Integrate GCP with Skyhigh CASB
To integrate GCP with Skyhigh CASB, add a service instance in Skyhigh CASB, then add a service account in GCP, then enable APIs and Services for a Config Audit scan.
Add a GCP Service Instance in Skyhigh CASB
To integrate GCP with Skyhigh CASB, perform the following steps
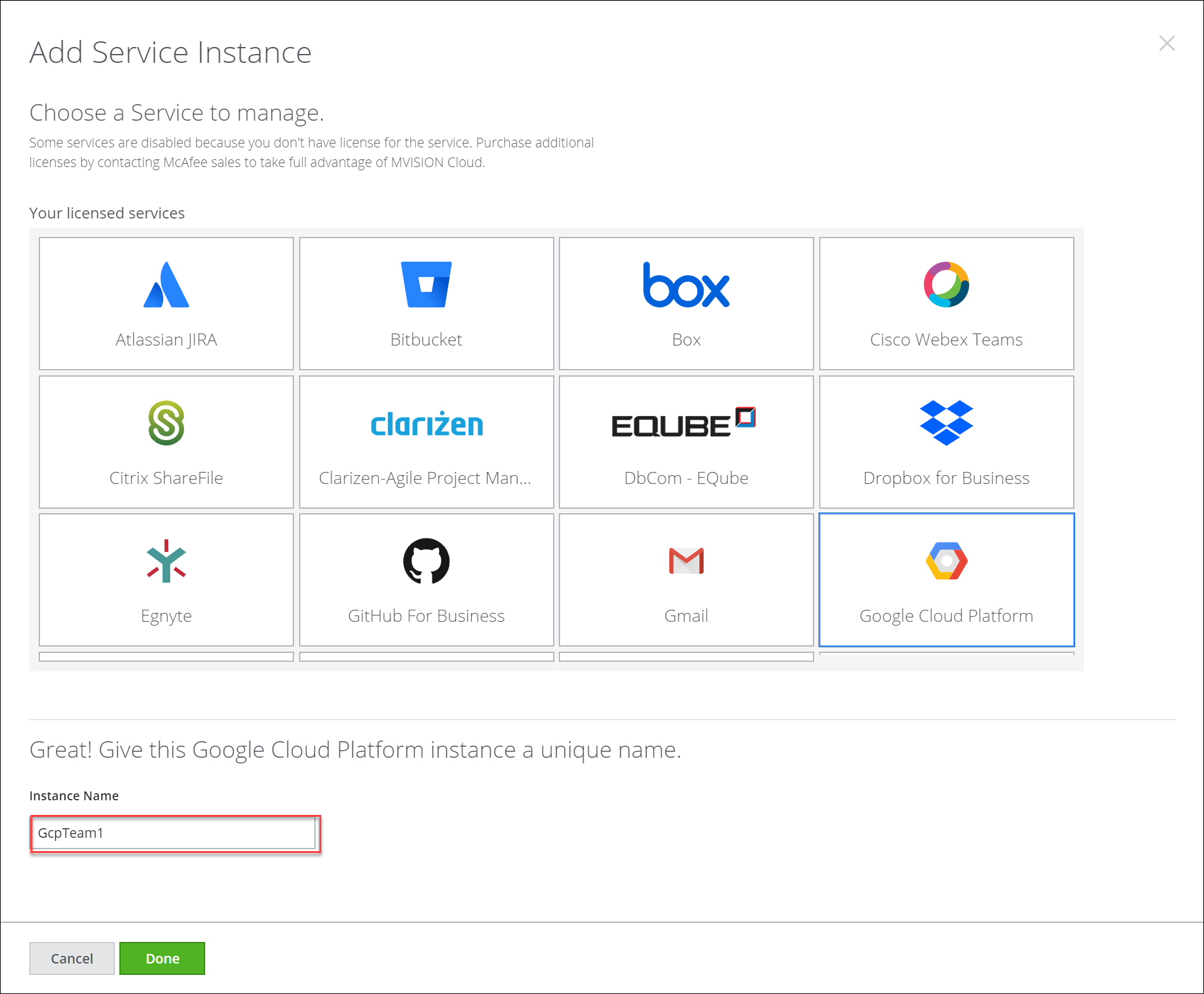
- In Skyhigh CASB go to Settings > Service Management.
