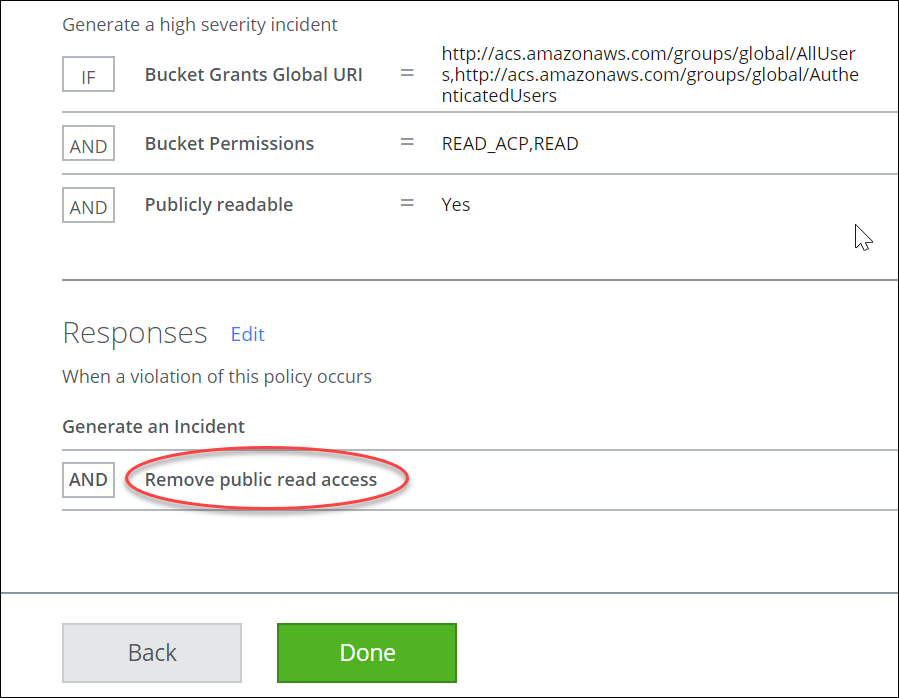
Auto-Remediate AWS Incidents
Auto-remediation is a triggered response to a policy violation, and it applies to AWS issues. Auto-remediation is an automated approach to security, applying the appropriate response to a vulnerability in your S3 deployment. It ensures a high level of functionality by continuously monitoring risks and it automates issue remediation. When a policy violation occurs, this instant remediation reduces the window of malicious opportunity.
NOTE: Skyhigh CASB requires write/update permissions in AWS to implement Auto-remediation.
Supported Remediation Actions
These are the supported remediation actions for AWS.
|
Remediation Actions |
Policy Templates |
Permissions Required |
|---|---|---|
|
Email Notification |
|
|
|
Enable AES 256 Encryption |
|
|
|
Remove Public Permissions
|
|
|
|
Remove Public Read Access |
World Readable S3 Buckets |
|
|
Remove Unrestricted Access
|
|
|
|
Scan Unsecured Resources
|
|
|
| Send to SNS Topic | All AWS policy templates |
|
| Send to SQS Queue | All AWS policy templates |
|
Setting up Auto-Remediation
Auto-Remediation can be added to any AWS policy. Changes are not applied retroactively.
