Create a Security Configuration Audit Policy
There are two ways to create a policy for Security Configuration: you can create a policy from a template, or you can create a policy using the Configuration Audit Policy Builder.
Create a Policy from a Policy Template
To use preconfigured Configuration Audit Policy Template:
- Go to Policy > Policy Templates.
- Filter for Policy Type > Security Configuration.
- Filter for Service Applicable to and select your service. Then select the policies you want to import into your instance.
- Click Create Policy.
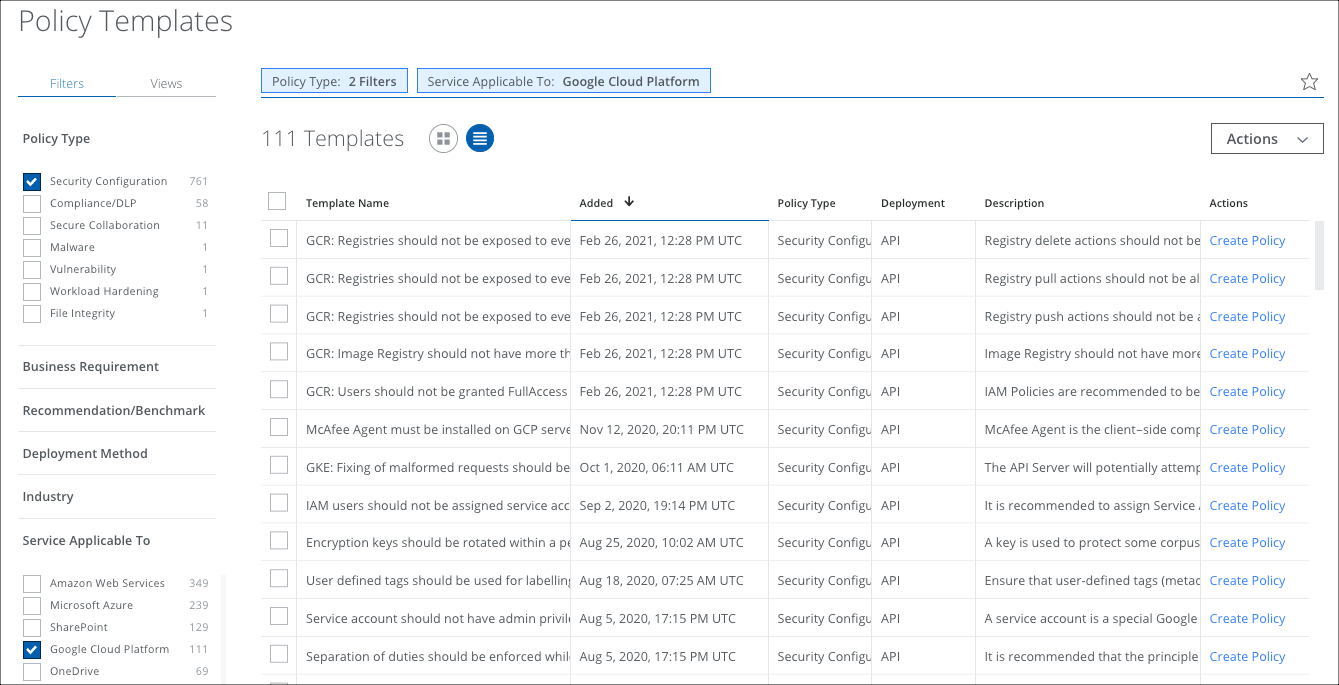
- The new policies display on the Policy > Configuration Audit page.
- Edit the policy as needed for your implementation.
Create a Policy using the Policy Builder
Use the Configuration Audit Policy Builder to create custom Security Configuration Audit policies to meet your organization's requirements. It supports policies for AWS, Azure, and GCP and provides compliance against industry standards such as CIS, PCI, HIPAA, and NIST 800-53.
The Policy Builder supports conditions as exceptions to the policy. It also allows you to test the policy and see sample results before you save it.
For information about policy builder syntax, errors, supported resource types, operators, and value types see Security Configuration Audit Policy Syntax.
To create a Security Configuration Audit Policy:
- Go to Policy > Configuration Audit.
- Click Actions > Create Policy.