- Click Add Service Instance.
- Select Google Cloud Platform, enter an Instance Name, and click Done.
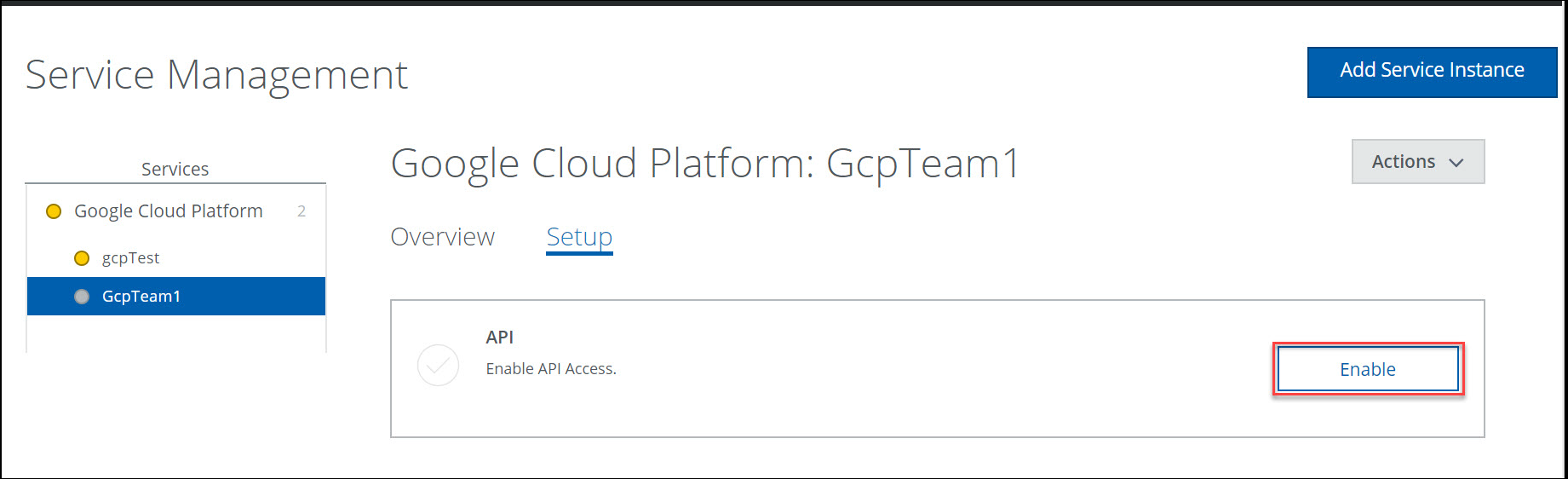
- Under Setup, for API, click Enable.
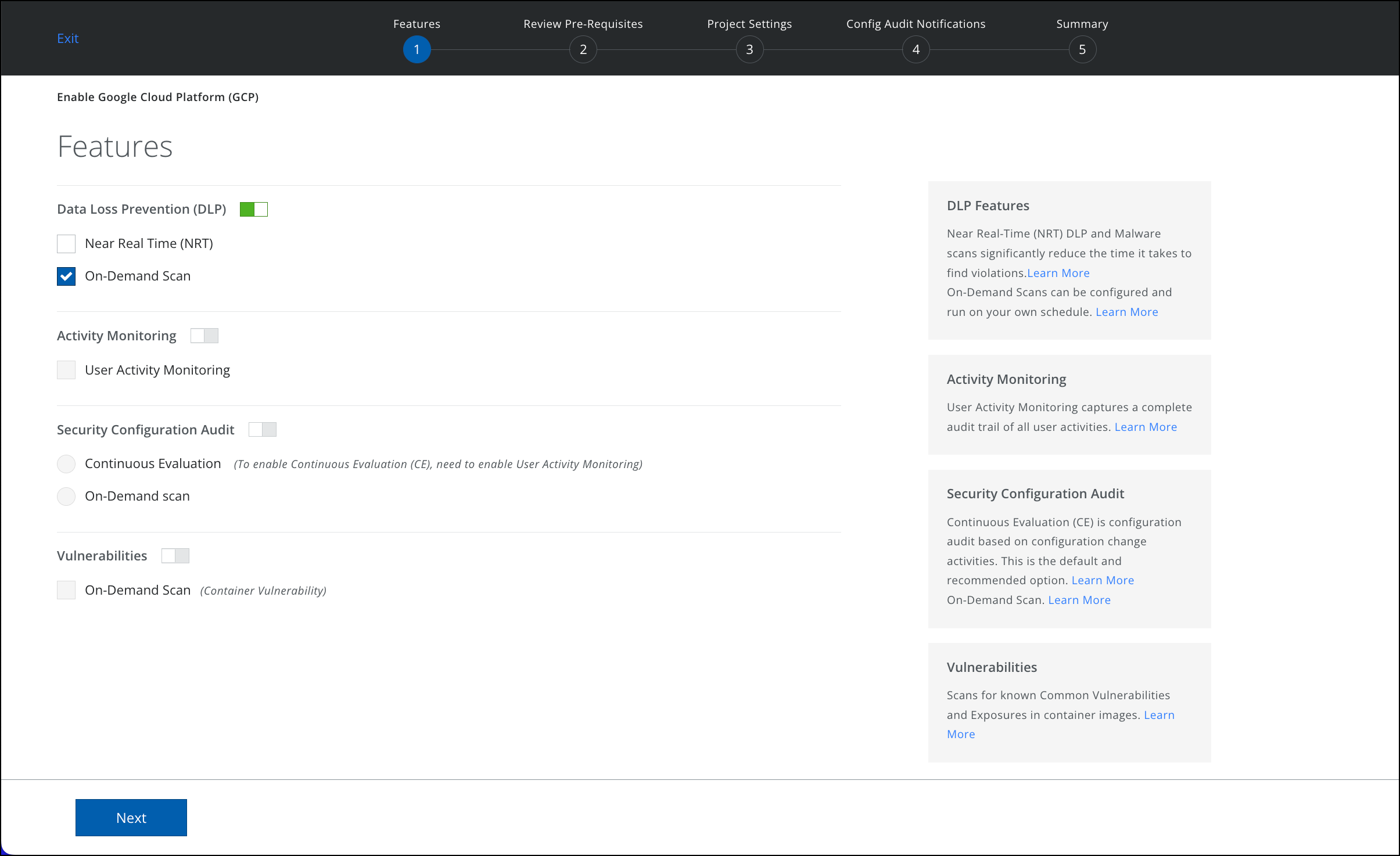
- Select the features you want to enable for your GCP account.
- DLP. Use On-Demand Scans to examine cloud services for content that violates your policies and support targeted investigations. Enable an On-Demand Scan to run your scan immediately or set the scan schedule to daily or weekly.