To add an auto-remediation response:
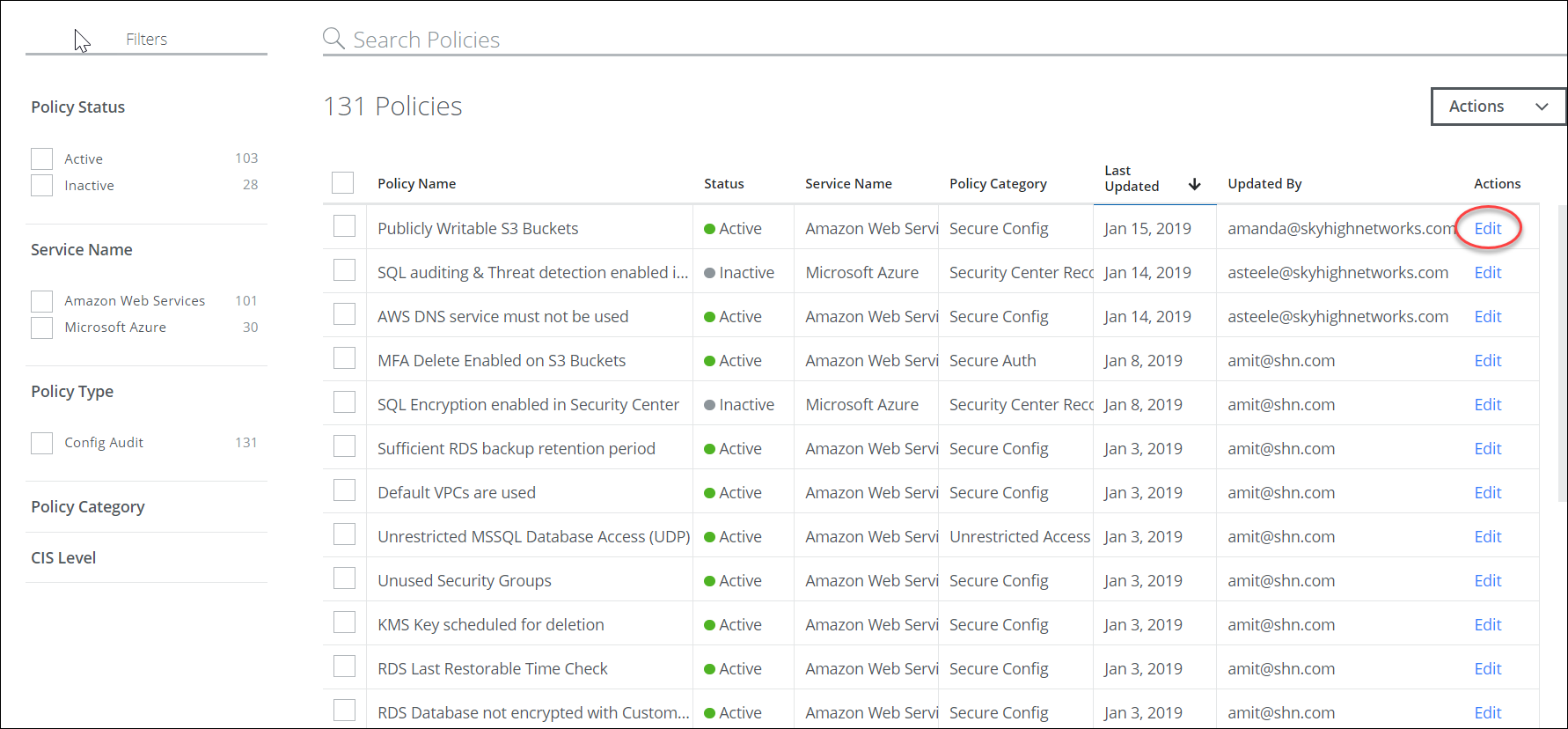
- Choose Policy > Configuration Audit.
- Choose Edit from the affected policy. It is under the Actions column to the right of the policy you'd like to customize.