- The policy builder wizard opens. On the Description page, configure the following fields:
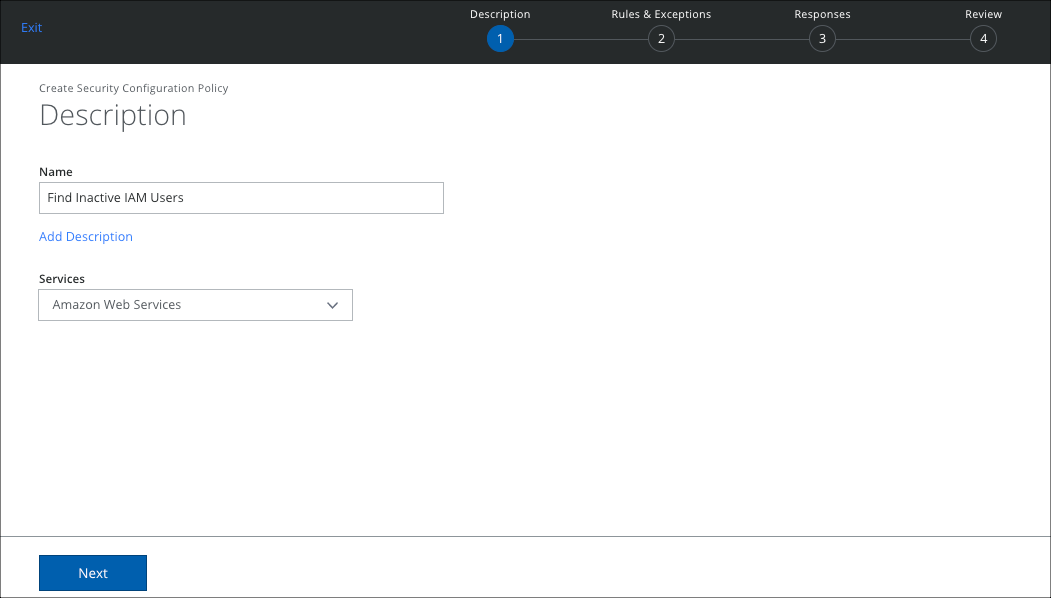
- Name. Enter a unique name for the policy.
- Description. Enter an optional description for the policy.
- Services. Select the service you want the policy to apply to.
- Click Next.
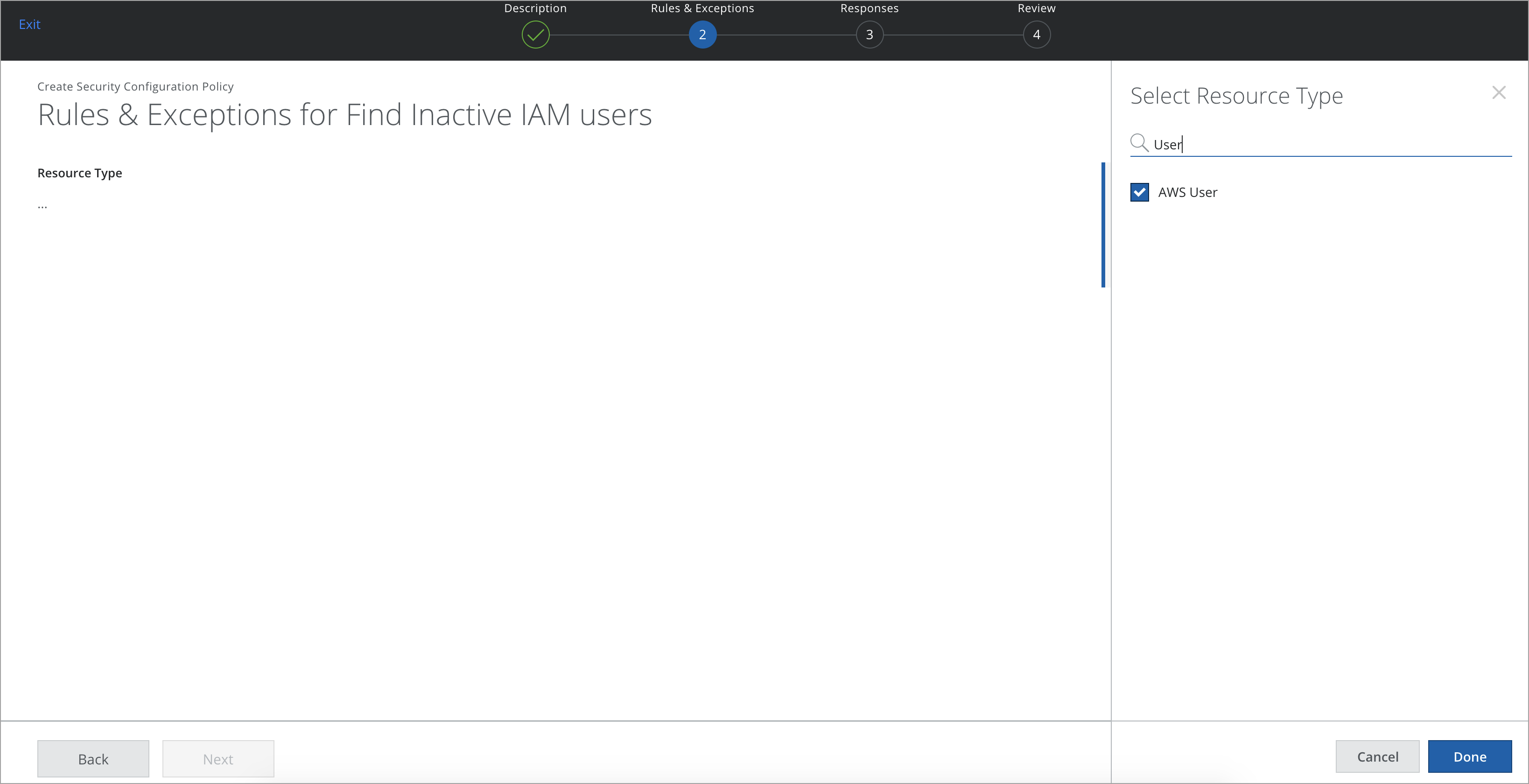
- Select one or more Resource Types.