- Activity Monitoring. Activity Monitoring allows forensic auditing and investigation of individual activities.
- Security Configuration Audit. Security Configuration Audit allows your policy team to monitor and discover if your cloud services have been configured per industry best practices.
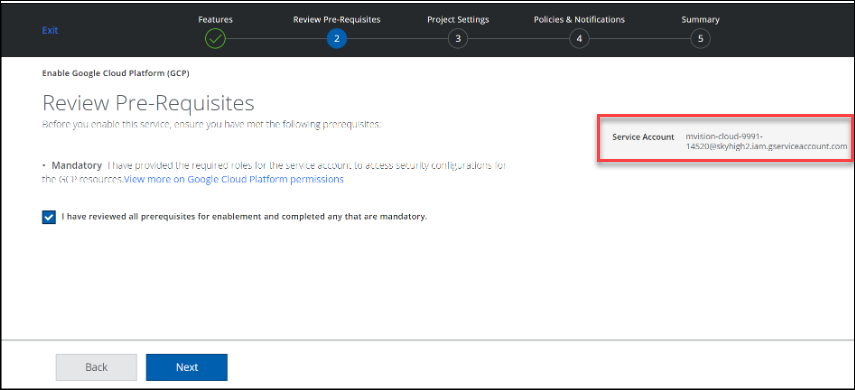
- Review prerequisites, copy the Service Account as shown in the following screenshot, and click Next.
- Add the Service Account to the GCP project in your GCP console. This is needed to allow Skyhigh CASB to access your GCP resources. To do this, refer Add a Service Account in GCP.