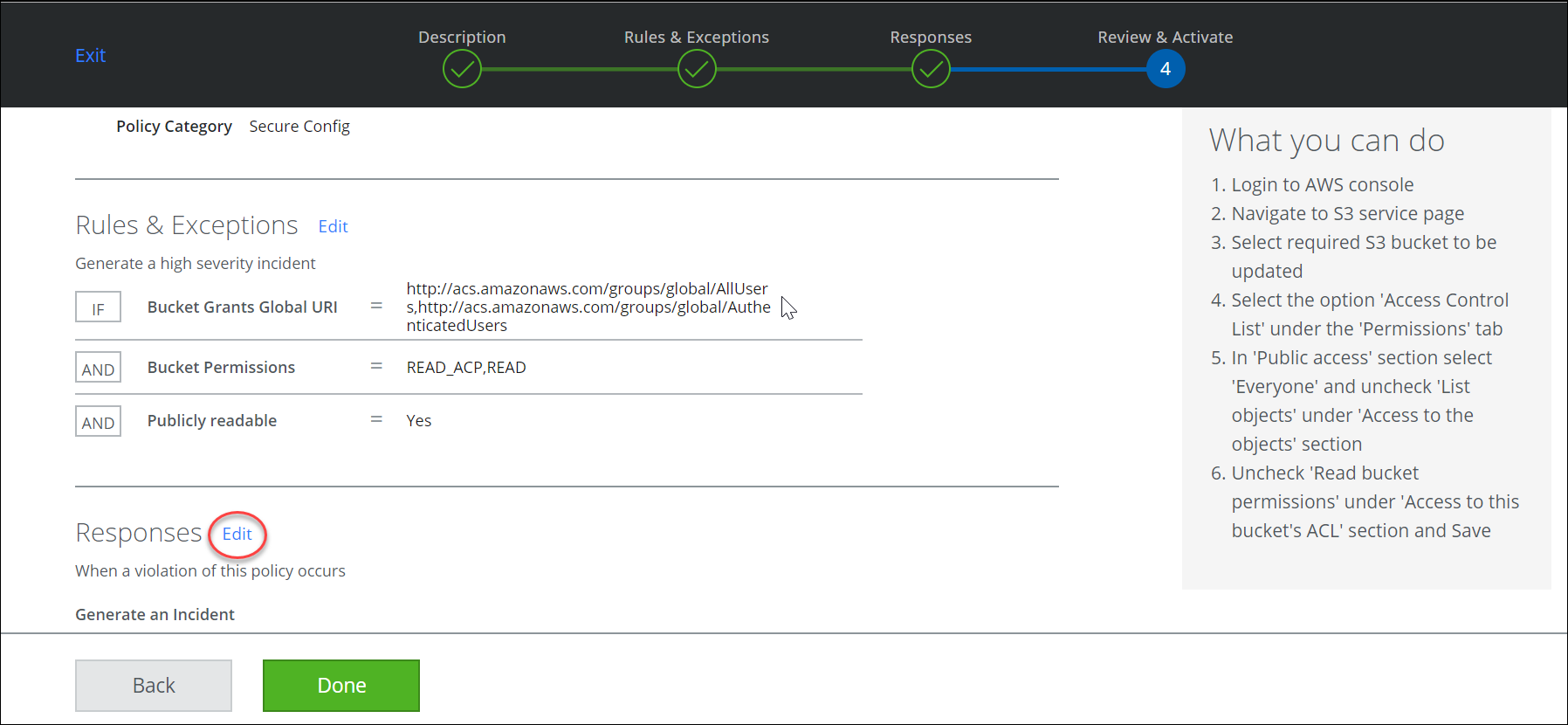
- From the Responses section, select Edit.
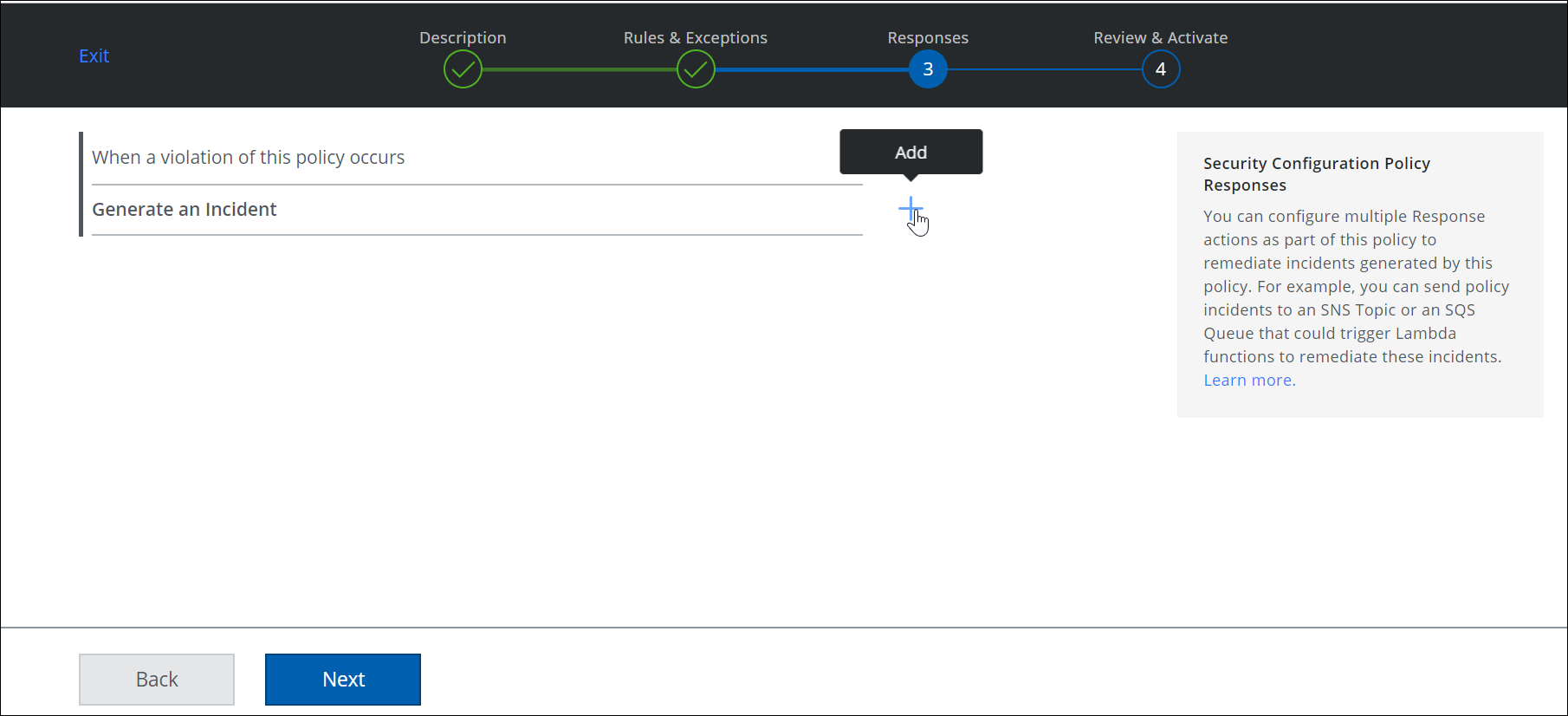
- The following screen will appear. Select Add then press the Next button.