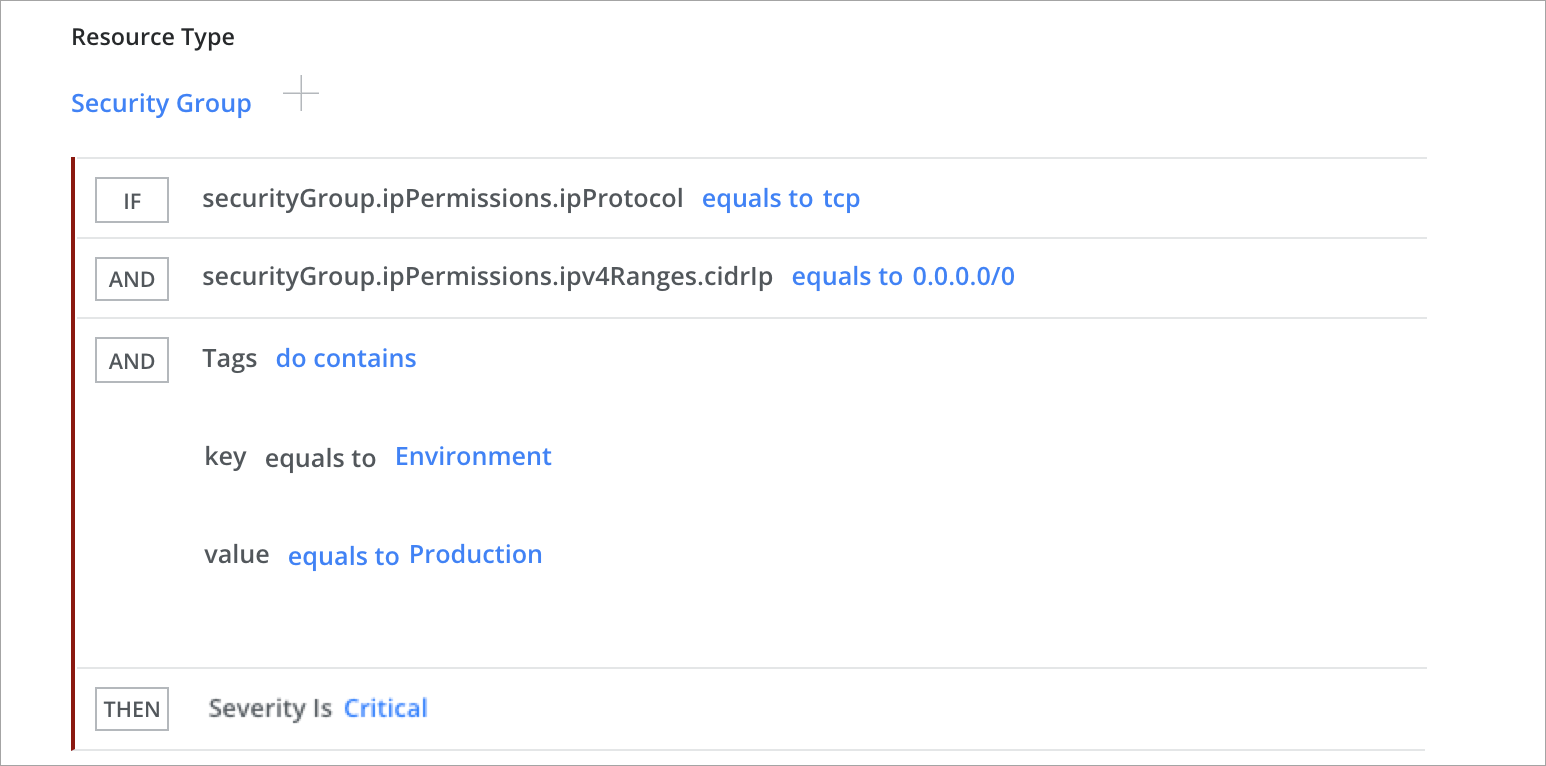
- IF. Add Policy Rules based on your requirements. Click + to add more and choose AND/OR
- Attribute values are auto-populated wherever applicable. If the value you want to provide is not there in the auto-populated list, you can still manually add them. To add a value, enter it in the search bar and click enter.