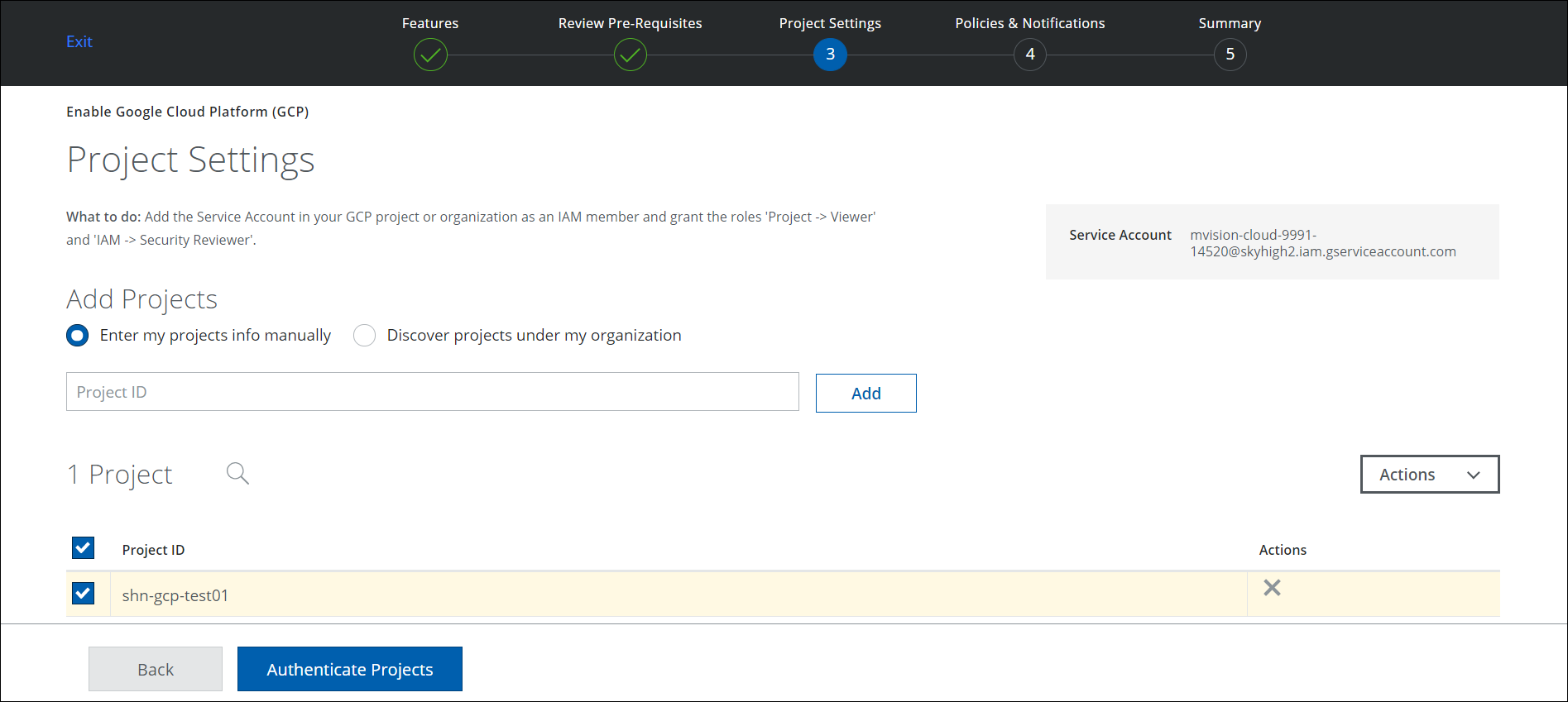
- Under Project Settings, add projects using one of two options:
- Enter my projects info manually. Enter the Project ID of an existing project.
- Discover projects under my organization. Select a project from the list of available projects under your organization, and click Authenticate Projects.
