Auto Remediation
Skyhigh CASB allows you to automatically remediate all incidents that are triggered when an IaaS Cloud Service Provider's Configuration policy is violated. To configure auto remediation for AWS, Azure, and GCP incidents using the Configuration Audit policy, see:
Skyhigh CASB scans every 24 hours, so incident data is updated daily.
The following incident states support auto-remediation:
- Archived. An incident is marked Archived if it is no longer valid. This could happen if the entity that triggered the violation (such as a user) is deleted from the Service Provider.
- Escalated. An incident is marked Escalated when it is moved to the next level of review.
- False Positive. When an incident is manually changed to False Positive status, it remains in that status even if a new scan detects the same violation.
- New. When an incident is detected for the first time during a scan, it is marked as a New incident.
- Open. An incident is marked as Open when it is resolved on the dashboard but is found again in the scan.
- Pending. An incident is marked Pending when it is pending review.
- Resolved. Incidents are marked Resolved if the configuration that caused the incident is resolved by a member of your team.
- Suppressed: When an incident is manually set to Suppressed status, it remains in that status even if a new scan detects the same violation.
NOTE: Suppressed is not listed in the UI, but you can search for it in the Omnibar.
- Suspended. If the incident is suspended, it is marked as Suspended.
- Under Investigation. An incident is marked Under Investigation when it is being actively reviewed.
- Viewed. An incident is marked Viewed when it has been viewed for review, but not otherwise categorized.
Manual Remediation
You can remediate the AWS, Azure, and GCP incidents manually. As an example, we have outlined how to remediate AWS incidents manually.
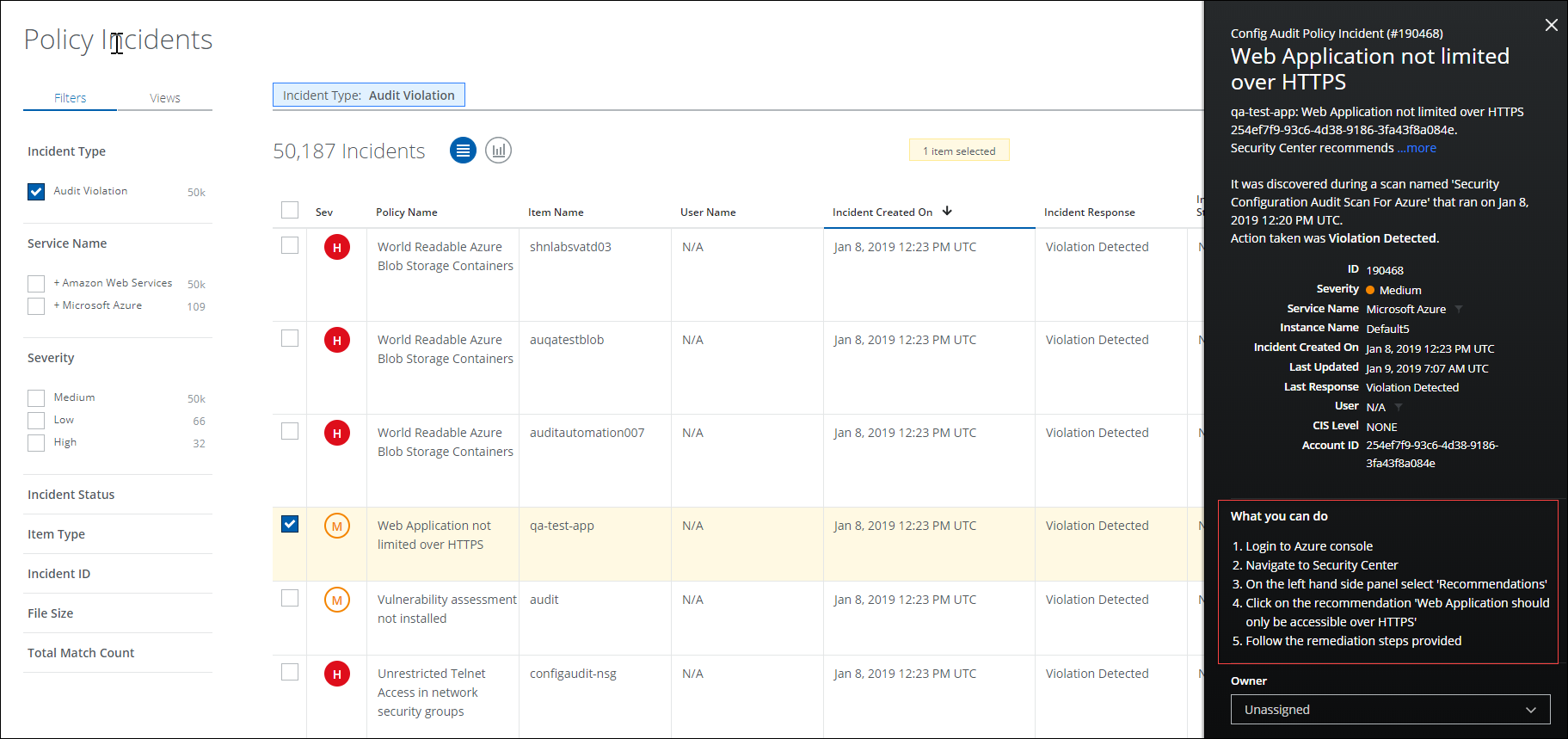
You can remediate the AWS policy incidents manually. When AWS policy incidents are generated, you can view the incidents and the recommended remediation steps in Skyhigh CASB.
To view AWS incident manual remediation steps:
- Go to Incidents > Policy Incidents.
- Find the incident and click the row to show the Cloud Card.
- Follow the steps displayed under What you can do.
Refresh AWS Incidents
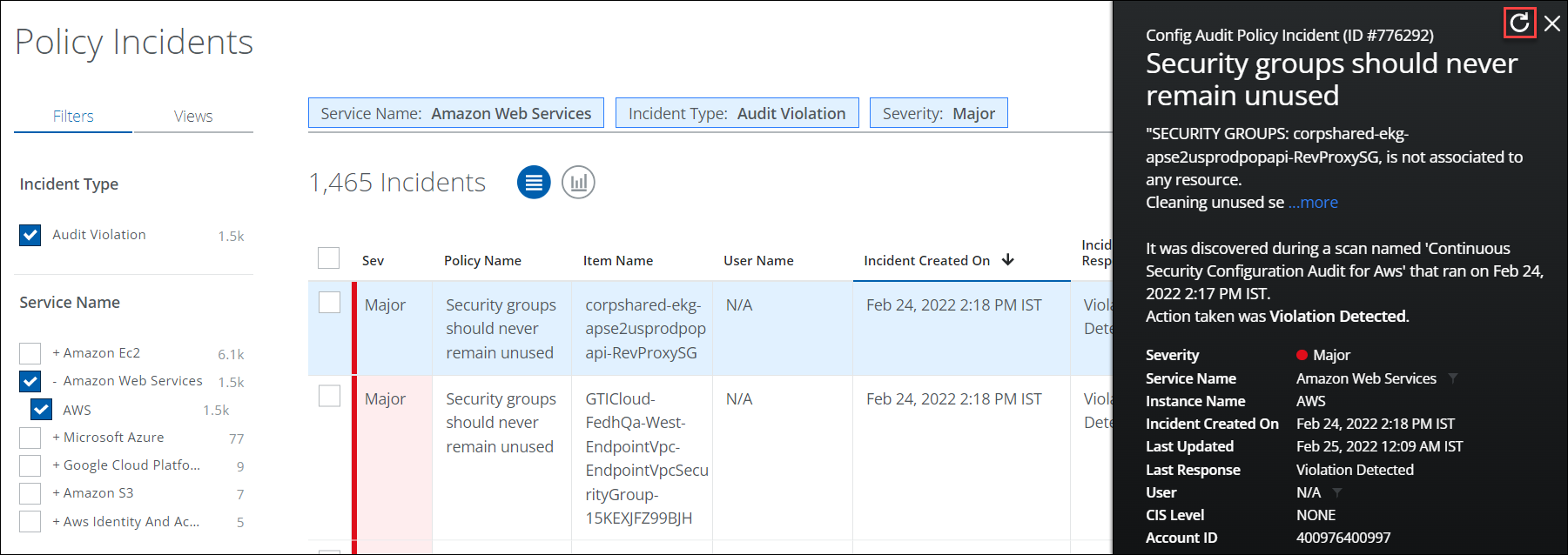
The refresh feature is used to view the most recent AWS violations on the Policy Incidents page. You can use this feature to refresh an AWS incident in real-time. You can also refresh incidents created from Custom Configuration Audit policies.
