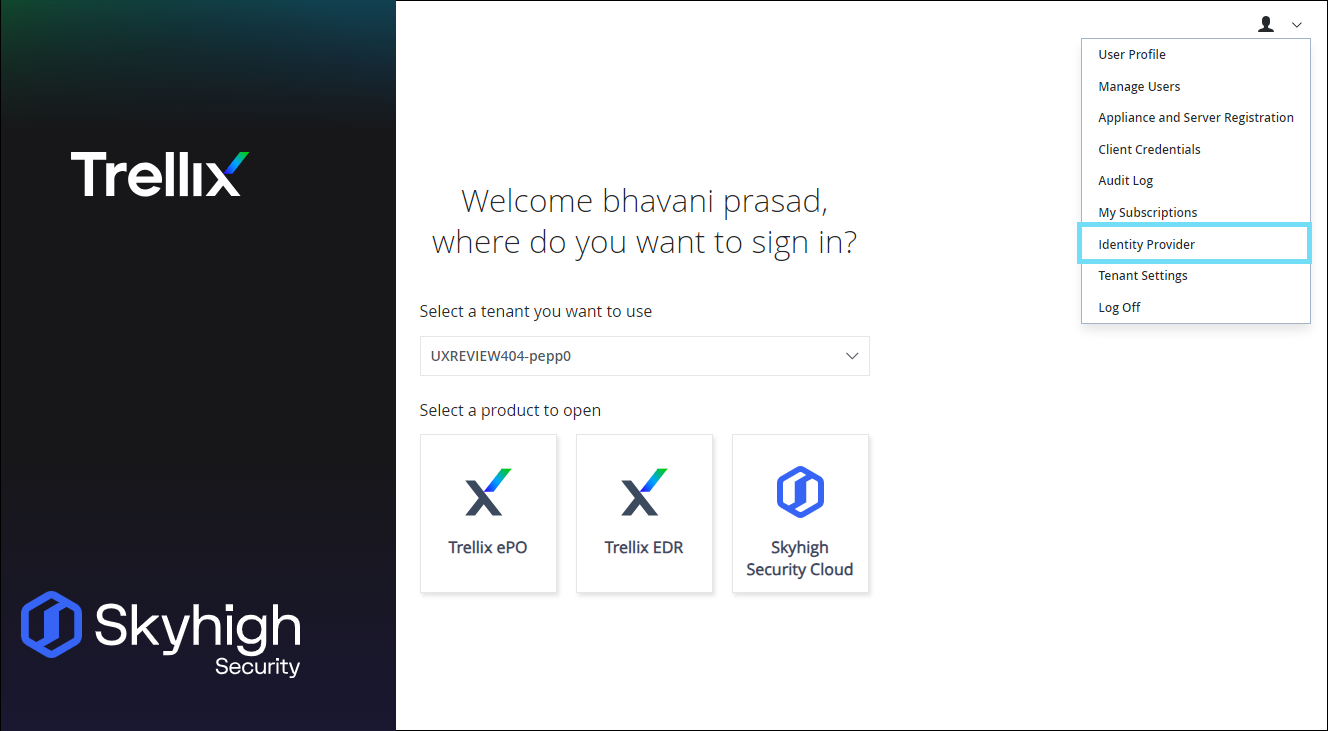
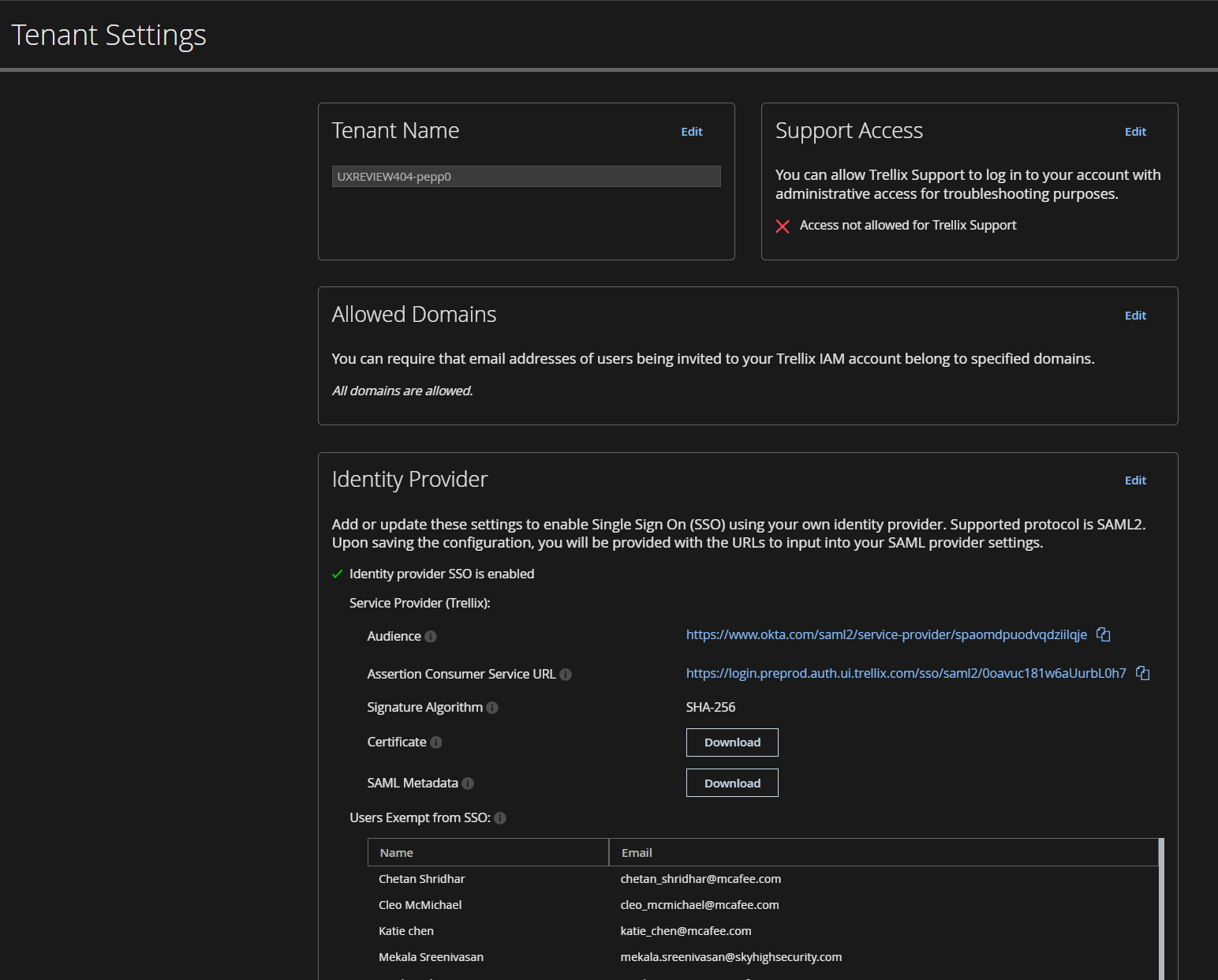
Configure SAML Only from the Trellix IDP 
Skyhigh recommends using the Trellix Identity Provider (found under the user menu on the product selection page) to enable Single Sign-On (SSO) and configure SAML (Security Assertion Markup Language). For details, see Primary User - Identity Provider.
NOTE: The Skyhigh SAML Configuration page (found under Settings > User Management > SAML Configuration) is decommissioned and this page is now in read-only mode. You cannot save any configuration settings on this page.
Refer to the table below for the availability of the pages:
| Use This: Trellix Identity Provider Page | Do Not Use This: Skyhigh SAML Configuration (Decommissioned) Page |
|---|---|
|
|
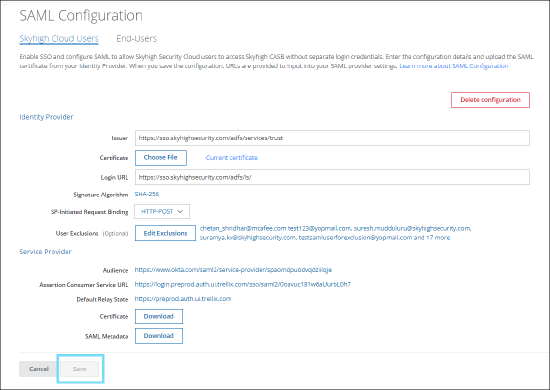 |
Enable API Integration for Unsecured Sanctioned Services 
Skyhigh CASB enables API integration for unsecured sanctioned services. This integration allows you to apply security controls such as Data Loss Prevention (DLP), Threat Protection, Activity Monitoring, and Configuration and Posture-based controls to secure your corporate data from exfiltration and ensure compliance. To enable API integration for unsecured sanctioned services, you can use the following pages:
| Page Name | Navigation Details |
|---|---|
| Services | Analytics > Services (About Services) |
| Cloud Registry | Governance > Cloud Registry (About the Cloud Registry) |
| Service Details | Analytics > Services > Service Name > Service Details (View Service Details) |
| Compare Cloud Services | Analytics > Services > Select up to four Sanctioned Services > Actions > Compare Cloud Services (Compare Cloud Services) |
For details about enabling API integration for unsecured sanctioned services, see Enable API Integration for Unsecured Sanctioned Services.
