Skyhigh Security Cloud 6.7.1 Release Notes (Aug 2024)
Legends Used
|
General Availability |
IMPORTANT: The Skyhigh Security Cloud 6.7.1 release addresses significant library updates for enhancing security and stability. For additional information about these fixes and updates, contact Skyhigh Support.
Skyhigh Cloud Platform
Skyhigh Data Loss Prevention (DLP)
Global Bypass List for Web/Shadow DLP Policies 
Skyhigh provides a global bypass list of predefined URLs for web/shadow services on the Data Protection (DLP) page (found under Policy > Web Policy > Policy > Web Policy > Data Protection (DLP) > Bypass List for DLP Scanning in Web) to exclude traffic from specific web/shadow services for DLP evaluation. This pre-configured list named Bypass List for DLP Scanning in Web enables you to define exclusions for Web/Shadow DLP policies based on browser telemetry URLs of major cloud service providers such as Google, Microsoft, and more.
Security Operations Center (SOC) analysts can leverage the bypass list to reduce the number of false positive DLP incidents. This enables SOC analysts to enhance their organization's data protection strategy and increase operational efficiency in incident management. For details, see Configure DLP Policy to Bypass URLs.

Classification Tester for DLP Classifications 
- The Classifications page (found under Policy > DLP Policies > Classifications > Test Classification) now includes a Classification Tester utility to validate DLP classifications.

- It generates match results for Skyhigh Built-In and Custom classifications defined using various conditions.

- The classification tester simplifies the process of validating expected match results by providing the following benefits. For details, see Evaluate Classifications.
| Classification Tester Benefits |
|---|
| Streamlined DLP Policy Deployment. Test classifications before integration in DLP policies to ensure seamless migration from data identifiers to data classification workflows. |
| Rapid Classification Validation. Quickly test classifications by entering text or uploading files. |
| Enhanced Confidence. Test classifications independently to verify the accuracy of your DLP classifications, building trust in your DLP strategy. |
| Unified Compatibility. Supports classifications for all types of DLP policies across Skyhigh SSE (Sanctioned DLP, Shadow/Web DLP, Private Access DLP, and more). |
| Risk Reduction. Minimize the risk of inaccurate matches, preventing false positives. |
View DLP Classification Events in the Audit Log 
- The Audit Log page (found under Settings > Audit Log) now includes various types of events for DLP classifications.
- Use the DLP Classifications event category to track events, such as the creation, modification, and deletion of DLP classifications by users within your organization.
- View the events for DLP classifications based on the selected event type (Classification created, Classification deleted, and Classification updated). For details, see View DLP Classification Events in the Audit Log.

For example, a Security Operations Center (SOC) may want to view the events for DLP classifications created by users on the Classifications page. To achieve this use case, the SOC can select DLP Classifications as the event category and select Classification created as the event type on the Audit Log page. This enables SOC admins to identify the users that triggered these classification updates and investigate any unauthorized or malicious activity related to classification management.
Additional DLP Improvement 
Enhanced AI Regular Expression Generator
Skyhigh has upgraded its AI-powered regular expression generator engine for Custom Advanced Patterns. This enhanced AI regular expression generator now provides complex regular expressions with improved stability and accuracy.
Skyhigh SSE Products
Skyhigh Secure Web Gateway
Dedicated Egress IP Support 
The Dedicated Egress IP service provided by Skyhigh Security (now available in LA) enables you to redirect your egress traffic through specific public IP addresses. These IP addresses are specifically assigned to your organization. Once you purchase these IP addresses, ownership will be transferred to your organization. This ensures that any WHOIS lookup accurately identifies and associates the IP address with the respective user.
You can choose to redirect all or specific traffic through the dedicated public IP addresses assigned to you. You can select which POP you want those IP addresses listed. Additionally, you can use policies to define which traffic to redirect using the Dedicated Egress IP assigned to you.
You will also have the flexibility to decide how the traffic behaves if the dedicated IP address assigned to you is not available. For details, see Skyhigh Dedicated Egress IP Capability.
.png?revision=1)


SWG for Cloud Integration with Trellix IVX 
Skyhigh SWG for Cloud integrates with Trellix IVX for Cloud for better sandboxing. If you intend to add extra malware scanning beyond what is provided by default using our GAM engine, you can achieve this with Trellix IVX. We already have a similar integration between our SWG for On-Prem and Trellix VX appliances, which has now been extended to the cloud. This will help you implement a hybrid setup, running both SWG for on-premises and cloud environments. After being filtered according to the rules of the default Anti-Malware rule set, web access requests are subsequently subjected to malware filtering with Trellix IVX Cloud. For details, see Trellix IVX Cloud — Perform Additional Malware Filtering.