- Go to Incidents > Policy Incidents.
- Filter for Incident Type > Audit Violation, and Service Name > AWS.
- Click any incident in the table to view the Cloud Card for the specific incident.
- On the Cloud Card, click Refresh.
- A status message is displayed on the Cloud Card as the account is rescanned.
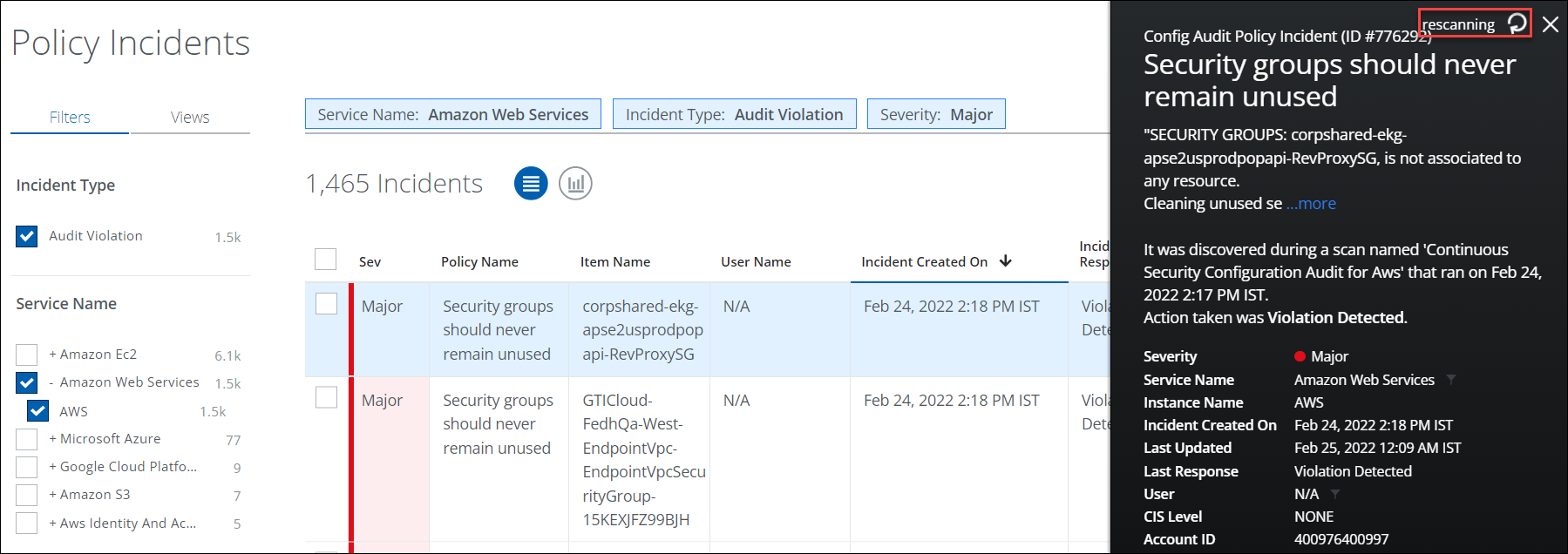 Any updates to the violation are displayed once the scan is complete.
Any updates to the violation are displayed once the scan is complete.