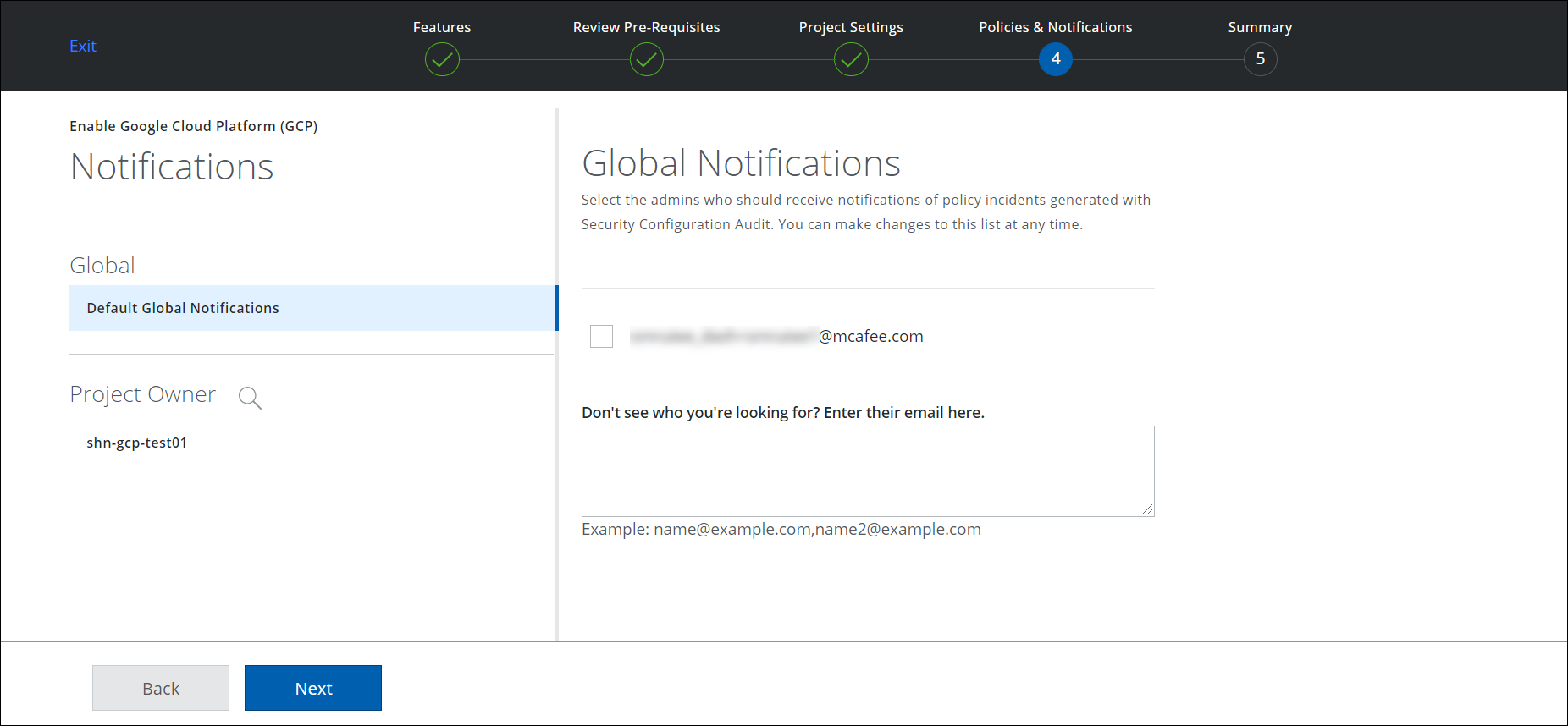
- Select an admin from the generated list, or enter an email to search for a specific person. Click Next.