- Select the response from the drop-down list then select Next.
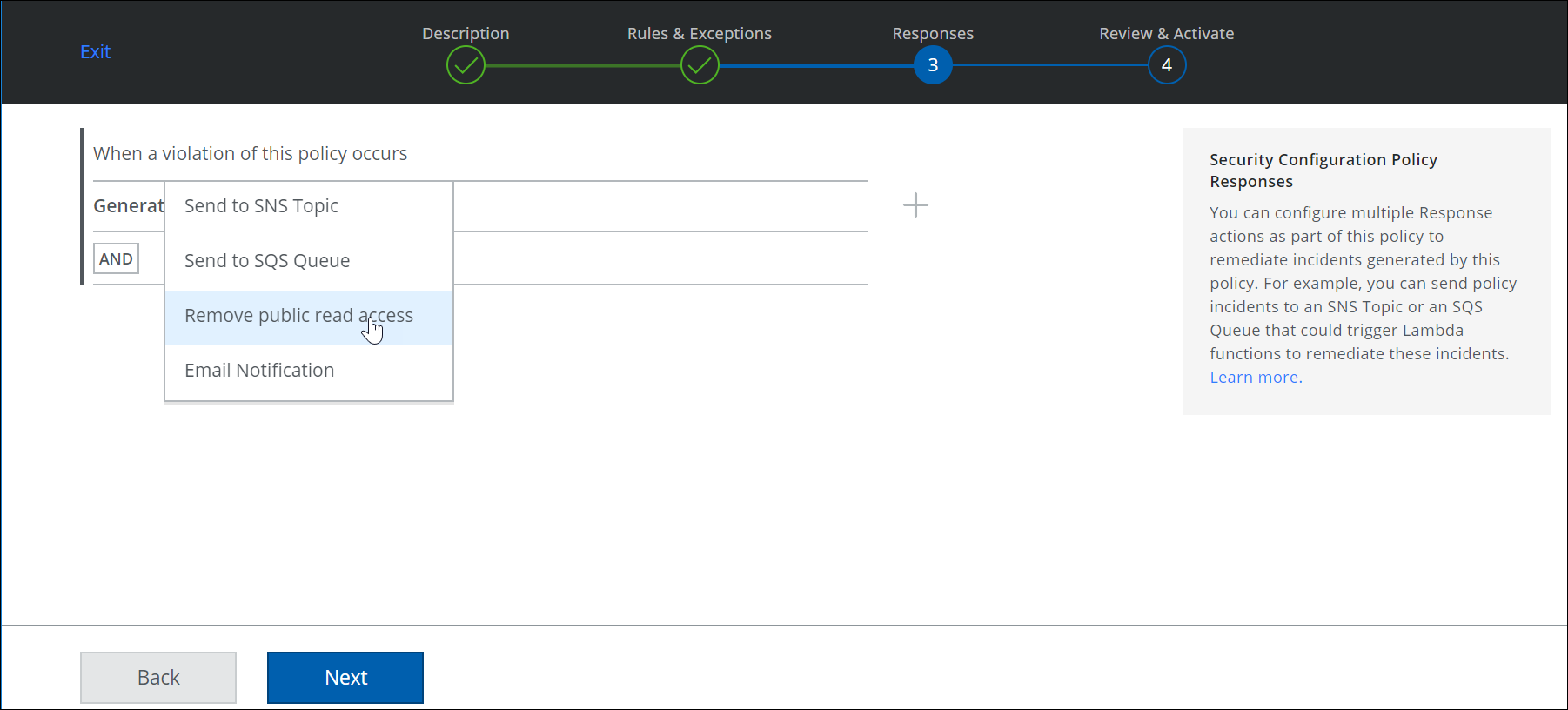
- Verify that your desired response is shown in the Response section then select Done.