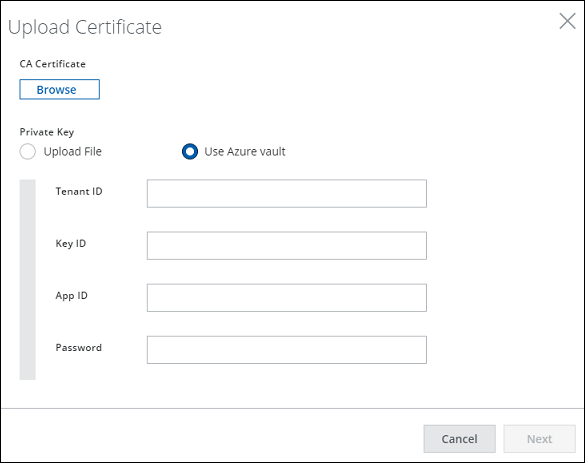
Integration with Azure Key Vault for Key Management in Cloud 
Skyhigh Secure Web Gateway for Cloud will support Azure Key Vault for Key Management integration. SWG On-Prem customers currently have the option of using Entrust and Thales for Key Management, which was missing for SWG for Cloud customers. This feature will greatly help bring parity between the two regarding feature offerings. This will greatly help Hybrid customers as well. For details, see Using Private Keys from an Azure Key Vault.
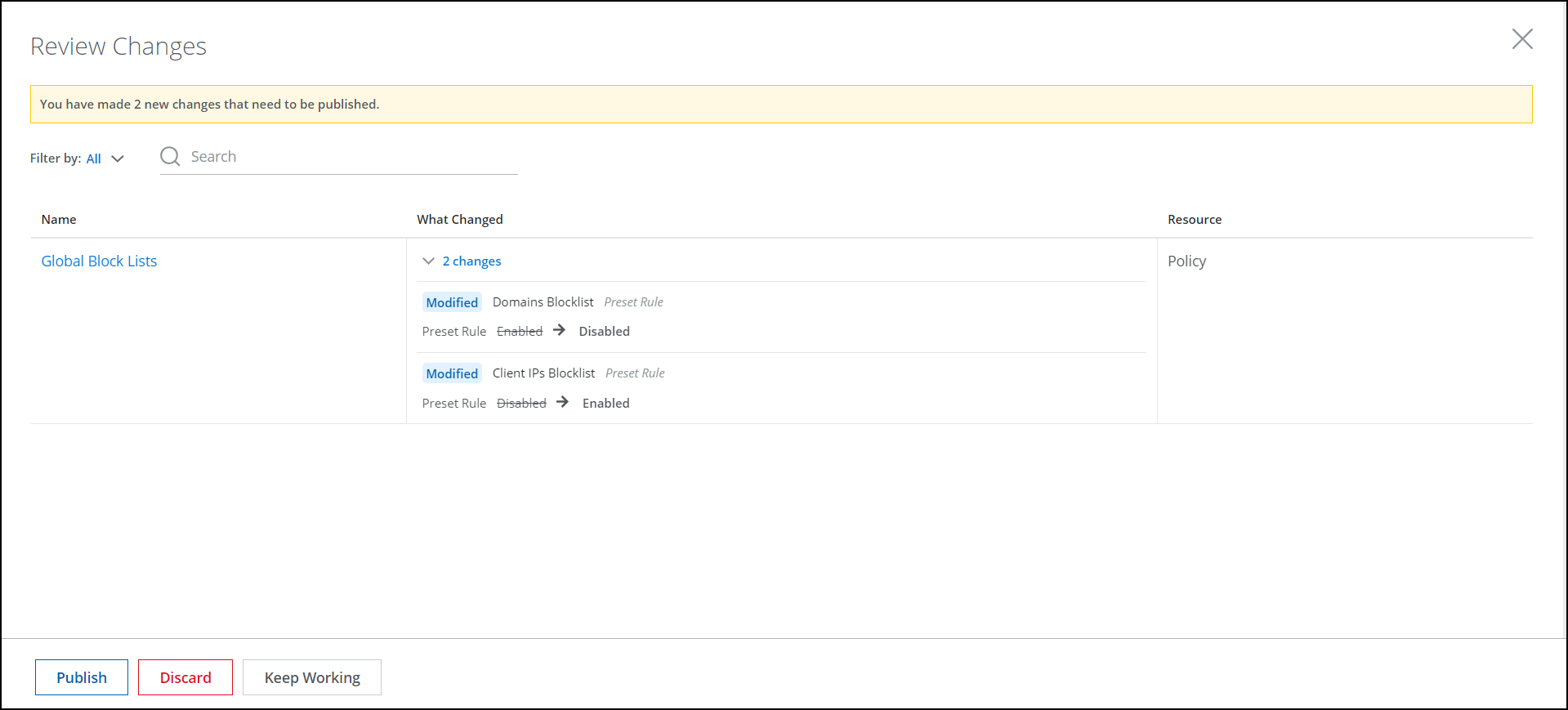
Comprehensive Review Changes Before Publish 
Review changes now show details of updates on various operations available, such as changed parameters like conditions, rule sets, and events within policies. The review changes specify the type of parameter change and provide details on the specific changes made for the Web Policy Builder. For details, see Review Configuration Changes When Working with Secure Web Gateway.
Clone and Edit for Web-builder Policies 
Skyhigh web policy now supports clone and edit for a rule set. You can clone and edit a rule set in the policy tree to preserve the default configuration and customize it for different regions. After you clone the rule set, you can edit the rules. For instance, if you need to modify specific details and test them, you can clone using the clone and edit option. You can disable the original policy and test the cloned version without affecting the original rule set. This approach minimizes changes from the existing/original policy. Whether you intend to use, modify, or reuse it, cloning offers flexibility for adaptation. This will also help you go hybrid. This feature was available in SWG On-Prem and has now been extended to SWG for Cloud. For details, see Clone a Rule Set.