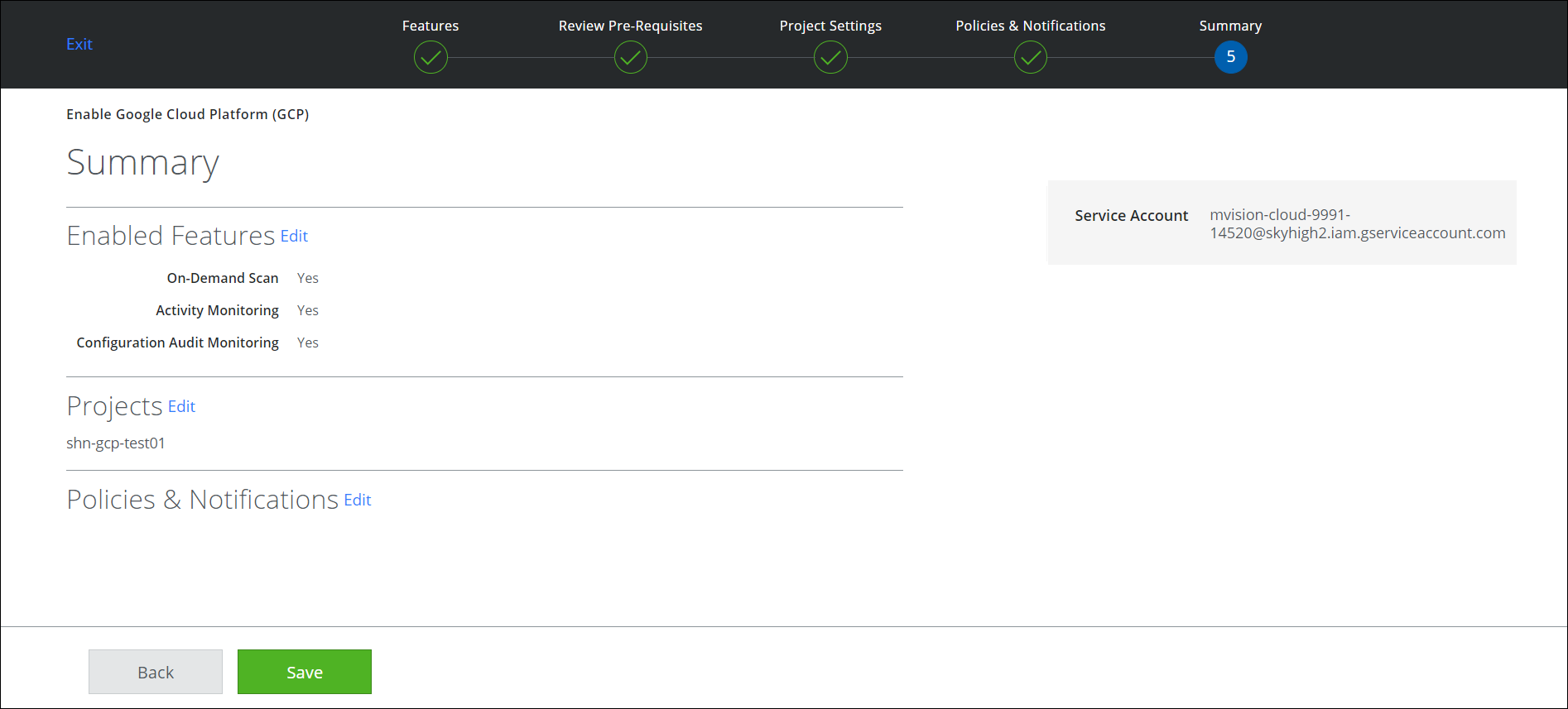
- In the Summary page, verify your settings and click Save.
Once authenticated, the API is enabled and the Instance setup is complete.
Add a Service Account in GCP
You need a Service Account to allow Skyhigh CASB to access your GCP resources. To do this, use the Service Account to your GCP project (or organization) as an IAM member, and grant the following roles:
- Project > Viewer
- IAM > Security Reviewer
- Service Usage > Service Usage Consumer. This role is required to fetch GCP activities using your organization's API quota. To avoid issues with API rate limiting by GCP while using Skyhigh Security's project, Skyhigh CASB now uses your organization's API quota to fetch the activities.
- Custom role with 'container.nodes.proxy' permission. This role is required only for GKE policies. Or, you can also use predefined roles like Kubernetes Engine Developer or Kubernetes Engine Admin.
- Custom role with 'Storage Legacy Bucket Writer' permission. This role is required if you want to Quarantine files as part of DLP or Malware On Demand Scans.
To add a service account, perform the following steps:
- In the GCP console, go to the IAM page.