Additional Enhancements for Sanctioned Services
Skyhigh CASB now provides granular visibility into the usage of sanctioned services within your organization with these enhancements:
- Sanctioned SaaS filter (found under Services or Cloud Registry page). Identifies the sanctioned services that are supported for API integration.
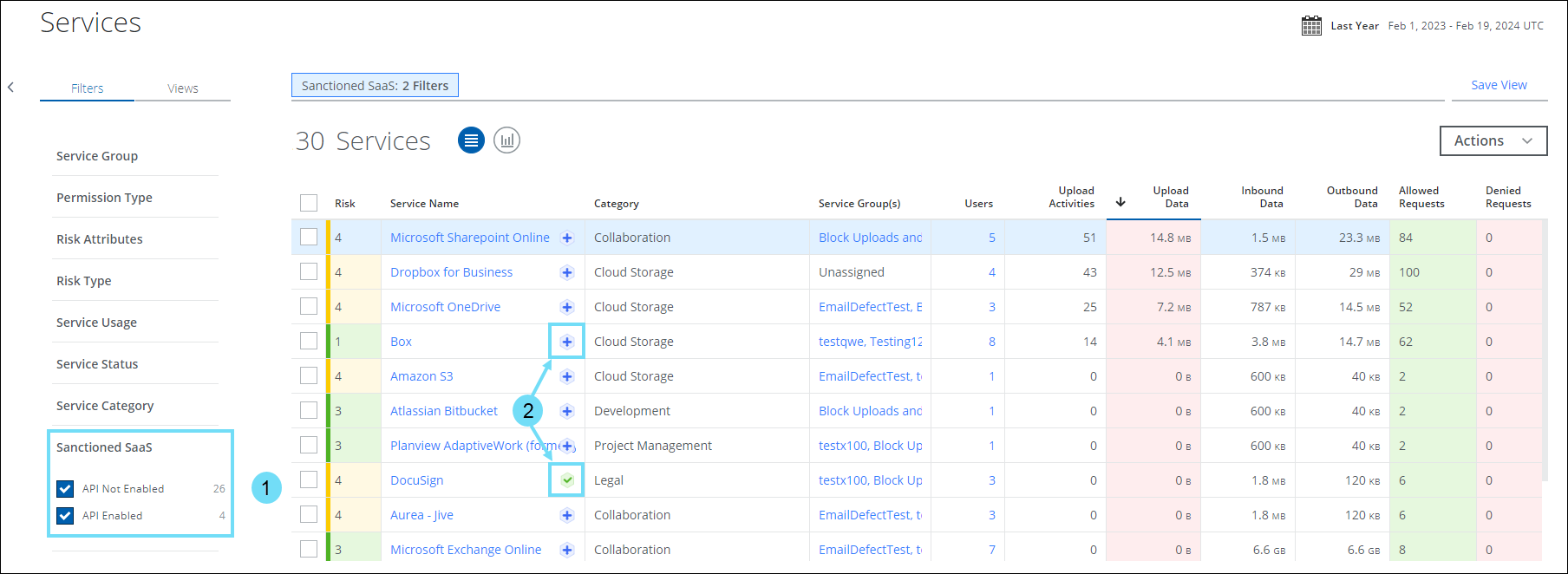
- API Status Icons. Click any of the following API status icons next to the Service Name to view the list of sanctioned services that are supported for API integration.
API Status Icon Icon Significance .png?revision=1)
API integration is not enabled for the sanctioned service. Click to enable API integration for the sanctioned service. .png?revision=1)
API integration is enabled for the sanctioned service. - Skyhigh CASB Sanctioned Apps modal. Analyze usage metrics of sanctioned services, identify sanctioned services that are secured/unsecured via API integration, and enable API integration for sanctioned services. For details, see Manage Sanctioned Services via Skyhigh CASB.
