Integrate Simple Notification Service
SNS is an AWS service that provides a push messaging service. Skyhigh CASB integrates with SNS by allowing configuration audit policy incidents to be sent to SNS. This is achieved on a per audit policy level.
The workflow is:
- Create a Topic in SNS. This creates a Topic ARN.
- Add a subscriber to the topic.
- Add the Topic ARN as a response to the SHN Configuration Audit policy. Think of this as associating a Skyhigh CASB policy with an SNS topic.
Prerequisites
Make sure you have configured Amazon SNS in your organization's AWS deployment.
Step 1. Configure SNS for Skyhigh CASB
To configure SNS:
- Login to your AWS tenant and find the SNS service.
- Create a topic. We have used the name Skyhigh CASB_Config_Audit_Notifications with a display name of SHN ConAud.
- Create a subscription to the topic with the following:
- Topic ARN: Leave as default
- Protocol: Email
- Endpoint: Where you want the notification to be sent.
- When you receive a confirmation email to the email address entered above, select the Confirm Subscription link provided.
- You receive this confirmation once the link is clicked.
- Refresh the SNS subscription page and you will see a Subscription ID.
- Copy the Topic ARN. You will enter this later in Skyhigh CASB.
Step 2. Configure AWS SNS Permissions
To set up AWS SNS permissions:
- Navigate to IAM and create a policy using the JSON editor, use this permissions set:
{
"Version": "2012-10-17",
"Statement": [
{
"Effect": "Allow",
"Action": [
"sns:Publish",
"sns:Subscribe",
"sns:Unsubscribe",
"sqs:ListQueues",
"sqs:SendMessage",
"sns:GetTopicAttributes"
],
"Resource": "*"
}
]
}
- Give the policy the name: "Skyhigh CASB_SNS_SQS"
- Description: Use by Skyhigh CASB CASB to allow access to SNS and SQS
2. Navigate to Roles and add the policy to the Skyhigh CASB Role.
Step 3. Pair an Skyhigh CASB Policy with AWS SNS
Now you can associate a Skyhigh CASB Policy with an SNS feed to enable Real-Time Incident Validation.
- Navigate to AWS Configuration Audit.
- Edit the Unencrypted S3 Buckets policy.
- Click Next until you get to the Response for Unencrypted S3 Buckets page. Then click + to add a response.
- Select Send to SNS Topic as the response
- Enter the SNS Topic ARN as captured earlier.
- The response page will now have two actions:
5. Review the policy and make sure the SNS notification is present as a response, and the policy is enabled.
Attach Lambda Functions to SNS Topics
To attach Lambda Functions to SNS topics:
- Login to AWS and then navigate to the SNS dashboard. The steps to create an SNS topic are defined above.
- From the SNS dashboard, select Subscriptions.
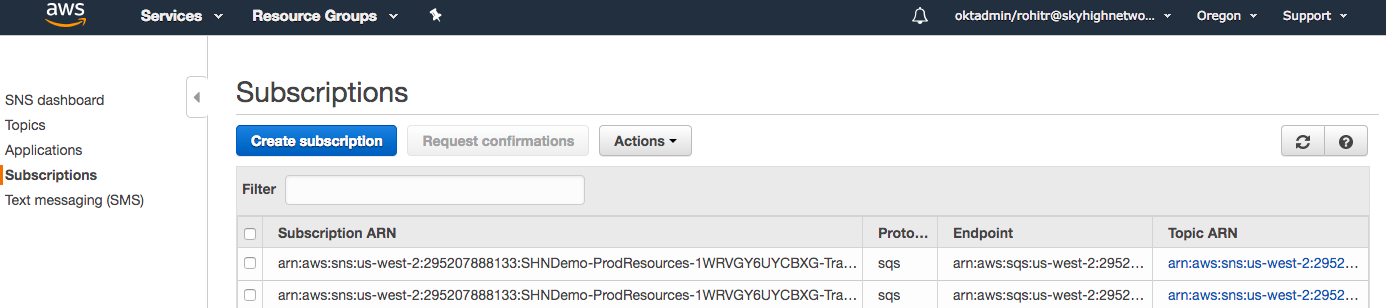
- Select Create Subscription.
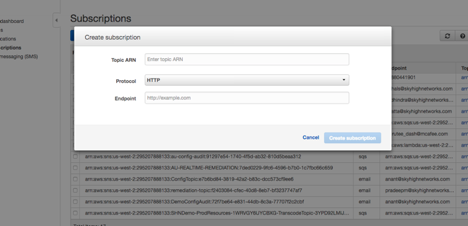
- In the Create Subscription dialog box, in Topic ARN, enter the SNS Topic ARN that you created in step 2. Then choose Protocol > AWS Lambda. From Endpoint, select the Lambda function ARN you want to trigger through SNS.
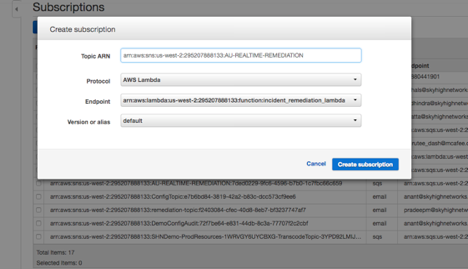
- Press Create subscription.
Sample Remediation Scripts
The following sample remediation scripts have been provided as examples of what is possible using Lambda. See the enclosed spreadsheet for information about what each Lambda function does, and the associated JSON and IAM/SNS/Lambda naming standards.