Skyhigh Private Access
Deploy Secure App Connector V2 on Azure for TCP Applications 
The Secure App Connector V2 is now available as an Azure image on Microsoft's cloud platform, enabling deployment as a virtual machine (VM). For more details, see Deploy Secure App Connector V2 on Azure for TCP Applications.
Skyhigh Cloud Firewall
Tunnel Status Enhancement 
The Cloud Firewall now detects a broken tunnel within a few seconds, significantly reducing the previous detection time. This improvement enables the prompt initiation of the tunnel re-establishment process with a fresh response.
Skyhigh CASB
Monthly Email Notifications for Top Used Sanctioned Services 
The Skyhigh CASB now supports monthly email notifications named SaaS Security Coverage Monthly Report, listing the top-used sanctioned services for which granular security controls are not enabled. The email notifications assist you with securing the sanctioned services via API integration.
You can enable API integration or edit the notification settings via the SaaS Security Coverage Monthly Report. For details, see Enable API Integration via Email Notifications.

LLM Risk Attributes for AI Category Services 
Skyhigh CASB now captures Large Language Model (LLM) details for AI categories on the Cloud Registry to provide a deeper assessment of the risks related to shadow AI applications. The LLMs play a crucial role in protecting AI-generated content in Cloud Services.
Under the AI category, if any service supports LLM, the following risk attributes are displayed for each AI service:
- Jailbreaking. The degree to which a model can be manipulated to generate content misaligned with its intended purpose.
- Toxicity. The degree to which a model generates toxic or harmful content like threats and hate speech.
- Bias. The degree to which a model generates biased or unfair content that could be introduced due to training data.
- Malware. The degree to which a model can be manipulated to generate malware or known malware signatures.
For details, see LLM Risk Attributes for AI Category Services.
Salesforce Summer 2024 Support 
Skyhigh CASB now supports the latest Salesforce Summer 2024 version. For details, see Supported Versions of Structured Apps.