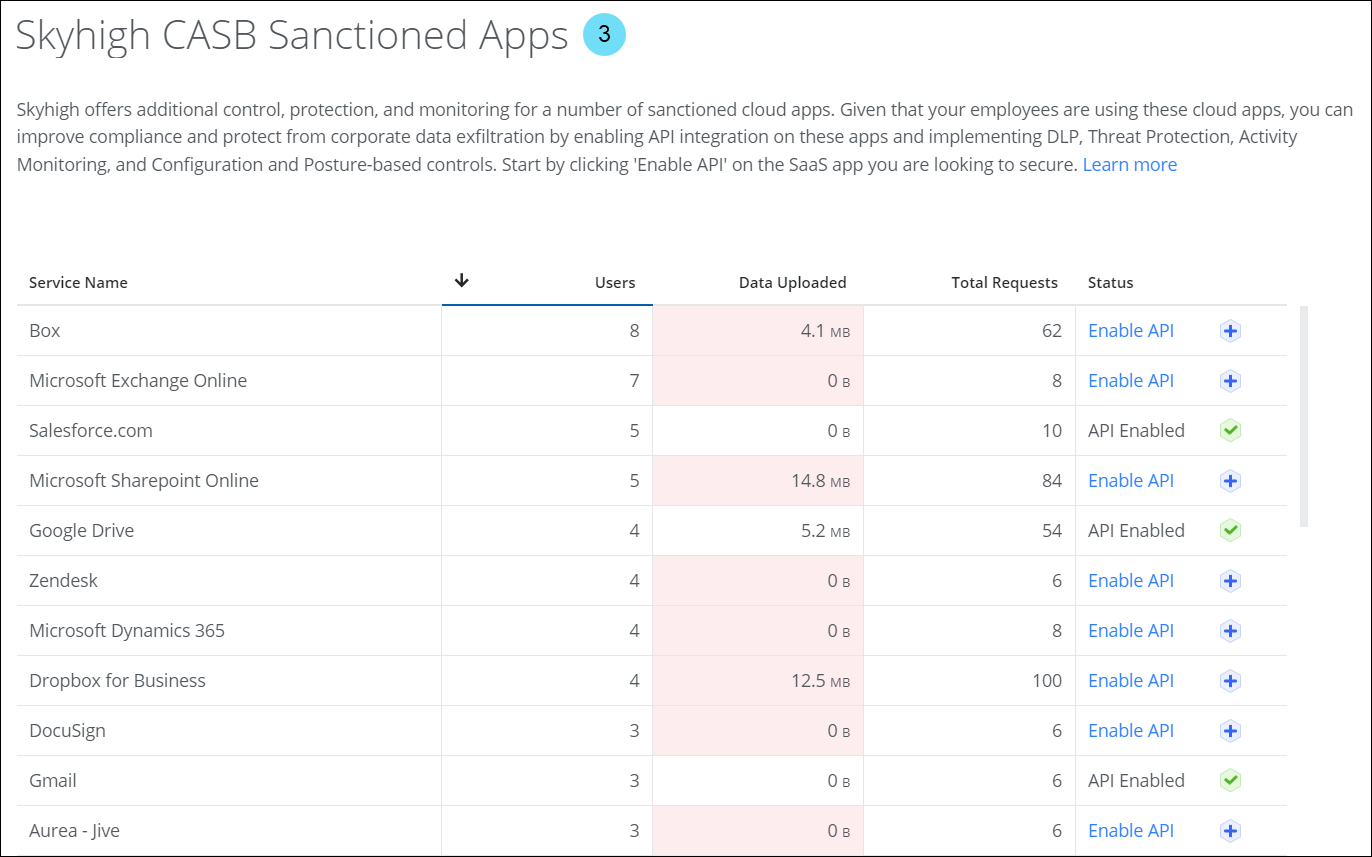
Skyhigh CASB for Procore 
Skyhigh CASB for Procore enables Security Operations Center (SOC) admins to monitor user activity across various resources in Procore, identify sensitive content, and apply Data Loss Prevention (DLP) controls on files or attachments uploaded to Procore. For details, see About CASB Connect for Procore.

Resolved and Known Issues
 Click here to view Resolved and Known Issues
Click here to view Resolved and Known Issues- For details, see Skyhigh Security Cloud Bug Fixes and Known Issues.