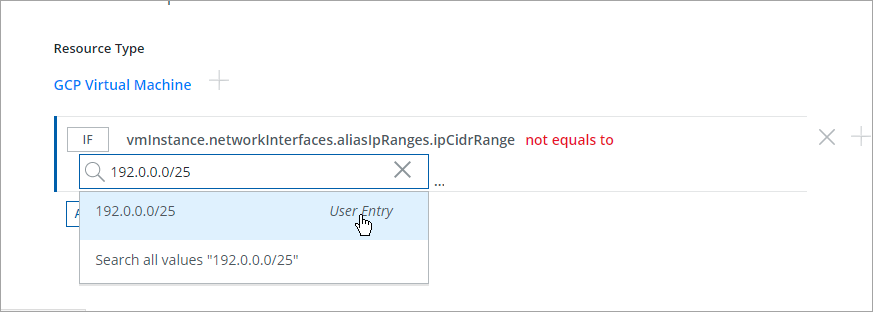
- Attribute values are auto-populated wherever applicable. If the value you want to provide is not there in the auto-populated list, you can still manually add them. To add a value, enter it in the search bar and click enter.
- THEN. Select a Severity, either Critical, Major, Minor, Warning, and Info.
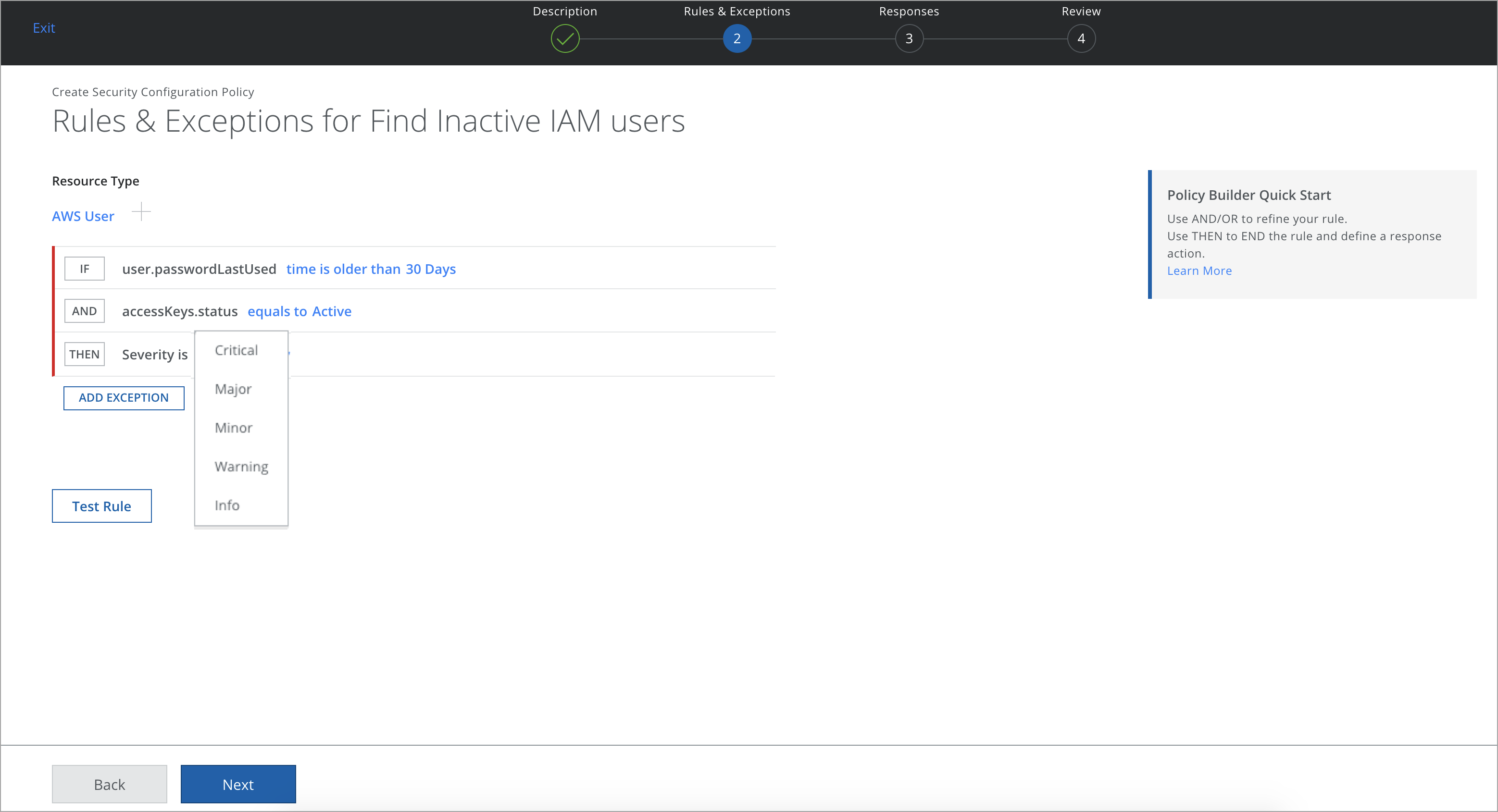
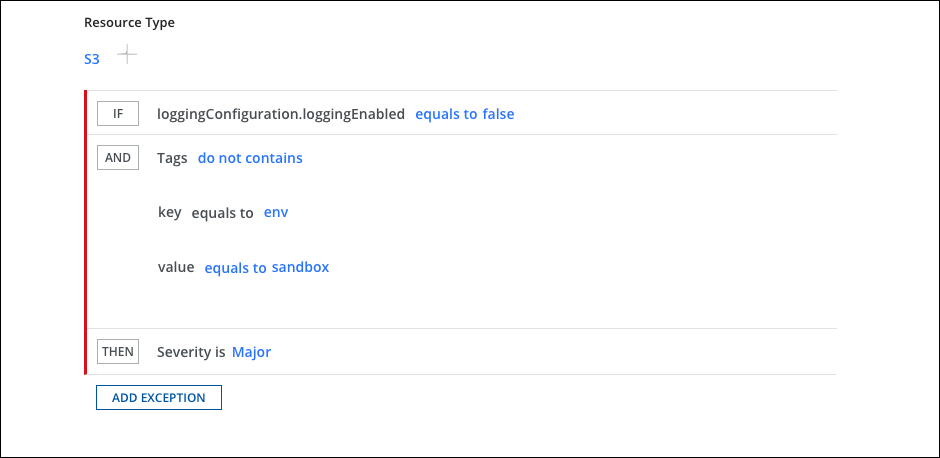
- ADD AN EXCEPTION. If you do not want to apply rules on some accounts, or you want to skip the policy evaluation for a specific resource instance based on some conditions, you can add a negation condition within your IF section. For example, you may want to exclude resources that are tagged with env as sandbox. Click + to add more.
NOTE: You can also specify the exclusions via optional exceptions, but this is not recommended as a best practice.
- Click Test Rule. This tests your policy and reports the total number of resources that are violating the policy. It also returns a maximum of 50 records as a sample result and displays and more if there are additional records which are not processed.
.png?revision=1&size=bestfit&width=955&height=424)
- Click Next.
- Responses. Add a Response Action to your policy, and then click Done. Select one or more responses that are triggered when the policy rules are matched:
- Create Incident
- Email Notification | Notify administrators
- Incident Owner
By default, all Security Configuration policies create an incident.

- Select users, and then click Done. Selected users will be notified when the policy generates an incident.

- Select the Incident Owner, and then click Next.

- Review your policy, and then click Save. By default, the policy is made active.

NOTES:
- Support for creating compliance policies against new services/ resource types added by vendors can be added dynamically by Skyhigh CASB in 2 weeks. This allows you to create custom policies for your organization's requirements.
- The Skyhigh CASB Configuration Audit Policy Builder now supports AWS-Managed IAM Policy and collects specific AWS-Managed Policies’ data to create custom policies. For custom policies, provide policy ARNs for the specific IAM policies. For example, if you have AmazonGuardDutyServiceRolePolicy as the AWS-Managed IAM policy, provide ARN as shown in the following format:
arn:aws:iam::aws:policy/aws-service-role/AmazonGuardDutyServiceRolePolicy
- Currently, we are collecting data only for AmazonGuardDutyServiceRolePolicy. To support more AWS-Managed IAM Policy, contact Skyhigh Security Support.
Sample Policies
For information about policy builder syntax, supported resource types, operators, and value types see Security Configuration Audit Policy Syntax.