Historical User Risk Type Filter for Threats and Anomalies 
From the Threats and Anomalies list, you can filter and categorize your search by Historical User Risk Type for low, medium, and high-risk users. The Historical User Risk Score allows you to track and manage users’ typical usage patterns related to data security and take necessary actions to strengthen the defense against potential threats in your organization. For details, see Threats and Anomalies pages.
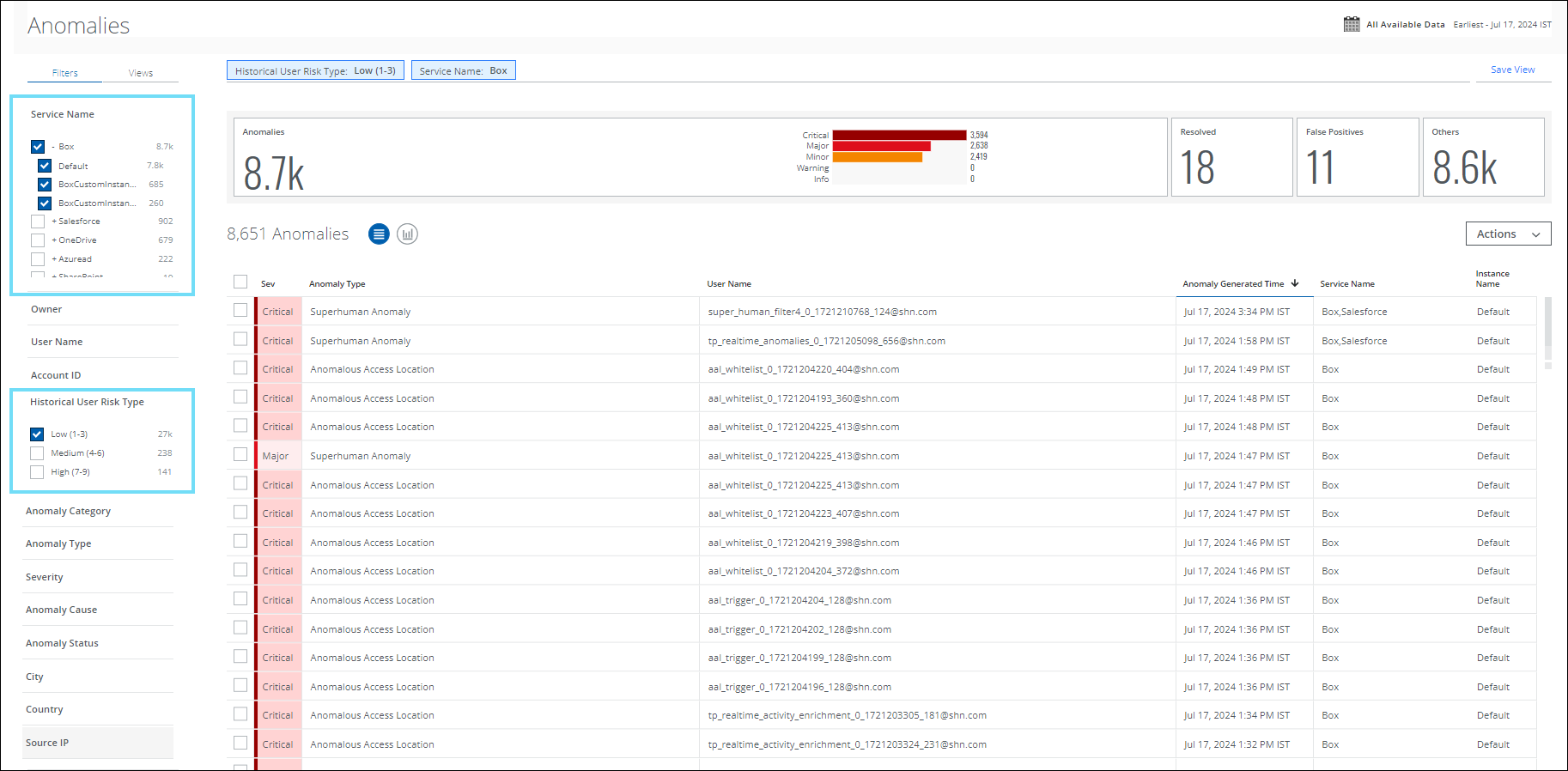
Historical User Risk Type Filter for User Activities 
From the Activities list, you can filter and categorize your search by Historical User Risk Type for low, medium, and high-risk users. The Historical User Risk Score allows you to track and manage users’ typical usage patterns related to data security and take necessary actions to strengthen the defense against potential threats in your organization. For details, see Activities page.
DLP Processing for Zoom In-Meeting Chat Messages 
Skyhigh CASB now detects and removes sensitive content posted in the Zoom real-time meeting chat with internal and external users. For details, see About Skyhigh CASB for Zoom.

Resolved and Known Issues
Click here to view Resolved and Known Issues
- For details, see Skyhigh Security Cloud Bug Fixes and Known Issues.