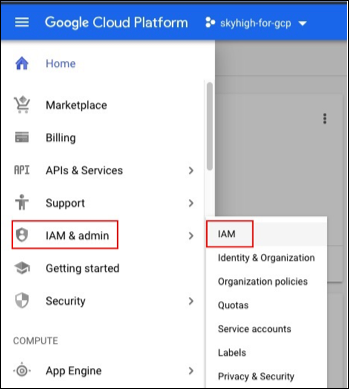
- Click Add.

- Add the roles.
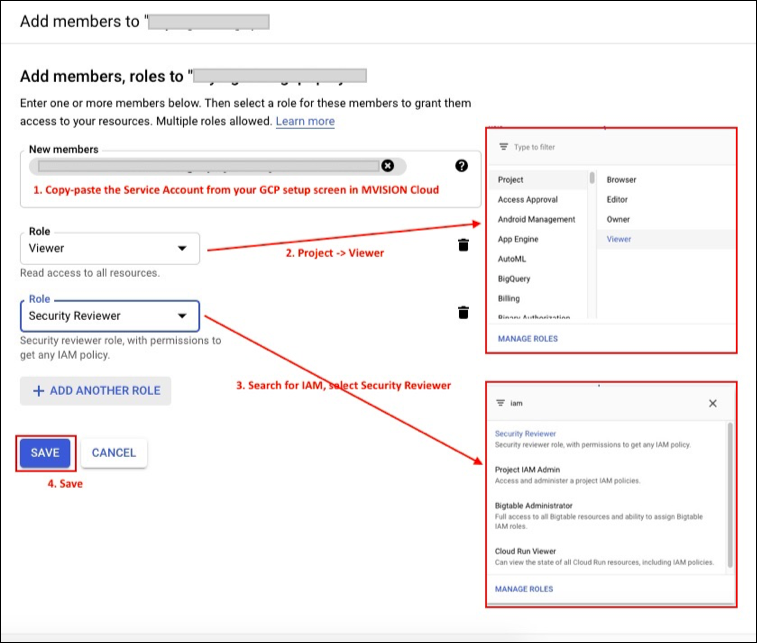
- Click Save.
NOTE: If you have domain restrictions, update your organization's policy to allow Skyhigh CASB. See the GCP article on how to set an organization policy. Set the following organization ID in the allowed_values list. Org ID: C02e0hze1
Enable APIs and Services for a Config Audit Scan
Enable the GCP APIs and services for the active Configuration Audit policies before you run the scan.
See the supported resource types to discover the corresponding APIs and services, which depend on the policies you enable. For example, when you enable a Configuration Audit policy that includes checks for the Key Management Service in GCP, make sure you enable the Key Management Services and API.
When you create custom Config Audit policies, you might have to enable other APIs and services in GCP to allow Skyhigh CASB to scan the configuration of the relevant resources.
Some required APIs and services for several policies from the policy template list for GCP are:
- Compute Engine API
- Cloud Storage
- Cloud DNS API
- Cloud Key Management Service (KMS) API
- Cloud Logging API - This is required for activity monitoring too.
Granular Permissions for a GCP Config Audit Scan
Create a custom role with the following permissions to run the Config Audit scan for GCP.
Basic Permissions to run GCP Config Audit scan
Provide the following permissions if you want to run Config Audit scan for GCP.
- resourcemanager.projects.get
- storage.buckets.get
- storage.buckets.getIamPolicy
- storage.buckets.list
- storage.objects.get
- storage.objects.getIamPolicy
- storage.objects.list
Granular Permissions for a DLP Scan
Create a custom role with the following permissions to run the DLP scan for GCP.
Basic Permissions to run DLP scan
Provide the following permissions if you want to run a DLP scan without quarantine as a response action.
- accessapproval.requests.get
- accessapproval.requests.list
- accessapproval.settings.get
- monitoring.timeSeries.list
- resourcemanager.projects.get
- storage.buckets.get
- storage.buckets.list
- storage.objects.get
- storage.objects.list
- pubsub.topics.list
- pubsub.subscriptions.list
Additional Permissions to run a DLP scan
In addition to the basic permissions, provide following permissions to support quarantine as a response action.
- storage.buckets.create
- storage.buckets.setIamPolicy
- storage.objects.delete
- storage.objects.update
- storage.objects.create
NOTE: These permissions are also valid when the cloud storage buckets are encrypted using Customer-Managed Key (Generated).