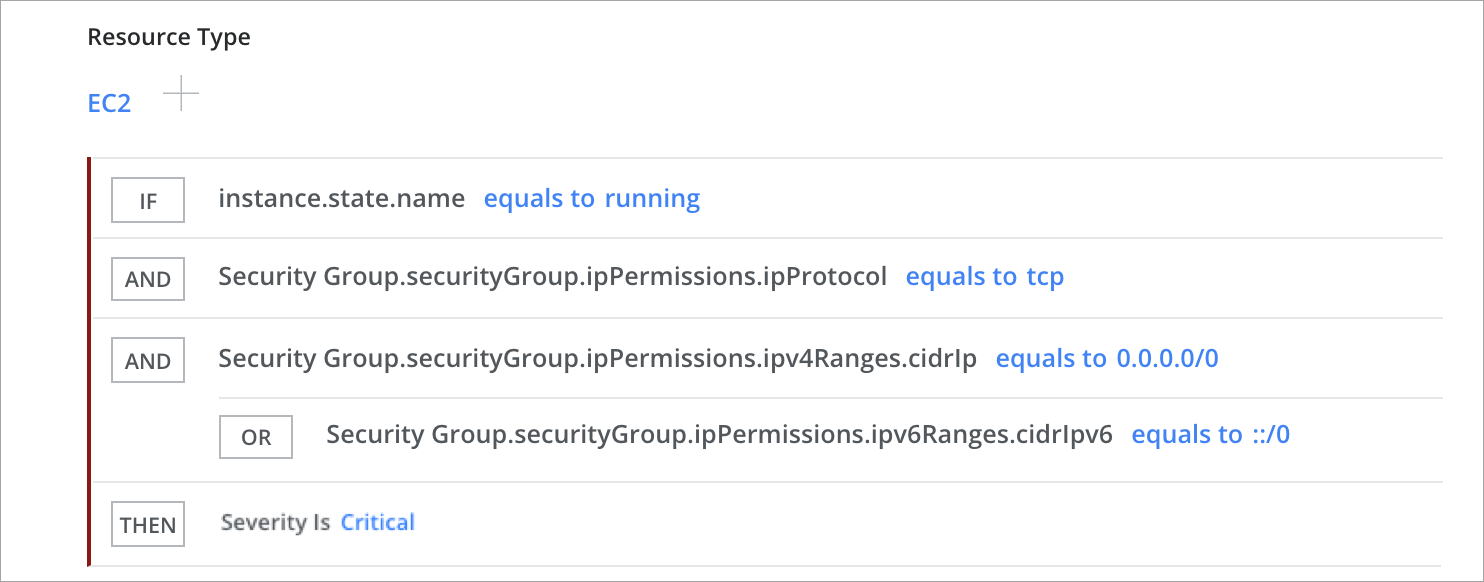
List EC2 Instances with Unrestricted TCP Access
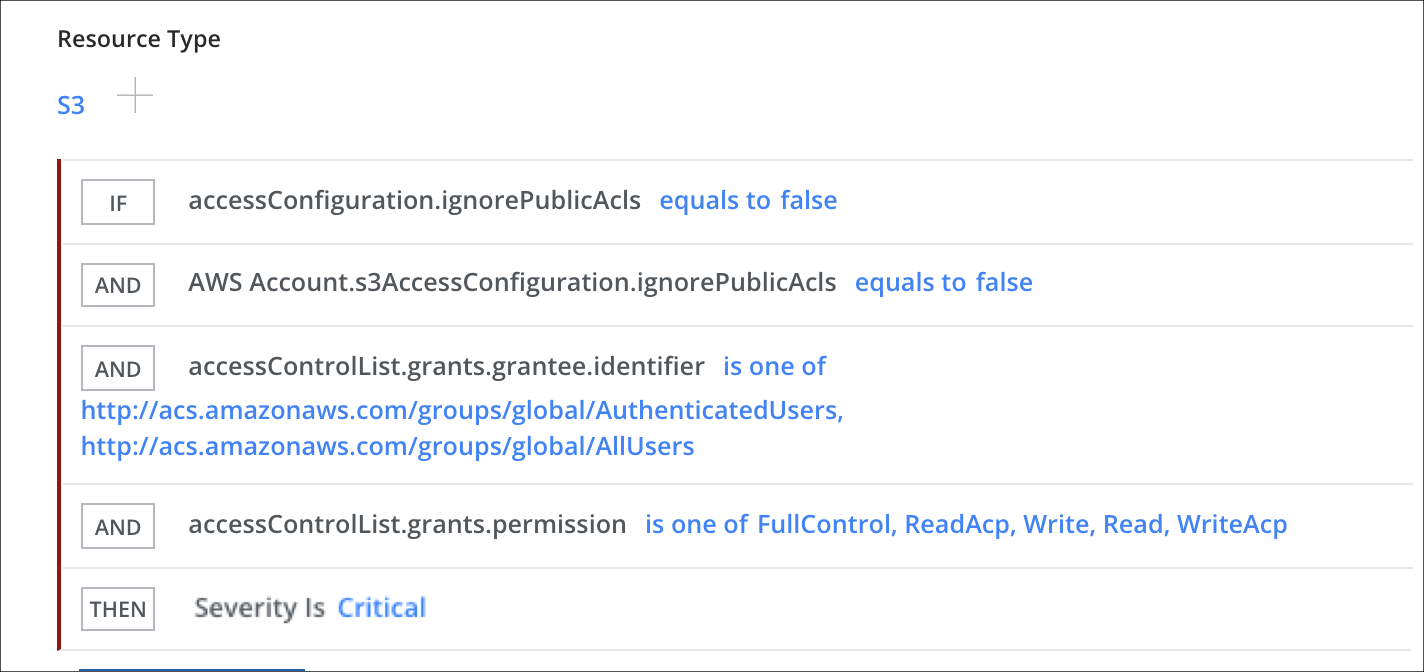
Publicly accessible S3 Buckets
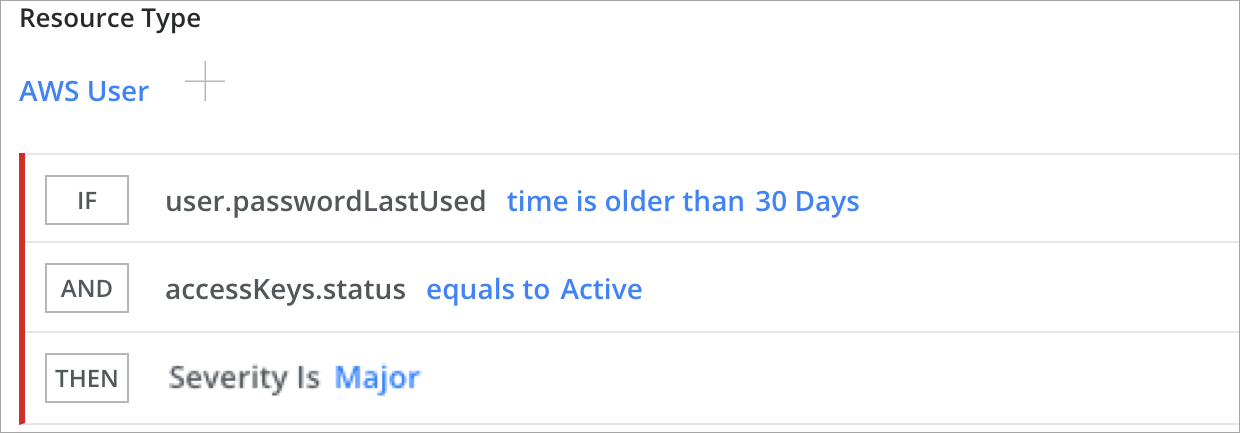
Find Inactive IAM Users
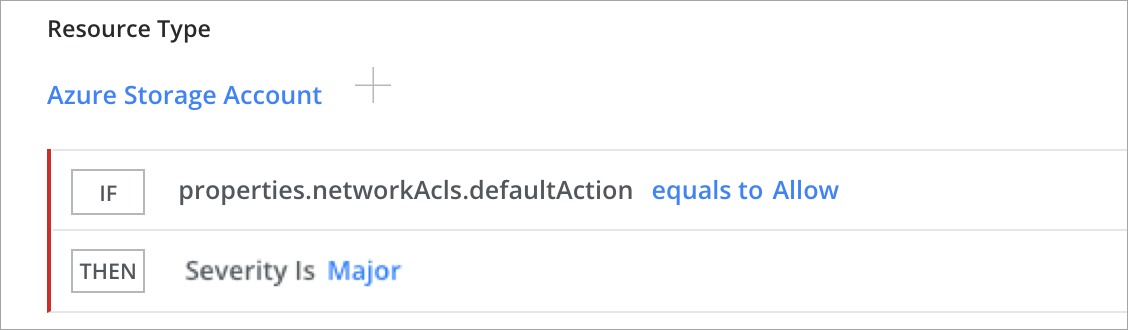
Storage Accounts with Unrestricted Access to Azure Activity Logs
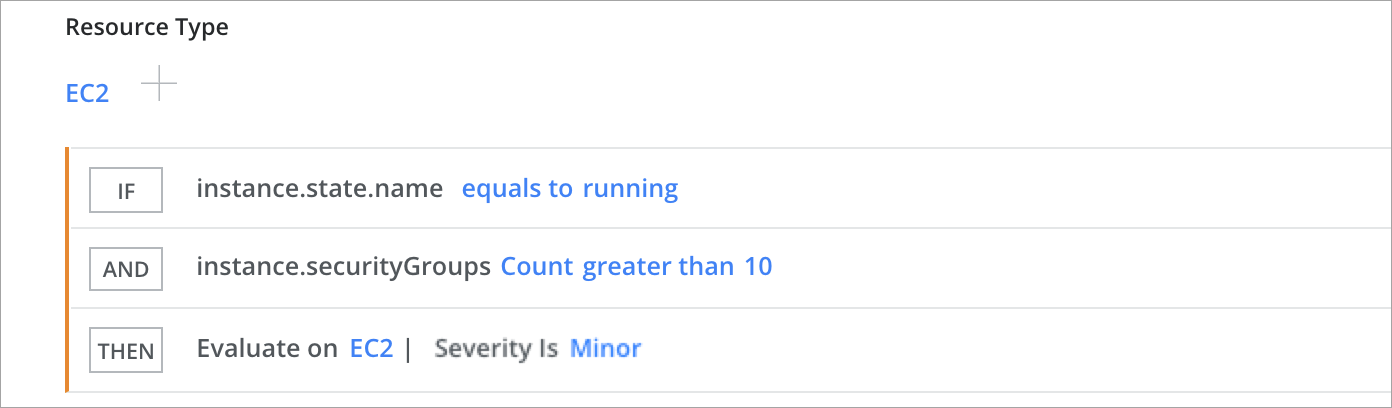
EC2 Instances with More Than 10 Security Groups Attached
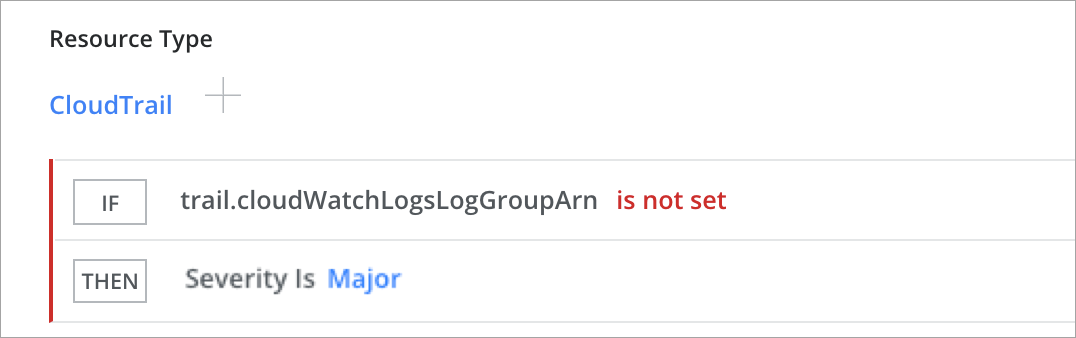
CloudTrail Trails not Integrated with CloudWatch Logs
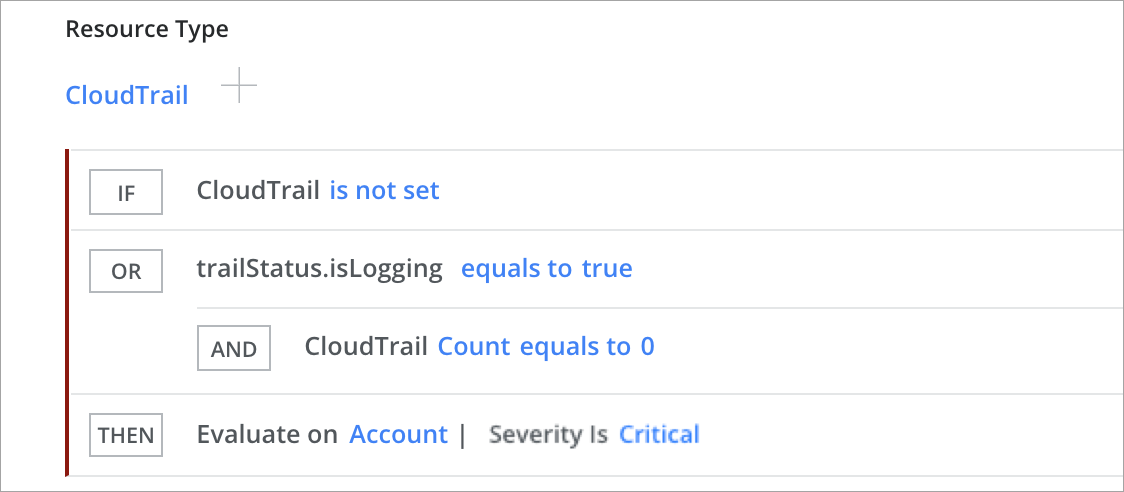
CloudTrail Logging Disabled for the Account
Security Group Should not Allow Inbound Traffic
No target tags set or target in a production environment.